BUUCTF逆向11-15题wp
Java逆向解密
jd-gui 打开,查看核心代码
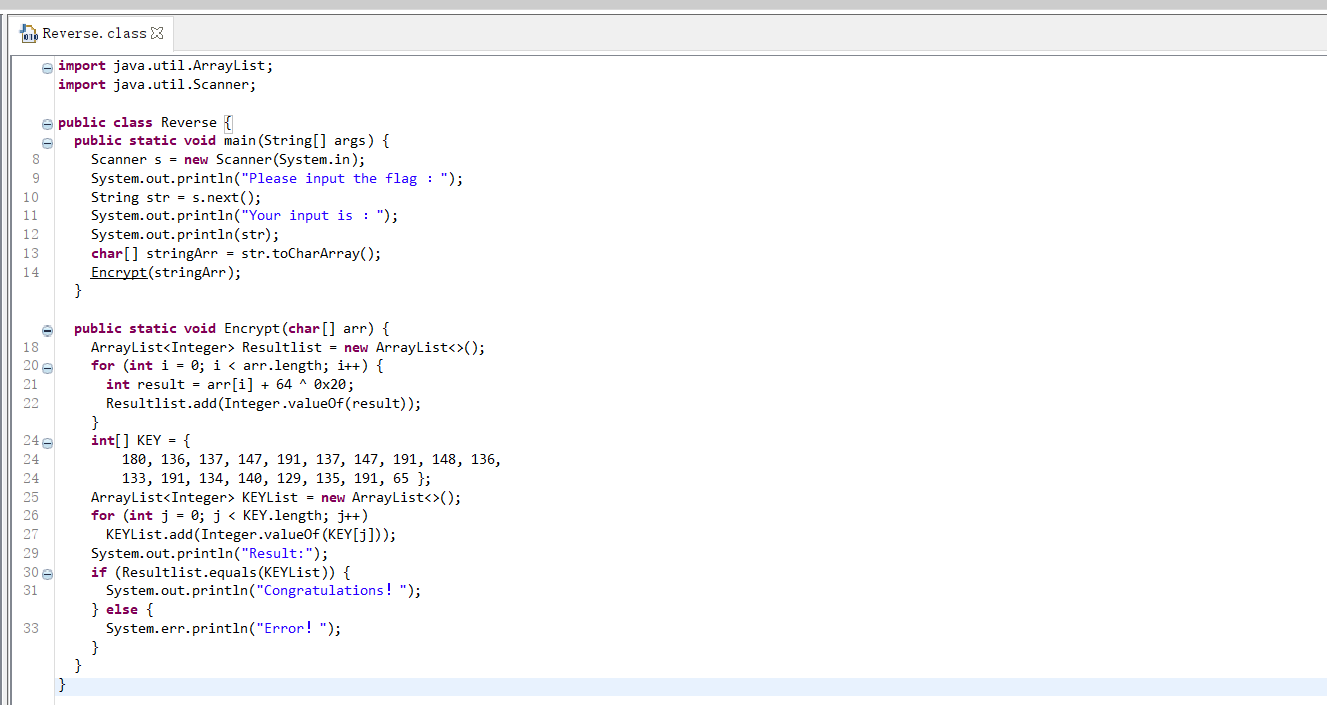
调用了 encrypt,在 encrypt 里会对输入的内容进行一个 +64^0x20 的操作然后与 key 对比,如果一致就输出 "Congratulations!"
所以得到脚本:
#include <bits/stdc++.h>
using namespace std;
int key[] = {
180, 136, 137, 147, 191, 137, 147, 191, 148, 136,
133, 191, 134, 140, 129, 135, 191, 65 };
int main() {
for (int i = 0; i < 18; i++)
cout << char(key[i] - 64 ^ 0x20);
return 0;
}
flag{This_is_the_flag_!}
刮开有奖
无壳,拖入 IDA 查看 main 函数
查看关键函数 dialogfunc
INT_PTR __stdcall DialogFunc(HWND hDlg, UINT a2, WPARAM a3, LPARAM a4)
{
const char *v4; // esi
const char *v5; // edi
int v7[2]; // [esp+8h] [ebp-20030h] BYREF
int v8; // [esp+10h] [ebp-20028h]
int v9; // [esp+14h] [ebp-20024h]
int v10; // [esp+18h] [ebp-20020h]
int v11; // [esp+1Ch] [ebp-2001Ch]
int v12; // [esp+20h] [ebp-20018h]
int v13; // [esp+24h] [ebp-20014h]
int v14; // [esp+28h] [ebp-20010h]
int v15; // [esp+2Ch] [ebp-2000Ch]
int v16; // [esp+30h] [ebp-20008h]
CHAR String[65536]; // [esp+34h] [ebp-20004h] BYREF
char v18[65536]; // [esp+10034h] [ebp-10004h] BYREF
if ( a2 == 272 )
return 1;
if ( a2 != 273 )
return 0;
if ( (_WORD)a3 == 1001 )
{
memset(String, 0, 0xFFFFu);
GetDlgItemTextA(hDlg, 1000, String, 0xFFFF);
if ( strlen(String) == 8 )
{
v7[0] = 90;
v7[1] = 74;
v8 = 83;
v9 = 69;
v10 = 67;
v11 = 97;
v12 = 78;
v13 = 72;
v14 = 51;
v15 = 110;
v16 = 103;
sub_4010F0(v7, 0, 10);
memset(v18, 0, 0xFFFFu);
v18[0] = String[5];
v18[2] = String[7];
v18[1] = String[6];
v4 = (const char *)sub_401000(v18, strlen(v18));
memset(v18, 0, 0xFFFFu);
v18[1] = String[3];
v18[0] = String[2];
v18[2] = String[4];
v5 = (const char *)sub_401000(v18, strlen(v18));
if ( String[0] == v7[0] + 34
&& String[1] == v10
&& 4 * String[2] - 141 == 3 * v8
&& String[3] / 4 == 2 * (v13 / 9)
&& !strcmp(v4, "ak1w")
&& !strcmp(v5, "V1Ax") )
{
MessageBoxA(hDlg, "U g3t 1T!", "@_@", 0);
}
}
return 0;
}
if ( (_WORD)a3 != 1 && (_WORD)a3 != 2 )
return 0;
EndDialog(hDlg, (unsigned __int16)a3);
return 1;
}
可以看到 v7 到 v16 其实是一个数组,String 也是
49 行进入一个 sub_4010F0 函数对 v7 进行了加工,跟进 sub_1010F0 看一下
int __cdecl sub_4010F0(int a1, int a2, int a3)
{
int result; // eax
int i; // esi
int v5; // ecx
int v6; // edx
result = a3;
for ( i = a2; i <= a3; a2 = i )
{
v5 = 4 * i;
v6 = *(_DWORD *)(4 * i + a1);
if ( a2 < result && i < result )
{
do
{
if ( v6 > *(_DWORD *)(a1 + 4 * result) )
{
if ( i >= result )
break;
++i;
*(_DWORD *)(v5 + a1) = *(_DWORD *)(a1 + 4 * result);
if ( i >= result )
break;
while ( *(_DWORD *)(a1 + 4 * i) <= v6 )
{
if ( ++i >= result )
goto LABEL_13;
}
if ( i >= result )
break;
v5 = 4 * i;
*(_DWORD *)(a1 + 4 * result) = *(_DWORD *)(4 * i + a1);
}
--result;
}
while ( i < result );
}
LABEL_13:
*(_DWORD *)(a1 + 4 * result) = v6;
sub_4010F0(a1, a2, i - 1);
result = a3;
++i;
}
return result;
}
直接复制粘贴稍作修改得到操作后的 v7
#include <bits/stdc++.h>
using namespace std;
int v7[] = {90, 74, 83, 69, 67, 97, 78, 72, 51, 110, 103};
int sub_4010F0(int *a1, int a2, int a3) {
int result; // eax
int i; // esi
int v5; // ecx
int v6; // edx
result = a3;
for (i = a2; i <= a3; a2 = i )
{
v5 = i;
//v6 = *(DWORD *)(4 * i + a1);
v6 = a1[i];
if ( a2 < result && i < result )
{
do
{
if ( v6 > a1[result] )
{
if ( i >= result )
break;
++i;
a1[v5] = a1[result];
if ( i >= result )
break;
while ( a1[i] <= v6 )
{
if ( ++i >= result )
goto LABEL_13;
}
if ( i >= result )
break;
v5 = 4 * i;
a1[result] = a1[i];
}
--result;
}
while ( i < result );
}
LABEL_13:
a1[result]= v6;
sub_4010F0(a1, a2, i - 1);
result = a3;
++i;
}
return result;
}
int main() {
sub_4010F0(v7, 0, 10);
for (int i = 0; i < 11; ++i)
cout << (char)v7[i];
return 0;
}
得到:3CSJNSaZEgn
接着往下看

先进入 sub_401000 看看
_BYTE *__cdecl sub_401000(int a1, int a2)
{
int v2; // eax
int v3; // esi
size_t v4; // ebx
_BYTE *v5; // eax
_BYTE *v6; // edi
int v7; // eax
_BYTE *v8; // ebx
int v9; // edi
int v10; // edx
int v11; // edi
int v12; // eax
int i; // esi
_BYTE *result; // eax
_BYTE *v15; // [esp+Ch] [ebp-10h]
_BYTE *v16; // [esp+10h] [ebp-Ch]
int v17; // [esp+14h] [ebp-8h]
int v18; // [esp+18h] [ebp-4h]
v2 = a2 / 3;
v3 = 0;
if ( a2 % 3 > 0 )
++v2;
v4 = 4 * v2 + 1;
v5 = malloc(v4);
v6 = v5;
v15 = v5;
if ( !v5 )
exit(0);
memset(v5, 0, v4);
v7 = a2;
v8 = v6;
v16 = v6;
if ( a2 > 0 )
{
while ( 1 )
{
v9 = 0;
v10 = 0;
v18 = 0;
do
{
if ( v3 >= v7 )
break;
++v10;
v9 = *(unsigned __int8 *)(v3 + a1) | (v9 << 8);
++v3;
}
while ( v10 < 3 );
v11 = v9 << (8 * (3 - v10));
v12 = 0;
v17 = v3;
for ( i = 18; i > -6; i -= 6 )
{
if ( v10 >= v12 )
{
*((_BYTE *)&v18 + v12) = (v11 >> i) & 0x3F;
v8 = v16;
}
else
{
*((_BYTE *)&v18 + v12) = 64;
}
*v8++ = byte_407830[*((char *)&v18 + v12++)];
v16 = v8;
}
v3 = v17;
if ( v17 >= a2 )
break;
v7 = a2;
}
v6 = v15;
}
result = v6;
*v8 = 0;
return result;
}
然后查看 byte_407830
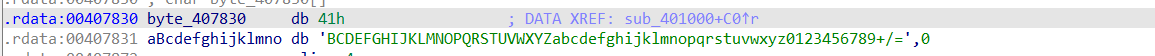
可以判定这个函数主要是进行了 base64 加密
所以 v4 和 v5 就可以通过 base64 解密得到
v4:jMp 以及 v5:WP1
然后再看那个最后的判断
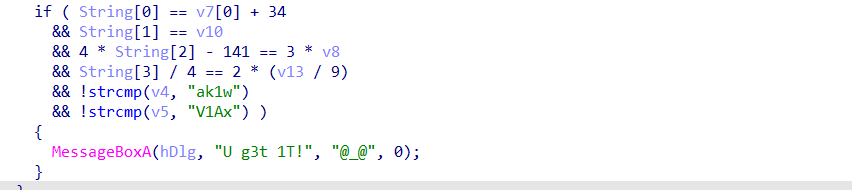
if ( String[0] == v7[0] + 34 //String == '3'+34 即第一位为'U'
&& String[1] == v10 //第二位为'J'
&& 4 * String[2] - 141 == 3 * v8 //第三位('E'*3+141)/4 即'W'
&& String[3] / 4 == 2 * (v13 / 9) //第四位为'P'
&& !strcmp(v4, "ak1w") //v4为jMp
&& !strcmp(v5, "V1Ax") ) //v5为WP1
//拼接起来即flag{UJWP1jMp}
flag{UJWP1jMp}
[GXYCTF2019]luck_guy
IDA 载入,查看主函数
进入关键函数 patch_me
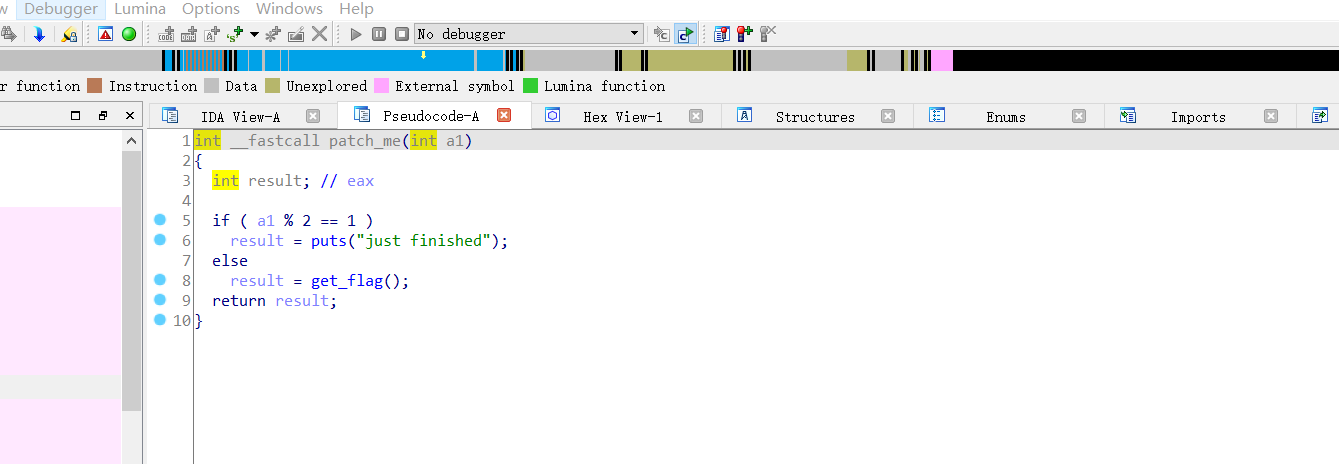
看到关键函数 get_flag,跟进去看到核心部分如下
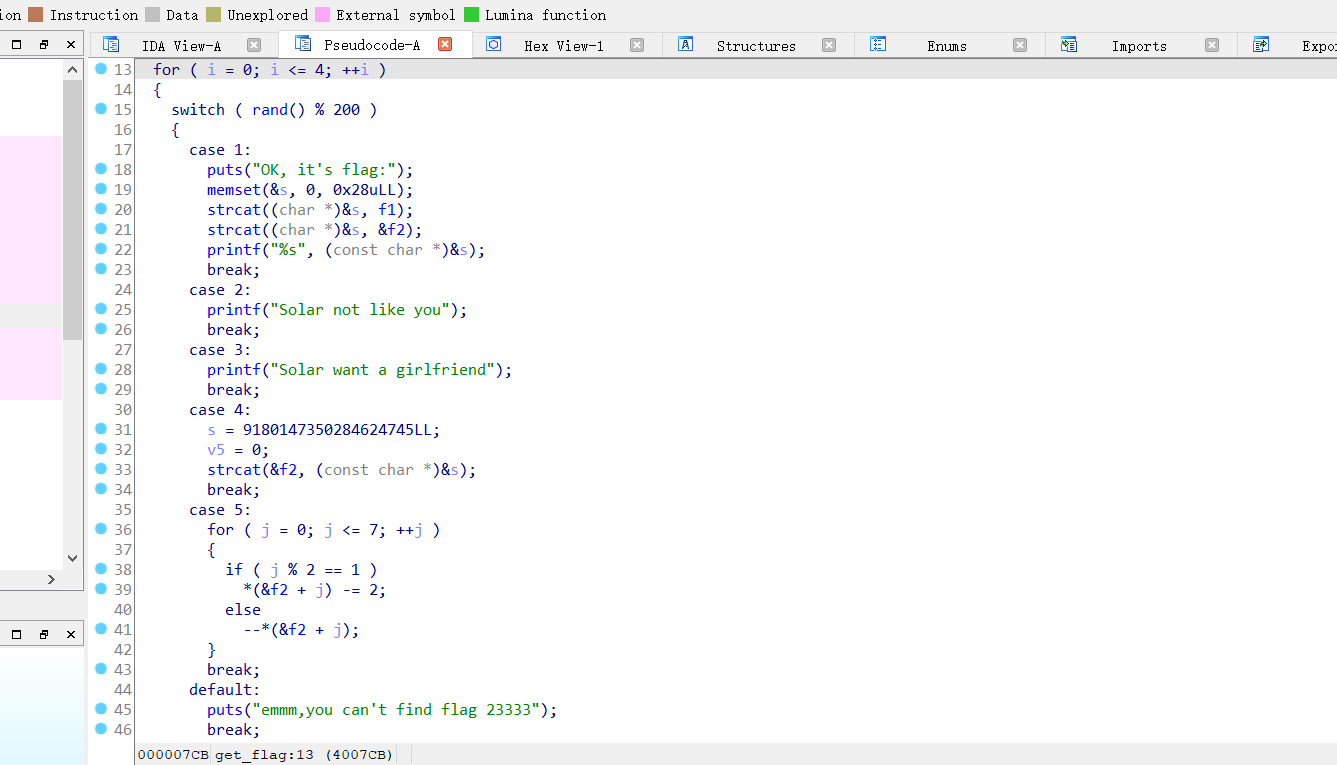
分析一下这一部分的代码,首先会获得一个随机数种子,然后 %200 进入 switch
只有 1,4,5 这三个操作是有用的,而且还要按照 4-->5-->1 的顺序,难怪题目为 lucky_boy
首先看 case4
case 4:
s = 0x7F666F6067756369LL;
v5 = 0;
strcat(&f2, (const char *)&s);
break;
可以发现,case4 对 f2 进行了赋值,将 s 赋值给 f2
然后看 case5
case 5:
for ( j = 0; j <= 7; ++j )
{
if ( j % 2 == 1 )
*(&f2 + j) -= 2;
else
--*(&f2 + j);
}
break;
将 f2 进行了些许变换,写出脚本
#include <bits/stdc++.h>
using namespace std;
char f2[] = {0x69, 0x63, 0x75, 0x67, 0x60, 0x6f, 0x66, 0x7f};
//由于IDA是反编译C语言,s=0x69,0x63,0x75,0x67,0x60,0x6f,0x66,0x7f应该逆序成s=0x7F666F6067756369LL作为小端储存
int main() {
for (int i = 0; i < 8; i++)
if (i % 2 == 1) f2[i] -= 2;
else --f2[i];
for (int i = 0; i < 8; i++)
cout << f2[i];
return 0;
}
得到了半个 flag:hate_me}
然后看 case1
case 1:
puts("OK, it's flag:");
memset(&s, 0, 0x28uLL);
strcat((char *)&s, f1);
strcat((char *)&s, &f2);
printf("%s", (const char *)&s);
break;
得知 flag 是由 f1 和 f2 拼接而成的,f2 就是我们上文得到的 "hate_me}",f1 的值双击就可以查看
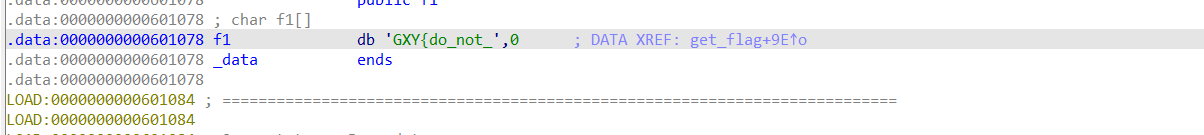
flag{do_not_hate_me}
findit
GDA 打开,查看 main 函数(截图没截全,右边还有一大截)
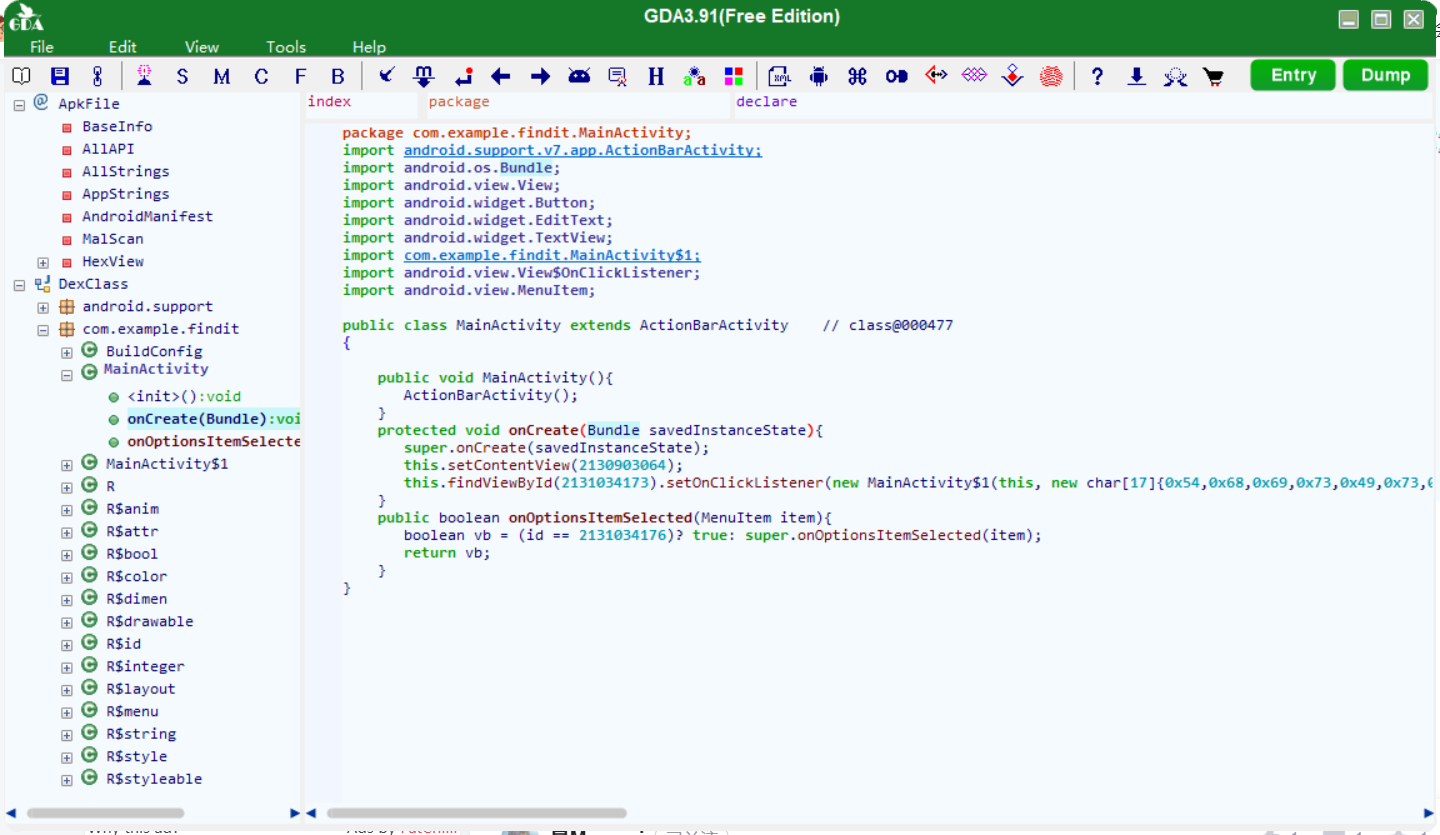
发现有两组十六进制数,输出看看是什么
#include <bits/stdc++.h>
using namespace std;
char f2[] = {0x54,0x68,0x69,0x73,0x49,0x73,0x54,0x68,0x65,0x46,0x6c,0x61,0x67,0x48,0x6f,0x6d,0x65};
char c2[] = {0x70,0x76,0x6b,0x71,0x7b,0x6d,0x31,0x36,0x34,0x36,0x37,0x35,0x32,0x36,0x32,0x30,0x33,0x33,0x6c,0x34,0x6d,0x34,0x39,0x6c,0x6e,0x70,0x37,0x70,0x39,0x6d,0x6e,0x6b,0x32,0x38,0x6b,0x37,0x35,0x7d};
int main() {
for (int i = 0; i < 17; i++)
cout << f2[i];
cout << endl;
for (int i = 0; i < 38; i++)
cout << c2[i];
return 0;
}
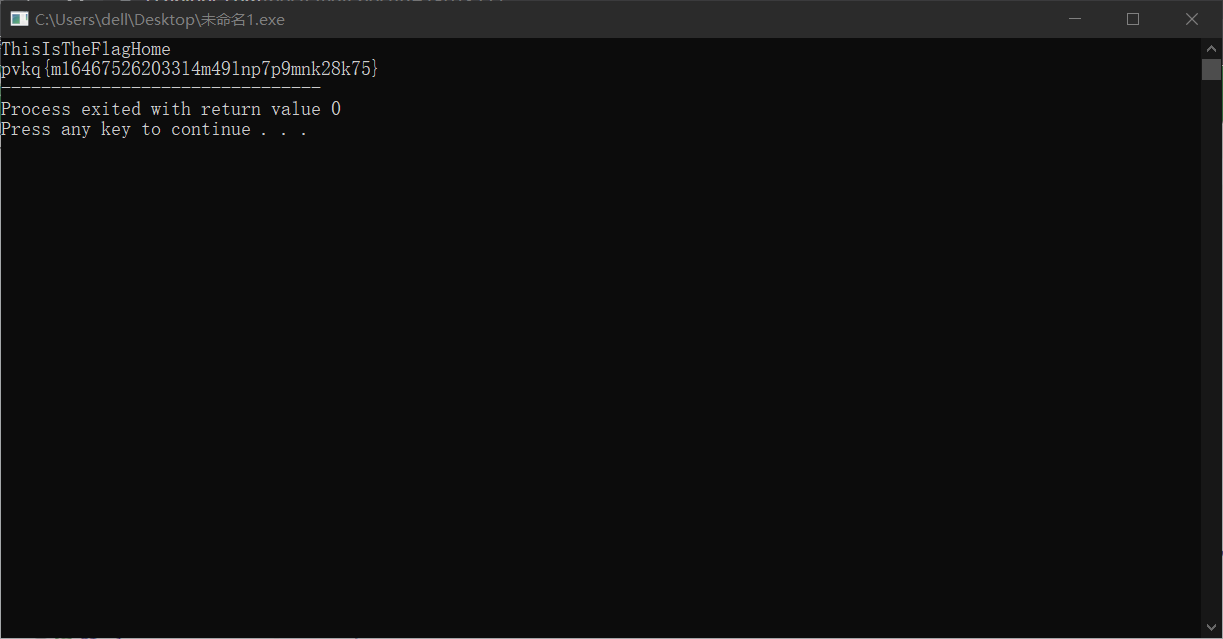
可以看到 pvkq{m164675262033l4m49lnp7p9mnk28k75}
猜测是凯撒加密,计算可得偏移量 10,解密得到 flag
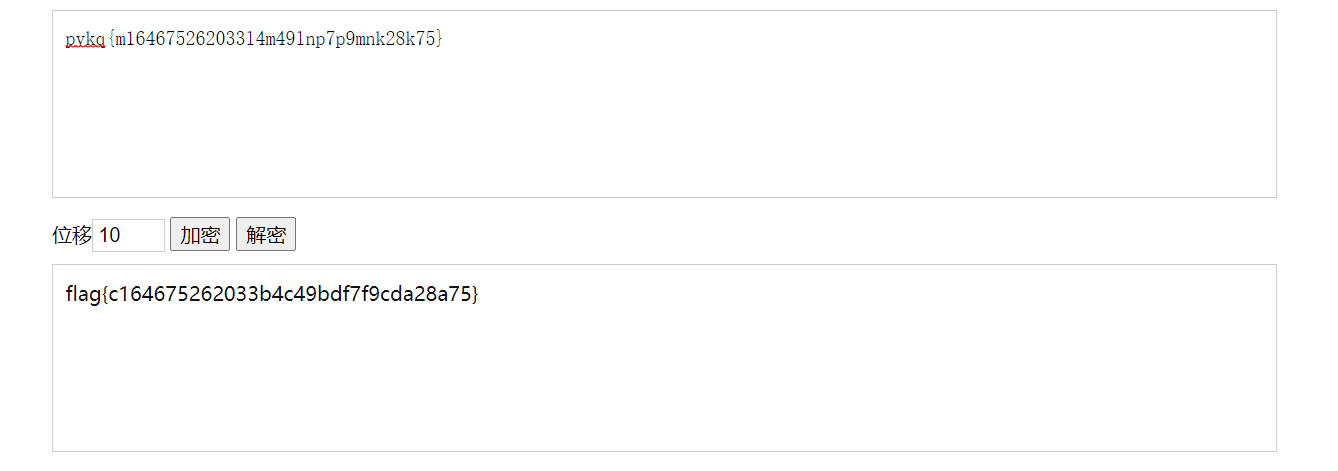
flag{c164675262033b4c49bdf7f9cda28a75}
简单注册器
用 jadx-gui 打开(这里尝试过 Androidkiller 和 GDA,但不知为何反编译出来的代码都不全,影响分析),找到 main 函数
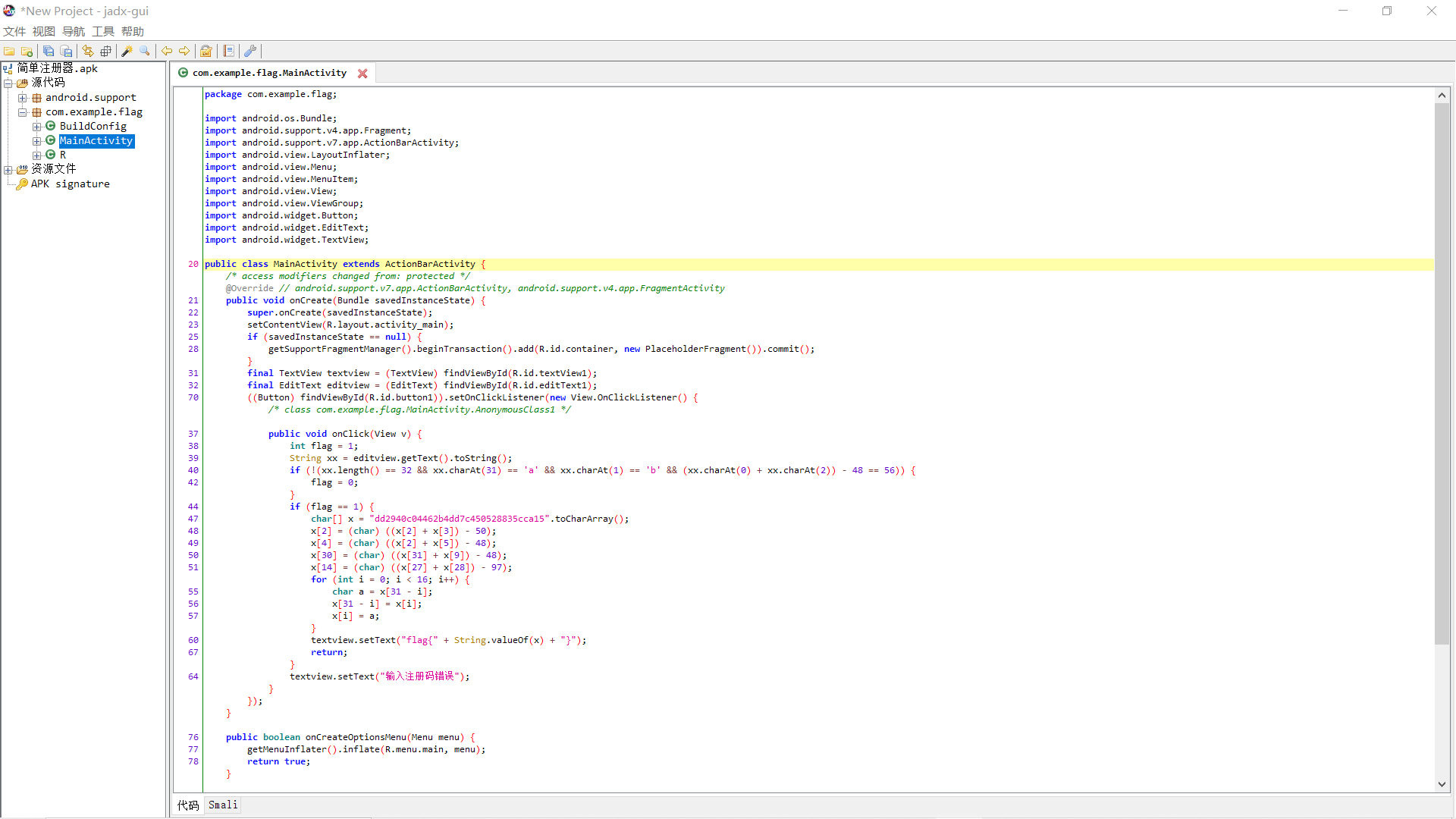
注意到关键部分:
char[] x = "dd2940c04462b4dd7c450528835cca15".toCharArray();
x[2] = (char) ((x[2] + x[3]) - 50);
x[4] = (char) ((x[2] + x[5]) - 48);
x[30] = (char) ((x[31] + x[9]) - 48);
x[14] = (char) ((x[27] + x[28]) - 97);
for (int i = 0; i < 16; i++) {
char a = x[31 - i];
x[31 - i] = x[i];
x[i] = a;
}
textview.setText("flag{" + String.valueOf(x) + "}");
很明显了,是对 x[2],x[4],x[30],x[14] 进行了相应变换然后循环将 x[31-i] 与 x[i] 交换,然后输出
于是得到脚本
#include <bits/stdc++.h>
using namespace std;
char x[] = "dd2940c04462b4dd7c450528835cca15";
int main() {
x[2] = (char) ((x[2] + x[3]) - 50);
x[4] = (char) ((x[2] + x[5]) - 48);
x[30] = (char) ((x[31] + x[9]) - 48);
x[14] = (char) ((x[27] + x[28]) - 97);
for (int i = 0; i < 16; i++) swap(x[31 - i], x[i]);
printf("%s", x);
return 0;
}
flag{59acc538825054c7de4b26440c0999dd}



 浙公网安备 33010602011771号
浙公网安备 33010602011771号