[HECTF 2021] 解题报告
Reverse
hard
签到题,字符串窗口直接看到flag
HECTF{HElLo_RRRRe}
Baby_upx
exeinfo查一下,发现有壳
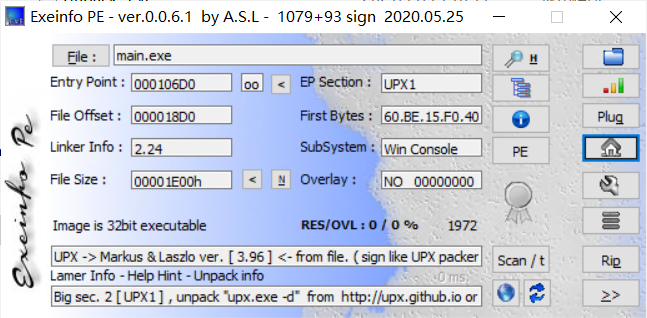
直接用Upx脱不掉壳,那考虑用ESP定律手脱(刚好刚学ESP脱壳,正好拿来练手,顺便记录一下详细的实现过程)
打开Ollydbg,程序的入口特征是pushad,等会肯定得找popad
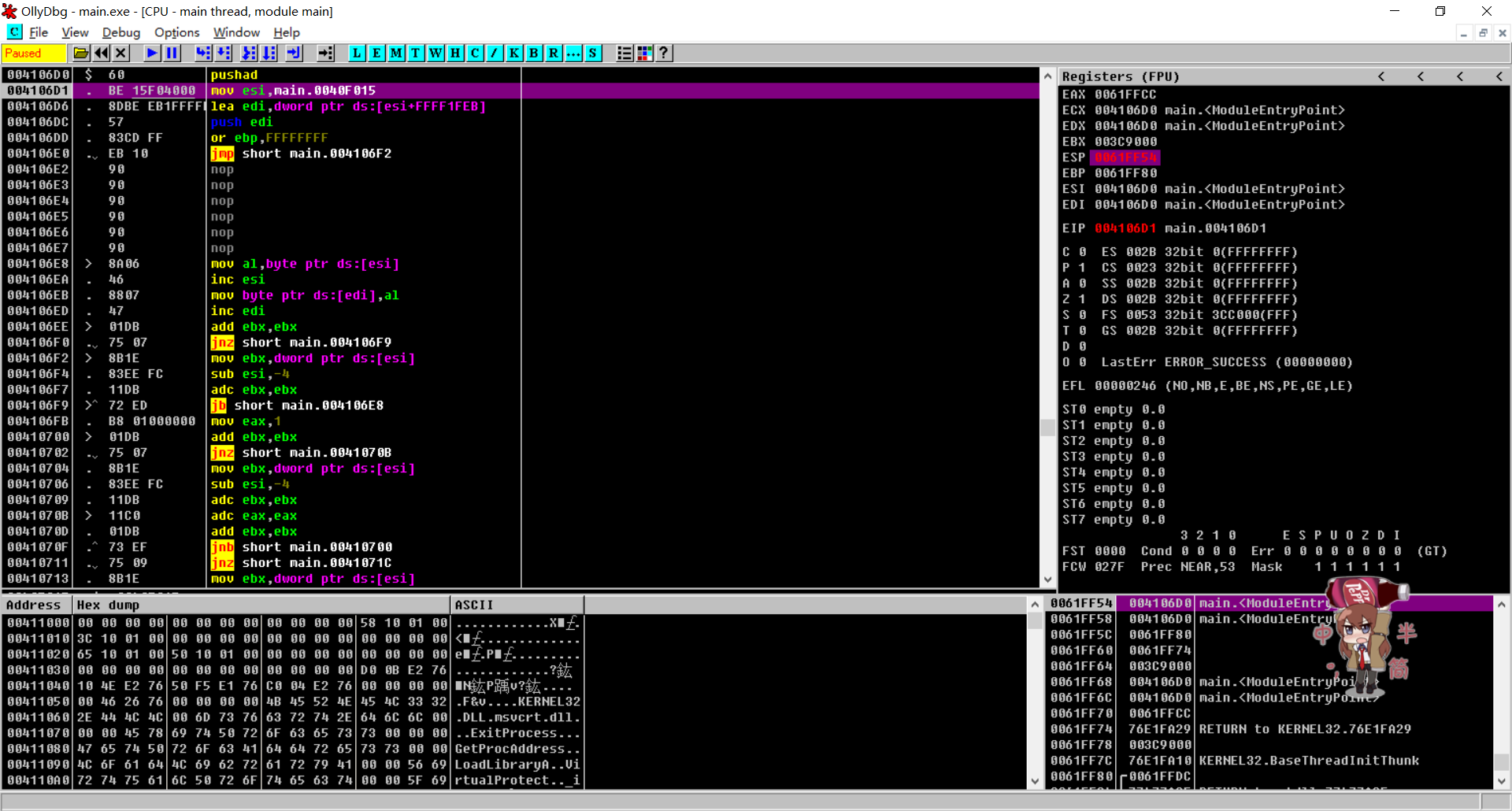
单步步入,然后在右边发现只有ESP改变了,右键ESP,点Follow in Dump,这时Hex Dump窗口第一行就是我们想要的东西
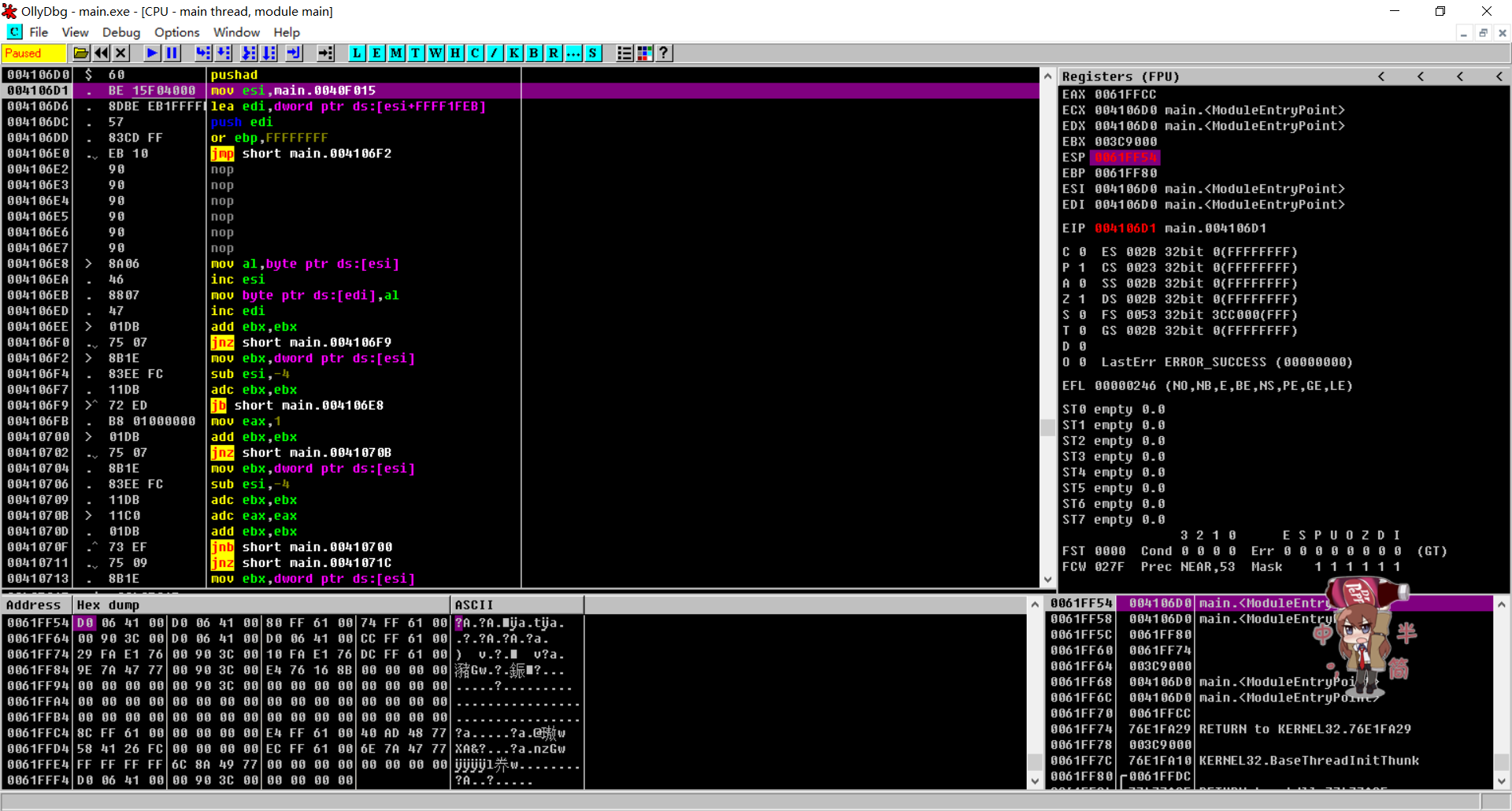
在Hex Dump窗口的第一行第一个字节右键,Breakpoint -> Hardware, on access -> word下硬件断点。
F9直接运行一下程序
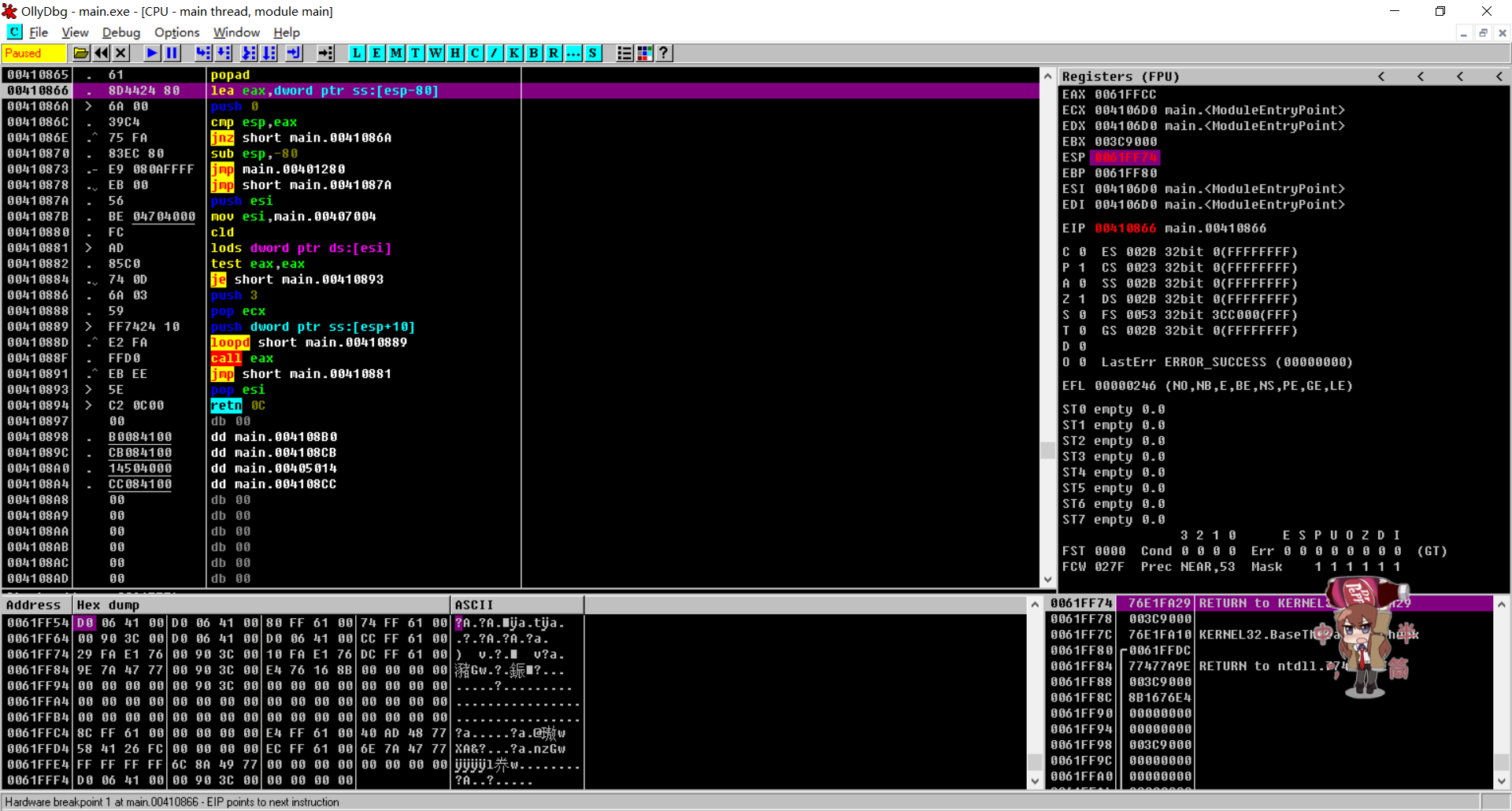
可以看到EIP的上一行有popad,很鲜明的出口特征
现在先在Debug -> Hardware Breakpoint里面把刚刚的断点删了,免得出锅
现在观察代码,看到00410873 .- E9 080AFFFF jmp main.00401280
这显然是步入OEP的操作,直接F7运行到这里面
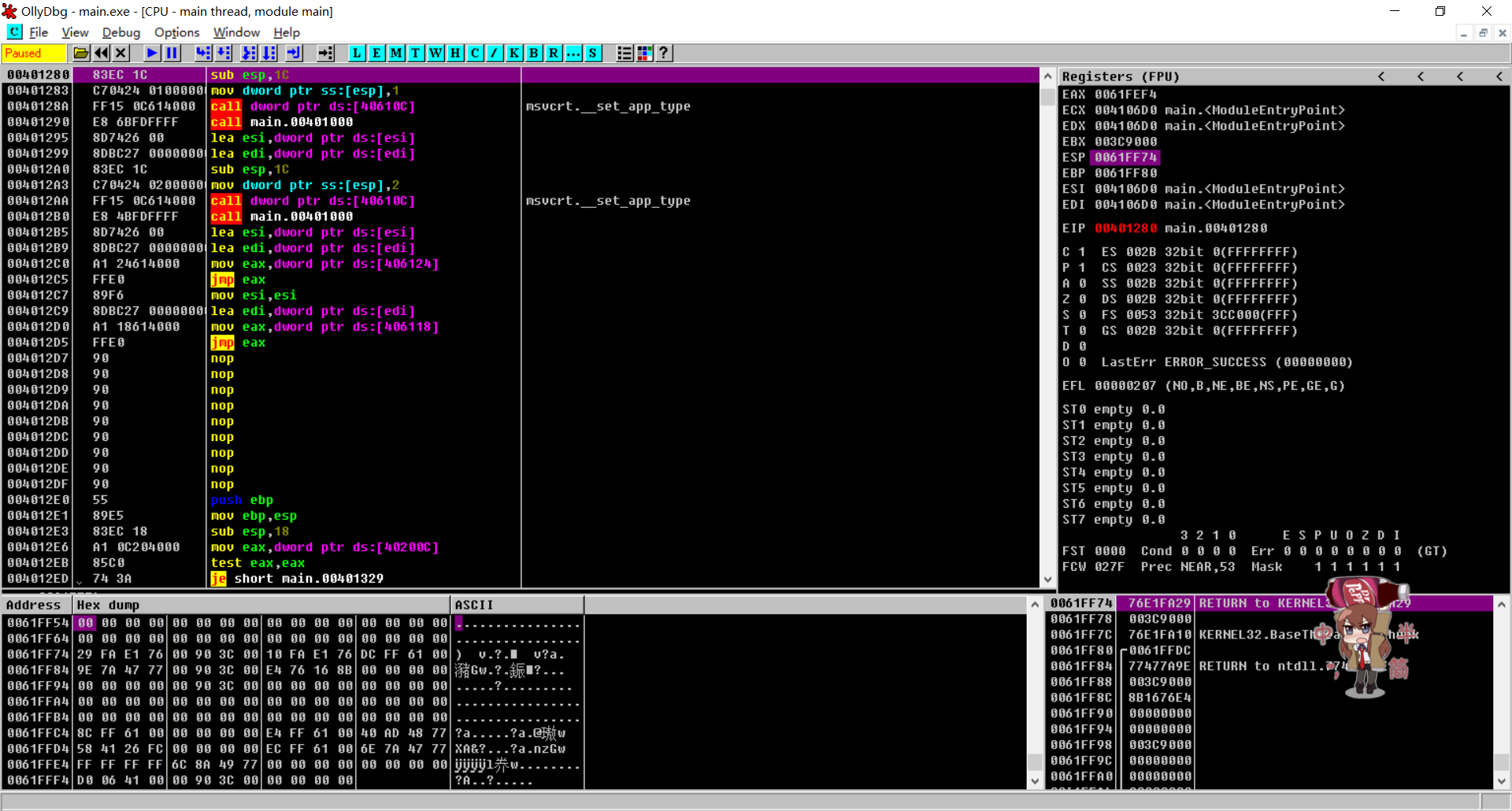
现在打开LordPE,找到我们的程序,右键点纠正镜像大小,然后再右键点完全脱壳
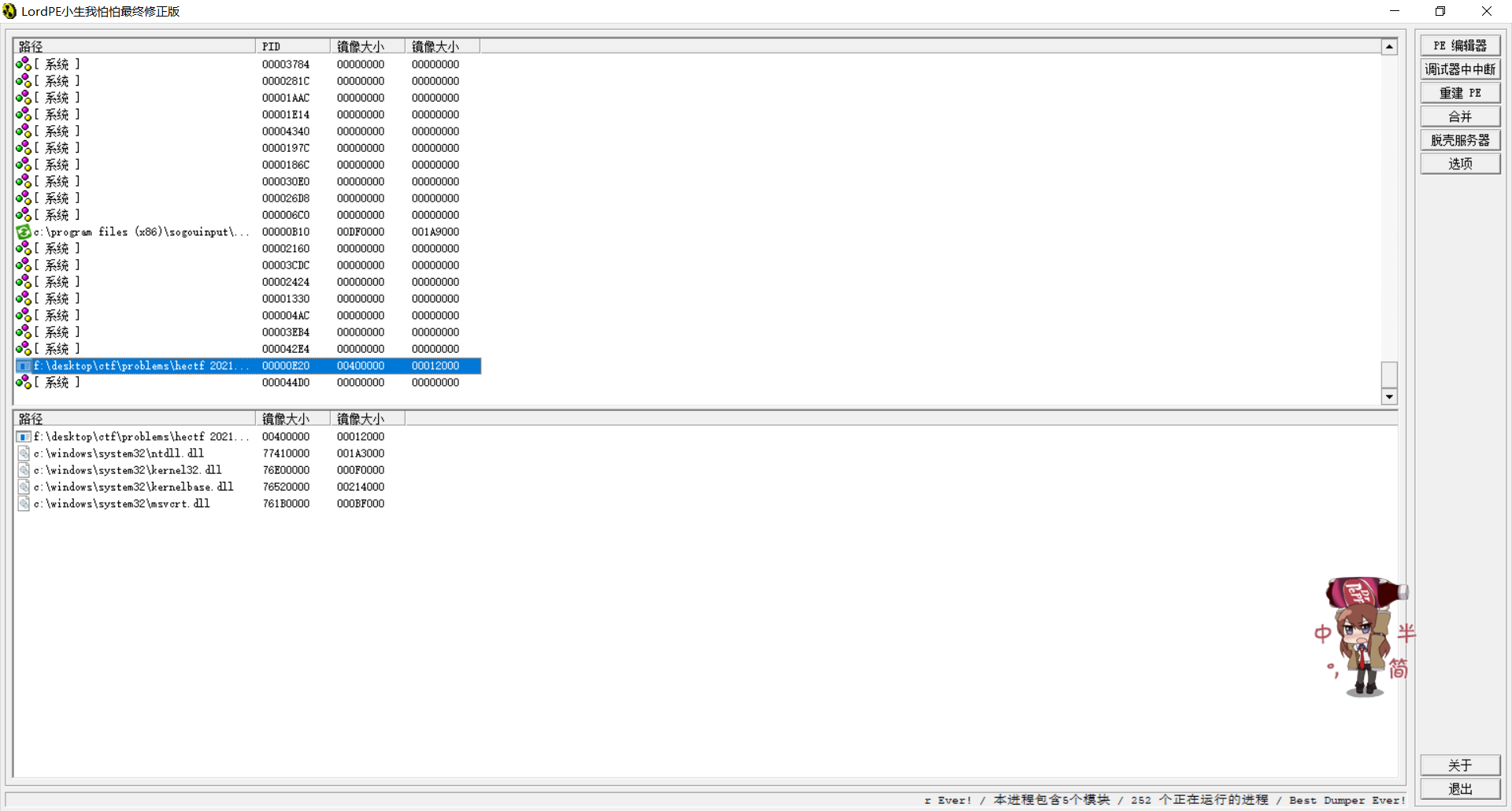
现在拿到了Unpack.exe,但是他是不完整的
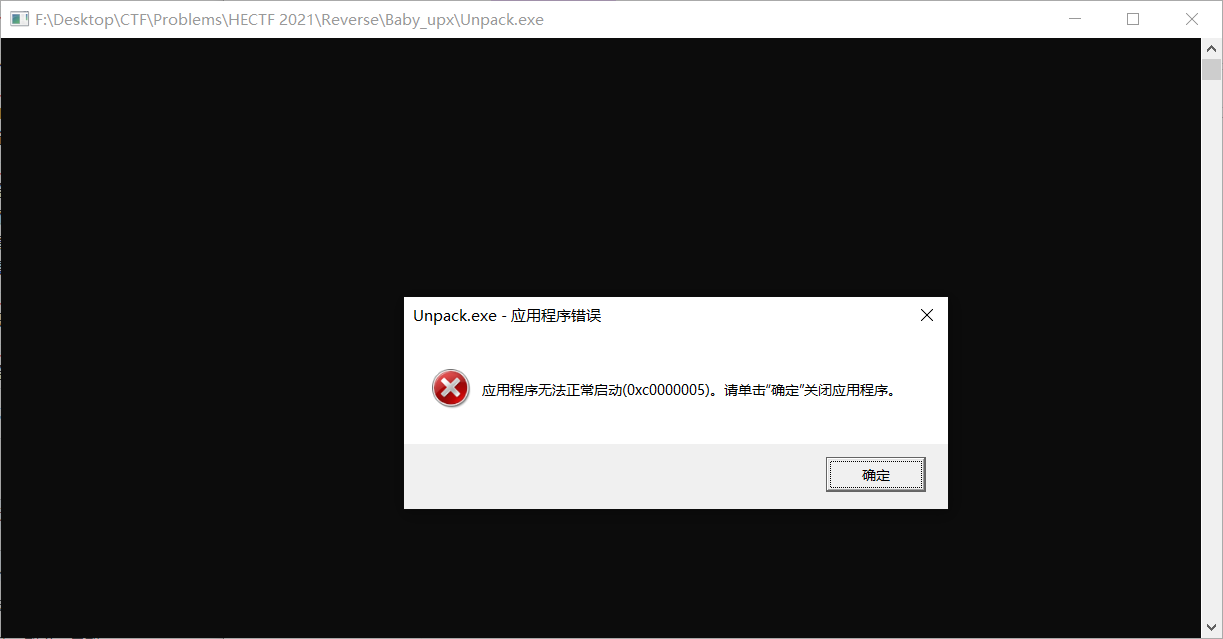
打开ImportREC,找到main.exe(刚刚Ollydbg打开的那玩意,现在还没关)
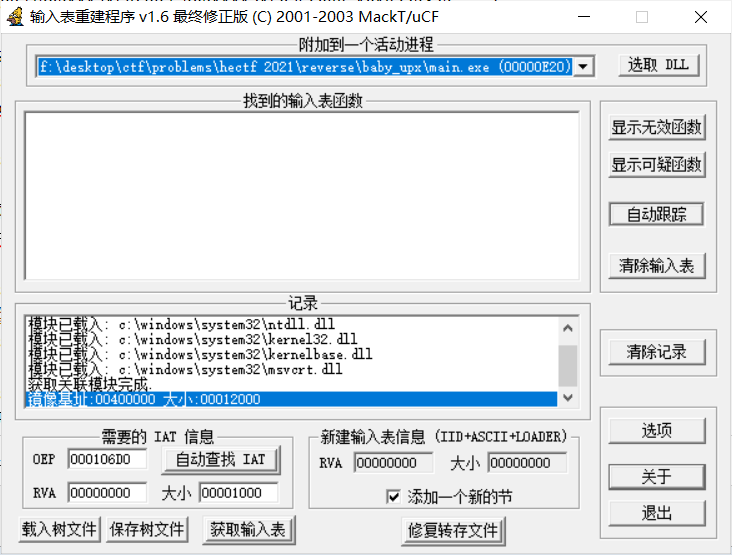
OEP那里写10873(就是前面看到的00410873 .- E9 080AFFFF jmp main.00401280这句话是OEP,只用改偏移量就行,不需要实际地址)
点自动查找IAT,获取输入表,修复转存文件(这里要选Unpack.exe)
修复成功
扔进IDA,发现是v9存加密后的flag(HECTF{}里面那部分),并且rand()是假随机,可以直接预处理出来
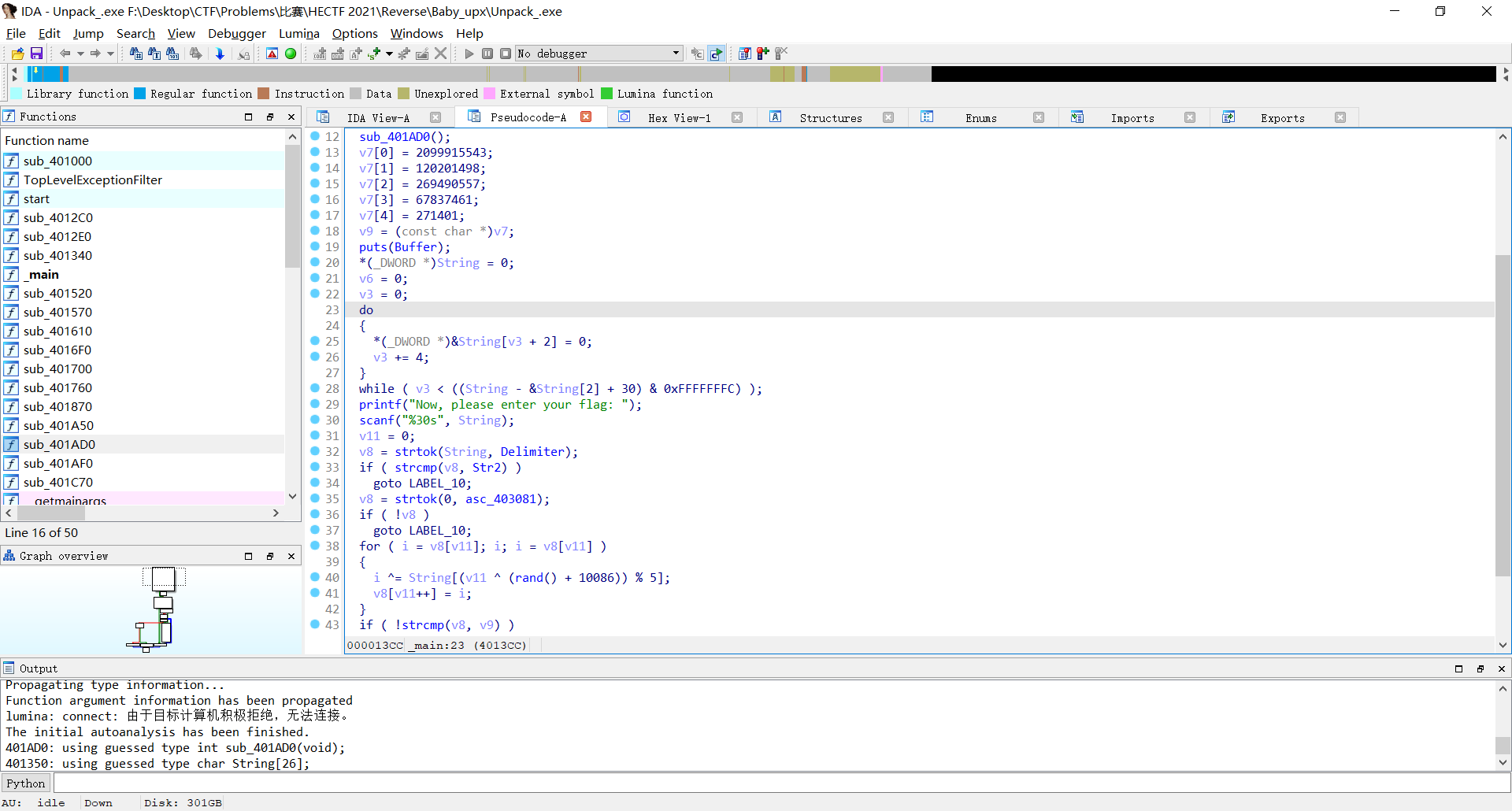
那么写出解密脚本
inline void make_list()
{
for (rg int i = 1; i <= 50; ++i)
{
printf("%d,", rand());
if (!(i % 5)) __endl;
}
}
int rand_list[] = {41,18467,6334,26500,19169,
15724,11478,29358,26962,24464,
5705,28145,23281,16827,9961,
491,2995,11942,4827,5436,
32391,14604,3902,153,292,
12382,17421,18716,19718,19895,
5447,21726,14771,11538,1869,
19912,25667,26299,17035,9894,
28703,23811,31322,30333,17673,
4664,15141,7711,28253,6868};
#define _DWORD unsigned int
unsigned int v7[233];
const char *v9;
char String[26], flag[233];
inline void init()
{
*(_DWORD *)String = 0;
rg int v6 = 0;
_DWORD v3 = 0;
do
{
*(_DWORD *)&String[v3 + 2] = 0;
v3 += 4;
}
while ( v3 < ((String - &String[2] + 30) & 0xFFFFFFFC) );
}
int main()
{
// make_list();
init();
v7[0] = 2099915543;
v7[1] = 120201498;
v7[2] = 269490557;
v7[3] = 67837461;
v7[4] = 271401;
v9 = (const char *)v7;
rg int cnt = 18;
// cout << strlen(v9); // 19
// return 0;
String[0] = 'H';
String[1] = 'E';
String[2] = 'C';
String[3] = 'T';
String[4] = 'F';
String[5] = '{';
for (rg int i = v9[cnt]; cnt >= 0; i = v9[cnt])
{
i ^= String[(cnt ^ (rand_list[cnt] + 10086)) % 5];
flag[cnt--] = i;
}
cout << flag;
// cout << strlen(v9); // 19
return 0;
}
得到flag:
HECTF{Thi5_iiS5_UUPX_LalA}
Baby_pp
exeinfo查一下,发现是pyinstaller打包的
用pyinstxtractor解包后反编译main.pyc
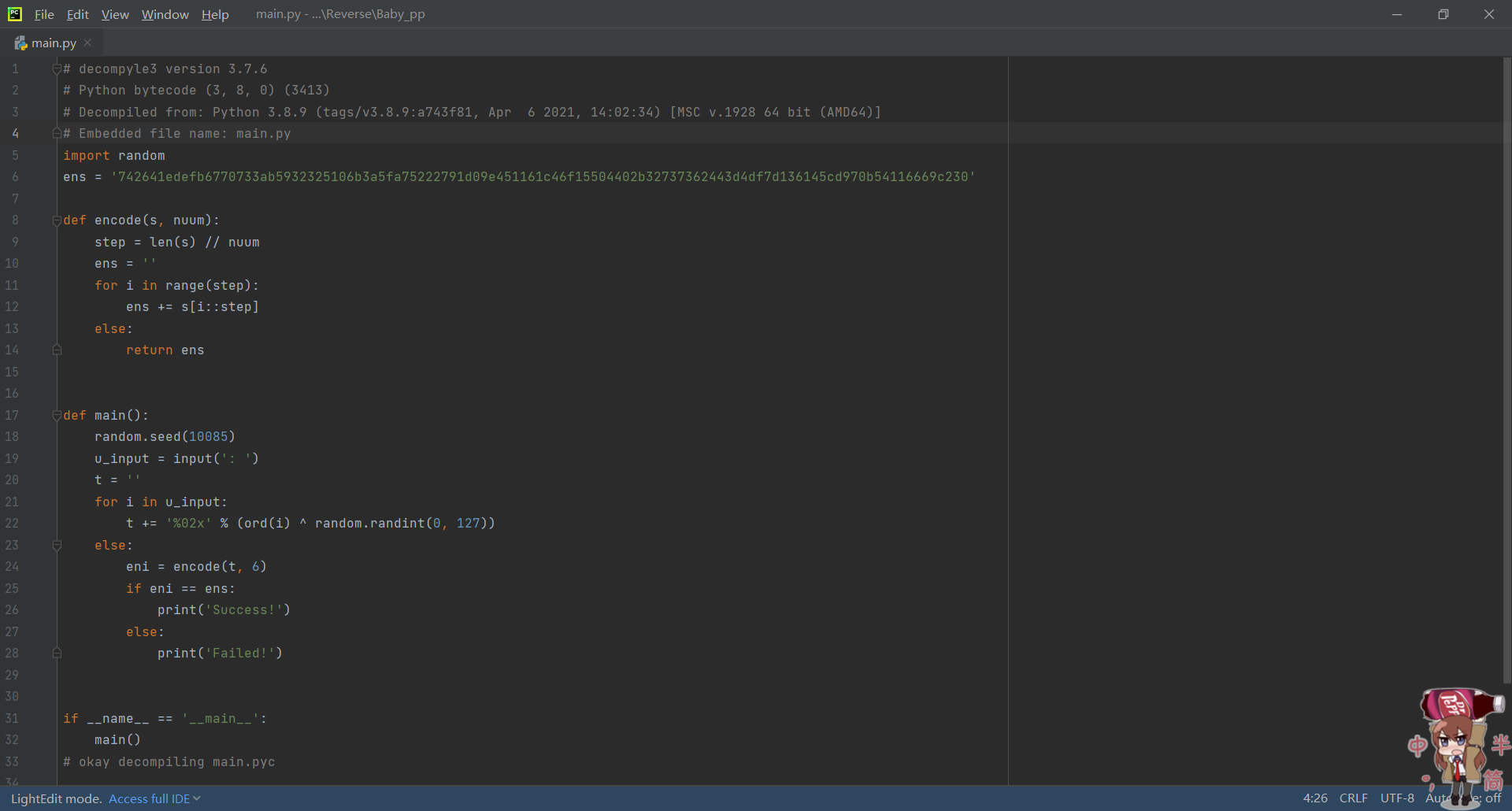
用眼睛瞪发现t是按16进制2个字节2个字节存储的,那么根据eni == ens想办法把t解出来,然后进行异或运算就行了
random是假随机,所以跟着循环跑一次还是那些数,不用管他
(python语法现学的,前面写的c++脚本,发现2个语法的rand用同一个随机化种子居然随机出来不一样。。)
import random
ens = '742641edefb6770733ab5932325106b3a5fa75222791d09e451161c46f15504402b32737362443d4df7d136145cd970b54116669c230'
def trans(a, b):
if (ord(a) >= ord('a')): a = ord(a) - 87
else: a = ord(a) - ord('0')
if (ord(b) >= ord('a')): b = ord(b) - 87
else: b = ord(b) - ord('0')
return a * 16 + b
def main():
step = 18
cnt = 0
enflag = '7e7a3b794c5b3d1c564d7b23515403643d492e055a2d16422d691c6f7915201f474f17124b330f29610347406316326a7e15273d5b60'
flag = ''
# for i in range(step):
# for j in range(i, 108, step):
# enflag[j] = ens[cnt] # t
# cnt = cnt + 1
random.seed(10085)
for i in range(0, 54, 1):
tmp = trans(enflag[2 * i: 2 * i + 1], enflag[2 * i + 1: 2 * i + 2])
flag += chr(tmp ^ random.randint(0, 127))
print(flag)
main()
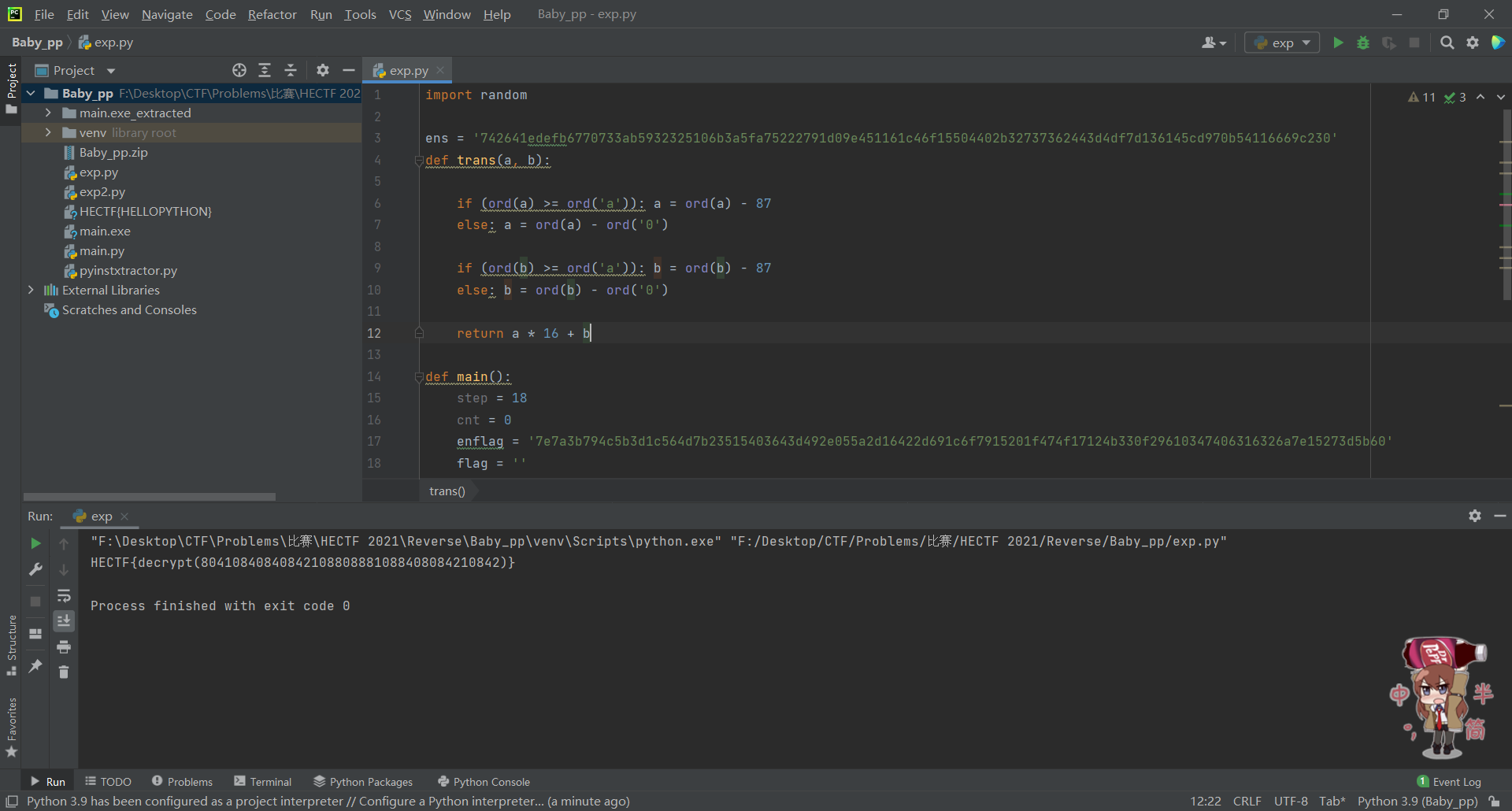
(为什么re题里面还得套个crypto..)
用眼睛瞪decrypt(80410840840842108808881088408084210842),发现只有01248 5个数字,感觉是一种现存的加密方法
www.baidu.com后发现这个玩意叫「云影加密」,直接在网上嫖一份解密脚本
# """
# # @Author : pig
# # @CreatedTime:2019-11-2423:54:02
# # @Description :
# """
def de_code(c):
dic = [chr(i) for i in range(ord("A"), ord("Z") + 1)]
flag = []
c2 = [i for i in c.split("0")]
for i in c2:
c3 = 0
for j in i:
c3 += int(j)
flag.append(dic[c3 - 1])
return flag
def encode(plaintext):
dic = [chr(i) for i in range(ord("A"), ord("Z") + 1)]
m = [i for i in plaintext]
tmp = [];flag = []
for i in range(len(m)):
for j in range(len(dic)):
if m[i] == dic[j]:
tmp.append(j + 1)
for i in tmp:
res = ""
if i >= 8:
res += int(i/8)*"8"
if i%8 >=4:
res += int(i%8/4)*"4"
if i%4 >=2:
res += int(i%4/2)*"2"
if i%2 >= 1:
res += int(i%2/1)*"1"
flag.append(res + "0")
print ("".join(flag)[:-1])
c = input("Input the string you wanna decrypt")
print (de_code(c))
m_code = input("Input the string you wanna encrypt")
encode(m_code)
得到flag:
HECTF{HELLOPYTHON}
Misc
快来公众号ya
微信关注后回复flag后取关
得到flag
HECTF{good_luck_for_you}
JamesHarden
解压后文件扔进010 Editor
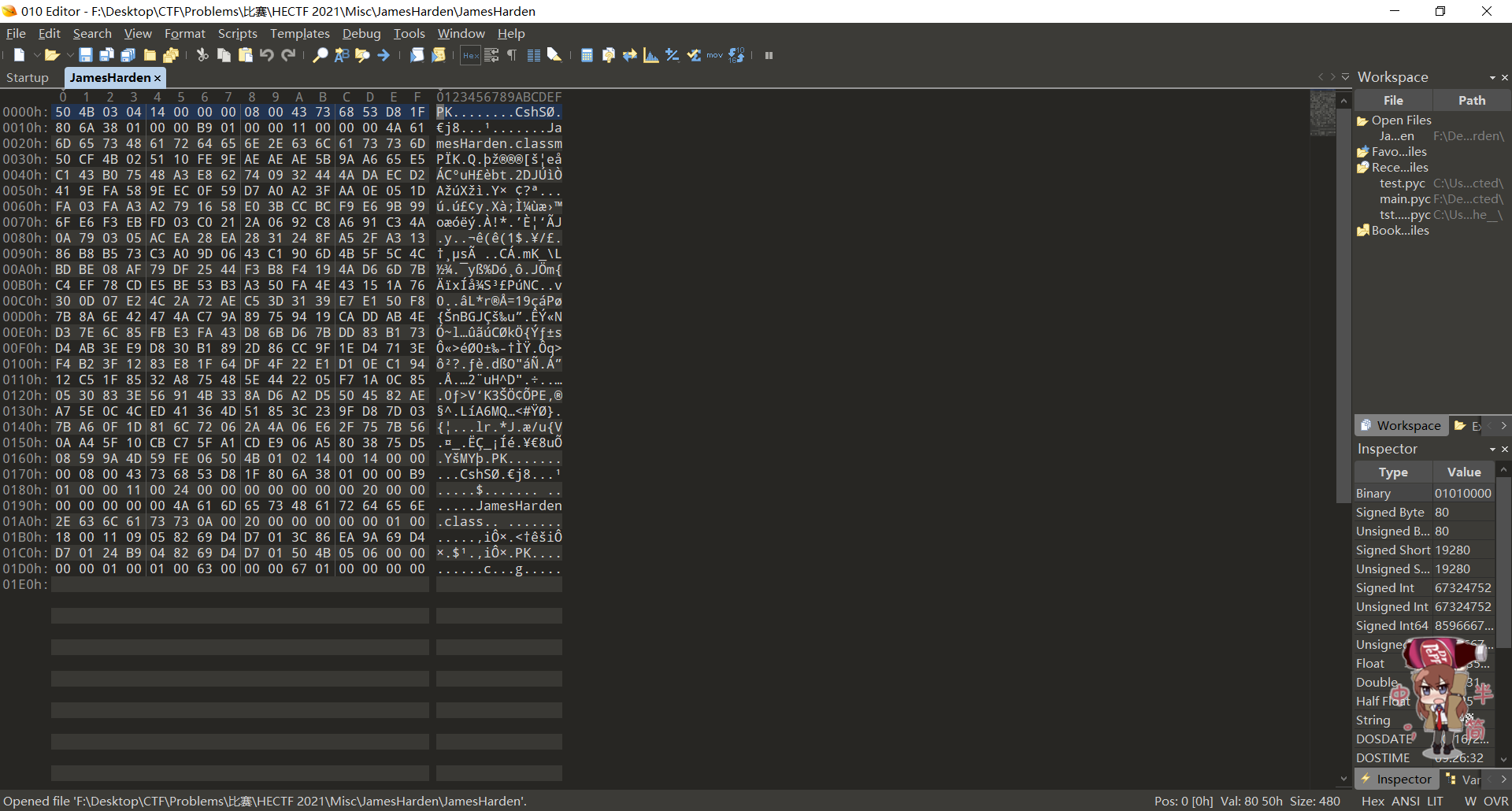
发现是.zip文件头,后缀改一下解压,.class的扔进jd-gui
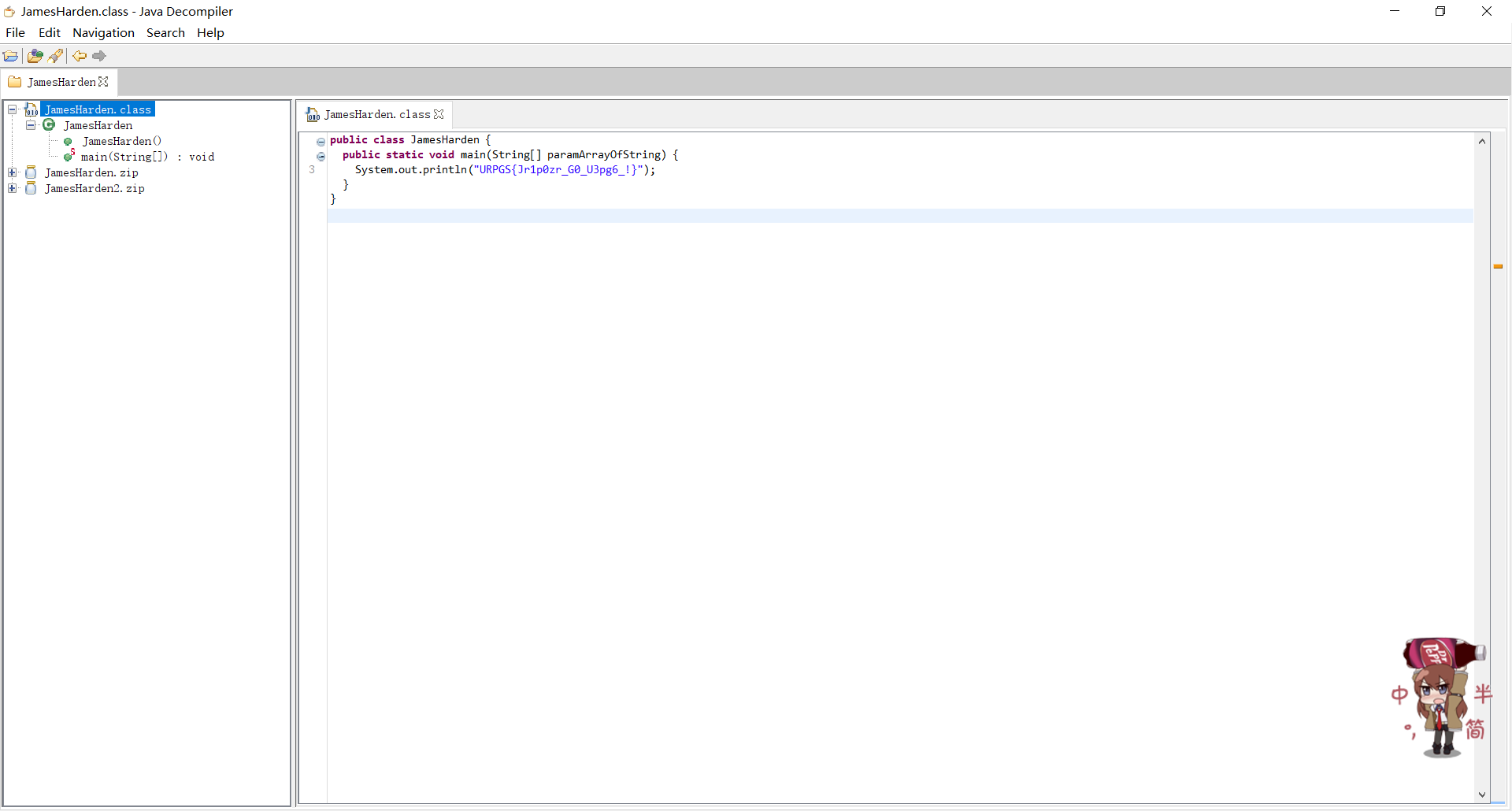
用眼睛瞪后盲猜caiser加密,试到13后得到flag:
HECTF{We1c0me_T0_H3ct6_!}
捉迷藏
和上面那个题一样是个.zip
解压后把document.xml扔进任何一个ide,用眼睛瞪发现是jsfck(我搞出来就一行代码没得截图)
打开浏览器,F12调出控制台,把不是jsfc的全扬了
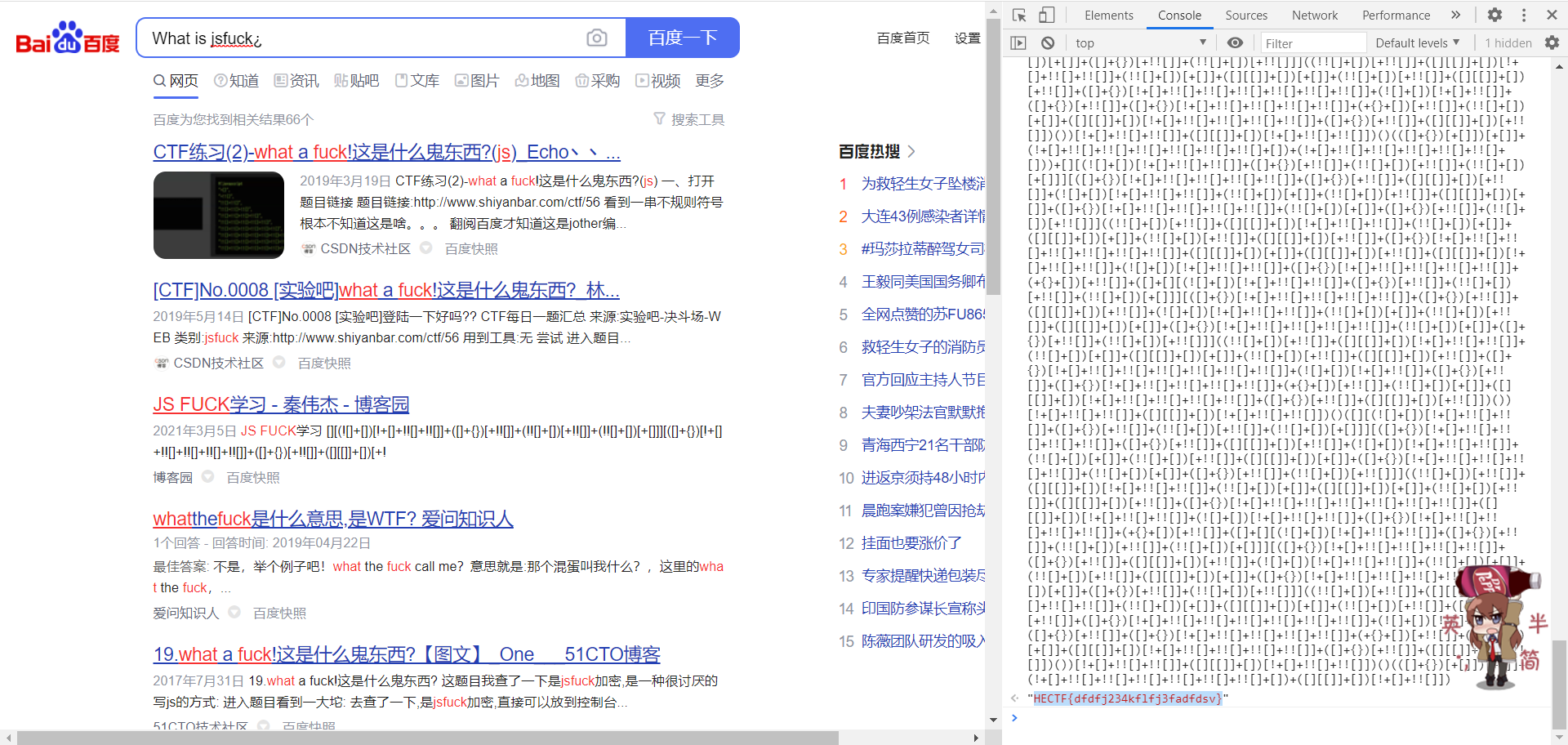
得到flag:
HECTF{dfdfj234kflfj3fadfdsv}

