IOS IKEv2 IPSec配置(SVTI)
1、拓扑
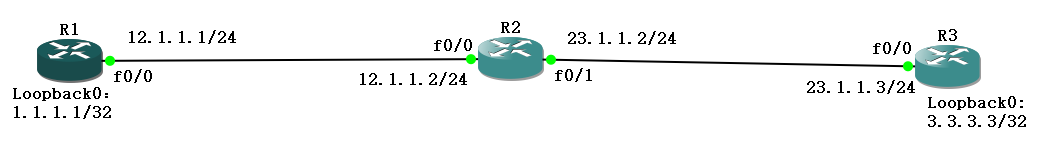
2、目标
通过在R1和R3建立IPSEC,让R1的Lo0和R3的Lo0互通
3、配置步骤
IP地址配置忽略。
3.1、打通路由器连通性
为了实现R1和R3物理接口网段互通,通过R1和R3的静态路由配置。
R1(config)#ip route 23.1.1.0 255.255.255.0 12.1.1.2 R1(config)# R3(config)#ip route 12.1.1.0 255.255.255.0 23.1.1.2 R3(config)#
R1(config)#do ping 23.1.1.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 23.1.1.3, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 56/64/76 ms
R1(config)#
3.2、配置IPSec
第一阶段:
| R1 | R3 |
| R1#configure Configuring from terminal, memory, or network [terminal]? Enter configuration commands, one per line. End with CNTL/Z. R1(config)# R1(config)#crypto ikev2 proposal Ikev2-Policy IKEv2 proposal MUST have atleast an encryption algorithm, an integrity algorithm and a dh group configured R1(config-ikev2-proposal)# encryption aes-cbc-256 R1(config-ikev2-proposal)# integrity sha1 R1(config-ikev2-proposal)# group 2 R1(config-ikev2-proposal)# exit R1(config)# R1(config)#crypto ikev2 policy Ikev2-Policy IKEv2 policy MUST have atleast one complete proposal attached R1(config-ikev2-policy)# proposal Ikev2-Policy R1(config-ikev2-policy)# match address local 12.1.1.1 R1(config-ikev2-policy)# exit R1(config)# R1(config)#crypto ikev2 keyring ipsec2-keyring R1(config-ikev2-keyring)# peer 23.1.1.3 R1(config-ikev2-keyring-peer)# address 23.1.1.3 R1(config-ikev2-keyring-peer)# pre-shared-key cisco R1(config-ikev2-keyring-peer)# exit R1(config-ikev2-keyring)# exit R1(config)# R1(config)#crypto ikev2 profile Ikev2-Profile IKEv2 profile MUST have: 1. A local and a remote authentication method. 2. A match identity or a match certificate or match any statement. R1(config-ikev2-profile)# match address local 12.1.1.1 R1(config-ikev2-profile)#$ntity remote address 23.1.1.3 255.255.255.255 R1(config-ikev2-profile)# authentication remote pre-share R1(config-ikev2-profile)# authentication local pre-share R1(config-ikev2-profile)# lifetime 28800 R1(config-ikev2-profile)# dpd 10 5 on-demand R1(config-ikev2-profile)# keyring local ipsec2-keyring R1(config-ikev2-profile)# exit R1(config)# |
R3(config)#crypto ikev2 proposal Ikev2-Policy IKEv2 proposal MUST have atleast an encryption algorithm, an integrity algorithm and a dh group configured R3(config-ikev2-proposal)# encryption aes-cbc-256 R3(config-ikev2-proposal)# integrity sha1 R3(config-ikev2-proposal)# group 2 R3(config-ikev2-proposal)# exit R3(config)# R3(config)#crypto ikev2 policy Ikev2-Policy IKEv2 policy MUST have atleast one complete proposal attached R3(config-ikev2-policy)# proposal Ikev2-Policy R3(config-ikev2-policy)# match address local 23.1.1.3 R3(config-ikev2-policy)# exit R3(config)# R3(config)#crypto ikev2 keyring ipsec2-keyring R3(config-ikev2-keyring)# peer 12.1.1.1 R3(config-ikev2-keyring-peer)# address 12.1.1.1 R3(config-ikev2-keyring-peer)# pre-shared-key cisco R3(config-ikev2-keyring-peer)# exit R3(config-ikev2-keyring)# exit R3(config)# R3(config)#crypto ikev2 profile Ikev2-Profile IKEv2 profile MUST have: 1. A local and a remote authentication method. 2. A match identity or a match certificate or match any statement. R3(config-ikev2-profile)# match address local 23.1.1.3 R3(config-ikev2-profile)#$ntity remote address 12.1.1.2 255.255.255.255 R3(config-ikev2-profile)# authentication remote pre-share R3(config-ikev2-profile)# authentication local pre-share R3(config-ikev2-profile)# lifetime 28800 R3(config-ikev2-profile)# dpd 10 5 on-demand R3(config-ikev2-profile)# keyring local ipsec2-keyring R3(config-ikev2-profile)# exit R3(config)# |
第二阶段:
| R1 | R2 |
| R1(config)# crypto ipsec transform-set TransformSet esp-aes 256 esp-sha256-hmac R1(cfg-crypto-trans)# mode tunnel R1(cfg-crypto-trans)# exit R1(config)# R1(config)#crypto ipsec profile IPsecProfile R1(ipsec-profile)# set transform-set TransformSet R1(ipsec-profile)# set ikev2-profile Ikev2-Profile R1(ipsec-profile)# set security-association lifetime seconds 3600 R1(ipsec-profile)# exit R1(config)# |
R3(config)# crypto ipsec transform-set TransformSet esp-aes 256 esp-sha256-hmac R3(cfg-crypto-trans)# mode tunnel R3(cfg-crypto-trans)# exit R3(config)# R3(config)#crypto ipsec profile IPsecProfile R3(ipsec-profile)# set transform-set TransformSet R3(ipsec-profile)# set ikev2-profile Ikev2-Profile R3(ipsec-profile)# set security-association lifetime seconds 3600 R3(ipsec-profile)# exit R3(config)# |
接口调用:
| R1 | R2 |
| R1(config)# int Tunnel11 R1(config-if)# ip address 169.254.0.1 255.255.255.255 R1(config-if)# tunnel mode ipsec ipv4 R1(config-if)# ip tcp adjust-mss 1350 R1(config-if)# tunnel source 12.1.1.1 R1(config-if)# tunnel destination 23.1.1.3 R1(config-if)# tunnel protection ipsec profile IPsecProfile R1(config-if)# exit R1(config)# *Sep 13 02:42:34.823: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is ON R1(config)# *Sep 13 02:42:35.806: %LINEPROTO-5-UPDOWN: Line protocol on Interface Tunnel11, changed state to down |
R3(config)# int Tunnel11 R3(config-if)# ip address 169.254.0.2 255.255.255.255 R3(config-if)# tunnel mode ipsec ipv4 R3(config-if)# ip tcp adjust-mss 1350 R3(config-if)# tunnel source 23.1.1.3 R3(config-if)# tunnel destination 12.1.1.1 R3(config-if)# tunnel protection ipsec profile IPsecProfile R3(config-if)# exit R3(config)# *Sep 13 02:43:21.723: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is ON R3(config)# *Sep 13 02:43:22.709: %LINEPROTO-5-UPDOWN: Line protocol on Interface Tunnel11, changed state to down |
4、状态检查
检查Tunnel建立情况
R1#sho ip int br Interface IP-Address OK? Method Status Protocol Ethernet0/0 12.1.1.1 YES manual up up Ethernet0/1 unassigned YES unset administratively down down Ethernet0/2 unassigned YES unset administratively down down Ethernet0/3 unassigned YES unset administratively down down Ethernet1/0 unassigned YES unset administratively down down Ethernet1/1 unassigned YES unset administratively down down Ethernet1/2 unassigned YES unset administratively down down Ethernet1/3 unassigned YES unset administratively down down Loopback0 1.1.1.1 YES manual up up Tunnel11 169.254.0.1 YES manual up up R1#
为了让1.1.1.1和3.3.3.3之间通过Tunnel之间互通;需要将目标网段出接口指向到Tunnel11
R3(config)#ip route 1.1.1.1 255.255.255.255 Tunnel11 R3(config)# R1(config)#ip route 3.3.3.3 255.255.255.255 Tunnel11 R1(config)#do ping 3.3.3.3 so 1.1.1.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 3.3.3.3, timeout is 2 seconds: Packet sent with a source address of 1.1.1.1 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 2/4/6 ms R1(config)#
如果需要Tunnel的169.254.0.x的接口互通,也可以指定路由通过Tunnel。
查看IPsec状态:
R1#sho crypto session brief Status: A- Active, U - Up, D - Down, I - Idle, S - Standby, N - Negotiating K - No IKE ivrf = (none) Peer I/F Username Group/Phase1_id Uptime Status 23.1.1.3 Tu11 23.1.1.3 00:05:09 UA R1#show crypto ikev2 sa IPv4 Crypto IKEv2 SA Tunnel-id Local Remote fvrf/ivrf Status 1 12.1.1.1/500 23.1.1.3/500 none/none READY Encr: AES-CBC, keysize: 256, Hash: SHA96, DH Grp:2, Auth sign: PSK, Auth verify: PSK Life/Active Time: 28800/317 sec IPv6 Crypto IKEv2 SA R1#show crypto ipsec sa | i encap|decap #pkts encaps: 15, #pkts encrypt: 15, #pkts digest: 15 #pkts decaps: 15, #pkts decrypt: 15, #pkts verify: 15 R1#
Refer to:
https://www.cisco.com/c/en/us/support/docs/security-vpn/ipsec-architecture-implementation/214938-configuring-ikev2-vrf-aware-svti.html
好好学习,天天向上!


