hws2022 wp
挺简单一个比赛 但是都在打强网杯
misc
最伟大的作品
听 输入谱子即可
random
随机数种子已知 读rgb加回去就好
import random
from PIL import Image
from hashlib import md5
from Crypto.Util.number import long_to_bytes as n2b
random.seed(793211)
def pbl(bits):
num = random.getrandbits(bits)
bins = []
while num:
bins.append(num & 1)
num >>= 1
while len(bins) != bits:
bins.append(0)
return bins
if __name__ == '__main__':
fuck = Image.open('xx.png')
original = Image.open('1.png')
x, y = fuck.size
bits = x * y
r1, r2 = pbl(bits), pbl(bits)
flen=len(n2b(random.getrandbits((bits - 28) * 8)))
testtt=[i for i in range(flen+28)]
random.shuffle(testtt)
# print(testtt)
r3=[]
for i in range(x):
for j in range(y):
pix = fuck.getpixel((i, j))
pix1=original.getpixel((i, j))
r3.append(pix[2]^pix1[2])
for i in range(28):
print(chr(r3[testtt.index(i)]),end="")
侧信道
侧信道1
一个是1 一个是0 转hex即可
re
re1
tea pro
逻辑啥的都很简单
#include <iostream>
#include <string>
#include <fstream>
#include <stdint.h>
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
#include <math.h>
#include <algorithm>
using namespace std;
void teaaaa(unsigned int a[8], unsigned int key[6])
{
unsigned int v2; // r9d
unsigned int sum; // edi
unsigned int V1; // ebp
unsigned int V0; // esi
unsigned int V2; // r14d
unsigned int V3; // r15d
unsigned int V4; // r12d
unsigned int V5; // r13d
unsigned int V7; // r13d
unsigned int V6; // r13d
unsigned int T; // r13d
unsigned int index; // r13d
unsigned int t1; // r13d
unsigned int t2; // r13d
unsigned int t3; // r13d
unsigned int t3list[12] = {1289961540, 1289961528, 1289961536, 1289961528, 1289961536, 1289961540, 1289961532, 1289961540, 1289961532, 1289961536, 1289961528, 1289961536};
unsigned int t1list[12] = {1289961536, 1289961532, 1289961540, 1289961532, 1289961540, 1289961536, 1289961528, 1289961536, 1289961528, 1289961540, 1289961532, 1289961540};
unsigned int t2list[12]{1289961532, 1289961536, 1289961528, 1289961536, 1289961528, 1289961532, 1289961540, 1289961532, 1289961540, 1289961528, 1289961536, 1289961528};
unsigned int indexlist[12] = {0, 3, 1, 3, 1, 0, 2, 0, 2, 1, 3, 1};
unsigned int sumlist[12] = {1788458156, 3428989683, 774553914, 2415085441, 4055616968, 1401181199, 3041712726, 387276957, 2027808484, 3668340011, 1013904242, 2654435769};
for (int i = 0; i < 12; i++)
{
sum = sumlist[i];
V0 = a[0];
V1 = a[1];
V2 = a[2];
V3 = a[3];
V4 = a[4];
V5 = a[5];
V6 = a[6];
V7 = a[7];
T = sum ^ V0;
t3 = key[(sum >> 2) & 3];
t2 = key[(sum >> 2) & 3 ^ 2];
t1 = key[(sum >> 2) & 3 ^ 1];
index = indexlist[i];
V7 -= (T + (key[index] ^ a[6])) ^ (((16 * a[6]) ^ (V0 >> 3)) + ((a[6] >> 5) ^ (4 * V0)));
a[7] = V7;
v2=V7;
V6 -= (((sum ^ V7) + (t2 ^ V5)) ^ (((16 * V5) ^ (V7 >> 3)) + ((V5 >> 5) ^ (4 * V7))));
a[6] = V6;
V5 -= ((t1 ^ V4) + (sum ^ V6)) ^ (((16 * V4) ^ (V6 >> 3)) + ((V4 >> 5) ^ (4 * V6)));
a[5] = V5;
V4 -= ((sum ^ V5) + (t3 ^ V3)) ^ (((16 * V3) ^ (V5 >> 3)) + ((V3 >> 5) ^ (4 * V5)));
a[4] = V4;
V3 -= ((sum ^ V4) + (key[index] ^ V2)) ^ (((16 * V2) ^ (V4 >> 3)) + ((V2 >> 5) ^ (4 * V4)));
a[3] = V3;
V2 -= ((sum ^ V3) + (t2 ^ V1)) ^ (((16 * V1) ^ (V3 >> 3)) + ((V1 >> 5) ^ (4 * V3)));
a[2] = V2;
V1 -= ((t1 ^ V0) + (sum ^ V2)) ^ (((16 * V0) ^ (V2 >> 3)) + ((V0 >> 5) ^ (4 * V2)));
a[1] = V1;
V0 -= ((sum ^ V1) + (t3 ^ v2)) ^ (((16 * v2) ^ (V1 >> 3)) + ((v2 >> 5) ^ (4 * V1)));
a[0] = V0;
}
}
int main(int argc, char const *argv[])
{
unsigned int enc[9] = {
0x10BD3B47, 0x6155E0F9, 0x6AF7EBC5, 0x8D23435F, 0x1A091605, 0xD43D40EF, 0xB4B16A67, 0x6B3578A9,0};
unsigned int key[6] = {
0x00001234, 0x00002345, 0x00004567, 0x00006789, 0x00000000, 0x00000000};
teaaaa(enc, key);
// printf("%32x",5);
puts((char *)&enc);
}
re2
字符串发现wrong
小解一下密发现fakeflag
看到tls回调
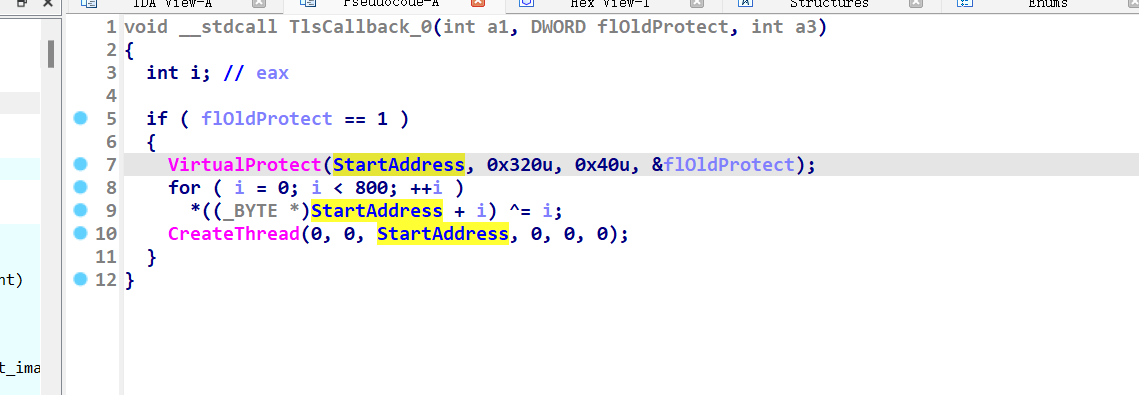
idapython脚本解密
import idc
import idaapi
import idautils
startadd=0x00401040
for i in range(800):
c=idc.get_wide_byte(startadd+i)
idc.patch_byte(startadd+i, c^i)
来到真正的check函数
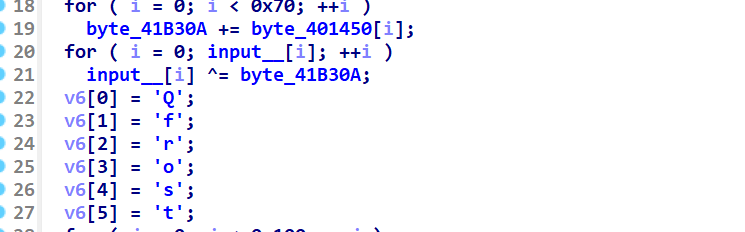
先异或某个定值
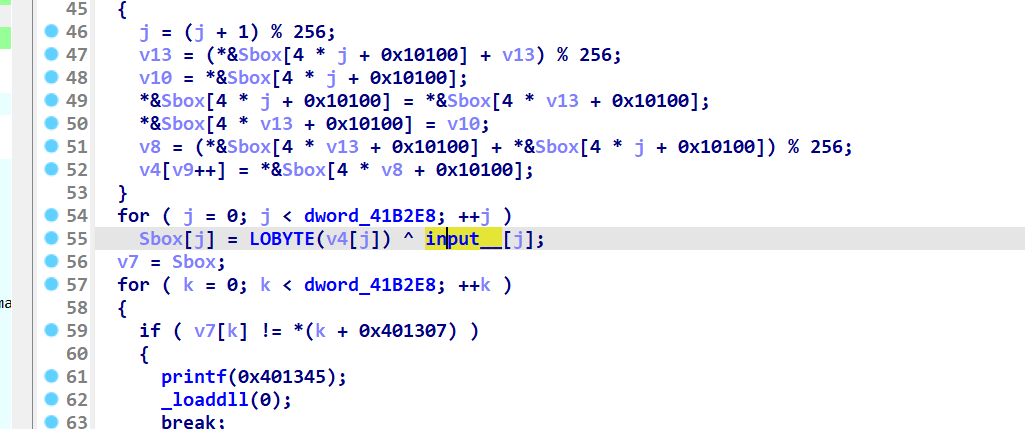
再异或某个sbox
因为patch了 懒得动调
就按原逻辑复现一下sbox和前面的定值即可
encc = [0x7F, 0xB6, 0x88, 0x12, 0xDC, 0xC3, 0xDE, 0xDB, 0x30, 0x24, 0xE3, 0xC1, 0x0F, 0xC9, 0x7F, 0xC2, 0x4D, 0x9C,
0x6B, 0x02, 0x26, 0x20, 0xF1, 0x25, 0xA0, 0xE3, 0xC6, 0xDE]
fuck1 = [0x55, 0x8B, 0xEC, 0x53, 0x56, 0x57, 0x8B, 0x4D, 0x10, 0x8B, 0x81, 0xC0, 0x00, 0x00, 0x00, 0x8B, 0x99, 0xB8,
0x00, 0x00, 0x00, 0x8B, 0x13, 0x81, 0xFA, 0xCC, 0xCC, 0xCC, 0x8B, 0x75, 0x21, 0x3D, 0x46, 0x02, 0x00, 0x00,
0x75, 0x0C, 0x43, 0x89, 0x99, 0xB8, 0x00, 0x00, 0x00, 0x74, 0x40, 0x75, 0x3E, 0xE9, 0x83, 0xC3, 0x02, 0x89,
0x99, 0xB8, 0x00, 0x00, 0x00, 0x74, 0x32, 0x75, 0x30, 0xE9, 0x81, 0xFA, 0xCC, 0xCC, 0x8B, 0x04, 0x75, 0x1A,
0xC7, 0x05, 0xE4, 0xB2, 0x41, 0x00, 0x01, 0x00, 0x00, 0x00, 0x68, 0x88, 0x13, 0x00, 0x00, 0xFF, 0x15, 0x04,
0x30, 0x41, 0x00, 0xE8, 0x6B, 0x34, 0x00, 0x00, 0x81, 0xFA, 0xCC, 0x8B, 0x04, 0x24, 0x75, 0x05, 0xE8, 0x11,
0xFF, 0xFF, 0xFF, 0x33]
fffff=0
for x in fuck1:
fffff+=x
fffff=fffff%256
print(fffff)
t = 0
v6 = [0] * 6
v6[0] = 81
v6[1] = 102
v6[2] = 0x72
v6[3] = 111
v6[4] = 115
v6[5] = 116
sbox0 = [v6[i % 6] for i in range(0x100)]
sbox1 = [i for i in range(0x100)]
v13 = 0
for j in range(0x100):
v13 = (sbox0[j] + sbox1[j] + v13) % 256
v10 = sbox1[j]
sbox1[j] = sbox1[v13]
sbox1[v13] = v10
j = 0
v13, v10 = 0, 0
v4 = [0] * 256
for iii in range(256):
j = (j + 1) % 256
v13 = (v13 + sbox1[j]) % 256
v10 = sbox1[j]
sbox1[j] = sbox1[v13]
sbox1[v13] = v10
v8 = (sbox1[v13] + sbox1[j]) % 256
v4[iii] = sbox1[v8]
for index in range(len(encc)):
encc[index]=encc[index]^v4[index]^fffff
for x in encc:
print(chr(x),end='')
crypto
HWS-easyRSA
就会求逆元就行了
p = 31893593182018727625473530765941216190921866039118147474754069955393226712079257707838327486268599271803
seed1 = 25820280412859586557218124484272275594433027771091486422152141535682739897353623931875432576083022273940
seed2 = 24295465524789348024814588142969609603624462580932512051939198335014954252359986260009296537423802567677
seed3 = 14963686422550871447791815183480974143372785034397446416396172429864269108509521776424254168481536292904
import gmpy2
a = gmpy2.invert(seed2 - seed1, p) * (seed3 - seed2) % p
b = (seed3 - a * seed2) % p
flag = (seed1 - b) * gmpy2.invert(a, p) % p
print(int(flag).to_bytes(43, byteorder="big"))


