OpenStack实例noVNC URL获取
Compute API地址获取
登录OpenStack Dashborad,选择项目下的访问API:
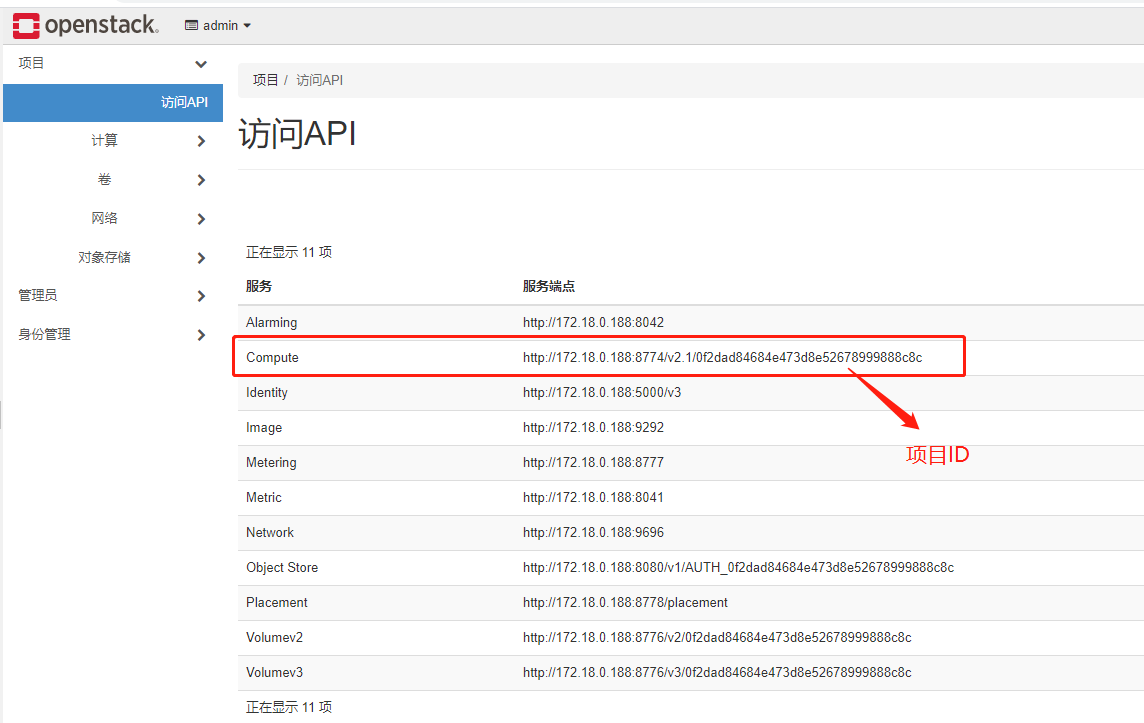
Server Consoles
Manage server consoles.
POST /servers/{server_id}/remote-consoles
Create Console
Microversion 2.6 or greater is required for this API.
The API provides a unified request for creating a remote console. The user can get a URL to connect the console from this API. The URL includes the token which is used to get permission to access the console. Servers may support different console protocols. To return a remote console using a specific protocol, such as RDP, set the protocol parameter to rdp.
Normal response codes: 200
Error response codes: badRequest(400), unauthorized(401), forbidden(403), itemNotFound(404), conflict(409), notImplemented(501)
Request
|
Name
|
In
|
Type
|
Description
|
|---|---|---|---|
| server_id | path | string | The UUID of the server. |
| remote_console | body | object | The remote console object. |
| protocol | body | string |
The protocol of remote console. The valid values are The protocol |
| type | body | string | The type of remote console. The valid values are novnc, rdp-html5, spice-html5, serial, and webmks. The type webmks is added since Microversion 2.8. |
|
X-Auth-Token |
header |
String |
token(生成token接口说明) |
|
X-OpenStack-Nova-API-Version |
header |
String |
microversion request header |
|
OpenStack-API-Version |
header |
String |
microversion request header |
Example Get Remote VNC Console
{
"remote_console": {
"protocol": "vnc",
"type": "novnc"
}
}
Response
|
Name
|
In
|
Type
|
Description
|
|---|---|---|---|
| remote_console | body | object | The remote console object. |
| protocol | body | string |
The protocol of remote console. The valid values are |
| type | body | string | The type of remote console. The valid values are novnc, rdp-html5, spice-html5, serial, and webmks. The type webmks is added since Microversion 2.8. |
| url | body | string | The URL is used to connect the console. |
2.生成token接口说明
接口链接:https://docs.openstack.org/api-ref/identity/v3/index.html?expanded=password-authentication-with-scoped-authorization-detail#password-authentication-with-scoped-authorization
Identity API地址获取
登录OpenStack Dashborad,选择项目下的访问API:
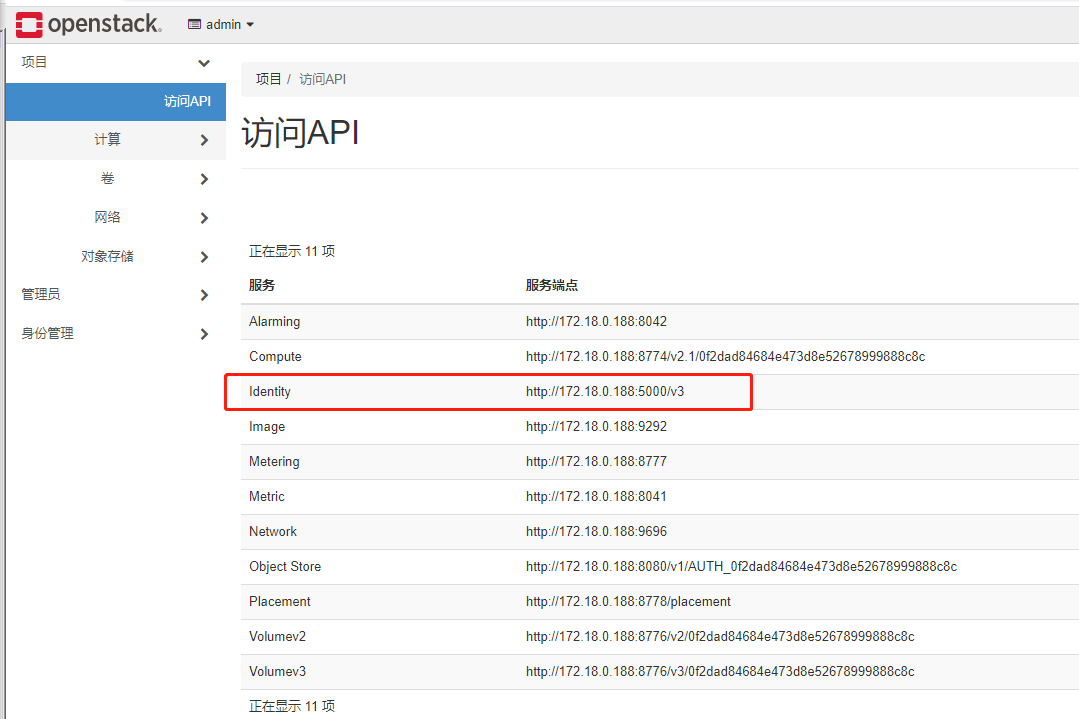
Authentication and token management
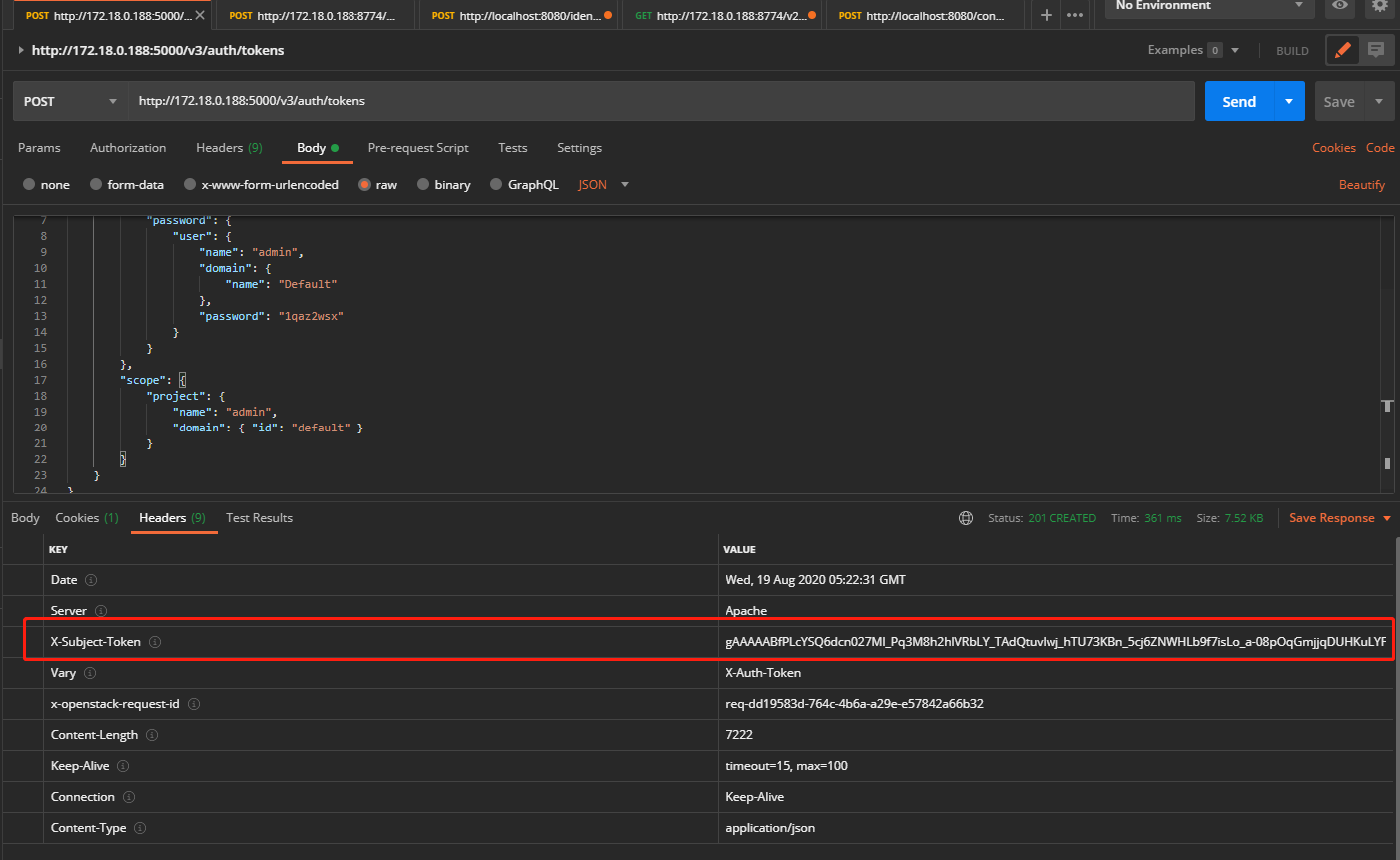
1.Tokens have IDs, which the Identity API returns in the
X-Subject-Tokenresponse header.(样例)2.After you obtain an authentication token, you can:
Make REST API requests to other OpenStack services. You supply the ID of your authentication token in the
X-Auth-Tokenrequest header.(样例)Validate your authentication token and list the domains, projects, roles, and endpoints that your token gives you access to.
Use your token to request another token scoped for a different domain and project.
Force the immediate revocation of a token.
List revoked public key infrastructure (PKI) tokens.
Authentication errors
|
Response code |
Description |
|
|
The Identity service failed to parse the request as expected. One of the following errors occurred:
|
|
|
One of the following errors occurred:
|
|
|
The identity was successfully authenticated but it is not authorized to perform the requested action. |
|
|
An operation failed because a referenced entity cannot be found by ID. For a POST request, the referenced entity might be specified in the request body rather than in the resource path. |
|
|
A POST or PATCH operation failed. For example, a client tried to update a unique attribute for an entity, which conflicts with that of another entity in the same collection. Or, a client issued a create operation twice on a collection with a user-defined, unique attribute. For example, a client made a POST |
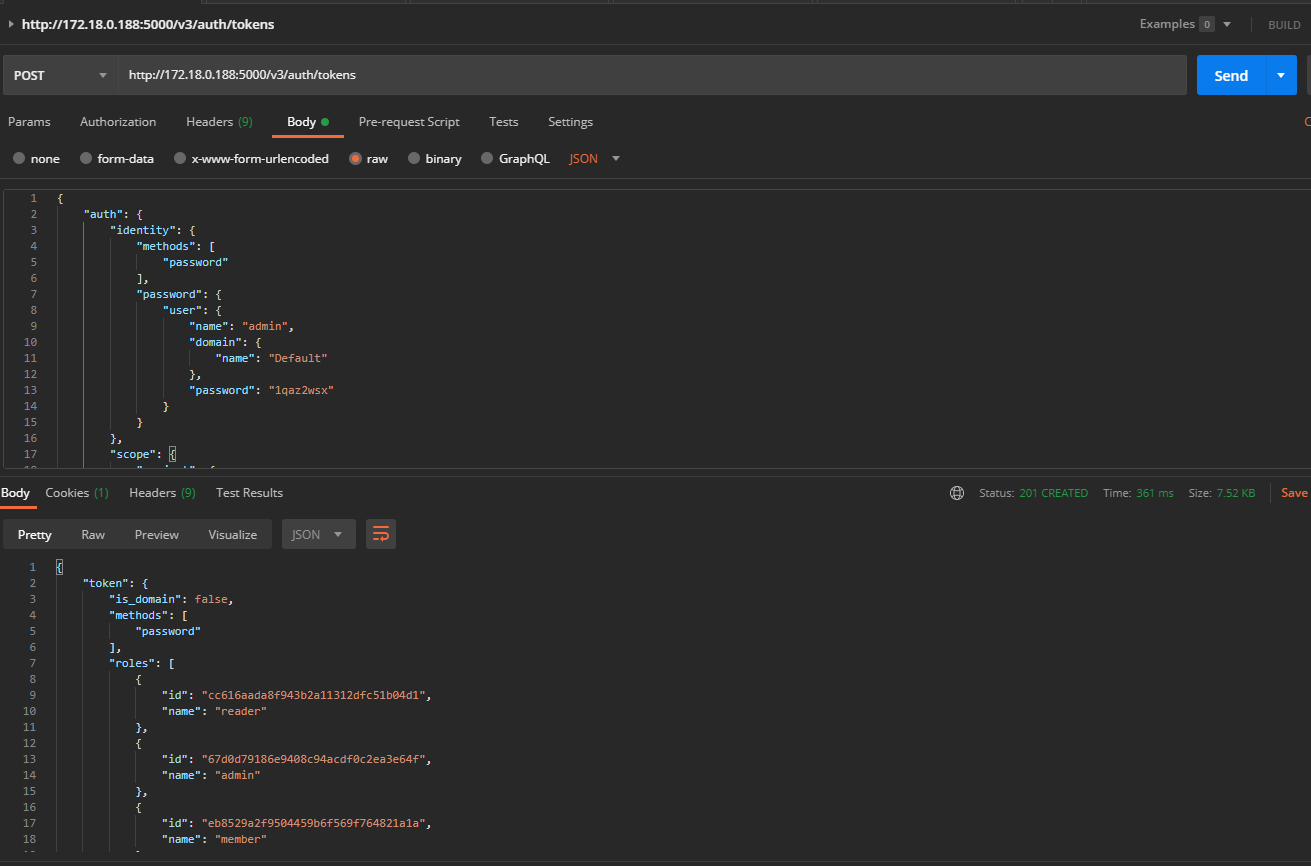
POST /v3/auth/tokens
Password authentication with scoped authorization
Authenticates an identity and generates a token. Uses the password authentication method and scopes authorization to a project, domain, or the system.
The request body must include a payload that specifies the password authentication method which includes the credentials in addition to a project, domain, or system authorization scope.
Relationship: https://docs.openstack.org/api/openstack-identity/3/rel/auth_tokens
Request
Parameters
|
Name |
In |
Type |
Description |
|---|---|---|---|
|
nocatalog (Optional) |
query |
string |
(Since v3.1) The authentication response excludes the service catalog. By default, the response includes the service catalog. |
|
name (Optional) |
body |
string |
The user name. Required if you do not specify the ID of the user. If you specify the user name, you must also specify the domain, by ID or name. |
|
auth |
body |
object |
An |
|
user |
body |
object |
A |
|
scope (Optional) |
body |
string |
The authorization scope, including the system (Since v3.10), a project, or a domain (Since v3.4). If multiple scopes are specified in the same request (e.g. |
|
password |
body |
object |
The |
|
id (Optional) |
body |
string |
The ID of the user. Required if you do not specify the user name. |
|
identity |
body |
object |
An |
|
methods |
body |
array |
The authentication method. For password authentication, specify |
Response
Parameters
|
Name |
In |
Type |
Description |
|---|---|---|---|
|
X-Subject-Token |
header |
string |
The authentication token. An authentication response returns the token ID in this header rather than in the response body. |
|
region_id |
body |
string |
(Since v3.2) The ID of the region that contains the service endpoint. |
|
methods |
body |
array |
The authentication method. For password authentication, specify |
|
roles |
body |
array |
A list of |
|
url |
body |
string |
The endpoint URL. |
|
region |
body |
string |
(Deprecated in v3.2) The geographic location of the service endpoint. |
|
token |
body |
object |
A |
|
expires_at |
body |
string |
The date and time when the token expires. The date and time stamp format is ISO 8601: CCYY-MM-DDThh:mm:ss.sssZ
For example, A |
|
system (Optional) |
body |
object |
A |
|
domain (Optional) |
body |
object |
A |
|
project (Optional) |
body |
object |
A |
|
issued_at |
body |
string |
The date and time when the token was issued. The date and time stamp format is ISO 8601: CCYY-MM-DDThh:mm:ss.sssZ For example, |
|
catalog |
body |
array |
A |
|
user |
body |
object |
A |
|
audit_ids |
body |
array |
A list of one or two audit IDs. An audit ID is a unique, randomly generated, URL-safe string that you can use to track a token. The first audit ID is the current audit ID for the token. The second audit ID is present for only re-scoped tokens and is the audit ID from the token before it was re-scoped. A re- scoped token is one that was exchanged for another token of the same or different scope. You can use these audit IDs to track the use of a token or chain of tokens across multiple requests and endpoints without exposing the token ID to non-privileged users. |
|
interface |
body |
string |
The interface type, which describes the visibility of the endpoint. Value is: - |
|
endpoints |
body |
array |
A list of |
|
type |
body |
string |
The endpoint type. |
|
id (Optional) |
body |
string |
The ID of the user. Required if you do not specify the user name. |
|
name (Optional) |
body |
string |
The user name. Required if you do not specify the ID of the user. If you specify the user name, you must also specify the domain, by ID or name. |
Status Codes
Success
|
Code |
Reason |
|---|---|
201 - Created |
Resource was created and is ready to use. |
Error
|
Code |
Reason |
|---|---|
400 - Bad Request |
Some content in the request was invalid. |
401 - Unauthorized |
User must authenticate before making a request. |
403 - Forbidden |
Policy does not allow current user to do this operation. |
404 - Not Found |
The requested resource could not be found. |





 浙公网安备 33010602011771号
浙公网安备 33010602011771号