buuoj-[ACTF新生赛2020]usualCrypt
1.winexe 32bit 无壳
2.shiftf+f12找一下
找到主体
把能识别出的变量名、函数名都改了
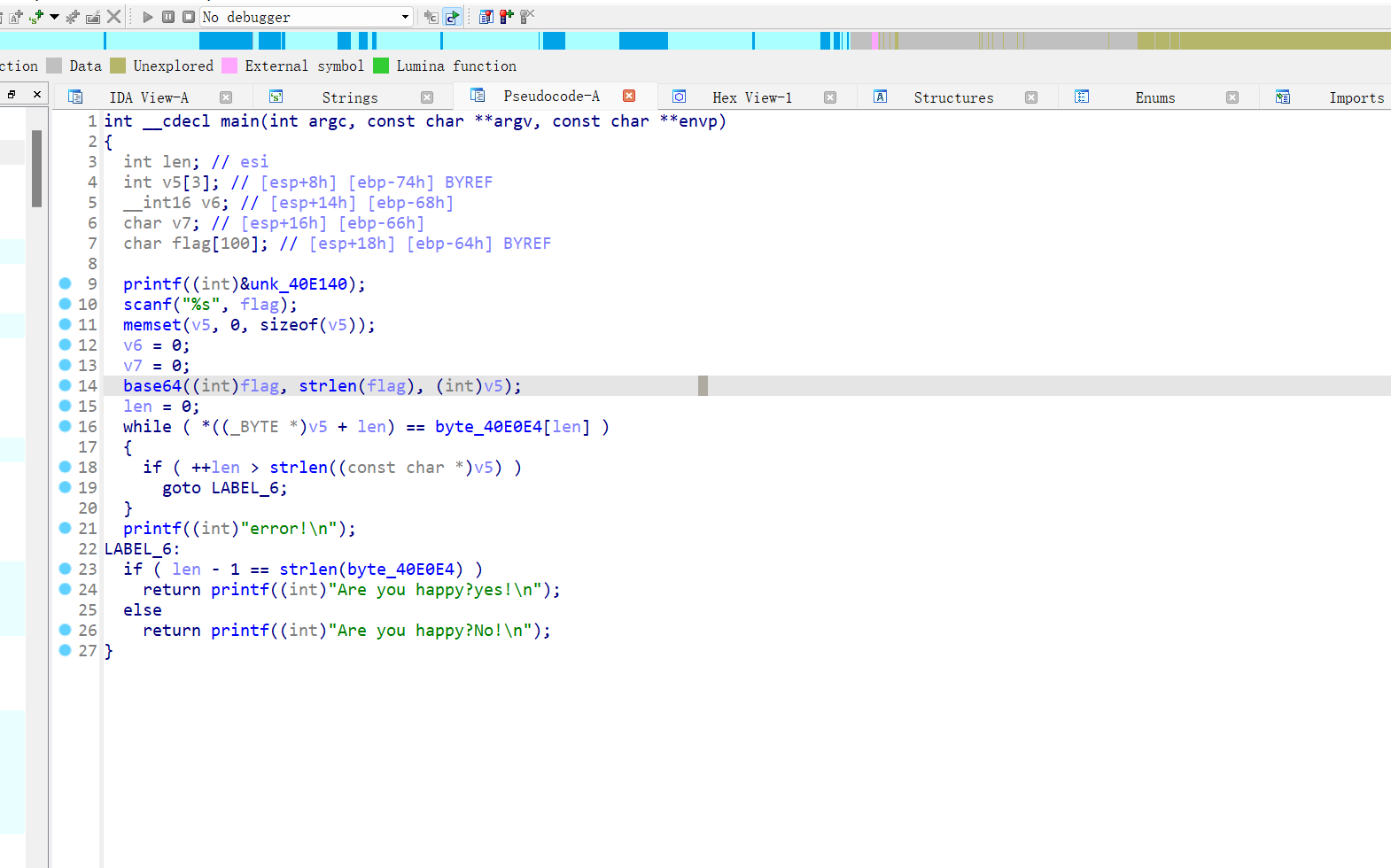
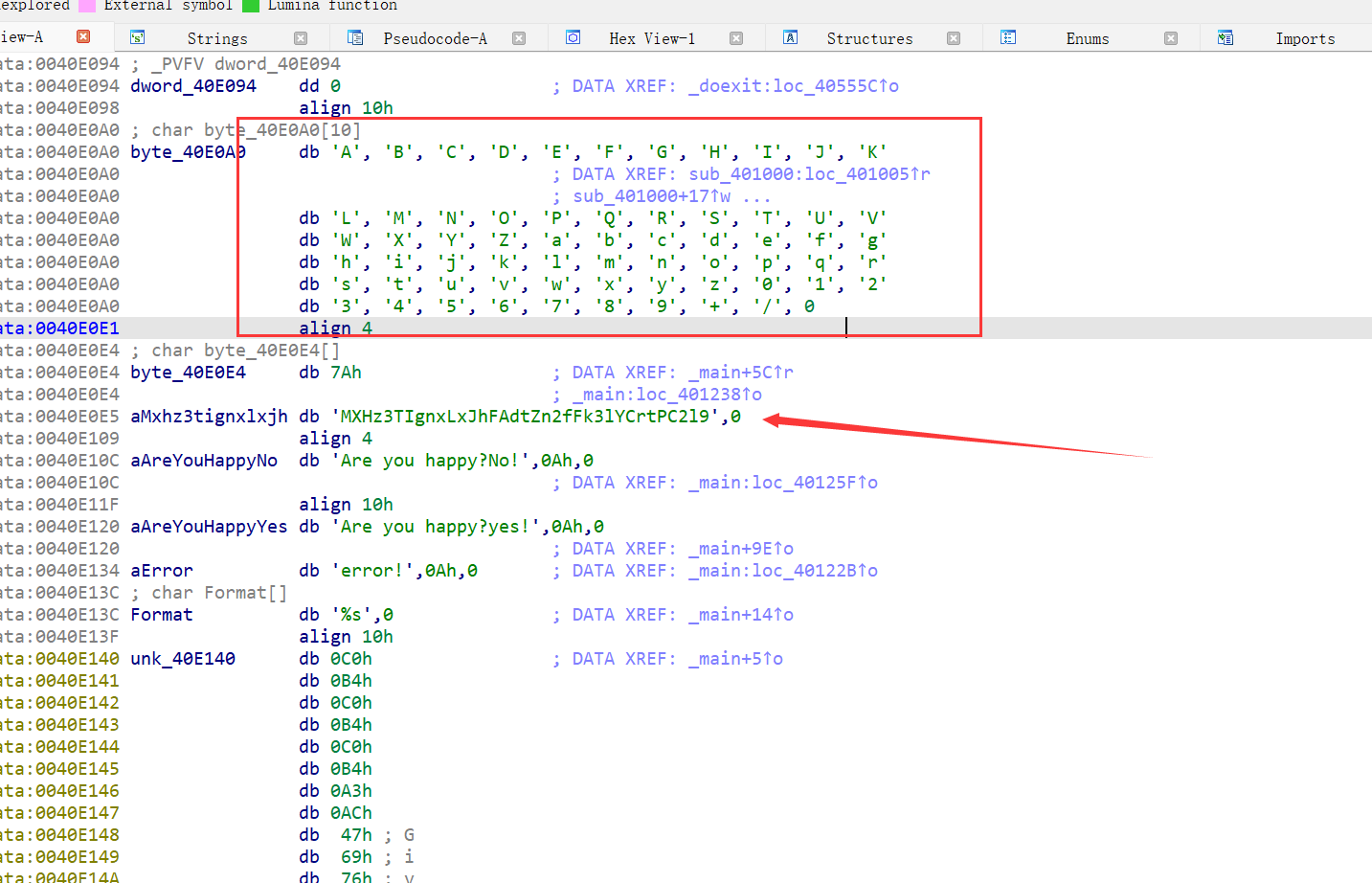
初步判断是base64
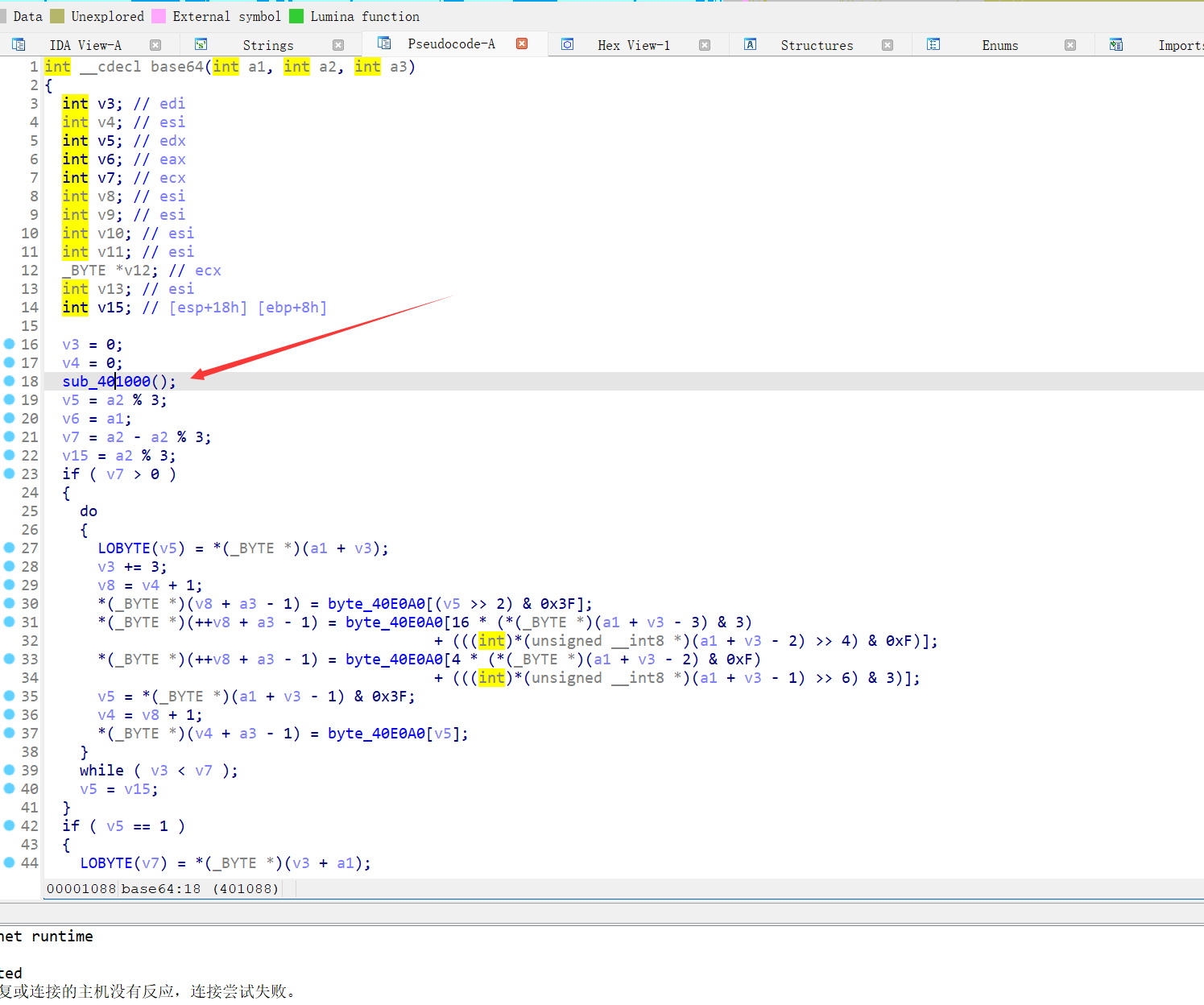
BASE加密函数里面还有一个函数,点进去:
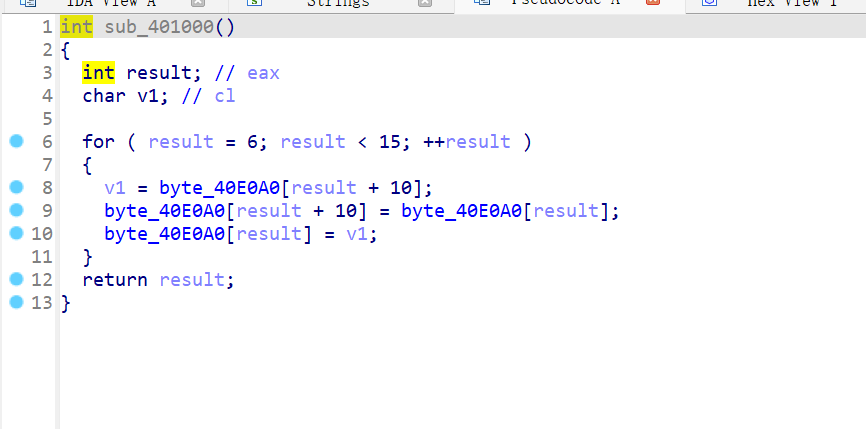
很好判断,是变表
写个脚本:
base=[ 0x41, 0x42, 0x43, 0x44, 0x45, 0x46, 0x47, 0x48, 0x49, 0x4A,
0x4B, 0x4C, 0x4D, 0x4E, 0x4F, 0x50, 0x51, 0x52, 0x53, 0x54,
0x55, 0x56, 0x57, 0x58, 0x59, 0x5A, 0x61, 0x62, 0x63, 0x64,
0x65, 0x66, 0x67, 0x68, 0x69, 0x6A, 0x6B, 0x6C, 0x6D, 0x6E,
0x6F, 0x70, 0x71, 0x72, 0x73, 0x74, 0x75, 0x76, 0x77, 0x78,
0x79, 0x7A, 0x30, 0x31, 0x32, 0x33, 0x34, 0x35, 0x36, 0x37,
0x38, 0x39, 0x2B, 0x2F, 0x00]
for i in range(6,15):
tem=base[i+10]
base[i+10]=base[i]
base[i]=tem
for al in base:
print(chr(al),end='')
变表:
ABCDEFQRSTUVWXYPGHIJKLMNOZabcdefghijklmnopqrstuvwxyz0123456789+/
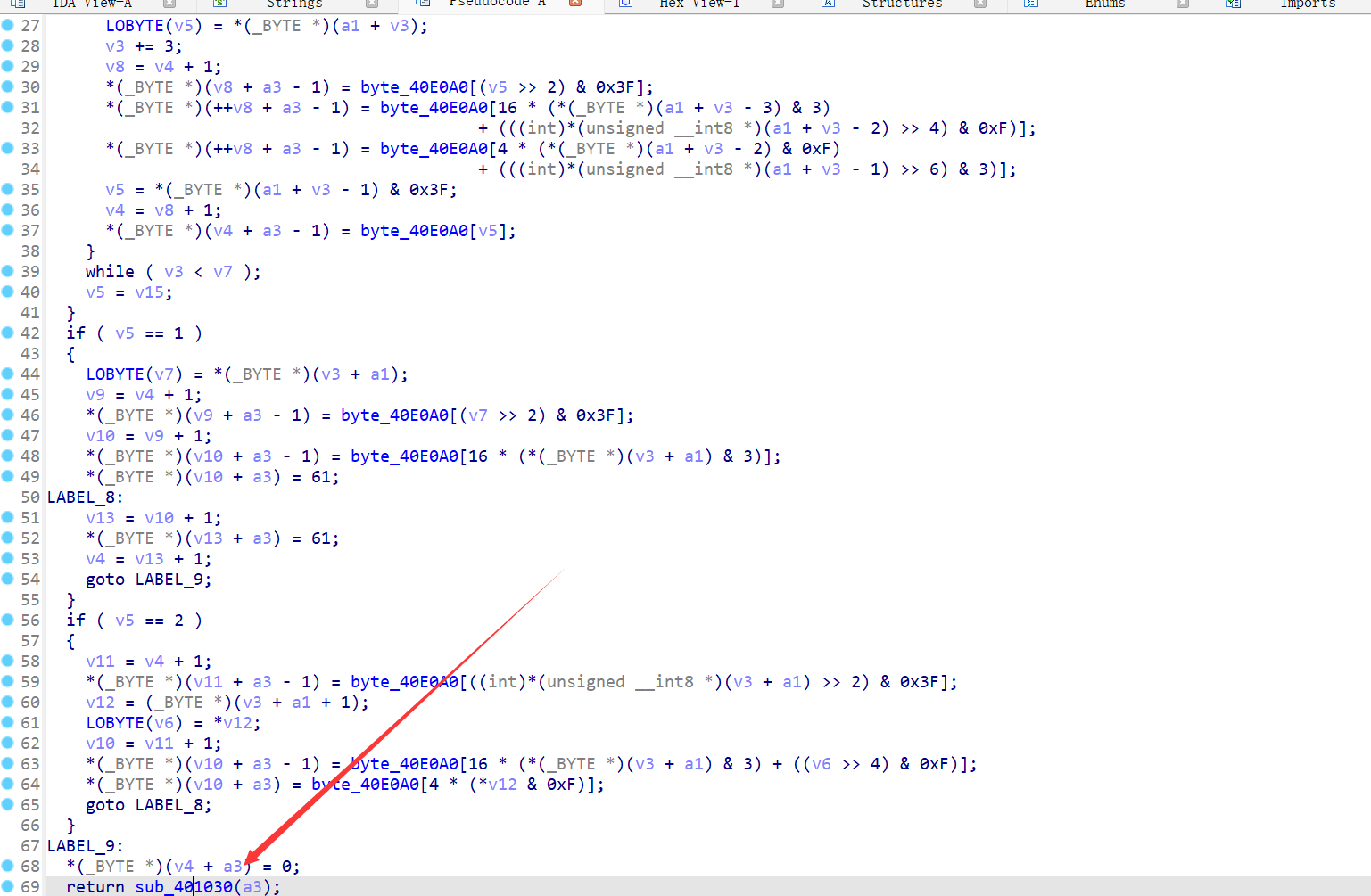
最下面还有一个函数,点进去:

思路就是先将zMXHz3TIgnxLxJhFAdtZn2fFk3lYCrtPC2l9大小写转换,然后变表解密
写个脚本解码就好了:
import base64
origin='zMXHz3TIgnxLxJhFAdtZn2fFk3lYCrtPC2l9=='
origin_tem=''
for al in origin:
al=ord(al)
if al>=ord('a') and al<=ord('z'):
al-=32
elif al>=ord('A') and al<=ord('Z'):
al+=32
al=chr(al)
origin_tem+=al
base64_biao=str.maketrans('ABCDEFQRSTUVWXYPGHIJKLMNOZabcdefghijklmnopqrstuvwxyz0123456789+/','ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/')
print(base64.b64decode(origin_tem.translate(base64_biao)))
得到flag
flag{bAse64_h2s_a_Surprise}


