【THM】Pickle Rick
0x00 信息收集

我们首先进行nmap扫描
┌──(root㉿Breeze)-[/home/breeze/Desktop]
└─# nmap 10.10.130.80 -sS -sV -A -T4
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-20 17:19 CST
Nmap scan report for 10.10.130.80
Host is up (0.33s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 e8:5c:71:68:34:1c:f2:c4:b0:91:28:4e:1f:66:a3:4b (RSA)
| 256 08:94:ca:67:84:3b:a8:a0:5f:70:68:9a:8a:b9:9c:44 (ECDSA)
|_ 256 eb:5f:a9:b6:38:fd:3a:02:c0:5e:eb:85:c8:b6:7d:2b (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Rick is sup4r cool
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.94SVN%E=4%D=5/20%OT=22%CT=1%CU=36559%PV=Y%DS=5%DC=T%G=Y%TM=664B
OS:15ED%P=x86_64-pc-linux-gnu)SEQ(SP=103%GCD=1%ISR=10B%TI=Z%CI=Z%II=I%TS=A)
OS:OPS(O1=M508ST11NW7%O2=M508ST11NW7%O3=M508NNT11NW7%O4=M508ST11NW7%O5=M508
OS:ST11NW7%O6=M508ST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6=FE88)
OS:ECN(R=Y%DF=Y%T=40%W=FAF0%O=M508NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%
OS:F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T
OS:5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=
OS:Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF
OS:=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40
OS:%CD=S)
Network Distance: 5 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 993/tcp)
HOP RTT ADDRESS
1 195.98 ms 10.17.0.1
2 ... 4
5 335.95 ms 10.10.130.80
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 48.20 seconds
并没有什么有用信息
查看web服务,我们看到了这些信息。
note to self, remember username!
Username: R1ckRul3s
我们得到了这个用户名,他可能是ssh登陆,也可能是web后台登陆,我们扫描一下网站目录,来爆破一下。
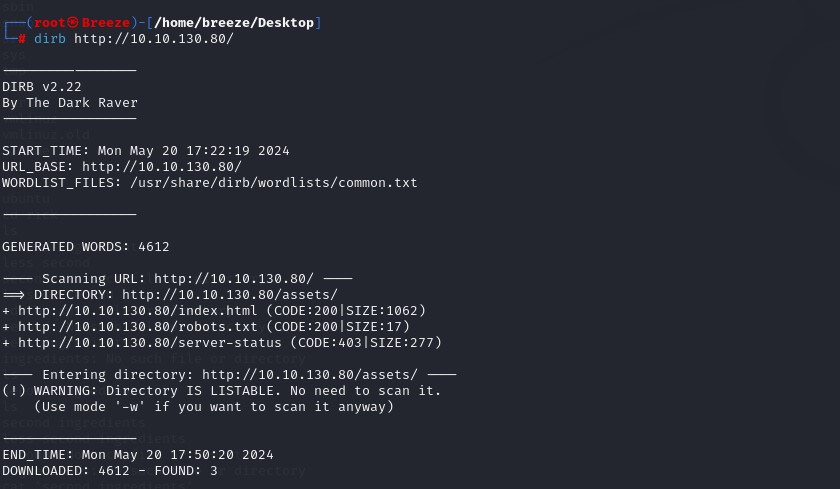
我们用 nikto -h ip来探测一下信息

但是都太慢了。
我们访问一下robots.txt,得到 Wubbalubbadubdub
但是并不知道有啥用。后来发现 后台的密码
命令执行
我们执行which python3,得到了回显,说明有python,我们试试用python反弹shell


我拿到shell后尝试sudo -l提权,发现成功。


 浙公网安备 33010602011771号
浙公网安备 33010602011771号