buuoj-[MRCTF2020]Transform
1.winexe 64bit 无壳
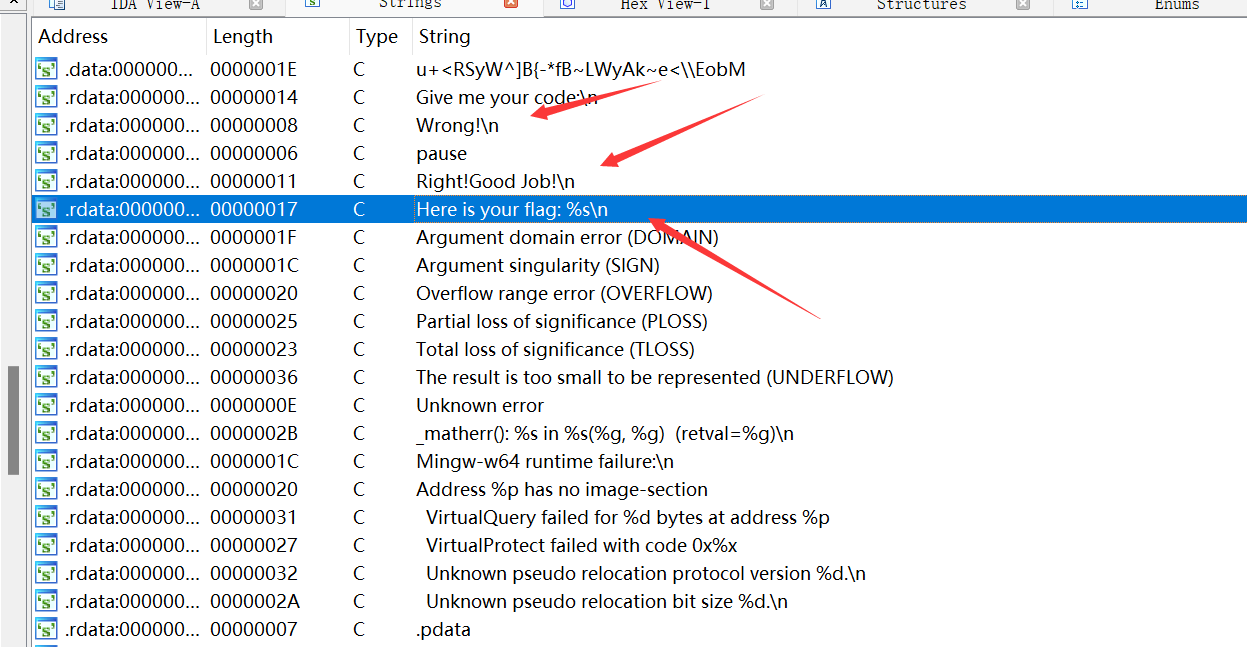
2.存在关键字符串
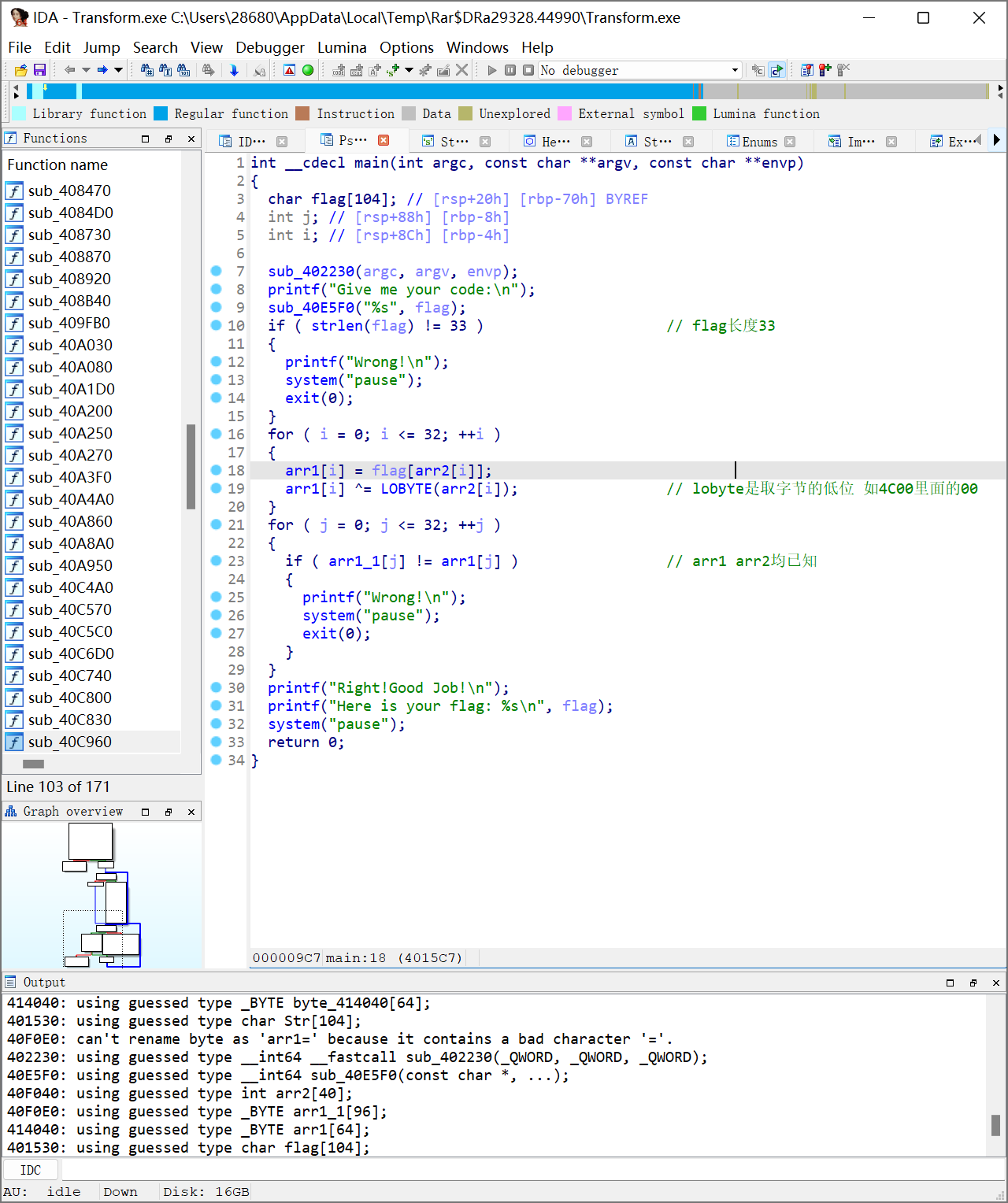
3.ctrl+x跟踪找到程序主体

4.浅浅分析+百度lobyte是啥一下
5.脚本
arr1=[0x67, 0x79, 0x7B, 0x7F, 0x75, 0x2B, 0x3C, 0x52, 0x53, 0x79,
0x57, 0x5E, 0x5D, 0x42, 0x7B, 0x2D, 0x2A, 0x66, 0x42, 0x7E,
0x4C, 0x57, 0x79, 0x41, 0x6B, 0x7E, 0x65, 0x3C, 0x5C, 0x45,
0x6F, 0x62, 0x4D]
arr2=[9, 10, 15, 23, 7, 24, 12, 6, 1, 16, 3, 17, 32, 29, 11, 30, 27, 22, 4, 13, 19, 20, 21, 2, 25, 5, 31, 8, 18, 26, 28, 14,0]
flag_tem=[0]*33
for i in range(0,33):
arr1[i]^=arr2[i]
for i in range(0,33):
flag_tem[arr2[i]]=arr1[i]
for i in range(0,33):
print(chr(flag_tem[i]),end='')
得到MRCTF{Tr4nsp0sltiON_Clph3r_1s_3z}
flag{Tr4nsp0sltiON_Clph3r_1s_3z}


