某乎搜索信息获取(x-zse-96)参数JS逆向破解
网站:aHR0cHM6Ly93d3cuemhpaHUuY29tLw==
1、网页抓包分析,找到返回数据接口与加密参数
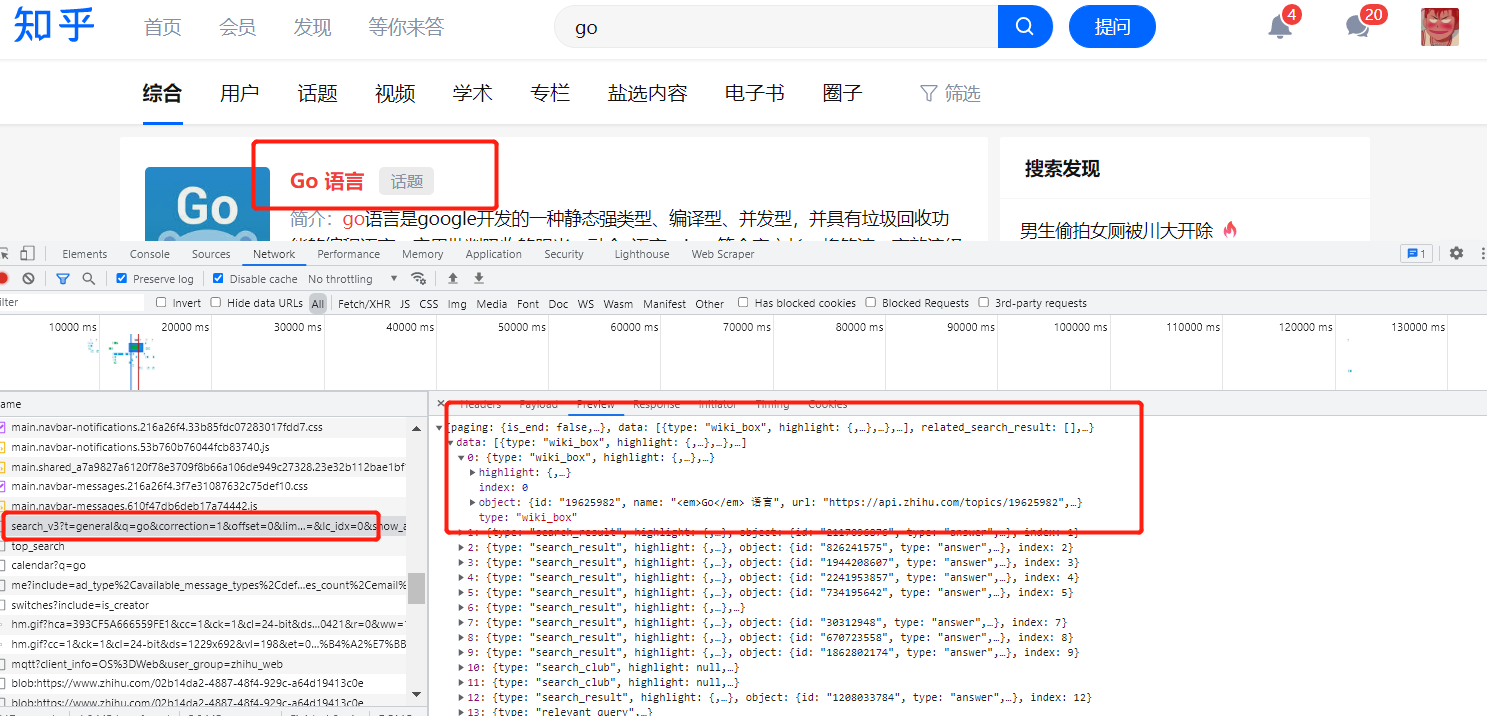
可以看到search_v3这个就是返回参数的接口,复制对应的cURL(base)到postman进行重新请求
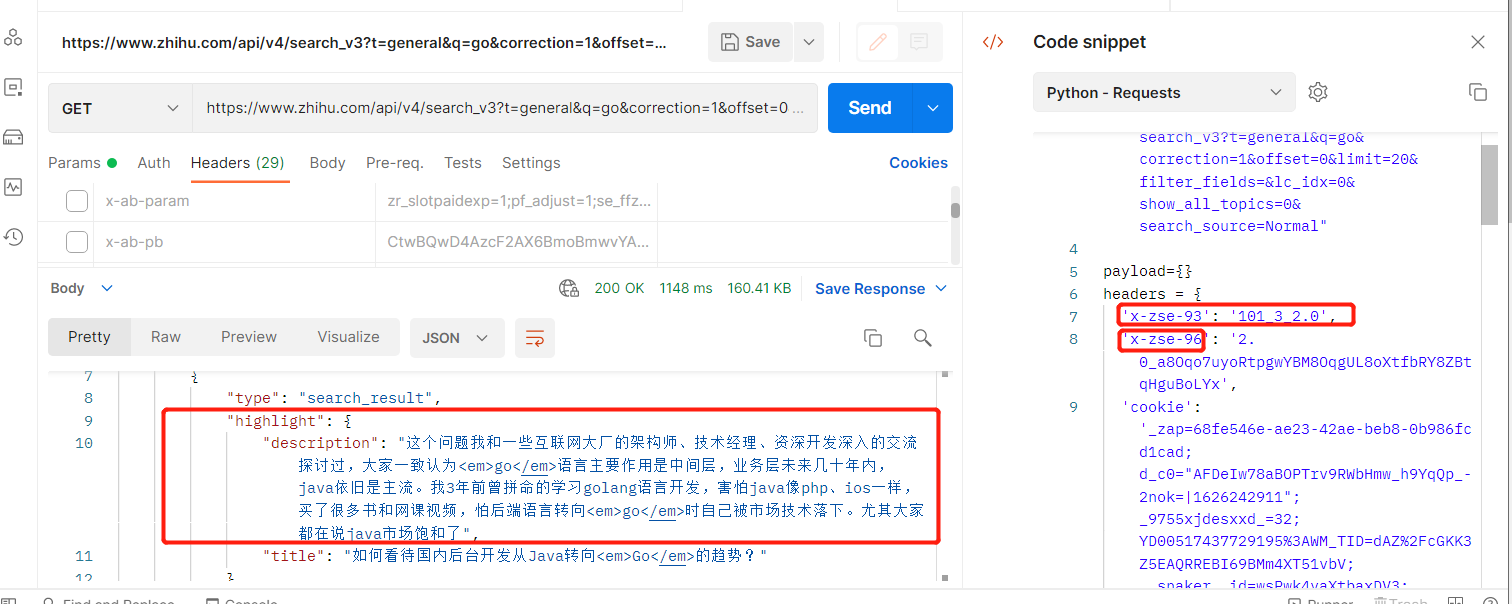
通过重复测试可以知道只需要三个参数就能获取到数据(x-zse-96、x-zse-93、cookie),其中x-zse-93为固定值、cookie为身份认证信息,只有x-zse-96为动态变化,下滑数据也能得到新的请求信息,验证x-zse-96为动态参数
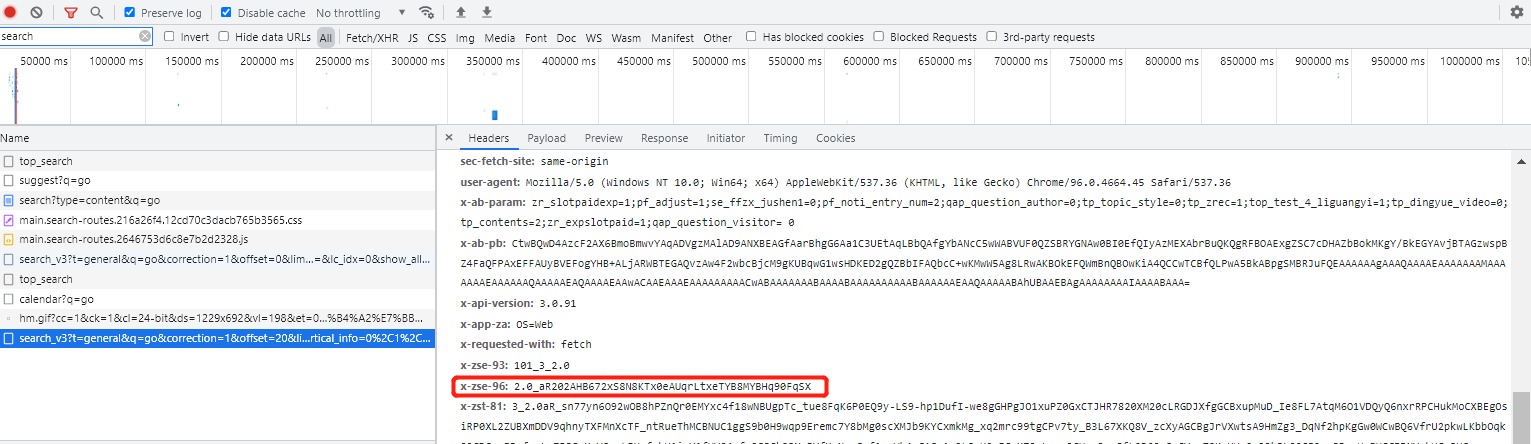
2、加密参数破解
老一套,全局搜索和找堆栈都行,我直接找堆栈,查找到对应的js文件,然后搜索,发现有两个位置有、全部打上断点,刷新页面
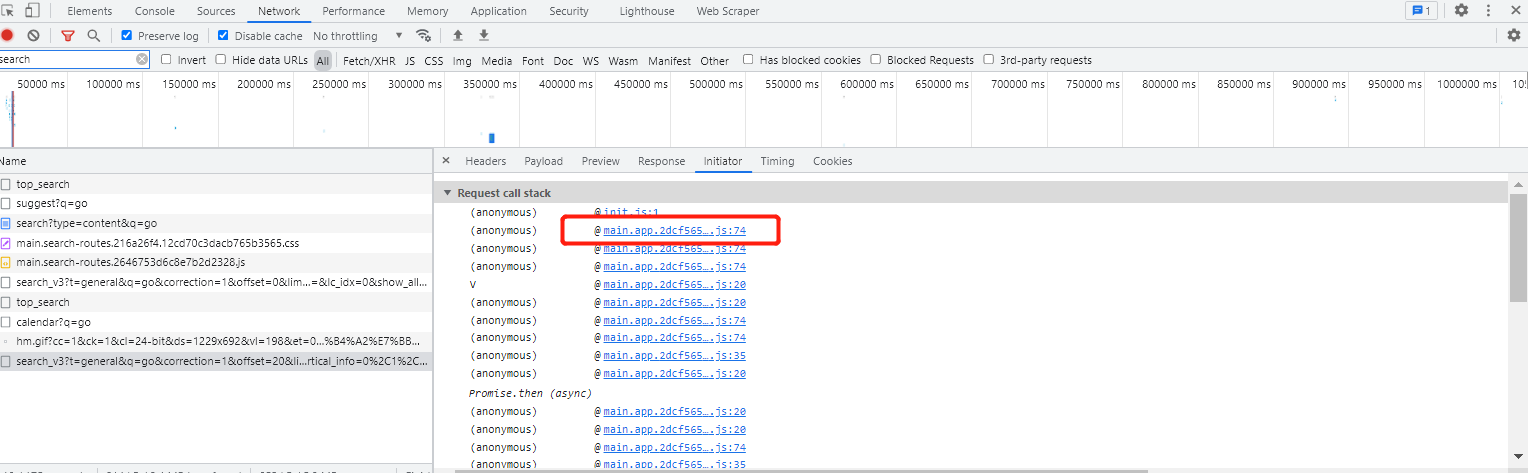
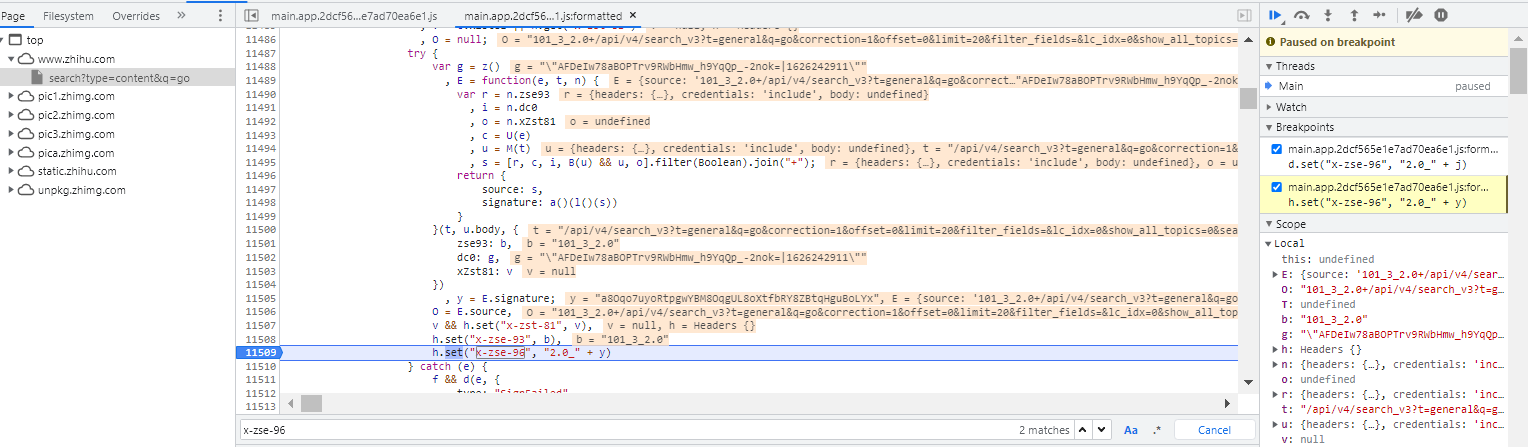
成功在第二个位置被断住,分析参数信息
signature: a()(l()(s))
y = E.signature;
h.set("x-zse-96", "2.0_" + y)
由上可以看出signature <==> x-zse-96、接下来打上断点分析signature的生成
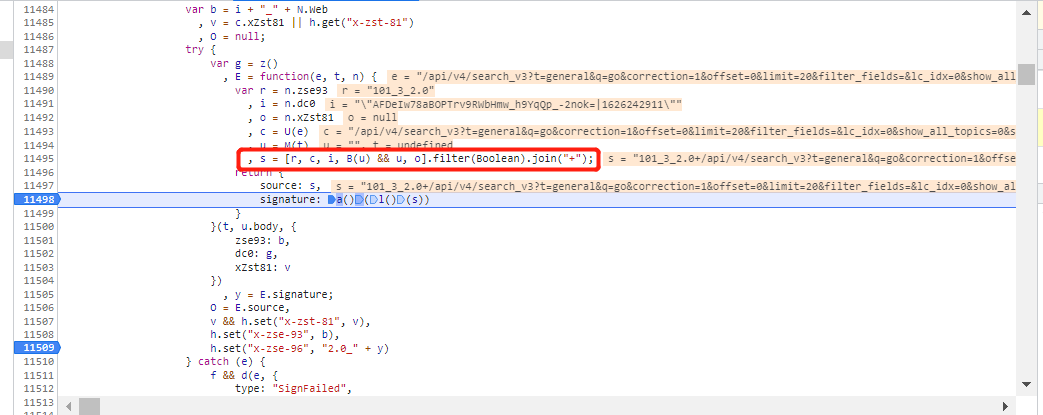
具体为两此加密,先使用l()函数对s加密,然后使用a()函数对第一次加密后的值进行加密,而s的几个参数拼接而来
r: 对应版本
c: 请求url后半断
i: uuid + 时间戳
此处不想扣代码的直接使用,l()函数为md5加密
3、扣代码
记一下s的值:101_3_2.0+/api/v4/search_v3?t=general&q=go&correction=1&offset=0&limit=20&filter_fields=&lc_idx=0&show_all_topics=0&search_source=Normal+"AFDeIw78aBOPTrv9RWbHmw_h9YqQp_-2nok=|1626242911" 方便后面进行比较
进入l()函数,跳到一个新的位置,发现这个函数在一个大函数里面。那么使用全局思想,将整个大函数全扣下来,然后调用中间的函数就行。
var md5 = function(e, t, n) {
var r;
return function(i) {
"use strict";
function o(e, t) {
var n = (65535 & e) + (65535 & t);
return (e >> 16) + (t >> 16) + (n >> 16) << 16 | 65535 & n
}
function a(e, t, n, r, i, a) {
return o((c = o(o(t, e), o(r, a))) << (u = i) | c >>> 32 - u, n);
var c, u
}
function c(e, t, n, r, i, o, c) {
return a(t & n | ~t & r, e, t, i, o, c)
}
function u(e, t, n, r, i, o, c) {
return a(t & r | n & ~r, e, t, i, o, c)
}
function s(e, t, n, r, i, o, c) {
return a(t ^ n ^ r, e, t, i, o, c)
}
function l(e, t, n, r, i, o, c) {
return a(n ^ (t | ~r), e, t, i, o, c)
}
function d(e, t) {
var n, r, i, a, d;
e[t >> 5] |= 128 << t % 32,
e[14 + (t + 64 >>> 9 << 4)] = t;
var f = 1732584193
, p = -271733879
, h = -1732584194
, b = 271733878;
for (n = 0; n < e.length; n += 16)
r = f,
i = p,
a = h,
d = b,
f = c(f, p, h, b, e[n], 7, -680876936),
b = c(b, f, p, h, e[n + 1], 12, -389564586),
h = c(h, b, f, p, e[n + 2], 17, 606105819),
p = c(p, h, b, f, e[n + 3], 22, -1044525330),
f = c(f, p, h, b, e[n + 4], 7, -176418897),
b = c(b, f, p, h, e[n + 5], 12, 1200080426),
h = c(h, b, f, p, e[n + 6], 17, -1473231341),
p = c(p, h, b, f, e[n + 7], 22, -45705983),
f = c(f, p, h, b, e[n + 8], 7, 1770035416),
b = c(b, f, p, h, e[n + 9], 12, -1958414417),
h = c(h, b, f, p, e[n + 10], 17, -42063),
p = c(p, h, b, f, e[n + 11], 22, -1990404162),
f = c(f, p, h, b, e[n + 12], 7, 1804603682),
b = c(b, f, p, h, e[n + 13], 12, -40341101),
h = c(h, b, f, p, e[n + 14], 17, -1502002290),
f = u(f, p = c(p, h, b, f, e[n + 15], 22, 1236535329), h, b, e[n + 1], 5, -165796510),
b = u(b, f, p, h, e[n + 6], 9, -1069501632),
h = u(h, b, f, p, e[n + 11], 14, 643717713),
p = u(p, h, b, f, e[n], 20, -373897302),
f = u(f, p, h, b, e[n + 5], 5, -701558691),
b = u(b, f, p, h, e[n + 10], 9, 38016083),
h = u(h, b, f, p, e[n + 15], 14, -660478335),
p = u(p, h, b, f, e[n + 4], 20, -405537848),
f = u(f, p, h, b, e[n + 9], 5, 568446438),
b = u(b, f, p, h, e[n + 14], 9, -1019803690),
h = u(h, b, f, p, e[n + 3], 14, -187363961),
p = u(p, h, b, f, e[n + 8], 20, 1163531501),
f = u(f, p, h, b, e[n + 13], 5, -1444681467),
b = u(b, f, p, h, e[n + 2], 9, -51403784),
h = u(h, b, f, p, e[n + 7], 14, 1735328473),
f = s(f, p = u(p, h, b, f, e[n + 12], 20, -1926607734), h, b, e[n + 5], 4, -378558),
b = s(b, f, p, h, e[n + 8], 11, -2022574463),
h = s(h, b, f, p, e[n + 11], 16, 1839030562),
p = s(p, h, b, f, e[n + 14], 23, -35309556),
f = s(f, p, h, b, e[n + 1], 4, -1530992060),
b = s(b, f, p, h, e[n + 4], 11, 1272893353),
h = s(h, b, f, p, e[n + 7], 16, -155497632),
p = s(p, h, b, f, e[n + 10], 23, -1094730640),
f = s(f, p, h, b, e[n + 13], 4, 681279174),
b = s(b, f, p, h, e[n], 11, -358537222),
h = s(h, b, f, p, e[n + 3], 16, -722521979),
p = s(p, h, b, f, e[n + 6], 23, 76029189),
f = s(f, p, h, b, e[n + 9], 4, -640364487),
b = s(b, f, p, h, e[n + 12], 11, -421815835),
h = s(h, b, f, p, e[n + 15], 16, 530742520),
f = l(f, p = s(p, h, b, f, e[n + 2], 23, -995338651), h, b, e[n], 6, -198630844),
b = l(b, f, p, h, e[n + 7], 10, 1126891415),
h = l(h, b, f, p, e[n + 14], 15, -1416354905),
p = l(p, h, b, f, e[n + 5], 21, -57434055),
f = l(f, p, h, b, e[n + 12], 6, 1700485571),
b = l(b, f, p, h, e[n + 3], 10, -1894986606),
h = l(h, b, f, p, e[n + 10], 15, -1051523),
p = l(p, h, b, f, e[n + 1], 21, -2054922799),
f = l(f, p, h, b, e[n + 8], 6, 1873313359),
b = l(b, f, p, h, e[n + 15], 10, -30611744),
h = l(h, b, f, p, e[n + 6], 15, -1560198380),
p = l(p, h, b, f, e[n + 13], 21, 1309151649),
f = l(f, p, h, b, e[n + 4], 6, -145523070),
b = l(b, f, p, h, e[n + 11], 10, -1120210379),
h = l(h, b, f, p, e[n + 2], 15, 718787259),
p = l(p, h, b, f, e[n + 9], 21, -343485551),
f = o(f, r),
p = o(p, i),
h = o(h, a),
b = o(b, d);
return [f, p, h, b]
}
function f(e) {
var t, n = "", r = 32 * e.length;
for (t = 0; t < r; t += 8)
n += String.fromCharCode(e[t >> 5] >>> t % 32 & 255);
return n
}
function p(e) {
var t, n = [];
for (n[(e.length >> 2) - 1] = void 0,
t = 0; t < n.length; t += 1)
n[t] = 0;
var r = 8 * e.length;
for (t = 0; t < r; t += 8)
n[t >> 5] |= (255 & e.charCodeAt(t / 8)) << t % 32;
return n
}
function h(e) {
var t, n, r = "";
for (n = 0; n < e.length; n += 1)
t = e.charCodeAt(n),
r += "0123456789abcdef".charAt(t >>> 4 & 15) + "0123456789abcdef".charAt(15 & t);
return r
}
function b(e) {
return unescape(encodeURIComponent(e))
}
function v(e) {
return function(e) {
return f(d(p(e), 8 * e.length))
}(b(e))
}
function O(e, t) {
return function(e, t) {
var n, r, i = p(e), o = [], a = [];
for (o[15] = a[15] = void 0,
i.length > 16 && (i = d(i, 8 * e.length)),
n = 0; n < 16; n += 1)
o[n] = 909522486 ^ i[n],
a[n] = 1549556828 ^ i[n];
return r = d(o.concat(p(t)), 512 + 8 * t.length),
f(d(a.concat(r), 640))
}(b(e), b(t))
}
function g(e, t, n) {
return t ? n ? O(t, e) : h(O(t, e)) : n ? v(e) : h(v(e))
}
return g
/*
void 0 === (r = function() {
return g
}
.call(t, n, t, e)) || (e.exports = r)
*/
}()
}
测试一下:

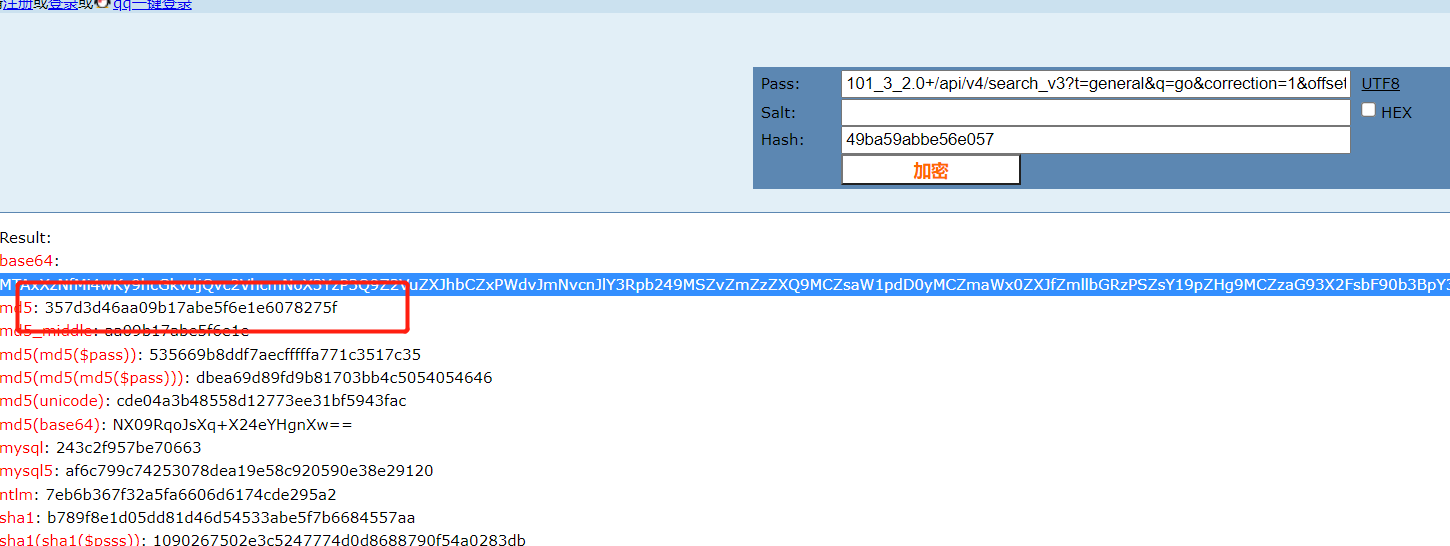
可以看到确实为md5加密,接下来分析a()函数,同理也是全局思想
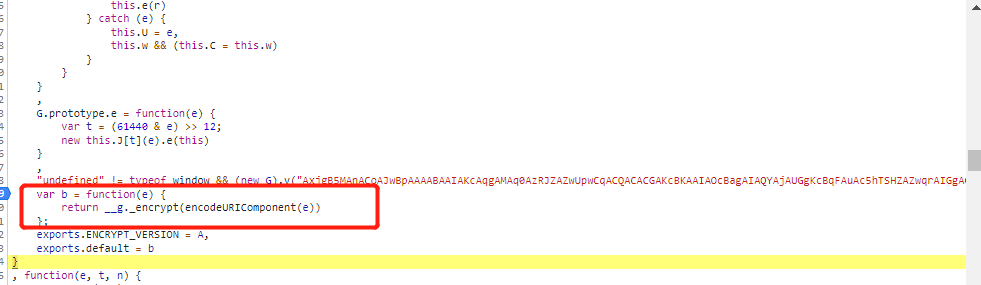
此处比较重要的一点是此函数需要进行参数的传入
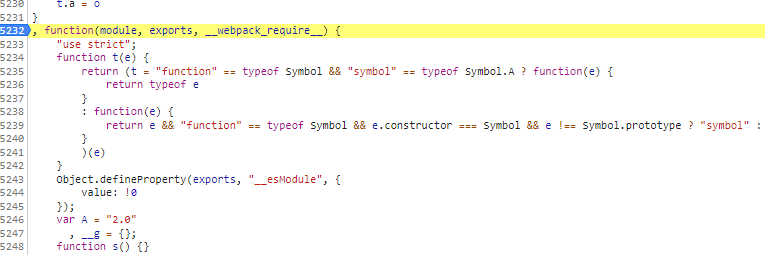
可以看到此函数是这个样子的,打上断点分析参数,将参数传进去
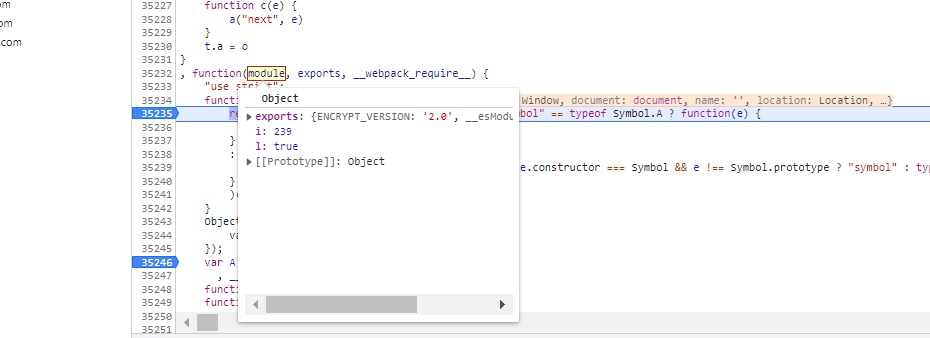
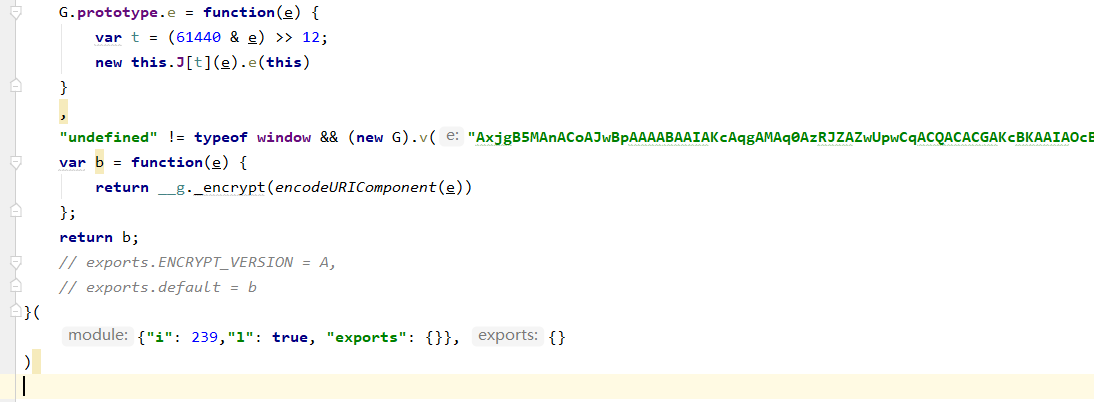
加密看下效果:
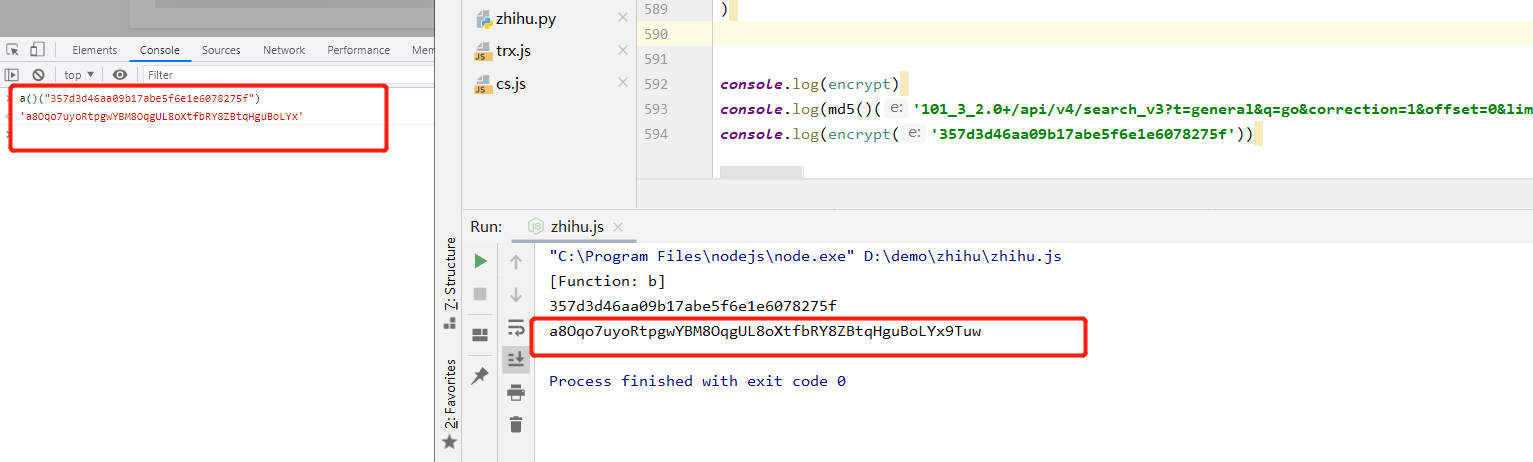
一致,完成。
结果:
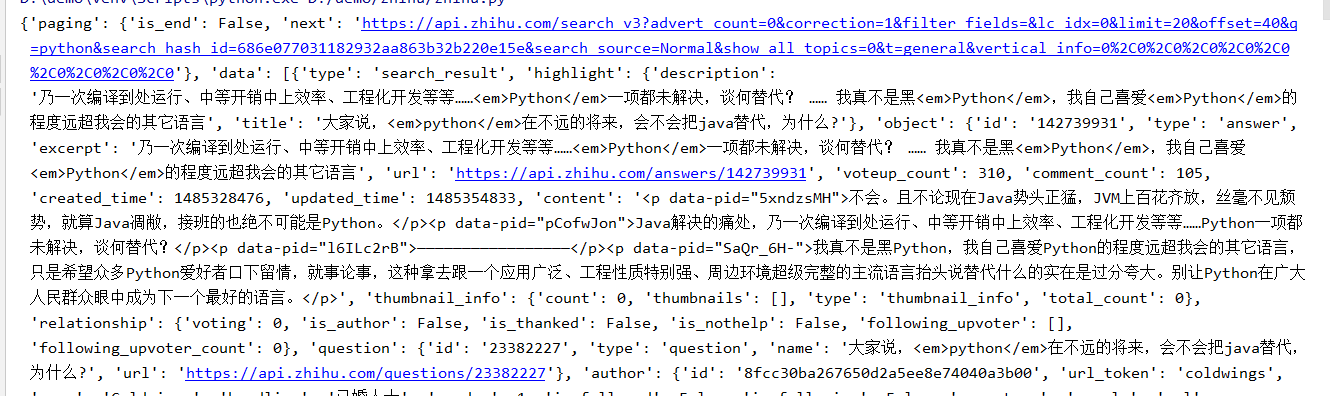
总结
全局思想,对于很多函数内部函数,很不好扣,或者说一扣起来就得扣半天,此时使用全局思想就好很多


 浙公网安备 33010602011771号
浙公网安备 33010602011771号