攻防世界--simple-check-100
测试文件:https://adworld.xctf.org.cn/media/task/attachments/2543a3658d254c30a89e4ea7b8950c27.zip
这道题很坑了,exe文件研究了半天。
1.准备
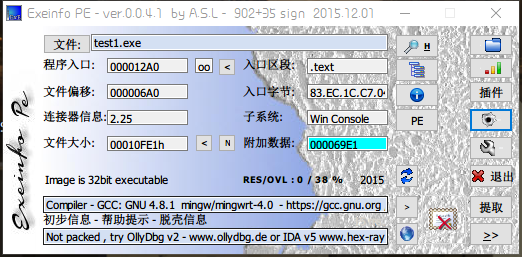
获得信息
- 32位文件
2.IDA打开
用IDA看了三个文件,都差不多。
1 int __cdecl main(int argc, const char **argv, const char **envp) 2 { 3 void *v3; // esp 4 void *v4; // esp 5 char *v6; // [esp+4h] [ebp-44h] 6 char v7; // [esp+8h] [ebp-40h] 7 char v8; // [esp+1Bh] [ebp-2Dh] 8 char *v9; // [esp+1Ch] [ebp-2Ch] 9 int v10; // [esp+20h] [ebp-28h] 10 char v11; // [esp+25h] [ebp-23h] 11 char v12; // [esp+26h] [ebp-22h] 12 char v13; // [esp+27h] [ebp-21h] 13 char v14; // [esp+28h] [ebp-20h] 14 char v15; // [esp+29h] [ebp-1Fh] 15 char v16; // [esp+2Ah] [ebp-1Eh] 16 char v17; // [esp+2Bh] [ebp-1Dh] 17 char v18; // [esp+2Ch] [ebp-1Ch] 18 char v19; // [esp+2Dh] [ebp-1Bh] 19 char v20; // [esp+2Eh] [ebp-1Ah] 20 char v21; // [esp+2Fh] [ebp-19h] 21 char v22; // [esp+30h] [ebp-18h] 22 char v23; // [esp+31h] [ebp-17h] 23 char v24; // [esp+32h] [ebp-16h] 24 char v25; // [esp+33h] [ebp-15h] 25 char v26; // [esp+34h] [ebp-14h] 26 char v27; // [esp+35h] [ebp-13h] 27 char v28; // [esp+36h] [ebp-12h] 28 char v29; // [esp+37h] [ebp-11h] 29 char v30; // [esp+38h] [ebp-10h] 30 char v31; // [esp+39h] [ebp-Fh] 31 char v32; // [esp+3Ah] [ebp-Eh] 32 char v33; // [esp+3Bh] [ebp-Dh] 33 char v34; // [esp+3Ch] [ebp-Ch] 34 char v35; // [esp+3Dh] [ebp-Bh] 35 char v36; // [esp+3Eh] [ebp-Ah] 36 char v37; // [esp+3Fh] [ebp-9h] 37 int *v38; // [esp+40h] [ebp-8h] 38 39 v38 = &argc; 40 __main(); 41 v8 = 'T'; 42 v37 = -56; 43 v36 = 126; 44 v35 = -29; 45 v34 = 100; 46 v33 = -57; 47 v32 = 22; 48 v31 = -102; 49 v30 = -51; 50 v29 = 17; 51 v28 = 101; 52 v27 = 50; 53 v26 = 45; 54 v25 = -29; 55 v24 = -45; 56 v23 = 67; 57 v22 = -110; 58 v21 = -87; 59 v20 = -99; 60 v19 = -46; 61 v18 = -26; 62 v17 = 109; 63 v16 = 44; 64 v15 = -45; 65 v14 = -74; 66 v13 = -67; 67 v12 = -2; 68 v11 = 106; 69 v10 = 19; 70 v3 = alloca(32); 71 v4 = alloca(32); 72 v9 = &v7; 73 printf("Key: "); 74 v6 = v9; 75 scanf("%s", v9); 76 if ( check_key((int)v9) ) 77 interesting_function((int)&v8); 78 else 79 puts("Wrong"); 80 return 0; 81 }
3.代码分析
很明显只要绕过第76行代码,我们就能够获取我们需要的flag,而且v8还是已知的,
3.1 GDB调试
将Linux下的那个文件放入Linux调试。
task9_x86_64_46d01fe312d35ecf69c4ff8ab8ace75d080891dc
命令:
gdb
file task9_x86_64_46d01fe312d35ecf69c4ff8ab8ace75d080891dc
b main
r
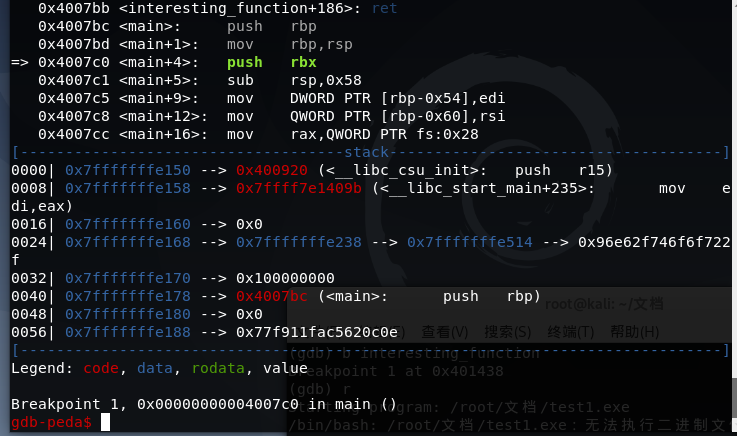
然后一直执行命令next,运行到check_key函数处
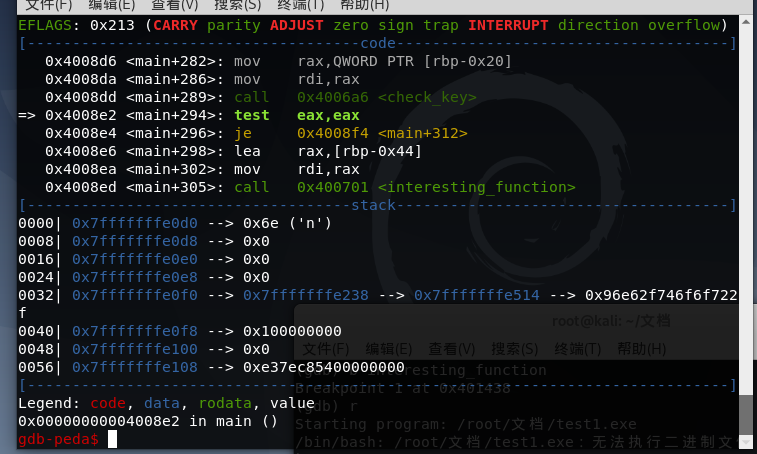
3.2 跳过check_key
把test eax,eax改为真就行,也就是把eax改为1。
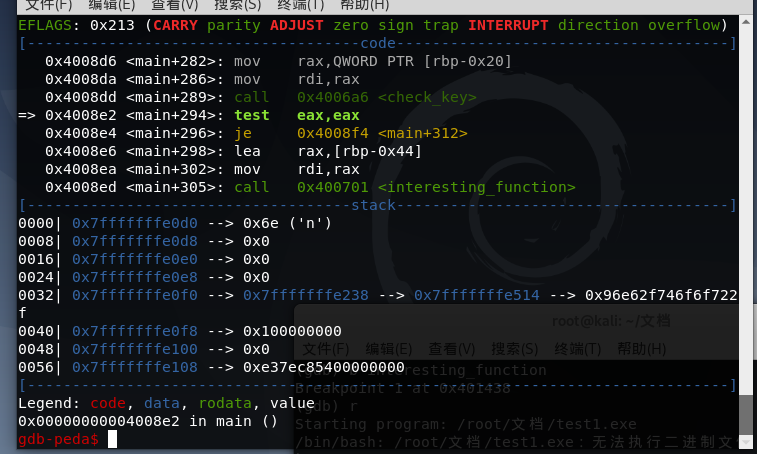
修改eax
set $eax=1
一直执行
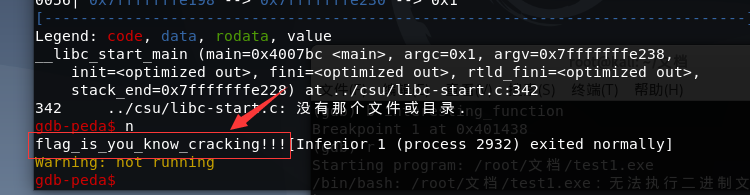
4.get flag!
flag_is_you_know_cracking!!!



