Cobaltstrike系列教程(十)安装扩展
0x00-前文
有技术交流或渗透测试培训需求的朋友欢迎联系QQ/VX-547006660,需要代码审计、渗透测试、红蓝对抗网络安全相关业务可以看置顶博文
2000人网络安全交流群,欢迎大佬们来玩
群号820783253
Cobaltstrike系列教程(一)简介与安装
https://bbs.ichunqiu.com/thread-52937-1-1.html
Cobaltstrike系列教程(二)Listner与Payload生成
https://bbs.ichunqiu.com/thread-52982-1-1.html
Cobaltstrike系列教程(三)beacon详解
https://bbs.ichunqiu.com/thread-52994-1-1.html
Cobaltstrike系列教程(四)菜单栏与视图
https://bbs.ichunqiu.com/thread-52997-1-1.html
Cobaltstrike系列教程(五)凭据导出
https://bbs.ichunqiu.com/thread-53001-1-1.html
Cobaltstrike系列教程(六)文件/进程管理与键盘记录
https://bbs.ichunqiu.com/thread-53003-1-1.html
Cobaltstrike系列教程(七)端口扫描与Net View
https://bbs.ichunqiu.com/thread-53012-1-1.html
Cobaltstrike系列教程(八)截图与浏览器代理
https://bbs.ichunqiu.com/thread-53013-1-1.html
Cobaltstrike系列教程(九)内置Socks与神器EW
https://bbs.ichunqiu.com/thread-53014-1-1.html
0x001-扩展的加载
扩展是Cobaltstrike一个极为重要的模块,它有效地丰盈了cobaltstrike的功能
选择菜单栏的CobaltStrike-->脚本管理器,点击load,然后选择cna扩展文件即可,旁边的unload为去除该扩展,,reload为重新加载该扩展

0x002-个人常用扩展
0x003-其他扩展汇总(来自WBG老哥)
脚本名称:elevate.cna
脚本名称:ProcessTree.cna
脚本名称:CVE-2018-4878.cna
脚本功能:CVE-2018-4878.cna
脚本名称:ArtifactPayloadGenerator.cna
脚本功能:创建多种类型的payload。生成的文件在cs目录下的opt\cobaltstrike

脚本名称:AVQuery.cna
脚本功能:查询目标所安装的所有杀软
脚本名称:CertUtilWebDelivery.cna
脚本功能:利用CertUtil和rundll32生成会话这个应该都知道了解
脚本名称:RedTeamRepo.cna
脚本名称:ProcessColor.cna
脚本功能:显示带有颜色的进程列表(不同颜色有不同含义)
[ ]
]
脚本名称:EDR.cna
脚本功能:检查有无终端安全产品
脚本名称:logvis.cna
脚本功能:显示Beacon命令日志

脚本名称:ProcessMonitor.cna
脚本功能:记录一段时间内程序启动的情况
脚本名称:SMBPayloadGenerator.cna
脚本功能:生成基于SMB的payload
脚本名称:Persistence/Persistence_Menu.cna
脚本功能:持久化控制集合
备注:这个脚本是同目录脚本的一个集合

脚本名称:Eternalblue.cna 脚本功能:ms17-010
https://gist.github.com/rsmudge/9b54a66744a94f3950cc171254057942
备注:调用exploit/windows/smb/ms17_010_eternalblue
更多:https://mp.weixin.qq.com/s/CEI1XYkq2PZmYsP0DRU7jg
个人认位这位老哥整理的已经很全面了,为了方便查看我将里面的一些集合脚本介绍图片列了出来。
https://github.com/harleyQu1nn/AggressorScripts

https://github.com/bluscreenofjeff/AggressorScripts

https://github.com/michalkoczwara/aggressor_scripts_collection

https://github.com/vysec/Aggressor-VYSEC

https://github.com/killswitch-GUI/CobaltStrike-ToolKit

https://github.com/ramen0x3f/AggressorScripts
https://github.com/rasta-mouse/Aggressor-Script

https://github.com/Und3rf10w/Aggressor-scripts

https://github.com/001SPARTaN/aggressor_scripts

https://github.com/gaudard/scripts/tree/master/red-team/aggressor

https://github.com/branthale/CobaltStrikeCNA

https://github.com/threatexpress/aggressor-scripts https://github.com/threatexpress/red-team-scripts https://github.com/threatexpress/persistence-aggressor-script
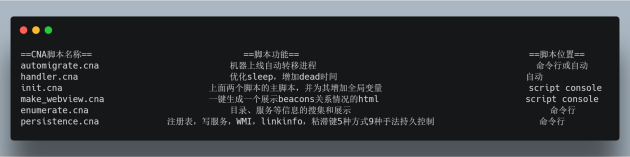
https://github.com/FortyNorthSecurity/AggressorAssessor

脚本来源:
https://github.com/rsmudge/ElevateKit
https://github.com/vysec/CVE-2018-4878 https://github.com/harleyQu1nn/AggressorScripts https://github.com/bluscreenofjeff/AggressorScripts https://github.com/ramen0x3f/AggressorScripts
https://github.com/360-A-Team/CobaltStrike-Toolset https://github.com/ars3n11/Aggressor-Scripts https://github.com/michalkoczwara/aggressor_scripts_collection https://github.com/vysec/Aggressor-VYSEC
https://github.com/killswitch-GUI/CobaltStrike-ToolKit https://github.com/ZonkSec/persistence-aggressor-script https://github.com/ramen0x3f/AggressorScripts
https://github.com/rasta-mouse/Aggressor-Script https://github.com/RhinoSecurityLabs/Aggressor-Scripts https://github.com/Und3rf10w/Aggressor-scripts
https://github.com/Kevin-Robertson/Inveigh
https://github.com/Genetic-Malware/Ebowla https://github.com/001SPARTaN/aggressor_scripts https://github.com/gaudard/scripts/tree/master/red-team/aggressor https://github.com/branthale/CobaltStrikeCNA https://github.com/oldb00t/AggressorScripts https://github.com/p292/Phant0m_cobaltstrike https://github.com/p292/DDEAutoCS https://github.com/secgroundzero/CS-Aggressor-Scripts https://github.com/skyleronken/Aggressor-Scripts https://github.com/tevora-threat/aggressor-powerview https://github.com/tevora-threat/PowerView3-Aggressor https://github.com/threatexpress/aggressor-scripts https://github.com/threatexpress/red-team-scripts
https://github.com/threatexpress/persistence-aggressor-script https://github.com/FortyNorthSecurity/AggressorAssessor https://github.com/mdsecactivebreach/CACTUSTORCH https://github.com/C0axx/AggressorScripts https://github.com/offsecginger/AggressorScripts https://github.com/tomsteele/cs-magik https://github.com/bitsadmin/nopowershell https://github.com/SpiderLabs/SharpCompile https://github.com/SpiderLabs/SharpCompile https://github.com/realoriginal/reflectivepotato
还有很多很多我就不列出来了太麻烦了。







