“古剑山”初赛Misc 幸运饼干
“古剑山”初赛Misc 幸运饼干
考点:Chrome的Cookies解密
赛中思路
bandzip极限压缩hint.jpg后打明文攻击
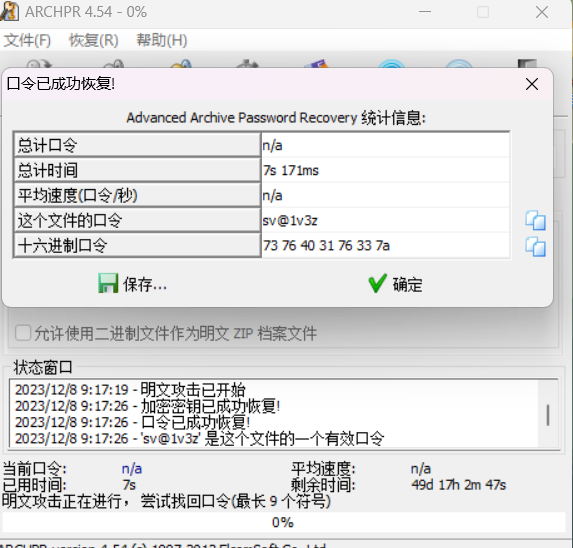
压缩包密码:sv@1v3z
┌──(root💀kali)-[~/桌面]
└─# file Cookies
Cookies: SQLite 3.x database, last written using SQLite version 3030001
SQLite3连接查询
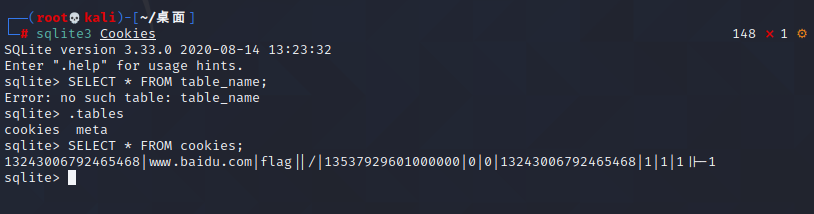
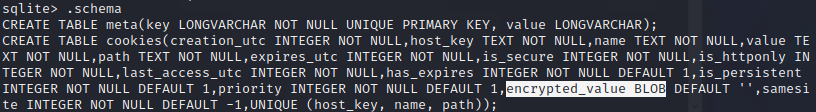
导出encrypted_value BLOB
from os import getenv
import sqlite3
import binascii
conn = sqlite3.connect("Cookies")
cursor = conn.cursor()
cursor.execute('select encrypted_value BLOB from cookies') # 导出encrypted_value BLOB字段
for result in cursor.fetchall():
print(result)
print (binascii.b2a_hex(result[0]))
f = open('save.txt', 'wb') # 保存为save.txt
f.write(result[0])
f.close()
admin.txt是mimikatz运行结果,密码没爆出来,只有ntlm
NTLM : 786515ed10d6b79e74c1739f72a158cc
hashcat爆破
hashcat.exe -m 1000 -a 0 786515ed10d6b79e74c1739f72a158cc .\demo\rockyou.txt

得到密码54231
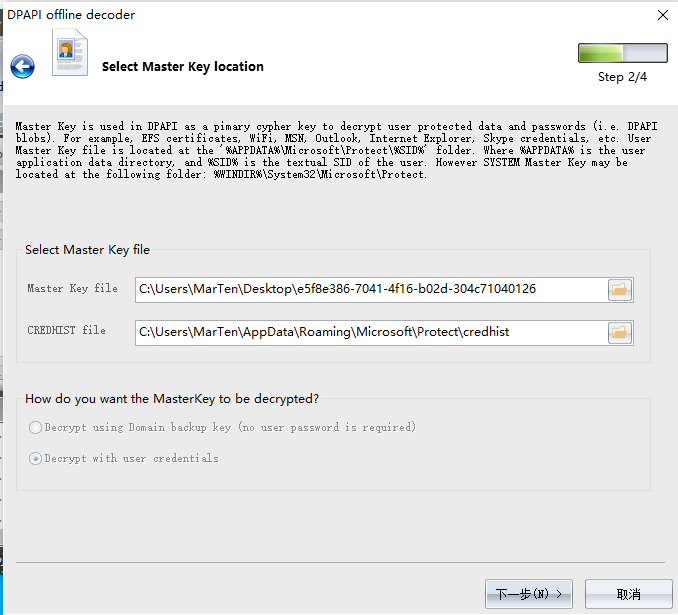
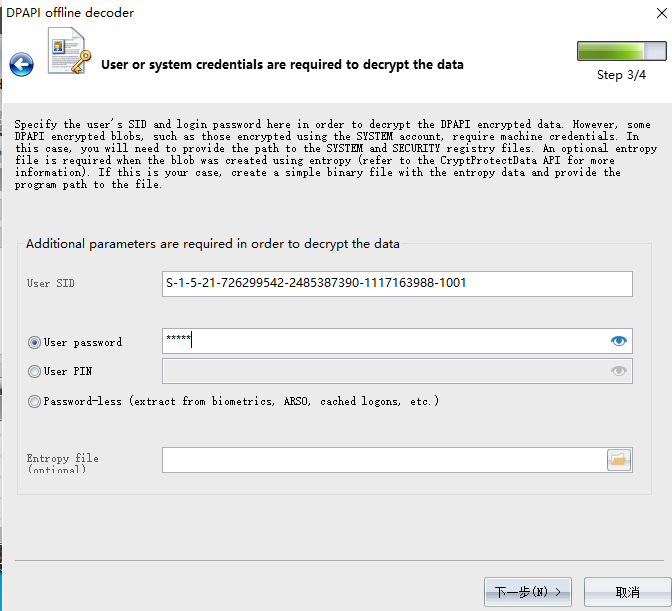
S-1-5-21-726299542-2485387390-1117163988-1001是Master Key file
User SID是S-1-5-21-726299542-2485387390-1117163988-1001
用Windows Password Recovery恢复,选择Utils->DPAPI Decoder and Analyser->Decrypt DPAPI data blob
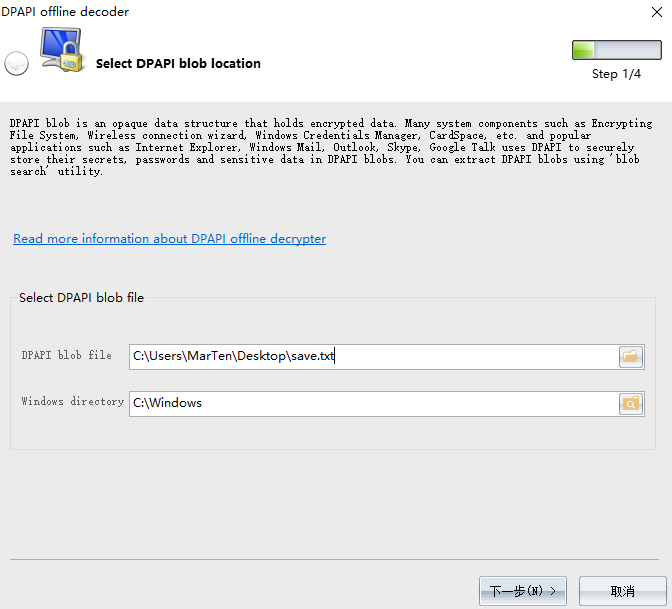
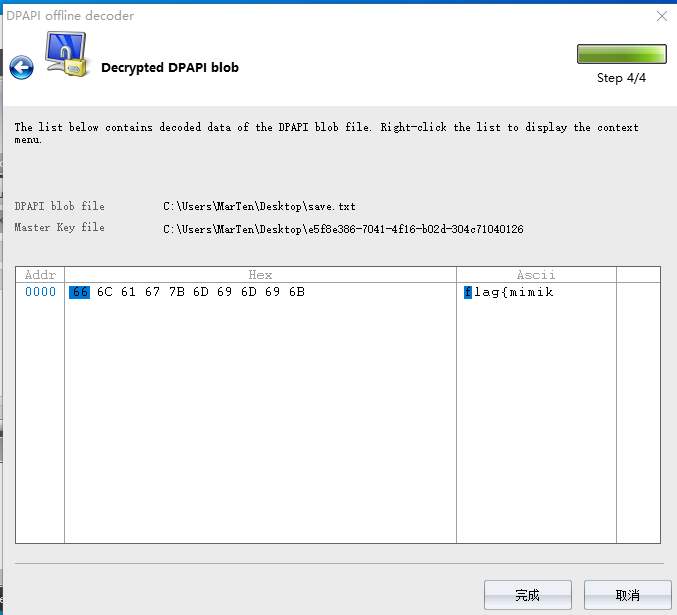
得到前半段flag:flag{mimik
参考文章:
https://blog.csdn.net/qq_38154820/article/details/106330148
https://blog.csdn.net/Onlyone_1314/article/details/113848990
赛中就到这为止,赛后在jiaqiniu、Z3n1th师傅帮助下成功复现
复盘
其实不用这么麻烦,重新整理一下思路
在明文攻击之后,现已知的数据有
Master Key file:S-1-5-21-726299542-2485387390-1117163988-1001
User SID:S-1-5-21-726299542-2485387390-1117163988-1001
NTLM: 786515ed10d6b79e74c1739f72a158cc
首先肯定是对NTLM解密得到password,这里直接用在线网站: Ntlm Decrypt & Encrypt Online
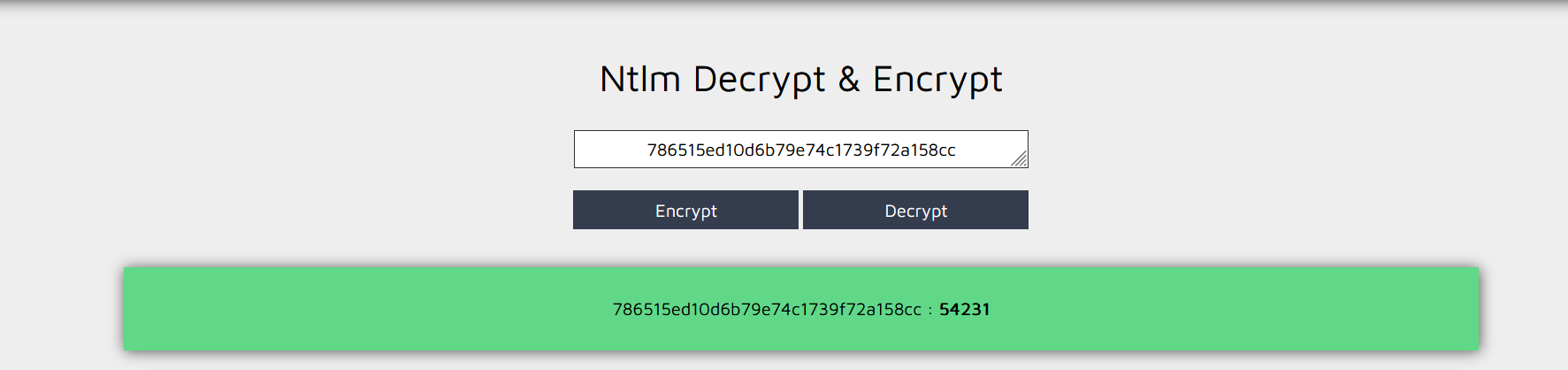
得到password:54231
解题点是对Cookies的解密,那么综上的各个信息可以利用mimikatz破解
第一步:得到masterkey,即MimiKatz读取 DPAPI 加密密钥
Master Key:
64字节,用于解密DPAPI blob,使用用户登录密码、SID和16字节随机数加密后保存在Master Key file中
Master Key file:
二进制文件,可使用用户登录密码对其解密,获得Master Key
D:\forensics\mimikatz\x64>mimikatz.exe
.#####. mimikatz 2.2.0 (x64) #18362 Feb 29 2020 11:13:36
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > http://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > http://pingcastle.com / http://mysmartlogon.com ***/
mimikatz # dpapi::masterkey /in:.\demo\e5f8e386-7041-4f16-b02d-304c71040126 /sid:S-1-5-21-726299542-2485387390-1117163988-1001 /password:54231 /protected
**MASTERKEYS**
dwVersion : 00000002 - 2
szGuid : {e5f8e386-7041-4f16-b02d-304c71040126}
dwFlags : 00000005 - 5
dwMasterKeyLen : 000000b0 - 176
dwBackupKeyLen : 00000090 - 144
dwCredHistLen : 00000014 - 20
dwDomainKeyLen : 00000000 - 0
[masterkey]
**MASTERKEY**
dwVersion : 00000002 - 2
salt : 878dd8440a0e80ff0ecfcc13da57d1ec
rounds : 00001f40 - 8000
algHash : 0000800e - 32782 (CALG_SHA_512)
algCrypt : 00006610 - 26128 (CALG_AES_256)
pbKey : a5fbc1213adb93e582b8cc53aaa107798e15041a497e644b2ef630f72855990d3f4cca62e967d80679e9903e64aaee91e82656b179dbbb25ff809f52b0b08a6458ba1337820ef34b0107ffc03a1481d26f5d627aa1607a17833f6fdf801c818f184fd7461bdd64e55c2d7844ee87f610945377c032d8334c82a780a5f253d65d9daa10d1096e1de44f81d440d8b5b5a4
[backupkey]
**MASTERKEY**
dwVersion : 00000002 - 2
salt : 8ff5a6cd081af8648c2d286a5818d26b
rounds : 00001f40 - 8000
algHash : 0000800e - 32782 (CALG_SHA_512)
algCrypt : 00006610 - 26128 (CALG_AES_256)
pbKey : e47dedb2912cf83ce3683410ea6d95bc4b19440840ef1398e4232dd62a7d0c6b5690e56ed2a33d8e872018574bf74789f4528a0463eeb322b0dc3b36ff855c207dd4392b7a0df71087b5eaba379aeb93fb635d1e589660c08c09d3abd1c4fa4d4db2e805e52621081629d9e6a8acd741
[credhist]
**CREDHIST INFO**
dwVersion : 00000003 - 3
guid : {70a2dbe6-bd4e-407b-86e1-744f01fb3833}
[masterkey] with password: 54231 (protected user)
key : 7a4d2ffbb42d0a1ab46f0351260aef16cae699e03e9d6514b3bf10e2977c5d228fda4a48e39b7b8a06a443c39653c2a3c3656596e7edc84e1c9682511c8343ac
sha1: 0da593d6efa52b90e548a703de74359cf355703a
成功得到masterkey,下一步是用masterkey解密Chrome的Cookies
mimikatz # dpapi::chrome /in:./demo/Cookies /masterkey: 7a4d2ffbb42d0a1ab46f0351260aef16cae699e03e9d6514b3bf10e2977c5d228fda4a48e39b7b8a06a443c39653c2a3c3656596e7edc84e1c9682511c8343ac
Host : www.baidu.com ( / )
Name : flag
Dates : 2020/8/27 20:59:52 -> 2030/1/1 8:00:01
* volatile cache: GUID:{e5f8e386-7041-4f16-b02d-304c71040126};KeyHash:0da593d6efa52b90e548a703de74359cf355703a
Cookie: flag{mimikatz_is_bravo_cvuwjr}
得到flag
参考文章:
https://www.cnblogs.com/-zhong/p/15744408.html
https://xz.aliyun.com/t/9810#


 浙公网安备 33010602011771号
浙公网安备 33010602011771号