巅峰极客obf
re
ObfPuzz
先起docker
按get传参flag即可
docker file中
CMD [ "php", "-d", "extension=ctf.so", "-S", "0.0.0.0:1447" ]
指php载入拓展 直接分析so
大概是重载了vardump?
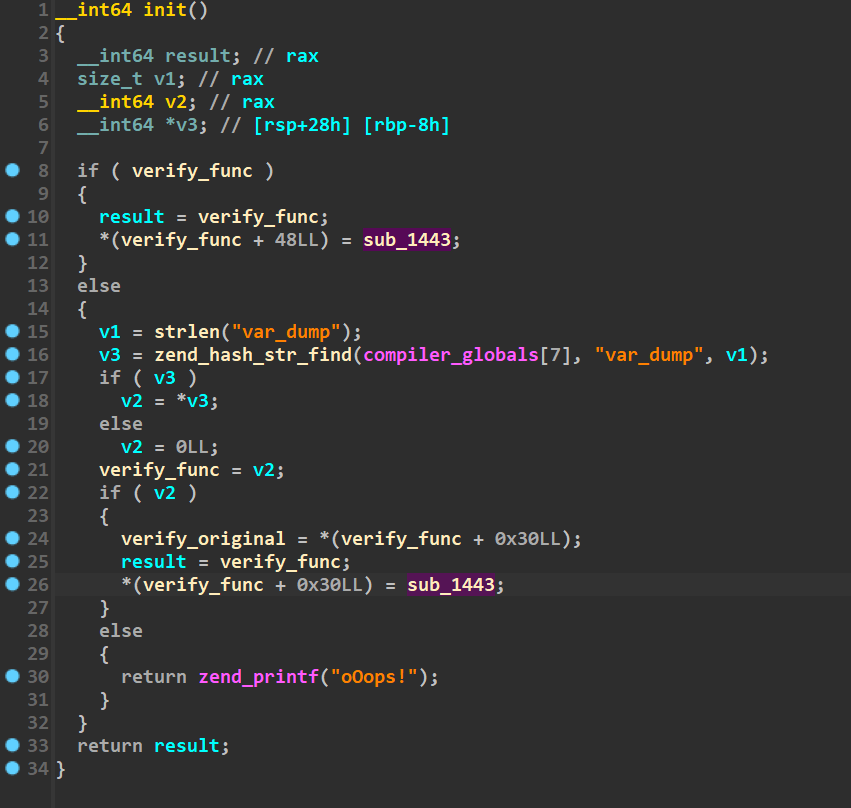
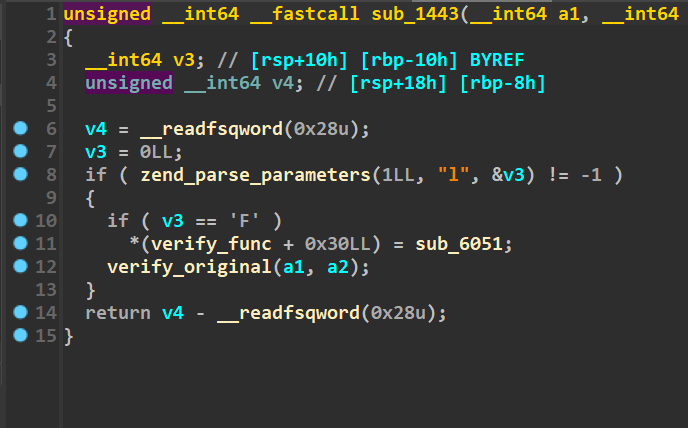
图论相关的题目 根据输入的字符进入不同的函数
起点是sub_1443
终点是sub_295778
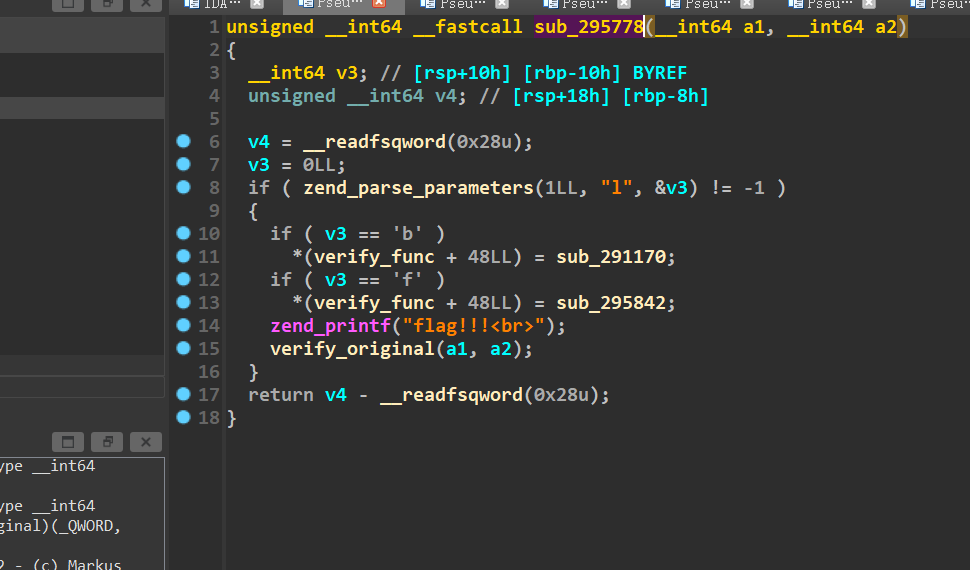
先写idapython 将所有函数的边拿到
import idaapi
import matplotlib.pyplot as plt
import idautils
import idc
all_funcs = idautils.Functions()
print(all_funcs)
keda={}
for fn in all_funcs:
#fn是个int 就是这个函数的地址
func_name = idc.get_func_name(fn)
func_name = func_name+"_ptr"
#print(func_name)
start = idc.get_func_attr(fn, FUNCATTR_START)
end = idc.get_func_attr(fn, FUNCATTR_END)
curr_addr = start
while curr_addr <= end:
# print(hex(curr_addr),idc.GetDisasm(curr_addr))
#当前地址的汇编
asmmm = idc.GetDisasm(curr_addr)
asmmm_1=idc.GetDisasm(idc.next_head(curr_addr, end))
asmmm_2=idc.GetDisasm(idc.next_head(idc.next_head(curr_addr, end),end))
asmmm_3=idc.GetDisasm(idc.next_head(idc.next_head(idc.next_head(curr_addr, end),end),end))
asmmm_4=idc.GetDisasm(idc.next_head(idc.next_head(idc.next_head(idc.next_head(curr_addr, end),end),end),end))
asmmm_5=idc.GetDisasm(idc.next_head(idc.next_head(idc.next_head(idc.next_head(idc.next_head(curr_addr, end),end),end),end),end))
#print(asmmm)
#print(asmmm_1)
#print(asmmm_2)
import re
if ("mov rax, [rbp+var_10]" in asmmm) and "cmp rax," in asmmm_1:
if func_name not in keda:
keda[func_name]=[]
keda[func_name].append([asmmm_5.split(":")[-1],asmmm_1.split(",")[-1]])
curr_addr = idc.next_head(curr_addr, end)
#break
#print(keda)
import json
c=json.dumps(keda)
with open (r"D:\CTF\J\ObfPuzz_98857a60fab26c4c9425423d23a6aa25\2.json","w")as f:
f.write(c)
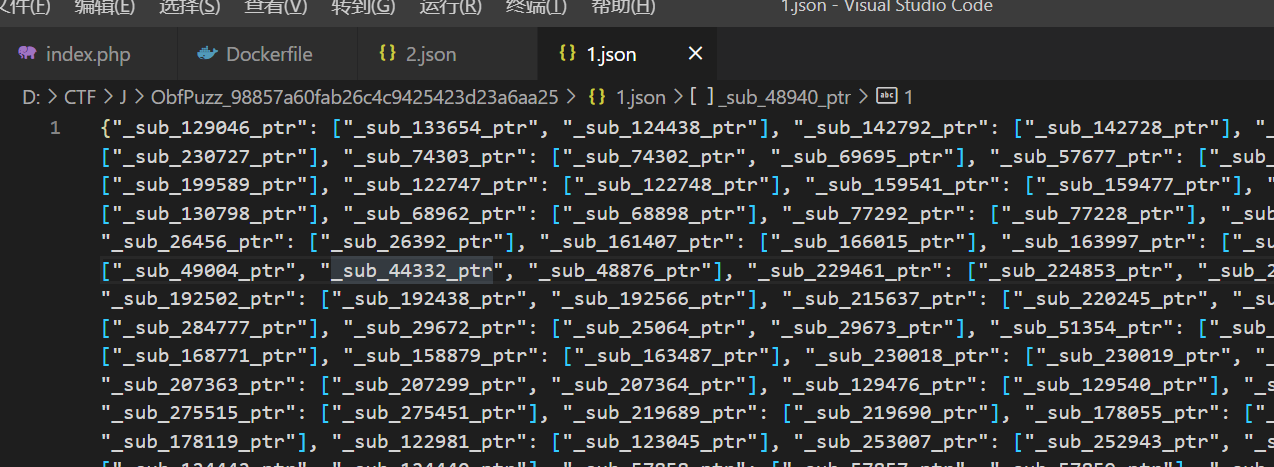
2.json如图
1.json是上个版本 脚本修改掉了
用nx导入 计算所有可能路径 再塞进去爆破就好
import string
import networkx as nx
import json
import matplotlib.pyplot as plt
with open("1.json", "r") as f:
keda = json.load(f)
with open("2.json", "r") as f:
keda2 = json.load(f)
# print(keda)
G = nx.DiGraph()
for x in keda.keys():
G.add_node(x)
for x in keda.keys():
for c in keda[x]:
G.add_edge(x, c)
start = "_sub_295778_ptr"
tem=[]
for path in nx.all_simple_paths(G, source="_sub_1443_ptr", target="_sub_295778_ptr"):
tem.append(path)
# print(tem[4])
for x in tem:
flag = ""
for index in range(1, len(x)):
flagt = keda2[x[index - 1]]
for tessssss in flagt:
if tessssss[0] == x[index]:
flag += tessssss[1].split("'")[-2]
# if "sub_295778" in x[-1]:
# print(flag)
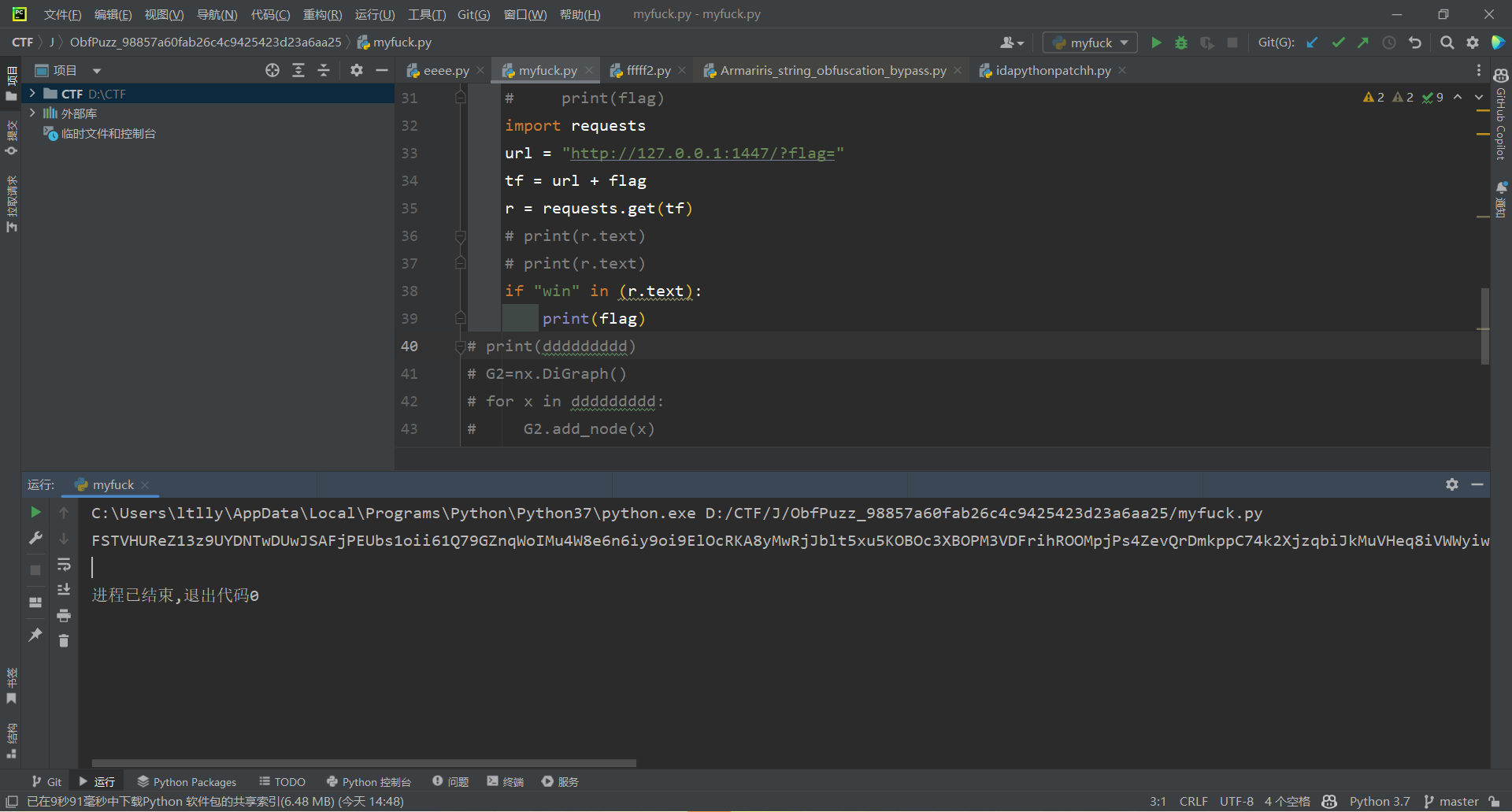
import requests
url = "http://127.0.0.1:1447/?flag="
tf = url + flag
r = requests.get(tf)
# print(r.text)
# print(r.text)
if "win" in (r.text):
print(flag)
# print(ddddddddd)
# G2=nx.DiGraph()
# for x in ddddddddd:
# G2.add_node(x)
# for x in ddddddddd:
# for c in keda[x]:
# G2.add_edge(x,c)
# c=G2.nodes()
# e=G2.out_degree()
# e=list(e)
# e.sort(key=lambda x:x[1],reverse=True)
# print(e)
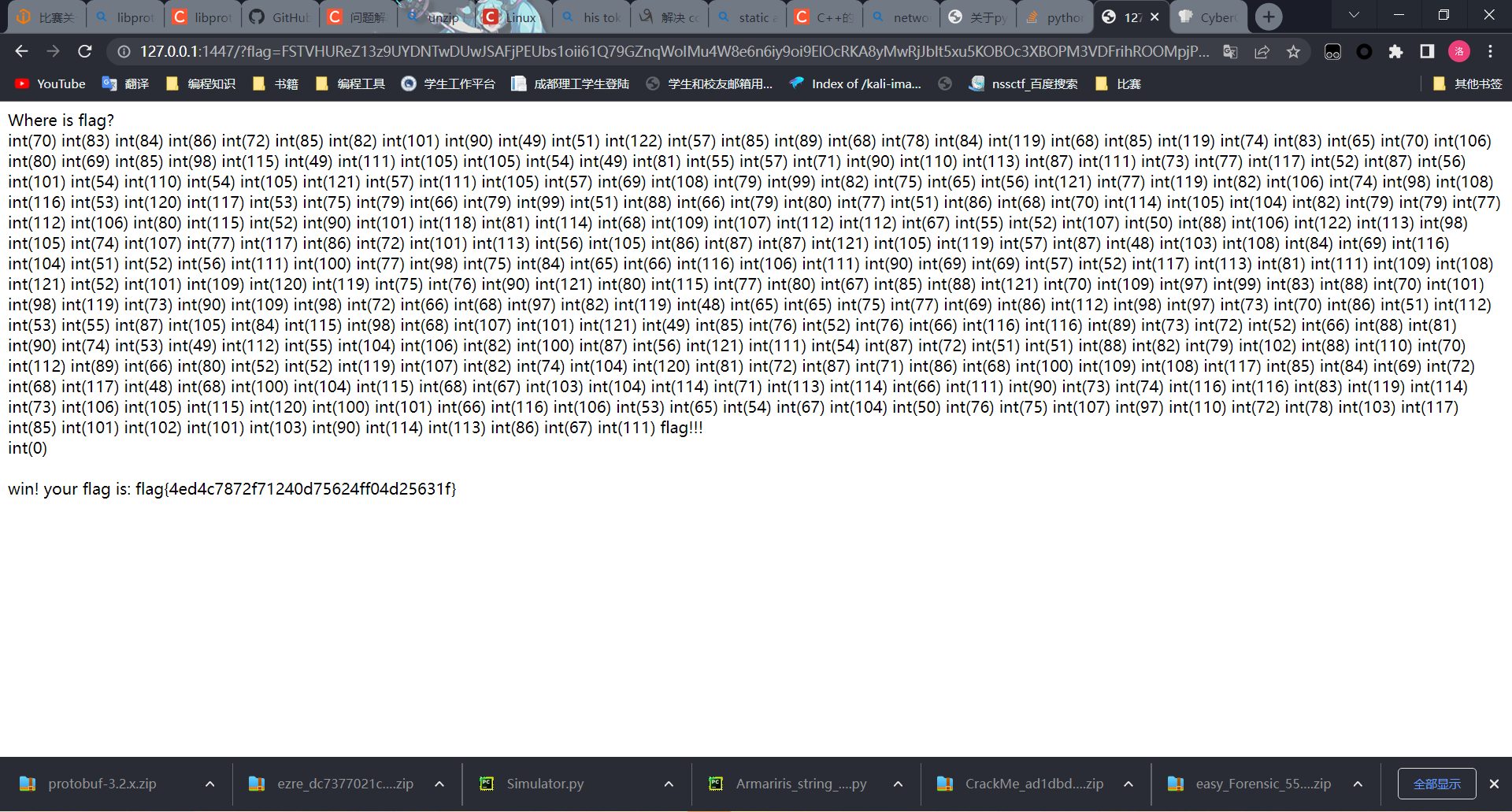
flag{4ed4c7872f71240d75624ff04d25631f}


