ofb
AES加密算法中五种模式的差异
最近,我与泽田先生在TDE上做了一些工作。所以我研究了加密算法。到目前为止,我研究了AES中的五种模式。在本文档中,我将介绍五种模式的差异。
一般
分组密码是用于加密或解密的方案,其中,将明文分组视为单个分组,并用于获取具有相同大小的密文分组。如今,AES(高级加密标准)是用于块加密的最常用算法之一。它已由NIST(美国国家标准技术研究院)于2001年进行了标准化,以取代该时期用于加密的DES和3DES。AES块的大小为128位,而加密密钥的大小可以为128位,192位或256位。请注意,密钥长度为3,但是加密块的大小始终为128位。分组密码算法应能够以不同于一个分组的定义大小的大小来加密明文。当明文不足以填充块时,我们可以使用一些算法来填充块,例如PKCS5或PKCS7,如果我们使用ECB或CBC模式,它也可以防御PA攻击。或者我们可以使用支持明文流的AES模式,例如CFB,OFB,CTR模式。
现在让我们介绍AES的五种模式。
- ECB模式:电子密码簿模式
- CBC模式:密码块链接模式
- CFB模式:密码反馈模式
- OFB模式:输出反馈模式
- 点阅率模式:计数器模式
攻击方式:
- PA:拍击
- CPA:选择明文攻击
- CCA:选择词
ECB模式
ECB(电子密码簿)模式是所有模式中最简单的。由于明显的弱点,通常不建议使用。这种模式的方框图如图1所示。
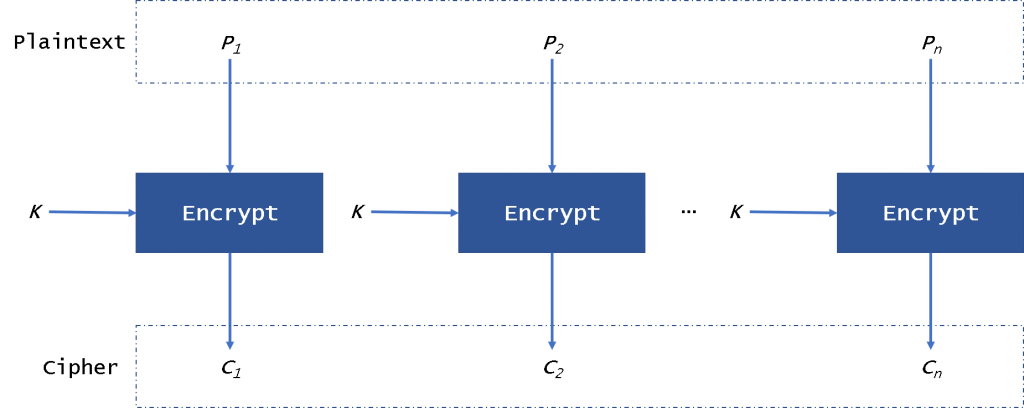

我们可以在图1中看到它,明文被分为多个块,作为AES块的长度128。因此,ECB模式需要填充数据,直到它与块的长度相同为止。然后,将使用相同的密钥和相同的算法对每个块进行加密。因此,如果我们加密相同的明文,我们将获得相同的密文。因此,此模式存在很高的风险。明文和密文块是一一对应的。因为加密/解密是独立的,所以我们可以并行加密/解密数据。而且,如果一个明文或密文块被破坏,则不会影响其他块。
由于ECB的功能,Mallory即使没有得到明文也可以发起攻击。例如,如果我们加密有关银行帐户的数据,如下所示:密文:C1:21 33 4e 5a 35 44 90 4b(该帐户)C2:67 78 45 22 aa cb d1 e5(密码)然后,Mallory可以将C1中的数据复制到C2。然后,他可以使用该帐户作为密码登录系统,该密码更容易获得。
在数据库加密中,我们可以使用ECB对表,索引,wal,临时文件和系统目录进行加密。但是出于安全性考虑,我们不建议使用此模式。
CBC模式
CBC(密码块链接)模式(图2)通过使用初始化向量– IV提供了此功能。IV具有与加密块相同的大小。通常,IV通常是随机数,而不是随机数。
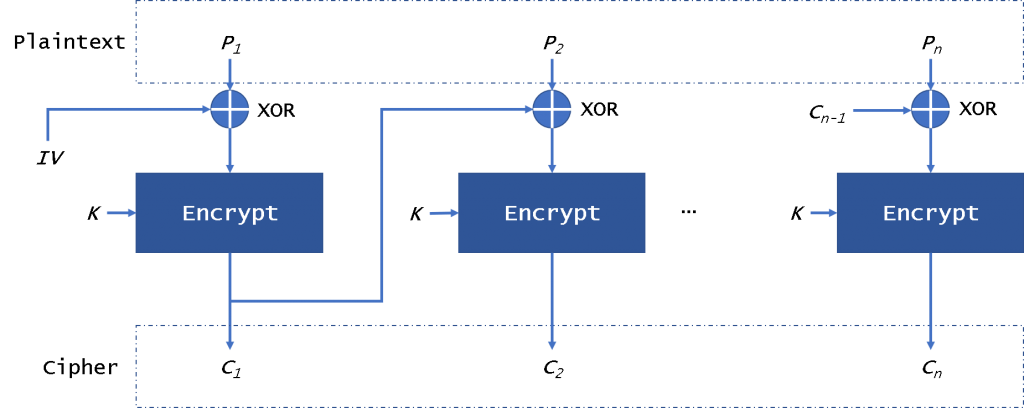
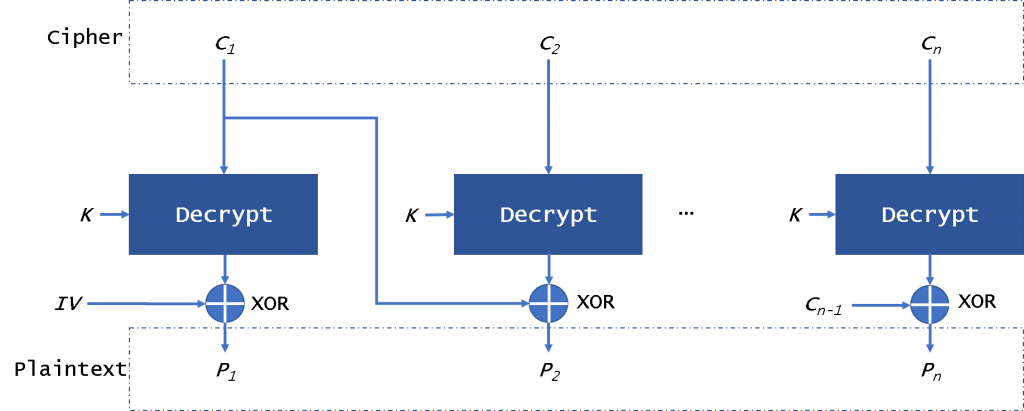
我们可以在图2中看到它,纯文本分为多个块,需要添加填充数据。首先,我们将对IV使用纯文本块xor。然后,CBC将结果加密到密文块。在下一个块中,我们将使用加密结果与明文块进行异或,直到最后一个块。在这种模式下,即使我们加密相同的明文块,也将获得不同的密文块。我们可以并行解密数据,但是在加密数据时是不可能的。如果明文或密文块被破坏,它将影响随后的所有块。
Mallory可以更改IV来攻击系统。即使IV中有一点错误,所有数据也会被破坏。马洛里还可以对Oracle进行填充攻击。他们可以使用一部分密文来填充密文块。这将返回一些有关明文的消息。它不受CPA的影响,但很容易被CCA和PA识别。
为了确保安全性,我们在加密2 ^((n + 1)/ 2)(n是一个块的长度)时需要更改密钥。
CFB模式
CFB(密码反馈)操作模式允许将块加密器用作流密码。它还需要IV。
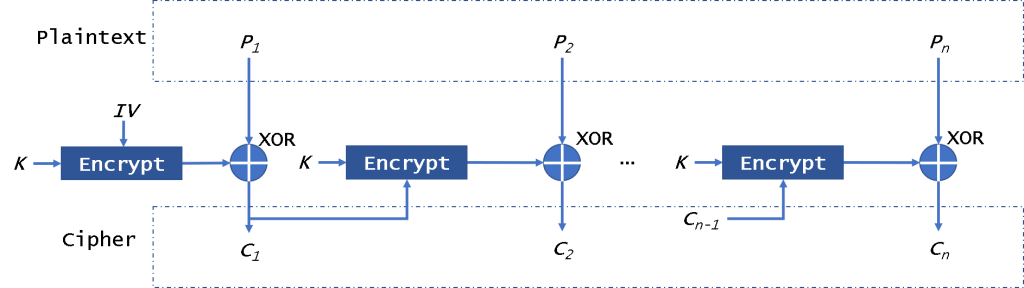
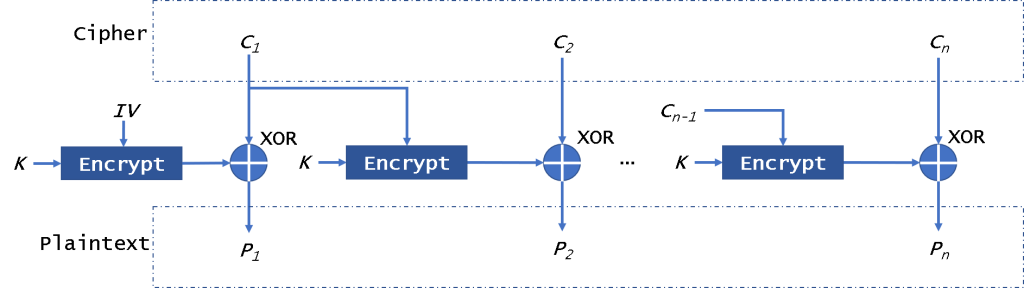
首先,CFB将加密IV,然后将其与纯文本块进行异或运算以获得密文。然后,我们将加密结果加密,以对明文进行异或。因为此模式不会直接加密明文,所以仅使用密文与明文进行异或运算以获取密文。因此,在这种模式下,不需要填充数据。
而且它可以并行解密数据,而不是加密数据。此模式类似于CBC,因此如果有坏块,它将影响所有后续块。
此模式可以通过重放攻击来攻击。例如,如果使用其他密文替换新的密文,则用户将获得错误的数据。但是他不会知道数据是错误的。它不受CPA的影响,但很容易被CCA识别。
为了确保安全,此模式下的密钥需要每2 ^((n + 1)/ 2)个加密块进行一次更改。
OFB模式
OFB(输出反馈)操作模式(图4)还使块加密器可以用作流加密器。它也不需要填充数据。
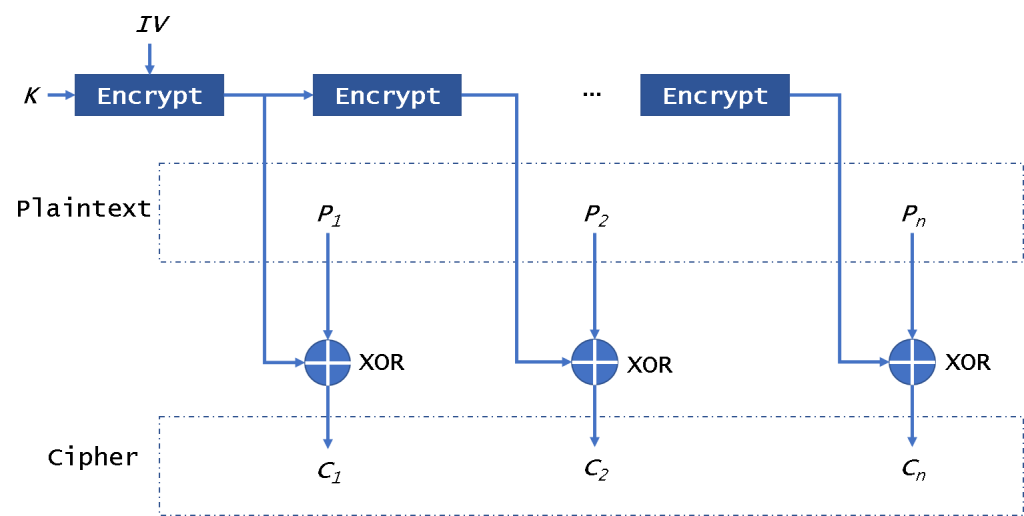
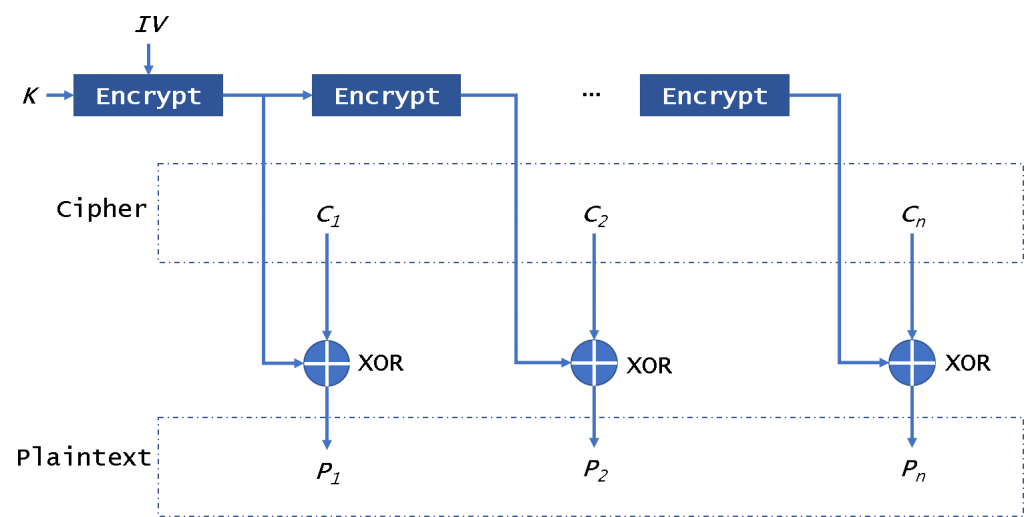
在这种模式下,它将第一次加密IV并加密每个结果。然后它将使用加密结果对明文进行异或运算以获得密文。它与CFB不同,它始终对IV进行加密。它不能并行加密/解密IV。请注意,我们不会解密IV加密结果来解密数据。它不会受到坏块的影响。它不受CPA的影响,但很容易被CCA和PA识别。
Mallory可以更改一些密文以破坏明文。
为了确保安全,此模式下的密钥需要每2 ^(n / 2)个加密块进行一次更改。
点阅模式
在图5所示的CTR(计数器)操作模式下,作为加密器(Encrypt)的输入块,即作为IV,一个计数器的值(Counter,Counter + 1,…,Counter + N – 1)被使用。它也是流加密器。
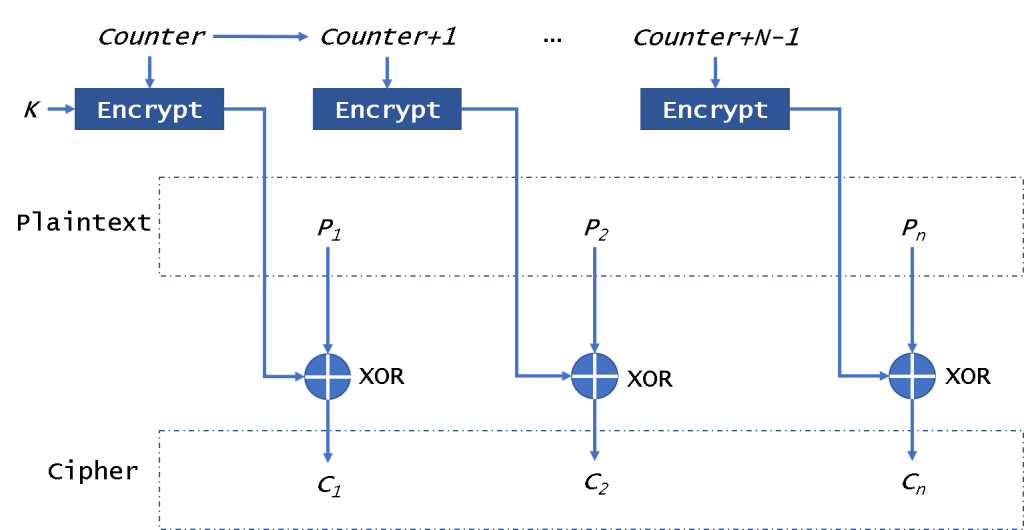
计数器的大小与所用块的大小相同。如图5所示,对来自加密器的输出块执行与纯文本块的XOR操作。所有加密块都使用相同的加密密钥。作为这种模式,它不会受到坏块的影响。这非常像OFB。但是CTR每次都会使用计数器进行加密,而不是使用IV。因此,如果您可以直接获得计数器,则可以并行加密/解密数据。
Mallory可以更改一些密文以破坏明文。在数据库加密中,我们可以使用CBC对所有文件进行加密。
为了确保安全,此模式下的密钥需要每2 ^(n / 2)个加密块进行一次更改。

Recently, I did some work with Sawada-san on the TDE. So I studied on the encryption algorithm. So far, I study five modes in the AES. In this document, I will introduce the difference in the five kinds of mode.
General
The block ciphers are schemes for encryption or decryption where a block of plaintext is treated as a single block and is used to obtain a block of ciphertext with the same size. Today, AES (Advanced Encryption Standard) is one of the most used algorithms for block encryption. It has been standardized by the NIST (National Institute of Standards and Technology) in 2001, in order to replace DES and 3DES which were used for encryption in that period. The size of an AES block is 128 bits, whereas the size of the encryption key can be 128, 192 or 256 bits. Please note this, there is three length in the key, but the size of the encryption block always is 128 bits. Block cipher algorithms should enable encryption of the plaintext with size which is different from the defined size of one block as well. We can use some algorithms for padding block when the plaintext is not enough a block, like PKCS5 or PKCS7, it also can defend against PA attack, if we use ECB or CBC mode. Or we can use the mode of AES which support a stream of plaintext, like CFB, OFB, CTR mode.
Now let’s introduce the five modes of AES.
- ECB mode: Electronic Code Book mode
- CBC mode: Cipher Block Chaining mode
- CFB mode: Cipher FeedBack mode
- OFB mode: Output FeedBack mode
- CTR mode: Counter mode
The attack mode:
- PA: Padding attack
- CPA: Chosen Plaintext Attack
- CCA: Chosen Ci
ECB Mode
The ECB (Electronic Code Book) mode is the simplest of all. Due to obvious weaknesses, it is generally not recommended. A block scheme of this mode is presented in Fig. 1.


We can see it in Fig. 1, the plaintext is divided into blocks as the length of the block of AES, 128. So the ECB mode needs to pad data until it is same as the length of the block. Then every block will be encrypted with the same key and same algorithm. So if we encrypt the same plaintext, we will get the same ciphertext. So there is a high risk in this mode. And the plaintext and ciphertext blocks are a one-to-one correspondence. Because the encryption/ decryption is independent, so we can encrypt/decrypt the data in parallel. And if a block of plaintext or ciphertext is broken, it won’t affect other blocks.
Because of the feature of ECB, the Mallory can make an attack even if they don’t get the plaintext. For example, if we encrypt the data about our bank account, like this: The ciphertext: C1: 21 33 4e 5a 35 44 90 4b(the account) C2: 67 78 45 22 aa cb d1 e5(the password) Then the Mallory can copy the data in C1 to C2. Then he can log in the system with the account as the password which is easier to get.
In the database encryption, we can use ECB to encrypt the tables, indexes, wal, temp files, and system catalogs. But with the issues of security, we don’t suggest to use this mode.
CBC mode
The CBC (Cipher Block Chaining) mode (Fig. 2) provides this by using an initialization vector – IV. The IV has the same size as the block that is encrypted. In general, the IV usually is a random number, not a nonce.


We can see it in figure 2, the plaintext is divided into blocks and needs to add padding data. First, we will use the plaintext block xor with the IV. Then CBC will encrypt the result to the ciphertext block. In the next block, we will use the encryption result to xor with plaintext block until the last block. In this mode, even if we encrypt the same plaintext block, we will get a different ciphertext block. We can decrypt the data in parallel, but it is not possible when encrypting data. If a plaintext or ciphertext block is broken, it will affect all following block.
A Mallory can change the IV to attack the system. Even if a bit is wrong in the IV, all data is broken. Mallory also can make a padding oracle attack. They can use a part of ciphertext to pad the ciphertext block. This will return some messages about the plaintext. It is safe from CPA, but it is easily sysceptible to CCA and PA.
To ensure security, we need to change the key when we encrypt 2^((n+1)/2)(n is the length of a block).
CFB mode
The CFB (Cipher FeedBack) mode of operation allows the block encryptor to be used as a stream cipher. It also needs an IV.


First, CFB will encrypt the IV, then it will xor with plaintext block to get ciphertext. Then we will encrypt the encryption result to xor the plaintext. Because this mode will not encrypt plaintext directly, it just uses the ciphertext to xor with the plaintext to get the ciphertext. So in this mode, it doesn’t need to pad data.
And it could decrypt data in parallel, not encryption. This mode is similar to the CBC, so if there is a broken block, it will affect all following block.
This mode can be attacked by replay attack. For example, if you use the other ciphertext to replace the new ciphertext, the user will get the wrong data. But he will not know the data is wrong. It is safe from CPA, but it is easily sysceptible to CCA.
To ensure security, the key in this mode need to be changed for every 2^((n+1)/2) encryption blocks.
OFB mode
The OFB (Output FeedBack) mode of operation (Fig. 4) also enables a block encryptor to be used as a stream encryptor. It also doesn’t need padding data.


In this mode, it will encrypt the IV in the first time and encrypt the per-result. Then it will use the encryption results to xor the plaintext to get ciphertext. It is different from CFB, it always encrypts the IV. It can not encrypt/decrypt the IV in parallel. Please note that we won’t decrypt the IV encryption results to decrypt data. It will not be affected by the broken block. It is safe from CPA, but it is easily sysceptible to CCA and PA.
A Mallory can change some bits of ciphertext to damage the plaintext.
To ensure security, the key in this mode need to be changed for every 2^(n/2) encryption blocks.
CTR mode
At the CTR (Counter) mode of operation, shown in Fig. 5, as an input block to the encryptor (Encrypt), i.e. as an IV, the value of a counter (Counter, Counter + 1,…, Counter + N – 1) is used. It also is a stream encryptor.


The counter has the same size as the used block. As shown in Fig. 5, the XOR operation with the block of plain text is performed on the output block from the encryptor. All encryption blocks use the same encryption key. As this mode, It will not be affected by the broken block. It is very like OFB. But CTR will use the counter to be encrypted every time instead of the IV. So if you could get counter directly, you can encrypt/decrypt data in parallel.
A Mallory can change some bits of ciphertext to break the plaintext. In the database encryption, we can use CBC to encrypt all the files.
To ensure security, the key in this mode need to be changed for every 2^(n/2) encryption blocks.



 浙公网安备 33010602011771号
浙公网安备 33010602011771号