Web API 2 使用SSL
在Server上启用SSL
稍后我会想在IIS 7 上配置SSL,现在先往下看。
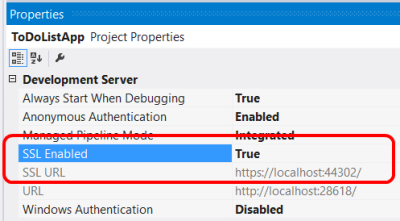
本地测试,您可以启用SSL的IIS Express Visual Studio。在属性窗口中,启用SSL设置为True。注意SSL URL的值,使用这个URL用于测试HTTPS连接。
执行SSL在Web API控制器
如果你有一个HTTPS和HTTP绑定,客户仍然可以使用HTTP访问网站。你可能会允许一些资源可以通过HTTP,而其他资源需要SSL。在这种情况下,使用一个操作过滤器需要SSL对受保护的资源。下面的代码显示了一个Web API检查SSL身份验证过滤器:
public class RequireHttpsAttribute : AuthorizationFilterAttribute
{
public override void OnAuthorization(HttpActionContext actionContext)
{
if (actionContext.Request.RequestUri.Scheme != Uri.UriSchemeHttps)
{
actionContext.Response = new HttpResponseMessage(System.Net.HttpStatusCode.Forbidden)
{
ReasonPhrase = "HTTPS Required"
};
}
else
{
base.OnAuthorization(actionContext);
}
}
}
这个过滤器添加到任何Web API需要SSL的操作:
public class ValuesController : ApiController
{
[RequireHttps]
public HttpResponseMessage Get() { ... }
}
SSL客户端证书
SSL提供了通过使用公钥基础设施证书身份验证。服务器必须提供一个服务器给客户端进行身份验证的证书。是不太常见的客户端提供一个证书服务器,但这是一个选择的对客户进行身份验证。使用客户端证书的SSL,您需要一种方法来签名证书分发给你的用户。对于许多应用程序类型,这不会是一个很好的用户体验,但在某些环境中(例如,企业)可能是可行的。
| 优势 | 劣势 |
|---|---|
| ——证书凭据比用户名/密码。SSL提供了一个完整的安全通道,与认证、消息完整性和消息加密。 | ——你必须获取和管理PKI证书。——客户机平台必须支持SSL客户端证书。 |
配置IIS接受客户端证书,打开IIS管理器和执行以下步骤:
- Click the site node in the tree view.
- Double-click the SSL Settings feature in the middle pane.
-
Under Client Certificates, select one of these options:
- Accept: IIS will accept a certificate from the client, but does not require one.
- Require: Require a client certificate. (To enable this option, you must also select "Require SSL")
你也可以设置这些选项ApplicationHost.config文件:
<system.webServer>
<security>
<access sslFlags="Ssl, SslNegotiateCert" />
<!-- To require a client cert: -->
<!-- <access sslFlags="Ssl, SslRequireCert" /> -->
</security>
</system.webServer>
The SslNegotiateCert flag means IIS will accept a certificate from the client, but does not require one (equivalent to the "Accept" option in IIS Manager). To require a certificate, set the SslRequireCert flag. For testing, you can also set these options in IIS Express, in the local applicationhost.Config file, located in "Documents\IISExpress\config".
为了测试创建一个客户端证书
For testing purposes, you can use MakeCert.exe to create a client certificate. First, create a test root authority:
makecert.exe -n "CN=Development CA" -r -sv TempCA.pvk TempCA.cer
Makecert will prompt you to enter a password for the private key.
Next, add the certificate to the test server's "Trusted Root Certification Authorities" store, as follows:
- Open MMC.
- Under File, select Add/Remove Snap-In.
- Select Computer Account.
- Select Local computer and complete the wizard.
- Under the navigation pane, expand the "Trusted Root Certification Authorities" node.
- On the Action menu, point to All Tasks, and then click Import to start the Certificate Import Wizard.
- Browse to the certificate file, TempCA.cer.
- Click Open, then click Next and complete the wizard. (You will be prompted to re-enter the password.)
Now create a client certificate that is signed by the first certificate:
makecert.exe -pe -ss My -sr CurrentUser -a sha1 -sky exchange -n "CN=name"
-eku 1.3.6.1.5.5.7.3.2 -sk SignedByCA -ic TempCA.cer -iv TempCA.pvk
在Web API中使用客户端证书
On the server side, you can get the client certificate by calling GetClientCertificate on the request message. The method returns null if there is no client certificate. Otherwise, it returns an X509Certificate2 instance. Use this object to get information from the certificate, such as the issuer and subject. Then you can use this information for authentication and/or authorization.
X509Certificate2 cert = Request.GetClientCertificate();
string issuer = cert.Issuer;
string subject = cert.Subject;


 浙公网安备 33010602011771号
浙公网安备 33010602011771号