攻防世界reverse-elrond32
- 题目来源:tinyctf-2014
扔进IDA,查看main函数
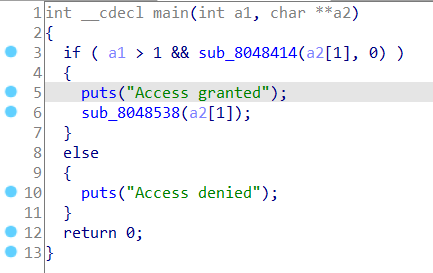
可以看到关键函数 sub_8048414,点进去看看
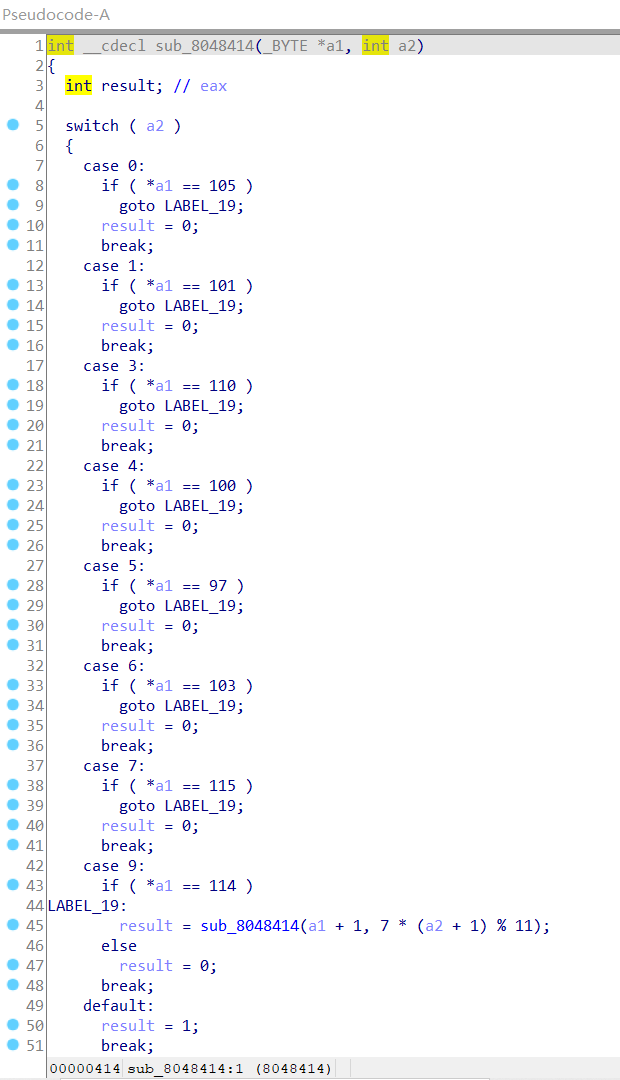
a2初始值传入0,经过运算,a2的值依次是:0 7 1 3 6 5 9 4
即 a1=[105,115,101,110,103,97,114,100]
继续分析 sub_8048538 这个函数
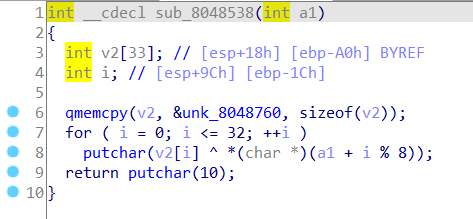
知道 v2 是从 unk_8048760 处复制了 33 个 int,查看 unk_8048760 的值

(截图太麻烦了,图片来源:这里)
一个 int 占 4 个内存,所以剩下 3 个的内存用 0 填充,可以得出
int v2[33] = { 0x0F,0x1F,0x04,0x09,0x1C,0x12,0x42,0x09,0x0C,0x44,0x0D,0x07,0x09,0x06,0x2D,0x37,0x59,0x1E,0x00,0x59,0x0F,0x08,0x1C,0x23,0x36,0x07,0x55,0x02,0x0C,0x08,0x41,0x0A,0x14};
最后写脚本即可得到flag
#include<bits/stdc++.h>
using namespace std;
int a1[20] = {105, 101, 0, 110, 100, 97, 103, 115, 0, 114};
int main() {
int a2[20], k = 0;
int v2[33] = {
0x0F,0x1F,0x04,0x09,0x1C,0x12,0x42,0x09,0x0C,0x44,0x0D,0x07,0x09,0x06,0x2D,0x37,0x59,0x1E,0x00,0x59,0x0F,0x08,0x1C,0x23,0x36,0x07,0x55,0x02,0x0C,0x08,0x41,0x0A,0x14};
for (int i = 0; ; i = 7 * (i + 1) % 11, k++){
a2[k] = a1[i];
if (i == 2 || i == 8 || i > 9) break;
}
for (int i = 0; i <= 32; i++) putchar(v2[i] ^ a2[i % 8]);
}



 浙公网安备 33010602011771号
浙公网安备 33010602011771号