A bilinear pairing is a map
A bilinear pairing is a map e : G1 × G2 → G3 where G1, G2 are additive groups, G3 is a multiplicative group, and the map is linear in each component: e(P + Q, R) = e(P, R) · e(Q, R) e(P, Q + R) = e(P, Q) · e(P, R).
Explaining SNARKs Part VII: Pairings of Elliptic Curves
In Part VI, we saw an outline of the Pinocchio zk-SNARK. We were missing two things – an HH that supports both addition and multiplication that is needed for the verifier’s checks, and a transition from an interactive protocol to a non-interactive proof system.
In this post we will see that using elliptic curves we can obtain a limited, but sufficient for our purposes, form of HH that supports multiplication. We will then show that this limited HH also suffices to convert our protocol to the desired non-interactive system.
We begin by introducing elliptic curves and explaining how they give us the necessary HH.
Elliptic curves and their pairings
Assume p is a prime larger than 3, and take some u,v∈Fp such that 4u3+27v2≠0. We look at the equation
Y2=X3+u⋅X+v
An elliptic curve C is the of set of points (x,y) [1] that satisfy such an equation. These curves give us an interesting way to construct groups. The group elements will be the points (x,y)∈F2p that are on the curve, i.e., that satisfy the equation, together with a special point O, that for technical reasons is sometimes refered to as the “point at infinity”, and serves as the identity element, i.e. the zero of the group.
Now the question is how we add two points P=(x1,y1),Q=(x2,y2) to get a third? The addition rule is derived from a somewhat abstract object called the divisor class group of the curve. For our purposes, all you have to know about this divisor class group is that it imposes the following constraint on the definition of addition: The sum of points on any line must be zero, i.e., O.
Let’s see how the addition rule is derived from this constraint. Look at a vertical line, defined by an equation of the form X=c. Suppose this line intersects the curve at a point P=(x1,y1). Because the curve equation is of the form Y2=f(X), if (x1,y1) is on the curve, so is the point Q:=(x1,−y1). Moreover, since it’s a vertical line and the curve equation is of degree two in Y, we can be sure these are the only points where the line and curve intersect.
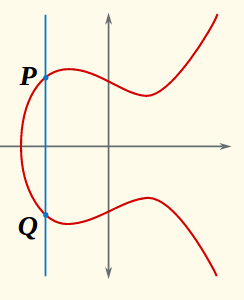
Thus, we must have P+Q=O which means P=−Q; that is, Q is the inverse of P in the group.
Now let us look at points P and Q that have a different first coordinate – that is, x1≠x2, and see how to add them. We pass a line through P and Q.
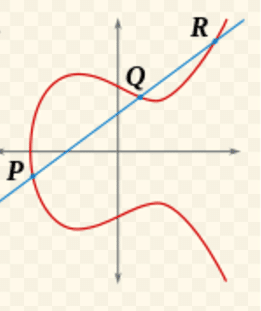
Since the curve is defined by a degree three polynomial in X and already intersects this (non-vertical) line at two points, it is guaranteed to intersect the line at a third point, that we denote R=(x,y), and no other points.
So we must have P+Q+R=O, which means P+Q=−R; and we know by now that −R is obtained from R by flipping the second coordinate from y to −y.
Thus, we have derived the addition rule for our group: Given points P and Q, pass a line through them, and then take the “mirror” point of the third intersection point of the line as the addition result. [2]
This group is usually called C(Fp) – as it consists of points on the curve C with coordinates in Fp; but let’s denote it by G1 from now on. Assume for simplicity that the number of elements in G1 is a prime number r, and is different from p. This is many times the case, for example in the curve that Zcash is currently using. In this case, any element g∈G1 different from O generates G1.
The smallest integer k such that r divides pk−1 is called the embedding degree of the curve. It is conjectured that when k is not too small, say, at least 6, then the discrete logarithm problem in G1, i.e. finding α from g and α⋅g, is very hard. (In BN curves [3] currently used by Zcash k=12.)
The multiplicative group of Fpk contains a subgroup of order r that we denote GT. We can look at curve points with coordinates in Fpk and not just in Fp. Under the same addition rule, these points also form a group together with O called C(Fpk). Note that C(Fpk) clearly contains G1. Besides G1, C(Fpk) will contain an additional subgroup G2 of order r (in fact, r−1

