fscan内网资产扫描并输出报告
fscan内网资产扫描并输出报告
fscan介绍
一款内网综合扫描工具,方便一键自动化、全方位漏扫扫描。
支持主机存活探测、端口扫描、常见服务的爆破、ms17010、redis批量写公钥、计划任务反弹shell、读取win网卡信息、web指纹识别、web漏洞扫描、netbios探测、域控识别等功能。
fscan开源,github上游详细的说明,详见:https://github.com/shadow1ng/fscan
使用说明(Linux)
- 指定单个IP
./fscan -h 192.168.160.1
- 指定网段
./fscan -h 192.168.75.0/24
- 将扫描结果保存到指定文件(默认保存到:result.txt)
./fscan -h 192.168.75.0/24 -o 192-168-75-0-24.txt
- 扫描结果样例
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.4
start infoscan
192.168.160.1:8089 open
192.168.160.1:9000 open
192.168.160.1:22 open
192.168.160.1:80 open
192.168.160.1:8008 open
192.168.160.1:3306 open
192.168.160.1:9001 open
192.168.160.1:8012 open
192.168.160.1:8443 open
192.168.160.1:8083 open
[*] alive ports len is: 10
start vulscan
[*] WebTitle http://192.168.160.1 code:307 len:61 title:None 跳转url: http://192.168.22.68:9001
[*] WebTitle http://192.168.160.1:9000 code:307 len:61 title:None 跳转url: http://192.168.160.1:9001
[*] WebTitle http://192.168.22.68:9001 code:200 len:1310 title:MinIO Console
[*] WebTitle http://192.168.160.1:9001 code:200 len:1310 title:MinIO Console
[*] WebTitle http://192.168.160.1:8089 code:403 len:555 title:403 Forbidden
[*] WebTitle http://192.168.160.1:8012 code:302 len:0 title:None 跳转url: http://192.168.160.1:8012/index
[*] WebTitle http://192.168.160.1:8012/index code:200 len:12409 title:kkFileView演示首页
[*] WebTitle http://192.168.160.1:9001 code:200 len:1310 title:MinIO Console
[*] WebTitle https://192.168.160.1:8083 code:502 len:559 title:502 Bad Gateway
[*] WebTitle https://192.168.160.1:8443 code:404 len:232 title:404 Not Found
[*] WebTitle http://192.168.160.1:8008 code:404 len:232 title:404 Not Found
[+] SSH 192.168.12.20:22:root root
[+] SSH 192.168.12.19:22:root root
[+] SSH 192.168.12.18:22:root root
[+] PocScan https://192.168.69.58:8443 poc-yaml-springboot-cve-2021-21234 spring3
[+] PocScan https://192.168.69.61:8443 poc-yaml-springboot-cve-2021-21234 spring3
[+] PocScan http://192.168.69.58:18000 poc-yaml-springboot-cve-2021-21234 spring3
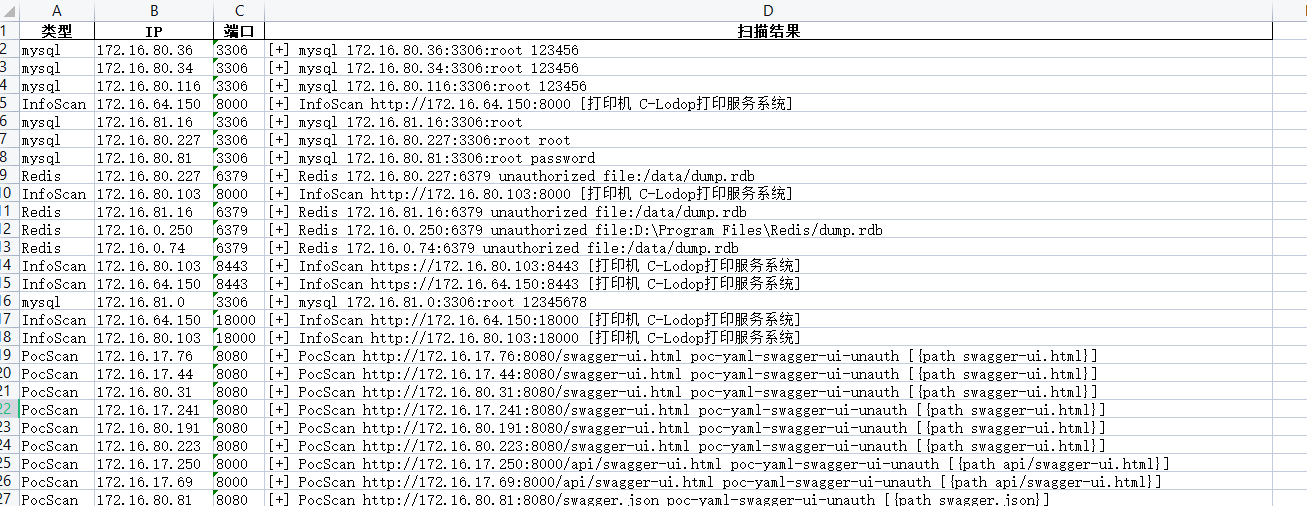
输出报告
可以看出来,fscan扫出来的内容包含很多描述性的INFO级别日志,如何提取出主要信息并输出报告。
可以结合Python + Pandas的形式利用正则表达式提取出主要信息再通过Pandas导出Excel。
- 首先要有Python3.5+的Python环境
- 安装pandas
pip install pandas
- 代码部分
#!/usr/bin/env python
# -*- coding:utf-8 -*-
# @Time:2024/6/27 14:35
# @Software:PyCharm
__author__ = "JentZhang"
import re
import pandas
def extract_info(text):
# 匹配SSH类型的文本
pattern = re.compile(r'\[\+\] (.+) (http://|https://)?([0-9]{1,3}\.[0-9]{1,3}\.[0-9]{1,3}\.[0-9]{1,3})(:(\d+))?.*')
match = pattern.search(text)
if match:
return {
'类型': match.group(1),
'IP': match.group(3),
'端口': match.group(5)
}
return None
def extract_lines(filepath, start_msg='[+]'):
"""
抽取扫描结果中的指定行
:param filepath:
:param start_msg:
:return:
"""
matching_lines = []
with open(filepath, 'r', encoding='utf-8') as file:
for line in file:
if line.startswith(start_msg):
matching_lines.append(line.strip())
return matching_lines
def export_to_excel(data, filename):
"""
导出数据到excel
:param data:
:param filename:
:return:
"""
df = pandas.DataFrame(data)
df.to_excel(f"{filename}资产测绘.xlsx", index=False)
def analysis_data(file_data):
"""
分析扫描的文件数据
:param file_data:
:return:
"""
res = []
for i in file_data:
# print(f"before: {i}")
info = extract_info(i)
if info:
info["扫描结果"] = i
res.append(info)
# print(f"after: {info}")
return res
if __name__ == '__main__':
# files = ["10_139_0_0_23.txt", "10_139_162_0_23.txt", "10_139_176_0_21.txt"]
files = ["172_16_0_0_16.txt"]
for file in files: # 循环便利扫描的结果文件,分析出结果并导出Excel
d = extract_lines(file)
export_to_excel(analysis_data(d), file.split(".")[0])
- 报告样式
好记性不如烂笔头!


