DWVA-关于存储型xss的漏洞详解<xss stored>
low级别
代码如下:
1 <?php 2 3 if( isset( $_POST[ 'btnSign' ] ) ) { 4 // Get input 5 $message = trim( $_POST[ 'mtxMessage' ] ); 6 $name = trim( $_POST[ 'txtName' ] ); 7 8 // Sanitize message input 9 $message = stripslashes( $message ); 10 $message = ((isset($GLOBALS["___mysqli_ston"]) && is_object($GLOBALS["___mysqli_ston"])) ? mysqli_real_escape_string($GLOBALS["___mysqli_ston"], $message ) : ((trigger_error("[MySQLConverterToo] Fix the mysql_escape_string() call! This code does not work.", E_USER_ERROR)) ? "" : "")); 11 12 // Sanitize name input 13 $name = ((isset($GLOBALS["___mysqli_ston"]) && is_object($GLOBALS["___mysqli_ston"])) ? mysqli_real_escape_string($GLOBALS["___mysqli_ston"], $name ) : ((trigger_error("[MySQLConverterToo] Fix the mysql_escape_string() call! This code does not work.", E_USER_ERROR)) ? "" : "")); 14 15 // Update database 16 $query = "INSERT INTO guestbook ( comment, name ) VALUES ( '$message', '$name' );"; 17 $result = mysqli_query($GLOBALS["___mysqli_ston"], $query ) or die( '<pre>' . ((is_object($GLOBALS["___mysqli_ston"])) ? mysqli_error($GLOBALS["___mysqli_ston"]) : (($___mysqli_res = mysqli_connect_error()) ? $___mysqli_res : false)) . '</pre>' ); 18 19 //mysql_close(); 20 } 21 22 ?>
代码中各个函数功能如下:
trim(string,charlist)
函数移除字符串两侧的空白字符或其他预定义字符,预定义字符包括、\t、\n、\x0B、\r以及空格,可选参数charlist支持添加额外需要删除的字符。
mysql_real_escape_string(string,connection)
函数会对字符串中的特殊符号(\x00,\n,\r,\,‘,“,\x1a)进行转义。
stripslashes(string)
函数删除字符串中的反斜杠。
对于输入的参数message,并没有做相关过滤,所以可以进行注入。
message栏填入:
<script>alert('hahaha')</script>
效果如下:
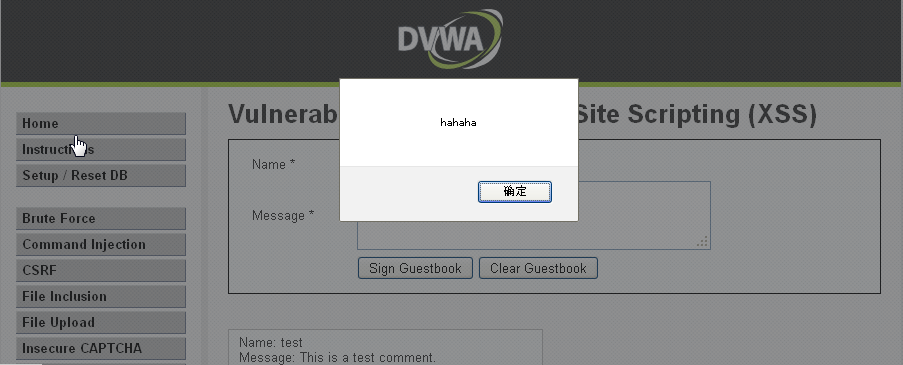
还有一种方法,在name栏填入构造的恶意代码,由于name栏有字符大小限制,所以可以用burpsuit抓包后改为<script>alert('hahaha')</script>
即可注入成功。
medium级别
代码如下:
1 <?php 2 3 if( isset( $_POST[ 'btnSign' ] ) ) { 4 // Get input 5 $message = trim( $_POST[ 'mtxMessage' ] ); 6 $name = trim( $_POST[ 'txtName' ] ); 7 8 // Sanitize message input 9 $message = strip_tags( addslashes( $message ) ); 10 $message = ((isset($GLOBALS["___mysqli_ston"]) && is_object($GLOBALS["___mysqli_ston"])) ? mysqli_real_escape_string($GLOBALS["___mysqli_ston"], $message ) : ((trigger_error("[MySQLConverterToo] Fix the mysql_escape_string() call! This code does not work.", E_USER_ERROR)) ? "" : "")); 11 $message = htmlspecialchars( $message ); 12 13 // Sanitize name input 14 $name = str_replace( '<script>', '', $name ); 15 $name = ((isset($GLOBALS["___mysqli_ston"]) && is_object($GLOBALS["___mysqli_ston"])) ? mysqli_real_escape_string($GLOBALS["___mysqli_ston"], $name ) : ((trigger_error("[MySQLConverterToo] Fix the mysql_escape_string() call! This code does not work.", E_USER_ERROR)) ? "" : "")); 16 17 // Update database 18 $query = "INSERT INTO guestbook ( comment, name ) VALUES ( '$message', '$name' );"; 19 $result = mysqli_query($GLOBALS["___mysqli_ston"], $query ) or die( '<pre>' . ((is_object($GLOBALS["___mysqli_ston"])) ? mysqli_error($GLOBALS["___mysqli_ston"]) : (($___mysqli_res = mysqli_connect_error()) ? $___mysqli_res : false)) . '</pre>' ); 20 21 //mysql_close(); 22 } 23 24 ?>
从代码可以看出,对于message的输入参数使用htmlspecialchars函数进行了重新编码,无法使用之前的xss注入了
但是对于name参数的输入,仅仅是将<script>便签转换为空,因此可以用组合进行绕过
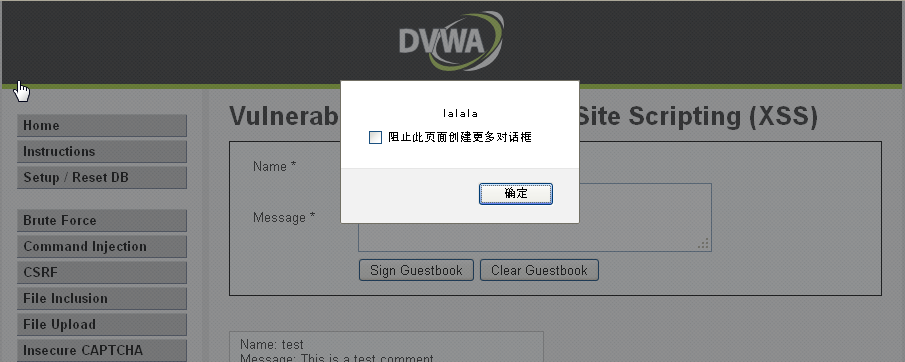
先输入任意参数提交,burpsuit抓包,更改为:
<scr<script>ipt>alert('lalala')</script>
效果如下:
也可以使用大小绕过
<sCrIpt>alert('aaaaa')</ScRipt>
效果如下:

high级别
代码如下:
1 <?php 2 3 if( isset( $_POST[ 'btnSign' ] ) ) { 4 // Get input 5 $message = trim( $_POST[ 'mtxMessage' ] ); 6 $name = trim( $_POST[ 'txtName' ] ); 7 8 // Sanitize message input 9 $message = strip_tags( addslashes( $message ) ); 10 $message = ((isset($GLOBALS["___mysqli_ston"]) && is_object($GLOBALS["___mysqli_ston"])) ? mysqli_real_escape_string($GLOBALS["___mysqli_ston"], $message ) : ((trigger_error("[MySQLConverterToo] Fix the mysql_escape_string() call! This code does not work.", E_USER_ERROR)) ? "" : "")); 11 $message = htmlspecialchars( $message ); 12 13 // Sanitize name input 14 $name = preg_replace( '/<(.*)s(.*)c(.*)r(.*)i(.*)p(.*)t/i', '', $name ); 15 $name = ((isset($GLOBALS["___mysqli_ston"]) && is_object($GLOBALS["___mysqli_ston"])) ? mysqli_real_escape_string($GLOBALS["___mysqli_ston"], $name ) : ((trigger_error("[MySQLConverterToo] Fix the mysql_escape_string() call! This code does not work.", E_USER_ERROR)) ? "" : "")); 16 17 // Update database 18 $query = "INSERT INTO guestbook ( comment, name ) VALUES ( '$message', '$name' );"; 19 $result = mysqli_query($GLOBALS["___mysqli_ston"], $query ) or die( '<pre>' . ((is_object($GLOBALS["___mysqli_ston"])) ? mysqli_error($GLOBALS["___mysqli_ston"]) : (($___mysqli_res = mysqli_connect_error()) ? $___mysqli_res : false)) . '</pre>' ); 20 21 //mysql_close(); 22 } 23 24 ?>
代码中对name的提交参数进行了过滤转换,所以不能用<script>进行注入,可以使用如下方法:
<img src=1 onerror=alert('yayaya')>
效果如下:



 浙公网安备 33010602011771号
浙公网安备 33010602011771号