攻防世界--getit
测试文件:https://adworld.xctf.org.cn/media/task/attachments/8ef2f7ef55c240418f84b3c514a7a28a
准备
得知
- 64位文件
2.IDA打开
反编译得到C语言代码
1 int __cdecl main(int argc, const char **argv, const char **envp) 2 { 3 char v3; // al 4 __int64 v5; // [rsp+0h] [rbp-40h] 5 int i; // [rsp+4h] [rbp-3Ch] 6 FILE *stream; // [rsp+8h] [rbp-38h] 7 char filename[8]; // [rsp+10h] [rbp-30h] 8 unsigned __int64 v9; // [rsp+28h] [rbp-18h] 9 10 v9 = __readfsqword(0x28u); 11 LODWORD(v5) = 0; 12 while ( (signed int)v5 < strlen(s) ) 13 { 14 if ( v5 & 1 ) 15 v3 = 1; 16 else 17 v3 = -1; 18 *(&t + (signed int)v5 + 10) = s[(signed int)v5] + v3; 19 LODWORD(v5) = v5 + 1; 20 } 21 strcpy(filename, "/tmp/flag.txt"); 22 stream = fopen(filename, "w"); 23 fprintf(stream, "%s\n", u, v5); 24 for ( i = 0; i < strlen(&t); ++i ) 25 { 26 fseek(stream, p[i], 0); 27 fputc(*(&t + p[i]), stream); 28 fseek(stream, 0LL, 0); 29 fprintf(stream, "%s\n", u); 30 } 31 fclose(stream); 32 remove(filename); 33 return 0; 34 }
2.1 常量参数值
接着其中一些参数的值
.data:00000000006010A0 public s .data:00000000006010A0 ; char s[] .data:00000000006010A0 s db 'c61b68366edeb7bdce3c6820314b7498',0 .data:00000000006010A0 ; DATA XREF: main+25↑o .data:00000000006010A0 ; main+3F↑r .data:00000000006010C1 align 20h .data:00000000006010E0 public t .data:00000000006010E0 ; char t .data:00000000006010E0 t db 53h ; DATA XREF: main+65↑w .data:00000000006010E0 ; main+C9↑o ... .data:00000000006010E1 aHarifctf db 'harifCTF{????????????????????????????????}',0 .data:000000000060110C align 20h .data:0000000000601120 public u .data:0000000000601120 u db '*******************************************',0 .data:0000000000601120 ; DATA XREF: main+A5↑o .data:0000000000601120 ; main+13F↑o .data:000000000060114C align 20h .data:0000000000601160 public p .data:0000000000601160 ; int p[43] .data:0000000000601160 p dd 1Eh ; DATA XREF: main+E1↑r .data:0000000000601160 ; main+104↑r
其中值得我们注意的是t的值,t的值应该是0x53+'harifCTF{????????????????????????????????}',即
SharifCTF{????????????????????????????????}
t很有可能是储存flag的数组。
2.2 代码分析
代码整体上可以分为3个部分
1~11 变量定义初始化
12~20 定义flag值
20~34 flag值写入文件
因此我们只需要将第二部分复现,输出flag即可。
2.3 flag获取代码
#include <stdio.h> #include <stdlib.h> #include <Windows.h> #pragma warning(disable:4996) int main(void) { char v3; __int64 v5; char s[] = "c61b68366edeb7bdce3c6820314b7498"; char t[] = "SharifCTF{????????????????????????????????}"; v5 = 0; while (v5 < strlen(s)) { if (v5 & 1) v3 = 1; else v3 = -1; *(t + v5 + 10) = s[v5] + v3; v5++; } printf("%s", t); system("PAUSE"); return 0; }
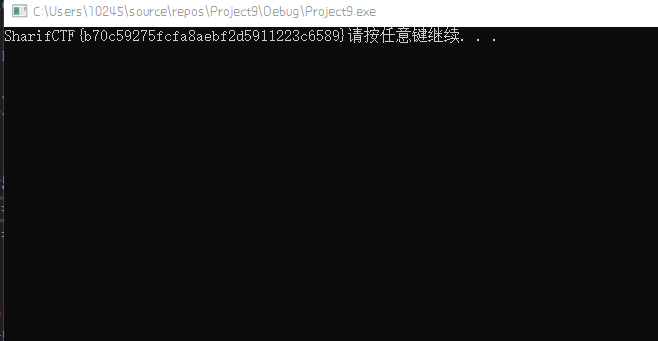
3. get flag!
SharifCTF{b70c59275fcfa8aebf2d5911223c6589}



