BUUCTF--Strange apk
测试文件:https://wwa.lanzous.com/ipbTSeoof6d
代码分析
APK数据处理
主要关注到这段代码
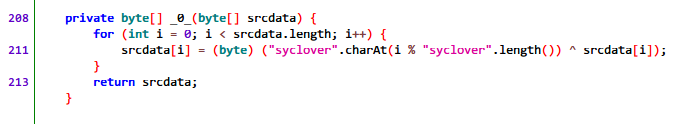
这里将某段数据与“syclover”循环异或,这段数据,在解压apk后,可以看到一个data文件,就是里面的数据。写出脚本
Python3
# -*- coding:utf-8 -*- import binascii model = 'syclover' new = '' res = '' with open(r'C:\Users\10245\Desktop\attachment2\assets\data', 'rb') as f: byte = f.read() for i in range(len(byte)): num = ord(model[i%len(model)]) ^ byte[i] tmp = hex(num)[2:] if len(tmp) == 1: tmp = '0'+tmp; new += tmp print (new) res = binascii.a2b_hex(new) with open(r'C:\Users\10245\Desktop\attachment2\assets\res', 'wb+') as f: f.write(res)
Python2
# !/usr/bin/env python2 # -*- coding:utf-8 -*- if __name__ == "__main__": key = "syclover" encode = open(r'C:\Users\10245\Desktop\attachment2\assets\data', "rb").read() fdecode = open(r'C:\Users\10245\Desktop\attachment2\assets\mydata', "wb") decode = '' cout = 0 for d in encode: decode += chr(ord(d) ^ ord(key[cout % 8])) cout += 1 with open(r'C:\Users\10245\Desktop\attachment2\assets\mydata', 'wb') as f: f.write(decode)
第一段flag
会生成一个新的apk文件,打开
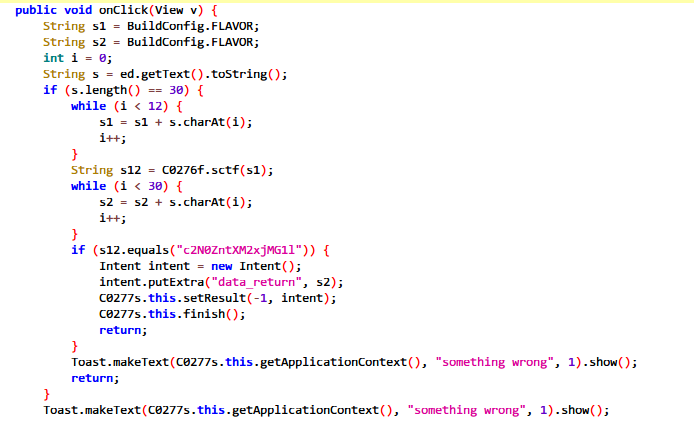
把那段密文base64解密后得到sctf{W3lc0me,是flag的第一部分
第二部分flag
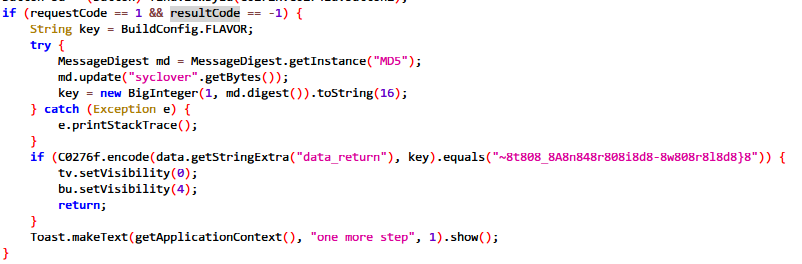
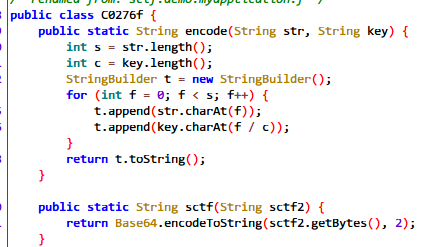
这里将syclover进行md5加密后,与第二部分flag间隔相加,得到~8t808_8A8n848r808i8d8-8w808r8l8d8}8
因此我们只需要取奇数位字符,与第一部分字符串结合就行
脚本
model = "~8t808_8A8n848r808i8d8-8w808r8l8d8}8" flag = "sctf{W3lc0me" for i in range(0, len(model),2): flag += model[i] print(flag)
get flag!
sctf{W3lc0me~t0_An4r0id-w0rld}



 浙公网安备 33010602011771号
浙公网安备 33010602011771号