DASCTF 2022.10 部分re wp
就做了俩
re
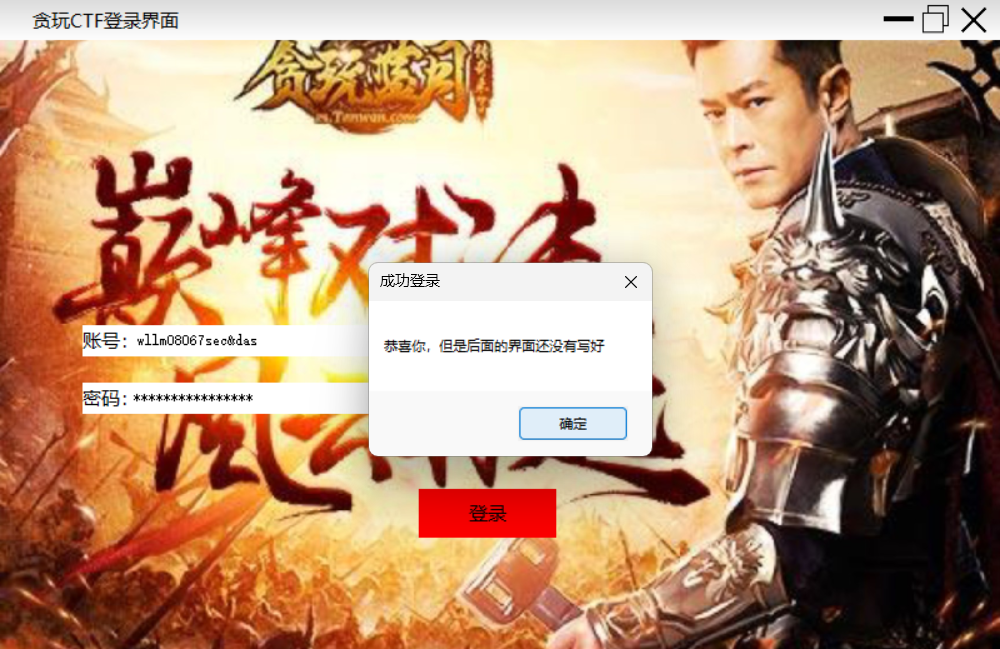
贪玩ctf
winmain!
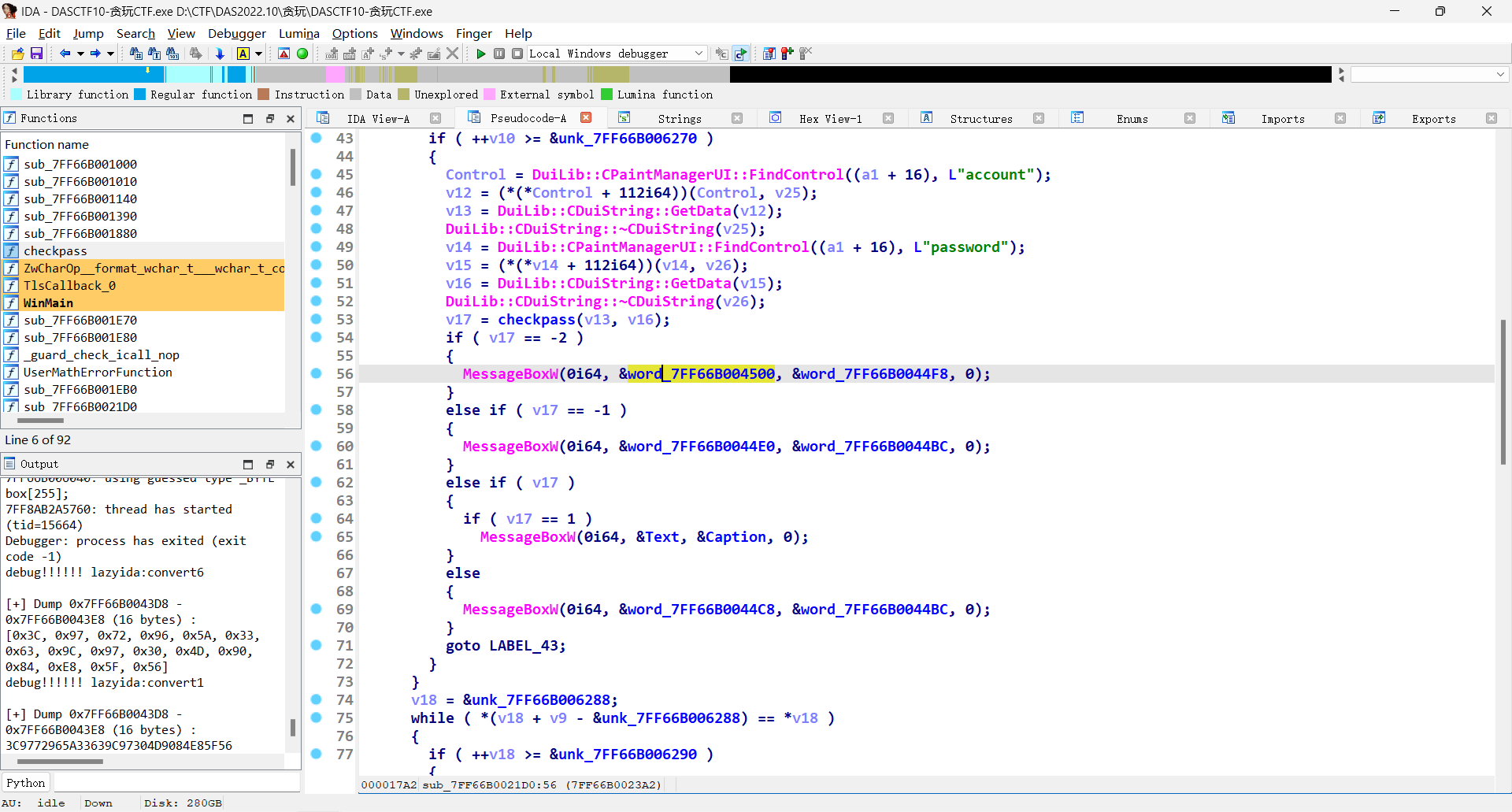
随便测试输入知道有弹窗
x64dbg直接为messbox下断
查找调用找到
这为checkpassword和account的函数
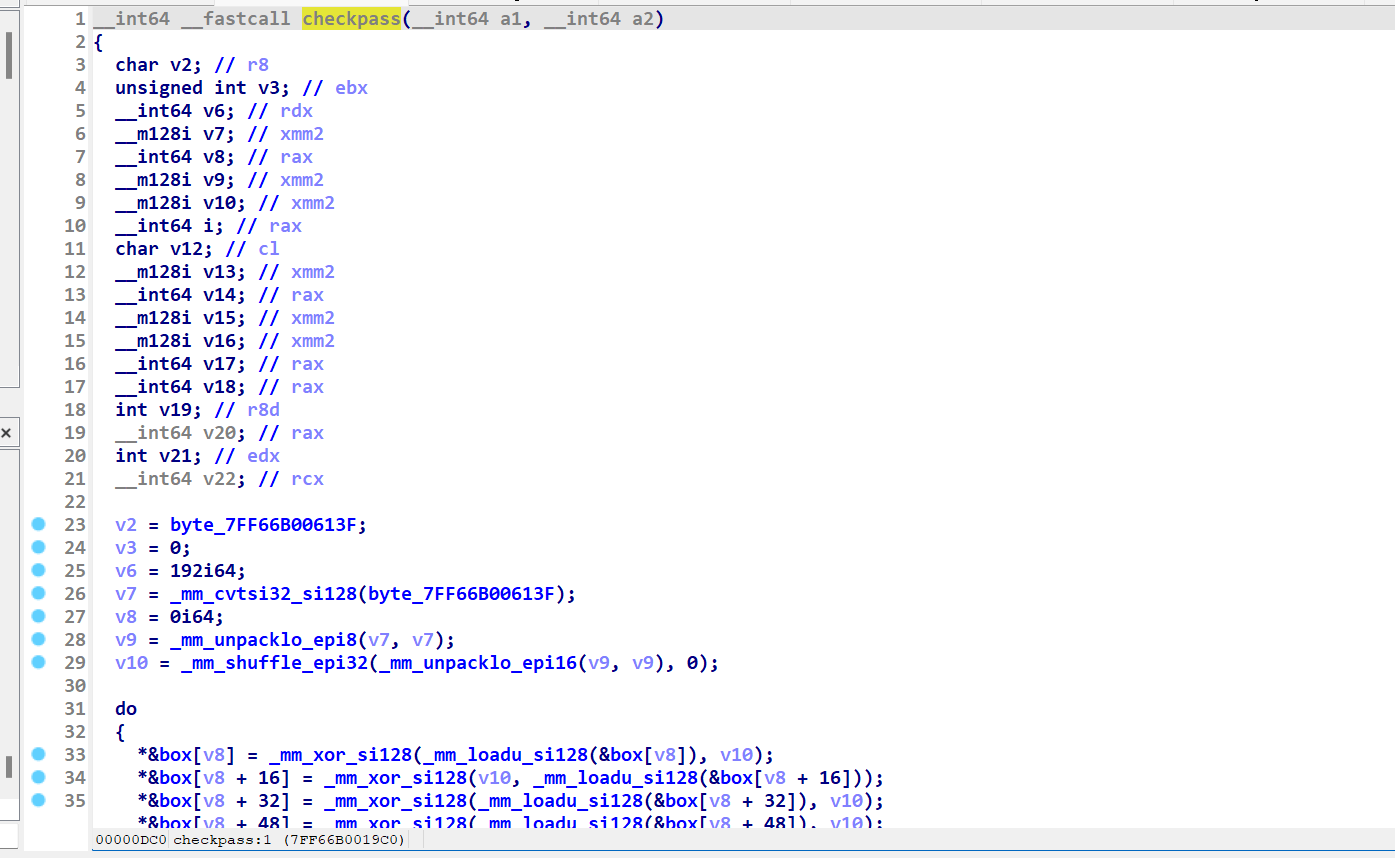
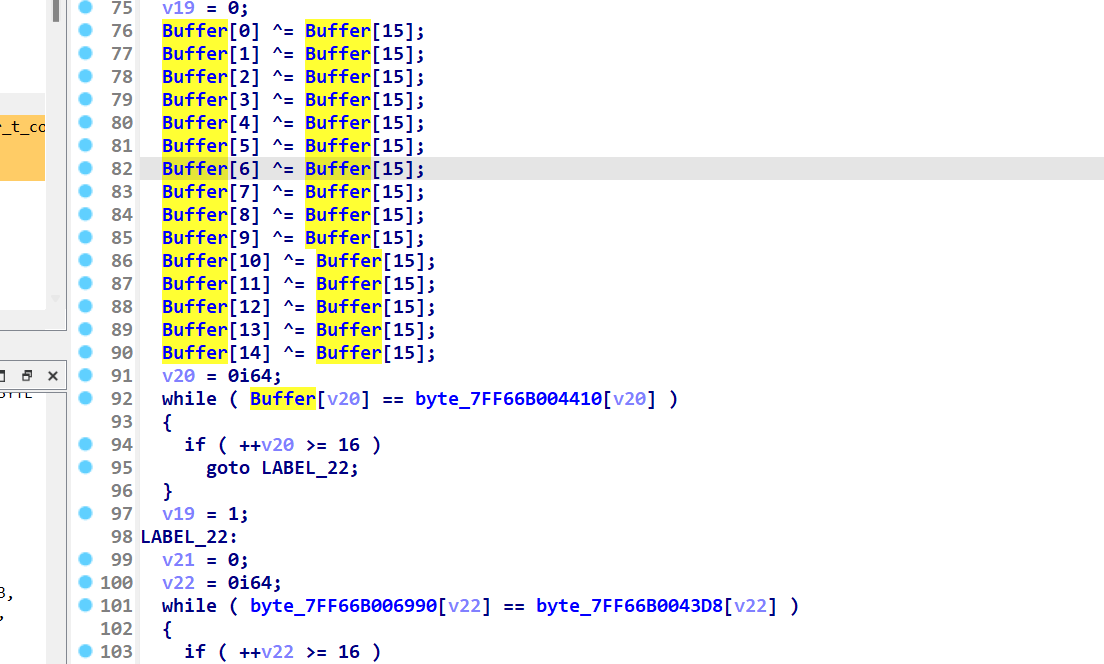
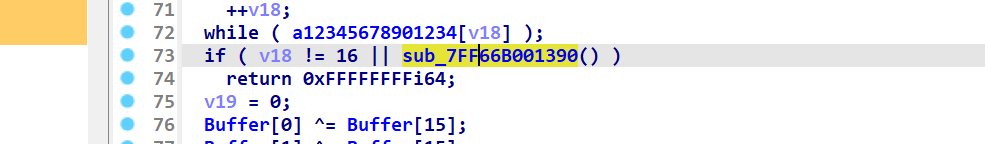
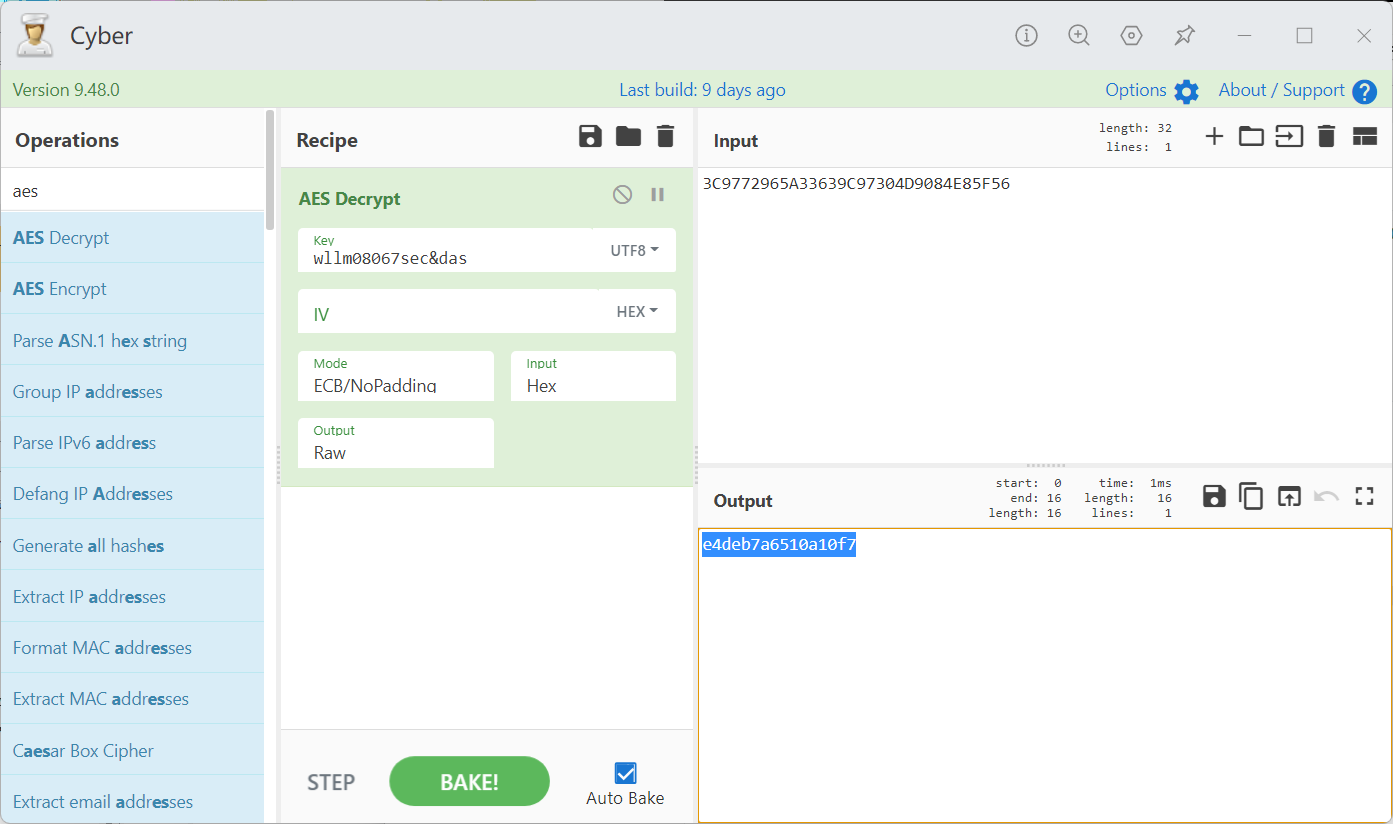
两个比较 上面为直接异或的加密过程
a=[0x04, 0x1F, 0x1F, 0x1E, 0x43, 0x4B, 0x43, 0x45, 0x44, 0x00, 0x16, 0x10, 0x55, 0x17, 0x12, 0x73]
for x in range(15):
a[x]^=a[15]
for x in a:
print(chr(x),end="")
解出
wllm08067sec&das
该函数加密 且调用了账号
有box盒 盲猜aes
即可
pycode
字节码逆向 读就行
使用python -m dis 1.py
来获得字节码
大致复原的逻辑
from Crypto.Util import number
def extract_number(x):
x = x ^ (x >> 11)
x = x ^ ((x << 7) & 2022072721)
x = x ^ ((x << 15) & 2323163360)
x = x ^ (x >> 18)
return x
def transform(m):
new_message = b''
l = len(m)
print(m)
for i in range(l):
enc = m[i * 4:i * 4 + 4]
enc = number.bytes_to_long(enc)
enc = extract_number(enc)
enc = number.long_to_bytes(enc, 4)
new_message += enc
print(new_message)
return number.bytes_to_long(new_message)
if __name__ == '__main__':
num = input('input your number:')
tmp = bytes.fromhex(num)
res = hex(transform(tmp))
print(res)
enc = '8b2e4e85 8126bc84 78d6a6a4 85215f03'
if enc == res:
print(num)
else:
print("wrong")
#flag=8b2e4e858126bc8478d6a6a485215f03
使用z3一把梭 四段分别约束即可
def extract_number(x):
x = x ^ (x >> 11)
x = x ^ ((x << 7) & 2022072721)
x = x ^ ((x << 15) & 2323163360)
x = x ^ (x >> 18)
return x
from Crypto.Util import number
from z3 import *
inp = BitVec("inp", 64)
a=extract_number(inp)
print(a)
s=Solver()
s.add(a==0x85215f03)
s.add(inp<=0xffffffff)
s.add(inp>=0)
print(s.check())
r=s.model()
print(r)
print(hex(r[inp].as_long()))
作者:FW-ltlly
出处:https://www.cnblogs.com/FW-ltlly/p/16895893.html
版权:本作品采用「署名-非商业性使用-相同方式共享 4.0 国际」许可协议进行许可。



【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· TypeScript + Deepseek 打造卜卦网站:技术与玄学的结合
· Manus的开源复刻OpenManus初探
· AI 智能体引爆开源社区「GitHub 热点速览」
· 三行代码完成国际化适配,妙~啊~
· .NET Core 中如何实现缓存的预热?