[GXYCTF2019]gakki
[GXYCTF2019]gakki
下载下来是一张图片,7zip打开可以直接看到后面有隐写图片
直接用foremost分离
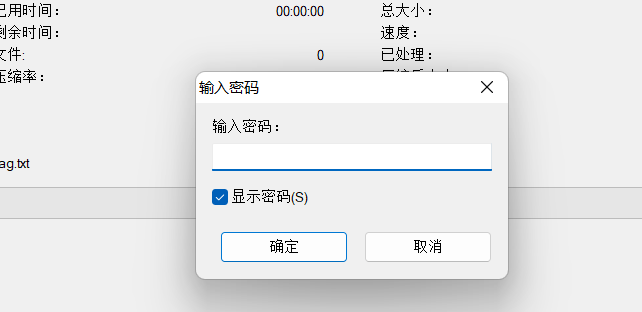
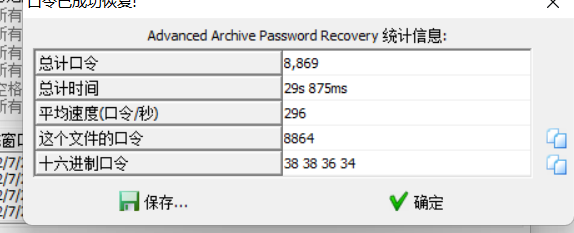
rar文件有密码,直接用archpr爆破出密码
解密之后,发现文件里面有很长的字符串,这里有一种思路,就是统计里面出现的字符个数,根据出现的次数排列就可以获得flag
alphabet = "abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ1234567890!@#$%^&*()_+- =\\{\\}[]"
strings = open('flag.txt').read()
result = {}
for i in alphabet:
counts = strings.count(i)
i = '{0}'.format(i)
result[i] = counts
res = sorted(result.items(),key=lambda item:item[1],reverse=True)
for data in res:
print(data)
for i in res:
flag = str(i[0])
print(flag[0],end="")
运行结果:
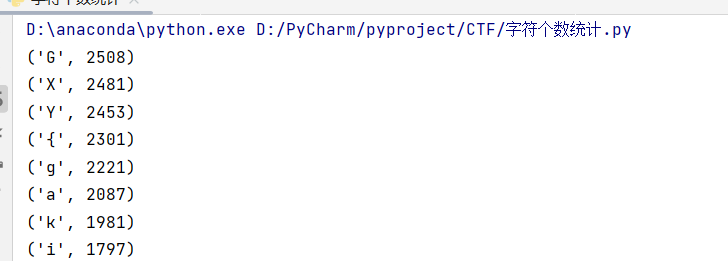
然后直接手打这些flag就行,把前缀改成flag
flag{gaki_IsMyw1fe}


