2020 Zh3r0 部分WP
测试文件:https://wwa.lanzous.com/iEIHddtrkwb
crypto
RSA-Warmup
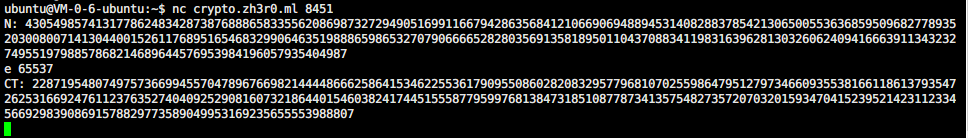
就是一个简单的RSA解密
import gmpy2 import rsa from Crypto.Util.number import long_to_bytes e = 65537 n = 410498917537920303260266719109576967260993991665256953311742364884150210432915310835865207111036400830428810414329739908868490183839915546875004813875948578775268863603721314519816891107904905552051724797372408241008165216310668239217161510001533176220623603332300737298195416759316147977982808952744735185499042992851 p = 2314713113 q = 177343323987952153300073657598697401625250131662971640715694327551921640853863910709121734305842851476699959583427538092867964922545421095074171644819272503415099832116310007062122212597455875540310089735674473729482935372436656792386332115621247260900026535310987689254169536801391139817672432632365156167627 enc = 281514135280131449141829505417513079250325933715045609473648447005814096770465720188289516151363972033489725088974133391622010638491163251851962623645431655330200732754796040933303093820956529388384535167167317814353993583657429669275504208675670077899340221038968938928780460438883730711177453290473326764507911871504 phin = (q-1)*(p-1) d = gmpy2.invert(e, phin) flag = pow(enc, d, n) flag = long_to_bytes(flag) print(flag)
zh3r0{RSA_1s_Fun}
Misc
Welcome to Phase 1
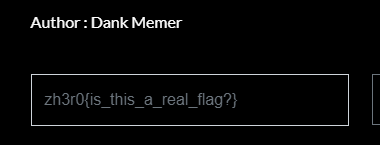
zh3r0{is_this_a_real_flag?}
Reverse
snakes everywhere
Python 字节码的题,不过相较于上次虎符要简单很多,还是可以利用dis.dis对照翻译,找到关键处的字节码。
23 216 LOAD_NAME 8 (ciphertext) 218 LOAD_NAME 7 (xor) 220 LOAD_NAME 4 (key) 222 LOAD_NAME 10 (i) 224 LOAD_CONST 10 (16) 226 BINARY_MODULO 228 BINARY_SUBSCR 230 LOAD_NAME 2 (flag) 232 LOAD_NAME 10 (i) 234 BINARY_SUBSCR 236 CALL_FUNCTION 2 238 INPLACE_ADD 240 STORE_NAME 8 (ciphertext) 242 JUMP_ABSOLUTE 212
翻译为对应的python代码就是
for i in range(16): ciphertext[i] = ciphertext[i] ^ key[i]
最后将ciphertext写入到snake中,因此只需要反向解密就行
key = "I_l0v3_r3v3r51ng" flag = '' enc = '' with open(r'C:\Users\10245\Desktop\snake.txt','r', encoding="utf-8") as f: enc = f.read() print (enc) for i in range(len(enc)): flag += chr(ord(enc[i]) ^ ord(key[i%len(key)])) print (flag)
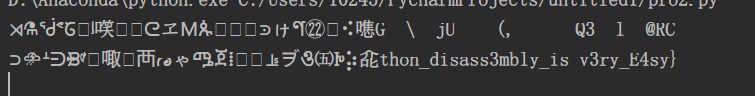
合理猜测,得到flag
zh3r0{Python_disass3mbly_is v3ry_E4sy}



