no-strings-attached writeup
no-strings-attach writeup
1、程序分析

主函数如图所示,关键函数在authenticate中,进入函数。

分析可得,decrypt代码段为关键代码段,进入关键函数decrypt。
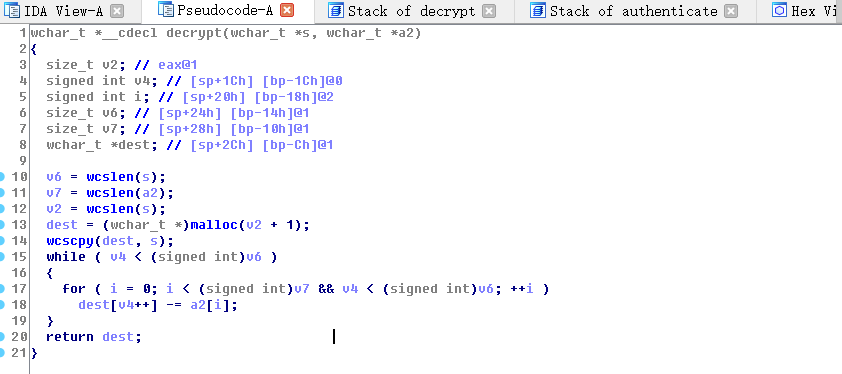
2、解题脚本
可以看到,des指针指向地址处存放的值应该就是flag了,直接静态分析应该可以得到,但是会比较吃力,这时候,我们可以打开gdb,查看一下对应内存处的值。

断点设在add esp,0x34处。
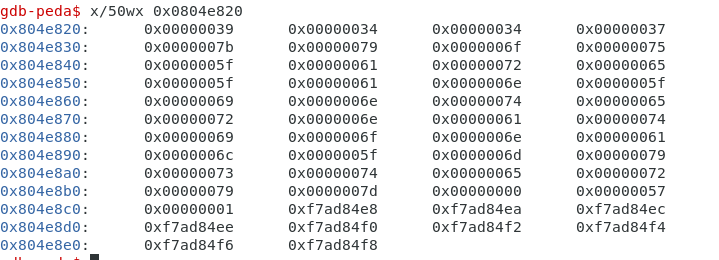
查看内存地址处的值,提取出来,写一个简单脚本跑一下。
ls=[0x39,0x34,0x34,0x37,0x7b,0x79,0x6f,0x75,0x5f, 0x61,0x72,0x65,0x5f,0x61,0x6e,0x5f,0x69,0x6e, 0x74,0x65,0x72,0x6e,0x61,0x74,0x69,0x6f,0x6e, 0x61,0x6c,0x5f,0x6d,0x79,0x73,0x74,0x65,0x72, 0x79,0x7d,0x0,0x57,0x1] flag="" for a in ls: flag+=chr(a) print(flag)




